
2022-11-23 22:36:57 Author: www.sentinelone.com(查看原文) 阅读量:25 收藏
With the rapid change in modern technologies, workforces are increasingly mobile and require direct access to applications across hybrid IT environments. They often access both on-premises and cloud applications from various devices and locations, some of which could be using public or unencrypted networks. At the same time, security teams have realized that the directory service widely used to manage the required identity-related services, Active Directory, is vulnerable, and identifying its loopholes to protect it from various attacks is a considerable challenge.
How can organizations detect and block identity-related attacks before adversaries or malicious insiders establish complete Active Directory Domain Controller (DC) dominance? How can they most effectively protect critical assets against advanced identity-based attacks?
The best approach is conditional access, which enables administrators to allow or deny access to resources based on the detection of suspicious or malicious activity. In this post, we’ll discuss conditional access solutions, why they are important, and how they can strengthen the overall security posture of an organization.

The Growing Risk of Identity-related Breaches
Identity-related breaches remain the most significant threat of compromise, lost data, or malicious operations. According to the Identity Defined Security Alliance (IDSA) report, 84% of organizations experienced an identity-related breach in the past year, 2021. The most common attacks are phishing attacks (59%), inadequately managed privileges (36%), and stolen credentials (33%).

Research conducted by Enterprise Management Associates also reported that 50% of organizations experienced an attack on Active Directory (AD), with more than 40% indicating the attack was successful.
Microsoft AD is the prime target for malicious operations. When attackers gain access to a compromised network, they attempt to discover domain identities and expand access to applications and data with stolen credentials. They can establish persistence, escalate privileges, and move laterally. Attackers attempt to take complete domain dominance through various means, such as OS Credential Dumping, stealing, or forging Kerberos tickets to perform a Pass-the-ticket Attack.
What Is Conditional Access and Why Is It Important?
Conditional access refers to the policy-driven concept of allowing access to corporate resources only when certain criteria are met. The solution is traditionally used in authentication systems to grant access to applications only if users go through Multi-Factor Authentication (MFA) while accessing a trusted resource from a new location or when attempting to access applications or data of a sensitive nature.
The same approach has been adopted for threat protection as well. Conditional access provides an extended layer of security by allowing secure access to on-premises and cloud applications only from trusted users or devices.
Conditional access is a mechanism to enforce access control policies based on suspicious or malicious activity. It is a risk-driven approach calculated based on risk factors such as severity and type of attack, among others.
Perimeter-based security is the traditional and obsolete solution for protecting external attackers from accessing the corporate network and applications. An identity security solution which offers conditional access capabilities allows security administrators to respond to the identified suspicious activities. It can help to quickly detect anomalous user or device behavior, restricting or allowing access to sensitive corporate resources. Conditional access enables administrators to set allow/deny conditions based on the severity of the threat detected.
Every organization can benefit from the following key features of conditional access solutions to improve their defense against threats and provide secure services to their users.
- Frictionless Identity Protection – Allow seamless user access without causing friction by quickly identifying threats and isolating systems before exfiltrating the data.
- Risk Driven Protection – Enforce access policy to Allow/Block using MFA based on the risk level of threats detected.
- Reduced Attack Surface – Significantly reduce the attack surface available for malicious activity against both on-premises and cloud applications.
What Can SentinelOne Singularity Identity’s Conditional Access Offer?
The Singularity™ Identity solution offers deep packet inspection, identifies abnormal behavior, and detects suspicious activities. The solution detects attackers conducting reconnaissance of AD objects based on SAMR (Security Account Manager Remote), LSARPC (Local Security Authority Remote Procedure Call), and LDAP (Lightweight Directory Access) protocols.
An attacker with discovered AD objects can perform the following domain dominance attacks. The solution can detect these attacks in real-time and apply the conditional access protection policy configured for each type of attack.
- Golden Ticket
- Silver Ticket Attack
- Skeleton Key Attack
- Pass-the-ticket Attack
- Forged PAC Attack
- DCSync Attack
- DCShadow Attack
- Pass-the-hash
- Overpass-the-hash Attack
- AS-REP Roasting Attack
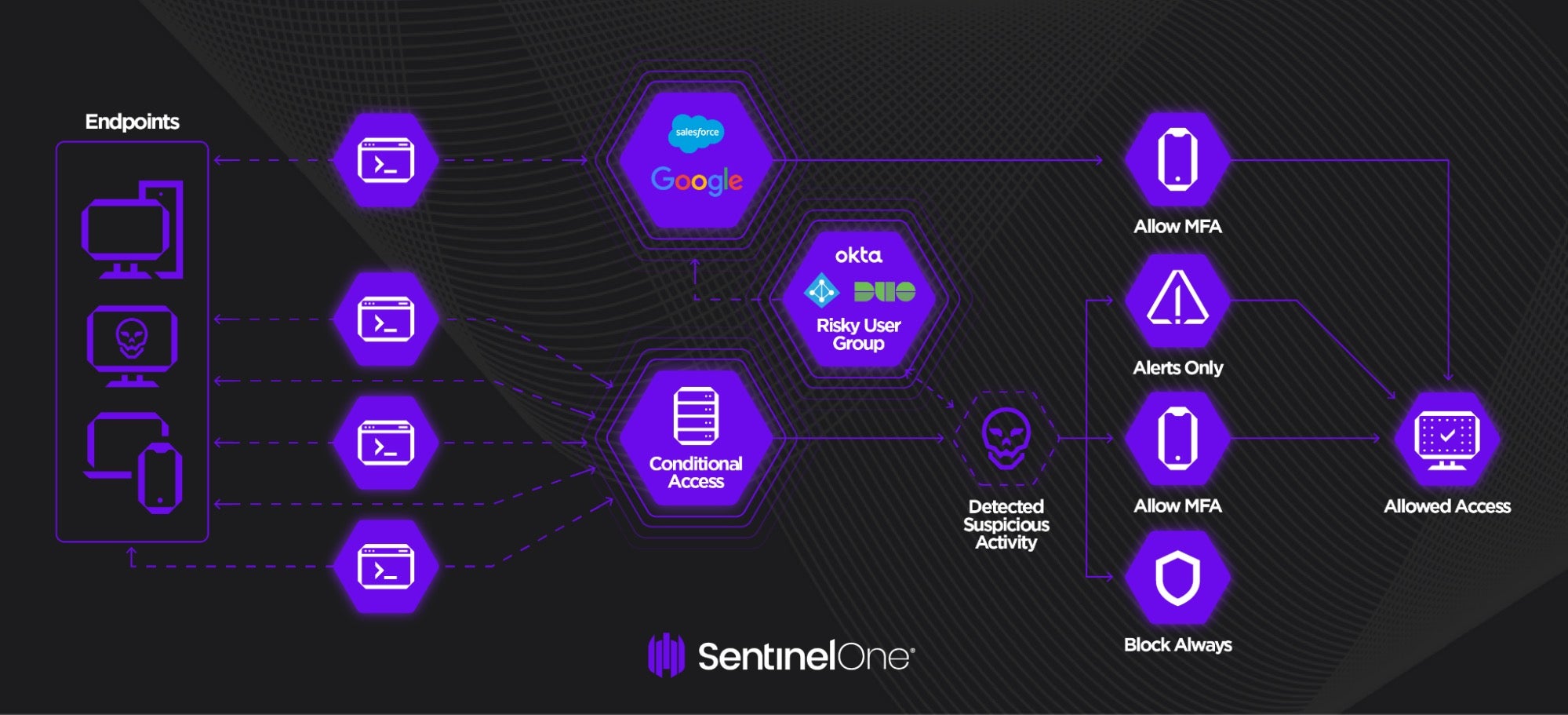
SentinelOne’s Singularity™ Identity conditional access solution also offers an extra layer of security for users accessing cloud applications. The solution enforces risk-driven policies at third-party identity providers based on suspicious activities detected. It can trigger a push notification through MFA and only allow access if approved.
For example, a condition can allow the triggering of MFA for the attack severity of the “High and Above” type. It can allow users access only after meeting certain criteria; otherwise, it blocks the risky access attempt.
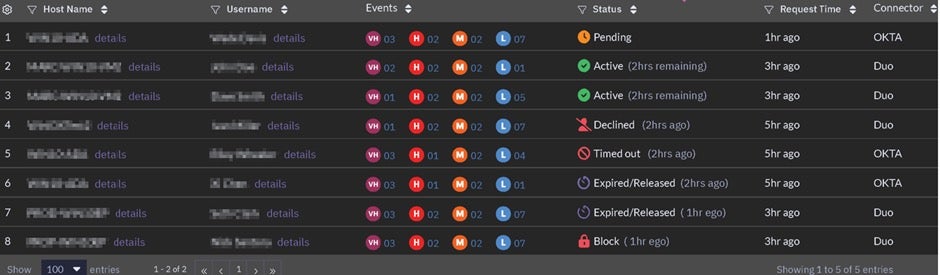
Singularity™ Identity’s conditional access capability helps improve an organization’s security posture by supporting Active Directory protection policies by offering the following response actions:
- Alert Only – Only triggers an event with suspicious details; Domain Username, IP address, AD query, API calls, etc. It is a passthrough action where user access will be permitted to on-premises or cloud applications while generating critical telemetry describing the details of the transaction for analysis.
- Allow using Multi-Factor Authentication (MFA) – Require Multi-Factor Authentication for the suspicious users detected based on threat severity.
- Add user to the risky user group – Adds the suspicious user detected in the on-premises environment to the risky user group in a connected identity provider (IdP) platform. This will require suspicious users to always go through additional authentication factors before accessing cloud applications.
- Block Always – Blocks access to on-premises applications for the suspicious users detected based on threat severity.
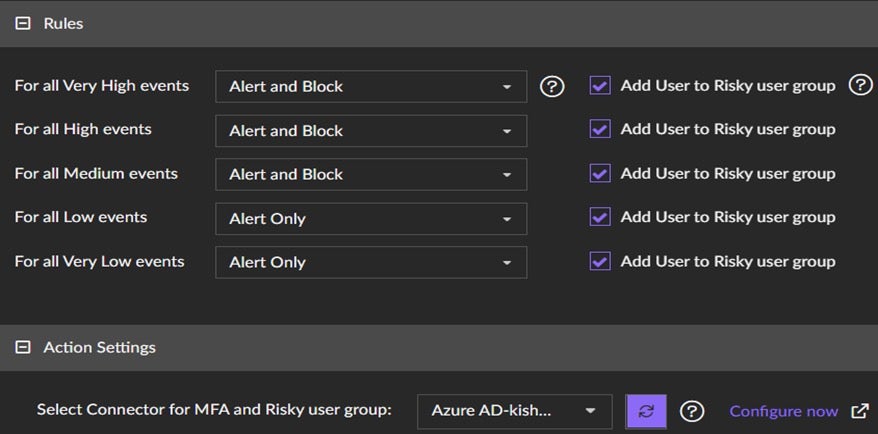
How Does Singularity Identity’s Conditional Access Protect Identities?
Attackers use discovery and reconnaissance techniques to find Active Directory objects, identify users, groups, and service accounts with elevated permissions, and perform privilege escalations. Using powerful techniques, attackers can gain unlimited access to any endpoint on the network or service, potentially damaging corporate data resources.
The Singularity Identity solution can prevent such attack techniques by leveraging conditional access requiring MFA. Only a legitimate privileged user who can successfully authenticate using MFA is allowed access. The organization must detect suspicious activities in real-time and only allow access to trusted connections. The deployed solutions must protect all on-premises applications relying on Active Directory and cloud applications integrated with the identity and MFA providers.
Conditional access offers key layers of security for both on-premises and cloud applications. Today, we’ll explore both types of conditional access.
Scenario #1: Conditional Access for On-Premises Applications
Attackers can use the AD data collected using various tools and access critical on-premises systems like Domain Controllers and application servers. If they can compromise AD by stealing credentials, moving laterally and elevating privileges, they can access any resource on the network.
An attacker can enumerate the Active Directory environment on a victim’s system using the standard built-in Windows utilities such as Net.exe, rundll32.exe, reg.exe, and wmic.exe to identify the user and group membership configuration of the system. Attackers can also use third-party open-source tools such as Adfind, Mimikatz, Cobalt Strike, Impacket, Rubeus and others, to advance their attacks.
The Singularity™ Identity solution detects these suspicious activities and blocks the user based on the threat severity. The solution can allow administrators to configure a protection policy that can trigger MFA for conditional access. The solution sends push notifications through Okta or Duo Security and allows access only after successful challenge/response.
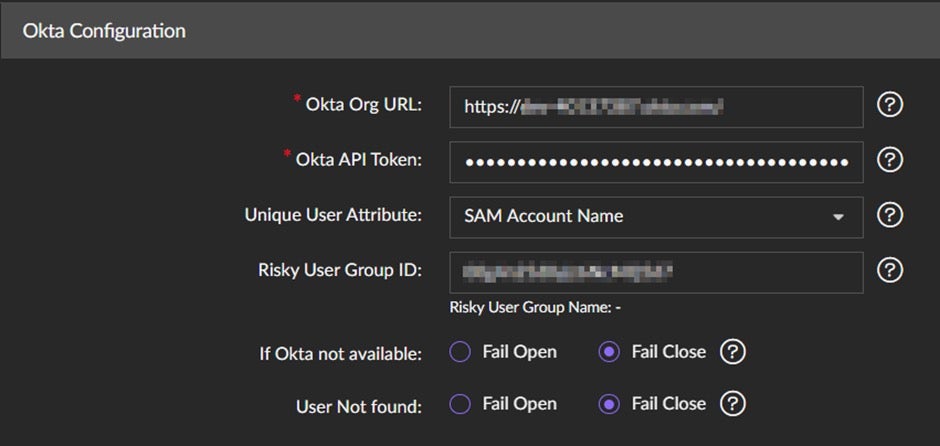
Scenario #2: Conditional Access for Cloud Applications
In this scenario, attackers with compromised identities attempt to access cloud applications such as Salesforce, Office 365, or Google Apps and perform advanced attacks. Organizations can leverage Single Sign-On (SSO) mechanisms that enable users to access multiple applications with a single login and one set of identities. They can be set up to trust a third-party IdP, such as Okta, Microsoft 365/ Azure AD, Duo Security, and similar, to authenticate users.
The conditional access solution adds the suspicious user to the risky user group in IdP once an attack is detected for that user in the on-premises environment. Users will then need to go through MFA while accessing any cloud application, thus protecting those systems and the data contained therein.
Singularity™ Identity’s conditional access solution can be deployed in the existing infrastructure and ecosystem. Additionally, the solution provides Active Directory protection against attacks originating from all devices, including Windows and non-Windows platforms such as Linux, macOS, Internet of Things (IoT), and Virtual Private Networks (VPNs).
An attacker could also bypass MFA in their journey, as noticed in the recent Cisco data breach. Attackers bypassed MFA using various techniques, including voice phishing (aka “vishing”) and MFA fatigue. Singularity™ Identity solution helps to detect such bypassing attempts and alerts on multiple failed attempts to perform a privileged operation by the same user.
Conclusion
In today’s threat landscape, organizations implementing multi-factor authentication and conditional access for identities are well-positioned to detect and block attackers’ attempts to establish identity access and domain takeover.
On top of MFA, a comprehensive identity protection program can reduce the attack surface of the corporate AD infrastructure. Such an approach will allow remediation of vulnerable exposures, detection of malicious attempts at reconnaissance, and prevention of identity-based attacks from compromising critical systems and data.
For more information, please visit Singularity™ Identity.
Get a Demo of SentinelOne's Identity Suite
Bringing Identity to XDR. Ready to experience the market’s leading identity security suite?
如有侵权请联系:admin#unsafe.sh