2023-2-3 22:0:46 Author: www.sentinelone.com(查看原文) 阅读量:30 收藏
The Good
The FTC this week has handed out a $1.5 million penalty to a U.S. healthcare company that promised its customers it would “never share personal health information with advertisers or third parties” and then allegedly did precisely that.
The Department of Justice filed an enforcement action on behalf of the FTC against GoodRx under its new Health Breach Notification rule. The complaint against the company accused it of failing to notify customers about unauthorized disclosure of health PII (personally identifiable information). According to the FTC, GoodRx repeatedly shared individually identifiable health information over a four year period with Facebook, Google, Twilio, Branch, and Criteo.
FTC enforcement action to bar GoodRx from sharing consumers’ sensitive health info for advertising: https://t.co/ag4TCYS2Ii /1
— FTC (@FTC) February 1, 2023
The FTC went on to complain that GoodRx had uploaded contact details of its own customers to Facebook along with advertising IDs, and that it used privileged information about those customers’ previous medication purchases to target their profiles with health-related ads. In doing so, the company exposed their information to Facebook, which itself is facing multiple ongoing lawsuits related to scraping data from hospital websites for use in targeted ads.
FTC director Samuel Levine said of the action that “Digital health companies and mobile apps should not cash in on consumer’s extremely sensitive and personally identifiable health information” and that the FTC would continue to use its legal authority to protect American consumers.
The Bad
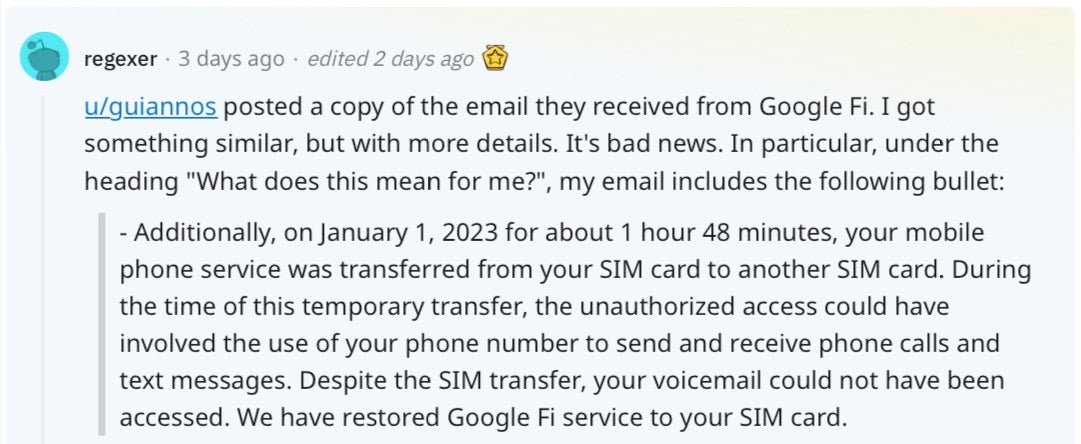
SIM swapping attacks, where a threat actor impersonates a customer of a mobile phone carrier and requests a transfer of the customer’s number to a new device, have been utilized to pull off some high profile hacks recently. This week, it’s bad news for Google Fi customers, who have been targeted by hackers that gained access to technical SIM data after breaching a Google Fi network provider.
Google’s U.S. telecommunications and mobile internet service, Google Fi, informed customers this week that personal data had been exposed after a breach of one of its network providers. Google notified customers that the incident had exposed their phone numbers, SIM card serial numbers, and other details. However, the company emphasized that there was no access to Google’s systems or any systems overseen by Google.
Users on social media, however, soon began reporting notifications from Google Fi that described SIM swapping attacks.
SIM swapping attacks allow the attacker to receive both phone calls and SMS text messages intended for the legitimate user and, among other things, allow attacks to intercept text-based 2FA authentication messages.
Google says its incident response team investigated the breach and implemented measures to secure data on the provider’s system and notified everyone potentially impacted. The SIM swapping attacks were temporary and Google Fi has since restored service to all customers’ registered SIM cards.
The Ugly
Threat actors have been creating malicious OAuth applications as part of a phishing campaign aimed at breaching Microsoft cloud services, it was revealed this week.
According to MSRC, threat actors ran a consent phishing campaign after impersonating companies enrolling in MCPP/MPN (Microsoft Cloud Partner Program, aka Microsoft Partner Network). Consent phishing works by tricking users into granting permissions to malicious cloud applications that can then be weaponized to compromise legitimate cloud services and access sensitive data.

Once victims granted access to the malicious OAuth apps, threat actors used them to exfiltrate email mailboxes, likely with the further objective to use the stolen data in email Reply Chain attacks, Business Email Compromises (BEC), and spear phishing attacks.
The campaign, which primarily targeted MCPP customers in the UK and Ireland, was first spotted on December 15th last year, with the actors using fraudulent partner accounts to register OAuth applications in Azure AD that appeared to be from verified publishers.
The Redwood tech giant says that all identified fraudulent applications have now been disabled and affected customers informed. Even so, it comes amid turbulent times for the company. Despite announcing security sales of over $20 billion in 2022, the company’s products across endpoint and cloud remain notorious for multiple high-impact vulnerabilities and cloud-based attack vectors.
Attacks using bogus OAuth apps have targeted Microsoft’s cloud services before, with separate threat activities seen in January 2022 and September 2022, according to reports.
如有侵权请联系:admin#unsafe.sh