
2023-4-7 21:0:51 Author: www.sentinelone.com(查看原文) 阅读量:23 收藏
Operation Cookie Monster | Genesis Market Bites the Dust
This week, cyber cops from multiple countries took down another major marketplace that traded stolen credentials and other sensitive information, known as Genesis market. According to the DoJ, Genesis offered access to over 1.5 million compromised devices worldwide and was a key enabler of ransomware.
Operation Cookie Monster involved law enforcement agencies from the Australia, Canada, Germany, Poland, Sweden, the U.K and the U.S. Aside from the dismantling of the site, authorities arrested 120 people known to be regular users of the site and conducted 200 searches across a number of countries.
Genesis offered criminals a variety of stolen data, including session cookies (hence the operation name) and other metadata criminals could use to access victim’s personal and business accounts even when those were protected by MFA.
The DoJ said that credentials and other data found on the site included those belonging to victims associated with the White House, Department of State, Justice Department, the IRS, the Department of Energy, the U.S. Postal Service, NASA, and the Department of Defense.
A list of compromised victims has been provided to the Have I Been Pawned (HIBP) website. Concerned readers can check with HIBP to see if their credentials have appeared in various data breaches including Operation Cookie Monster.
The seizure of Genesis follow last month’s shuttering of BreachForums and represents a significant step forward in thwarting cybercrime and bringing to justice criminals who make use of such services.
Unpatched Windows | Millions of Endpoints Vulnerable to CISA KEVs
If the first rule of cybersecurity is “Patch early, and patch often”, then it seems the owners of millions of internet-facing endpoints have yet to hear it. Researchers this week said almost 900 known exploitable vulnerabilities (KEVs) catalogued by CISA over the last decade remain unpatched on around 15 million services today.
According to the research, around 3.5 million Windows hosts reachable from the public internet are vulnerable to one or more of 137 CVEs in CISA’s KEV. 4.5 million endpoints of the 15 million total are vulnerable to KEVs discovered between 2010 and 2020. There are almost 200,000 exposed hosts that remain vulnerable to CVE-2014-0160, aka Heartbleed, disclosed nearly ten years ago. Of the more recent bugs such as ProxyShell and ProxyLogon, both of which received a deluge of media attention in 2021, there remain 14.5K and 4.9K unpatched machines exposed to the internet.
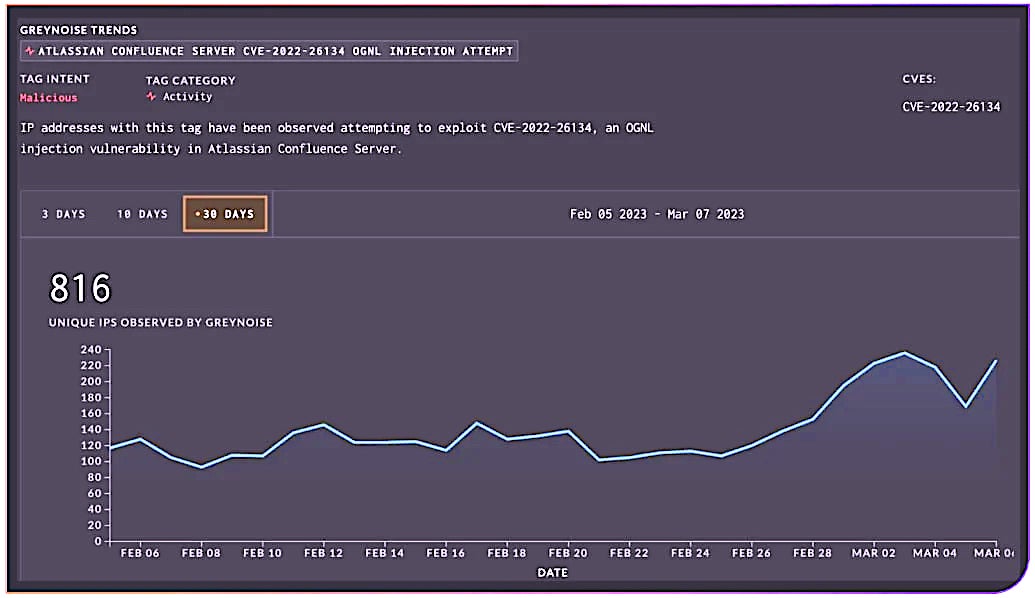
Using data from Greynoise, the researchers established that the Confluence bug CVE-2022-26134 was the most exploited, with over 800 exploitation attempts in the past month alone. The last 30 days prior to the report also showed 66 exploitation attempts of Log4Shell.
Organizations can have multiple dependencies that make patching complex. However, the researchers report that Microsoft Windows, Internet Explorer, Microsoft Office, and Win32k along with Adobe Flash Player account for a quarter of CISA’s Known Exploited Vulnerabilities catalog. Therefore, it is advisable to patch these as a priority and/or reduce dependencies on these services where practicable.
SmoothOperator Keeps Calling | Backdoors Target Cryptocurrency Companies
Details about targets and payloads are still emerging in the wake of last week’s supply chain attack on 3CX, dubbed SmoothOperator and widely attributed to North Korean aligned threat actor Lazarus. However, researchers this week linked the campaign to a known backdoor dubbed “Gopuram”, used in attacks against cryptocurrency companies.
Gopuram was seen in an attack associated with AppleJeus as long ago as 2020, but a spike in Gopuram infections had been observed in the weeks just prior to disclosure of the 3CX compromise. These compromises subsequently turned out to be related to the SmoothOperator campaign and targeted cryptocurrency companies.

The Gopuram backdoor reaches out to a C2 server and requests tasking from the operator. Available commands include:
| Command | Description |
| Ping | Pings a host specified in the argument. |
| Connect | Connects to a given host via a socket and waits for the server to send data. |
| Registry | Manipulates registry (lists, adds, deletes and exports keys). |
| Service | Manipulates (creates, lists, starts, stops and deletes) services. |
| Timestomp | Performs timestomping on files. |
| Inject | Performs payload injections through syscalls via mapping a shellcode to a remote process and creating a remote thread. |
| KDU | Kernel Driver Utility that allows an attacker to bypass driver signature enforcement. |
| Update | Encrypts a provided payload and writes it to the C:\Windows\System32\config\TxR\ |
| Net | Partially implements features of the net command: management of users, groups, sessions and network shares. |
The researchers identified the following additional indicators of compromise:
SHA1 011660842c3299e14a6ee7122494b9c78d448388 1b204f5969eb2ec9326f27244545d1f56547b14e c8c21c8a5d86c57650a887bf798ae83095a40e97 FILE PATHS C:\Windows\System32\config\TxR\.TxR.0.regtrans-ms C:\Windows\system32\catroot2\edb.chk.log
Security teams are advised to conduct additional threat hunting based on these IoCs. Further details are available from SentinelOne here and Kaspersky here.
如有侵权请联系:admin#unsafe.sh