2023-3-24 21:0:8 Author: www.sentinelone.com(查看原文) 阅读量:21 收藏
The Good
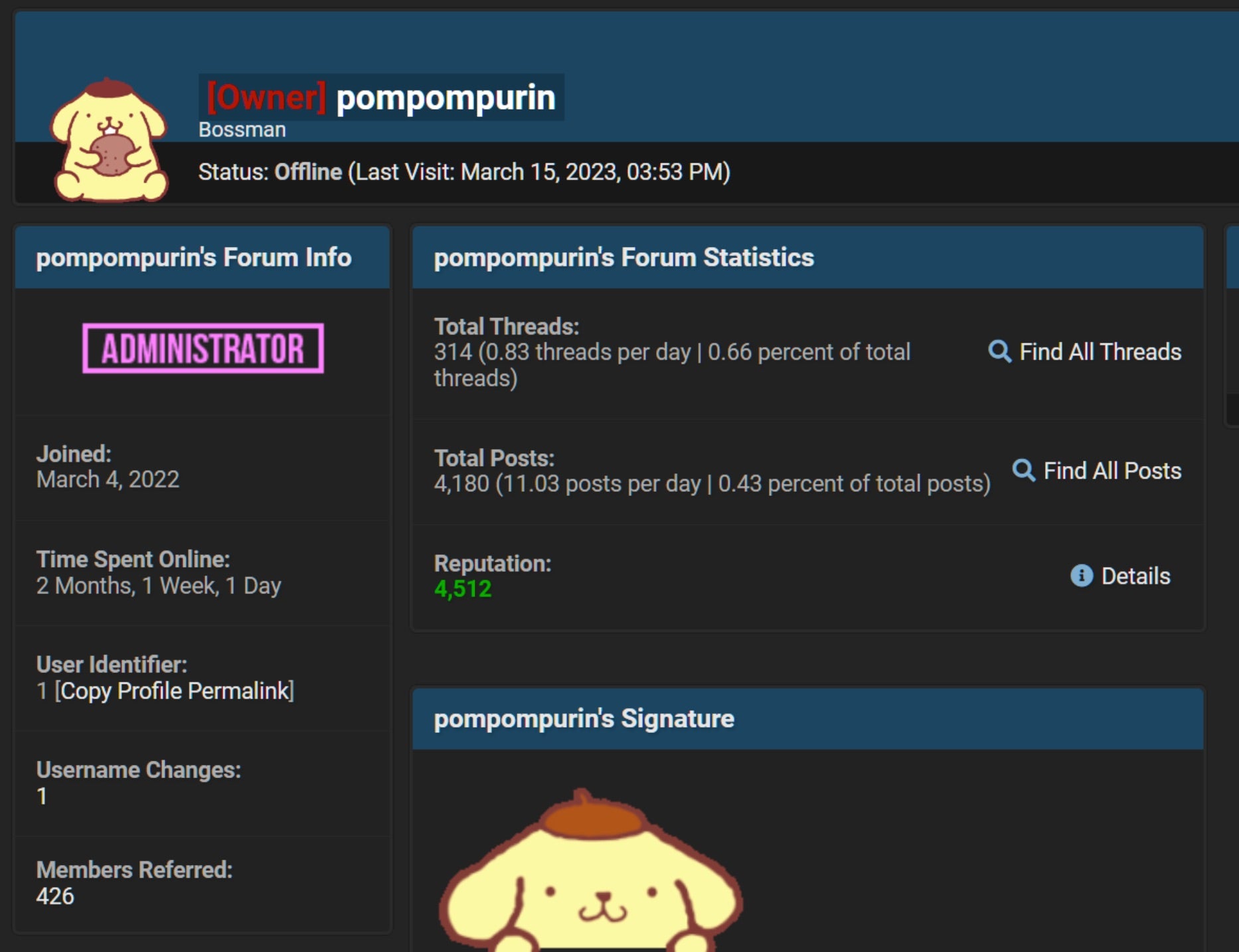
Dark forum site operator, ‘Pompompurin’, was arrested this week by U.S. law enforcement on the charge of conspiracy to commit access device fraud. One Conor Brian Fitzpatrick was arrested in his home where he admitted this alias and to owning and administrating the website, BreachForums, well-known across the cybercrime ecosystem for hosting stolen databases and selling personal data for fraudulent activities. Officials reported that Fitzpatrick had been under close investigation for over a year before the arrest.
After the DoJ announced the successful seizure of the RaidForums website in April of 2022, it was widely speculated that Fitzpatrick created BreachForums as its successor. Since then, BreachForums has gained notoriety for being one of the most active hacker forums available to cybercriminals.
Under the Pompompurin alias, Fitpatrick quickly filled in the gap of selling and leaking sensitive information through social media, propelling the site to becoming one of the largest data leak forums of its kind. Fitzpatrick has also been connected to various high-profile cyberattacks, including those involving the FBI, Twitter, and popular online stock trading platform, Robinhood. At the time of its takedown, BreachForums had more than 330000 members, 47000 threads, and almost one million posts.
Though the site is now defunct, these seizures remain critical in the uphill fight against increasingly sophisticated cybercrime syndicates. BreachForums was just one of many leak sites and dark marketplaces causing ongoing damage to government organizations and enterprises of all industries. Just as BreachForums rose from the ashes of RaidForums, it is vital for businesses to remain vigilant with protecting their data from opportunistic threat actors as new forums inevitably continue to propagate.
The Bad
A new Go-based, DDoS-focused malware dubbed ‘HinataBot’ hit the scene this week, taking its name from the popular anime series, Naruto. According to researchers, the threat actors behind the new malware were first observed in December of last year and have since started to develop their own malware approximately two months ago. Current indications point to the malware’s active evolution as it is updated by its authors and operators.

HinataBot is written in Golang and is the latest in emerging Go-based threats that continue to proliferate in the cyber underground. Go is increasingly in use by attackers for its high performance and support for multiple architectures. Security researchers have noted that Go-based malware presents extra challenges to analyze and reverse engineer.
So far, samples of the malware have been discovered in HTTP and SSH honeypots, where they have been observed abusing weak credentials and old remote code execution (RCE) vulnerabilities from as far back as nearly a decade ago. Analysis on the infection process for HinataBot has shown exploitation of the miniigd SOAP service on Realtek SDK devices (CVE-2014-8361), Huawei HG532 routers (CVE-2017-17215), as well as exposed Hadoop YARN servers.
The discovery of HinataBot brings to light the responsibilities of organizations to deepen their visibility surrounding deployed services as well as weak spots in their overall infrastructure. In this case, nearly 10-year old vulnerabilities are still being exploited as threat actors continue to use overlooked or low-hanging resources to evade detection, build on new functionalities, and get a high return on through small investments.
The Ugly
In a joint technical report released this week by SentinelLabs researchers and QGroup GmbH, telecom providers in the Middle East have become the latest target in a long-running cyberattack campaign dubbed Operation Tainted Love. Based on the investigations, this campaign has been attributed to Chinese-based cyber espionage threat actors.
Initial attack vectors observed in the string of cyberattacks began with the infiltration of Internet-facing Microsoft Exchange servers to deploy web shells for command execution. After securing a foothold, the attacker conducted a variety of reconnaissance, credential theft, lateral movement, and data exfiltration activities.
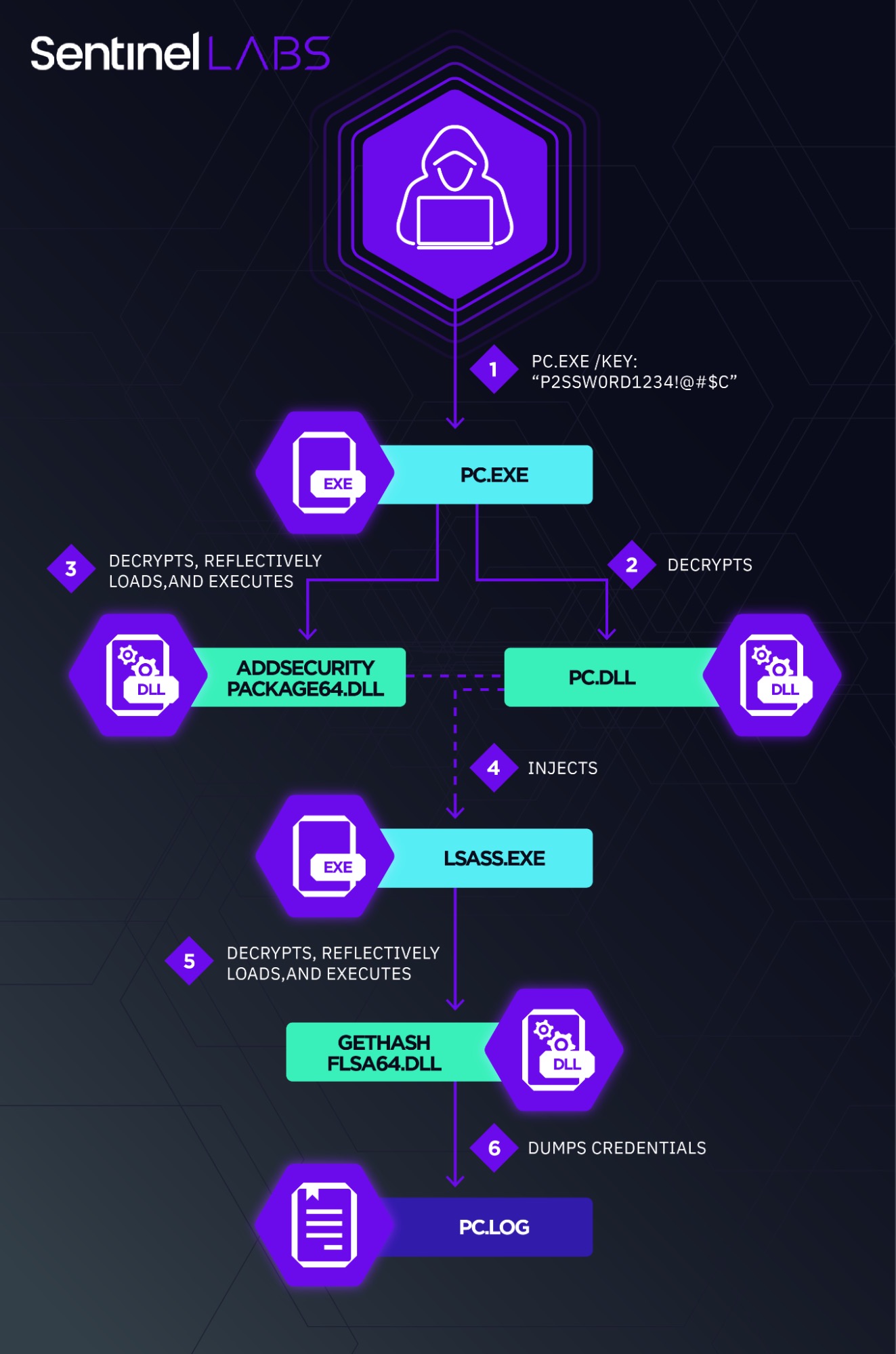
In the latest attacks on Middle Eastern telecom providers, the actors have been seen deploying a custom variant of Mimikatz called mim221 to facilitate lateral movement techniques and privilege escalation as well as all-new anti-detection and credential theft capabilities. Special-purpose modules like these underscore the threat actor’s drive to advance their toolset with a marked focus on stealth. Techniques noted by SentinelLabs researchers included in-memory mapping of malicious images to evade EDR API hooks and file-based detections, the termination of Event Log threads instead of the host process to inhibit logging without raising suspicions, and staging a credential theft capability in the LSASS process itself by abusing native Windows capabilities.
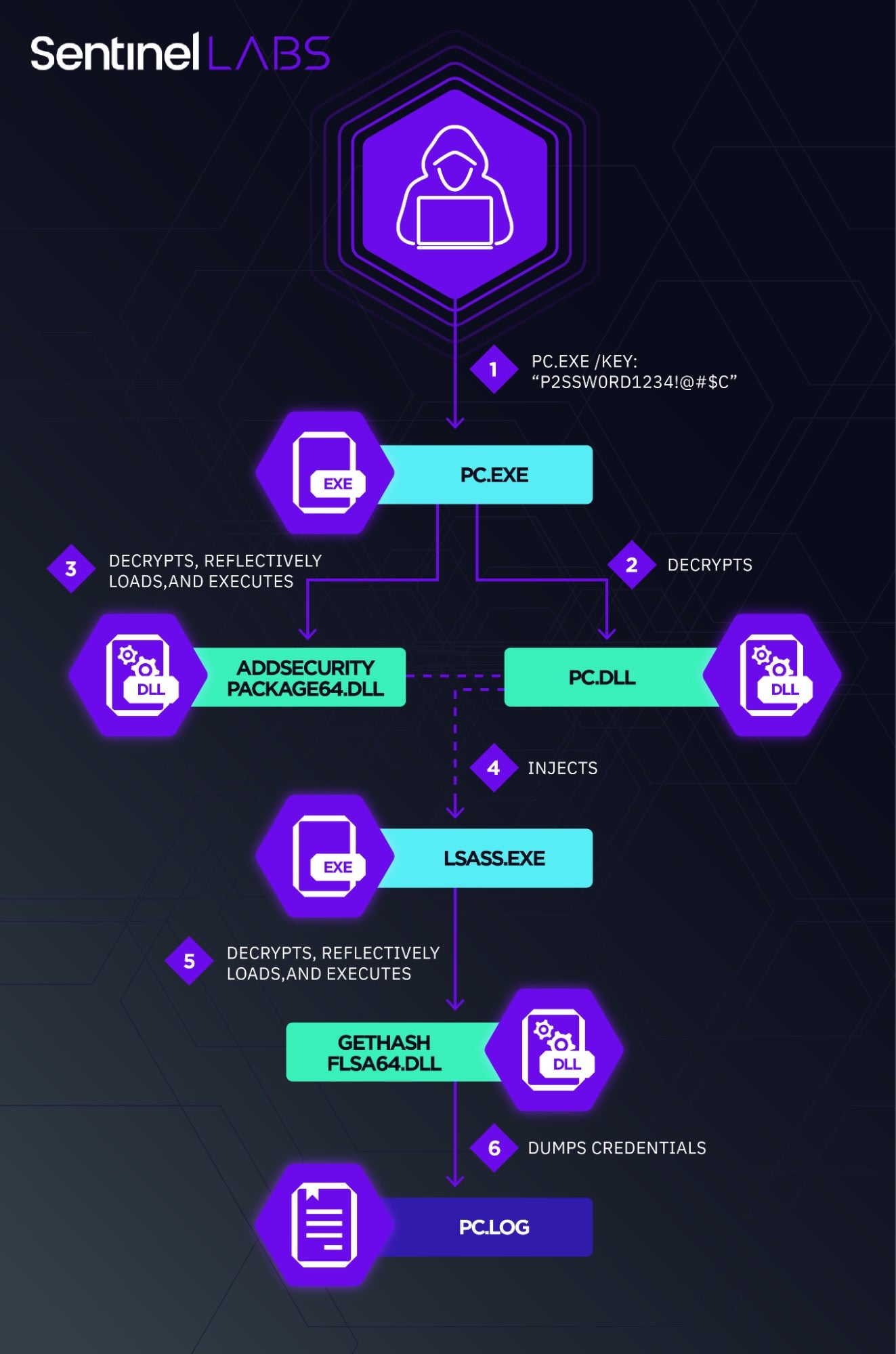
Telecom providers find themselves frequently in the crosshairs of attack for the large amounts of personal client data they hold and sensitive information transmitted. This campaign is expected to continue as the Chinese-linked threat actors upgrade their malware and zero in on strategic targets in the Middle East.
如有侵权请联系:admin#unsafe.sh