2022-12-30 22:0:39 Author: www.sentinelone.com(查看原文) 阅读量:30 收藏
Looking back at 2022, we’ve reported on positive strides and wins seen across our community as well as some seriously heinous threats to the digital landscape. The Good, Bad and the Ugly series takes this week’s edition to rewind and revisit the best, the worst, and the ugliest from the past 12 months.
The Best
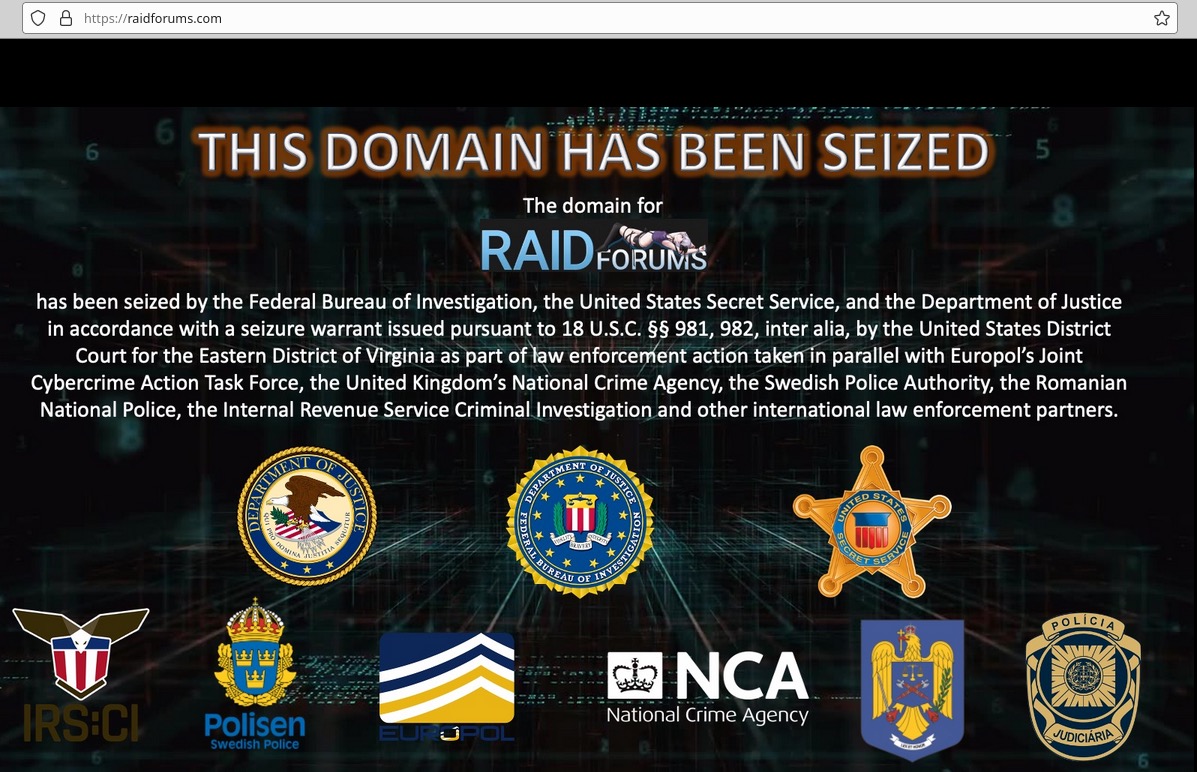
Throughout 2022, law enforcement groups across the globe made a sweeping number of arrests – many the result of international collaborations between agencies. Crackdowns this year saw the arrests of key members from infamous cyberthreat gangs such as JabberZeus and LockBit, as well as the shuttering of multiple darknet marketplaces and malicious domains.
From a policy standpoint, the U.S. government made good on their pledge to harden the country’s cyber posture by implementing the Digital Services and Digital Markets Acts, publishing new guidelines for securing supply chain operations, and adding key cybersecurity hires to their Crypto Assets and Cyber Units.
SentinelOne’s focus on technical innovations, partnership, and sharing security intel was best highlighted by the successful launch of LABScon this September. At this inaugural security conference, SentinelLabs hosted a gathering of the most prominent speakers and researchers from the infosec community with the goal of advancing cybersecurity research for the benefit of a collective digital defense.

The Worst
Despite the wins, threat actors were busy across the year attacking targets old and new.
At the beginning of the year, a Red Cross contractor suffered a large-scale cyberattack exposing the personally identifiable information (PII) of over half-million individuals. In April, a ransomware attack on the Costa Rican government triggered a national emergency that took over a month to remediate. In July, it was revealed that a Conti attack on a healthcare debt collection firm impacted more than 1.91 million patients and 650 medical providers.
As students returned to education in September, the Los Angeles school district supporting over 640,000 students disclosed a data breach on their IT systems.
Los Angeles Unified Targeted by Ransomware Attack
For more information, please visit https://t.co/Itdix5TlqK. pic.twitter.com/HDgktJKT0S
— Los Angeles Unified (@LASchools) September 6, 2022
Cybercrime-as-a-Service has introduced a new wave of low and medium-level cyber criminals to more complex and devastating attack methods. Services like Caffeine, for example, allow anyone on the internet to pay for customized phishing kits and URLs for hosting malware payloads.
Threat groups such as Vice Society were reported in October to be taking on a fluid approach to the spectrum of data extortion. Adapting different tactics based on their targets, some groups have been known to demand ransoms without deploying ransomware, instead threatening victims with exposure of the leaked data. Public exposure of sensitive data can be catastrophic for some organizations, while for others, just the cost of returning to normal operations can put an organization out of business entirely.
Attacks on enterprise cloud surfaces have also become an increasingly worrisome vector throughout 2022, with breaches of major companies such as Twilio, Okta, NetStandard, and LastPass raising fears that even as businesses have understood the need to harden endpoint security, cloud workloads and user identities remain easy targets.
The Ugliest
Amidst an ongoing economic downturn, active warfare, and civil unrest, the ugliest moments of 2022 showed that cybersecurity and cybersecurity awareness is a challenge for society across the board.
A feature of some of 2022’s worst moments was the increasing awareness of how governments around the world are using private espionage companies to throttle dissent and attack civilians including journalists, lawyers and civil rights protesters. In February, SentinelLabs reported on ModifiedElephant, an APT that has been targeting activists by planting false digital evidence.
A private sector offensive actor based in Austria was uncovered in July, while Spain-based IT company Variston were outed in early December as trading in commercial spyware.
Of course, the dominant news of 2022 centered around Ukraine. As the conflict in Ukraine unfolded in the early months of the year, banks, major websites, and other public services in Ukraine were hit with distributed denial-of-service (DDoS) attacks leading up to Russia’s invasion.
In February, SentinelOne researchers reported on HermeticWiper, a new custom wiper malware circulating in Ukrainian organizations in an effort to break down the country’s information systems. Shortly after, another wiper attack on Ukraine dubbed AcidRain hit satellite modems in neighboring countries.
The traffic wasn’t all one way: Russian courts and mayoral offices were targeted with CryWiper. Elsewhere, wipers were deployed by Iranian-linked APT Agrius on targets in Hong Kong, Israel and South Africa. Unlike ransomware, these wipers do not attempt to extort the victim; their intent is only to destroy the victim’s ability to operate, and collectively may be the most nefarious of cyber threats we’ve seen over the last year.
Conclusion
2022 was a year in which cybersecurity headlines reached out into the mainstream media and public consciousness more so than ever. We can hope that this increased awareness will pay dividends in 2023, as public and private organizations, and indeed individual users, develop a greater understanding of cyber risk and how to mitigate it.
Our regular weekly roundups will return next Friday. Meanwhile, find our predictions for 2023 here, and from all of us at SentinelOne, have a happy and very safe New Year.
如有侵权请联系:admin#unsafe.sh