2022-10-28 21:0:5 Author: www.sentinelone.com(查看原文) 阅读量:21 收藏
The Good
This week, U.S. law enforcement charged a Ukrainian national for his alleged participation in an international cybercrime operation known as Raccoon Infostealer. Authorities say the MaaS (Malware-as-a-Service) infostealer has infected millions of computers worldwide.
Mark Sokolovsky, 26, is currently being held in the Netherlands and is awaiting extradition to the U.S. Sokolovsky was arrested by Dutch police after fleeing Ukraine in March, reportedly in a Porsche Cayenne.

Raccoon Stealer is advertised in cybercrime market places and offers its services to other criminals for a subscription of $200 per month. The MaaS allows users access to the malware, which they subsequently deploy on victims’ computers via cracked software and email phishing infection vectors.
After Sokolovksy’s arrest, authorities were able to temporarily take down the infrastructure supporting Raccoon Stealer and identified over 50 million unique credentials including bank accounts, cryptocurrency addresses, credit card numbers and other forms of identification stolen by the operators, many of which belong to U.S. citizens. The FBI has set up a website for any individuals wishing to check if their email address appears in the cache of stolen data.
If found guilty, Sokolovsky, who allegedly used various online nicknames including Photix, raccoonstealer and black21jack77777, faces a maximum penalty of 20 years in prison for wire fraud and money laundering.
Unfortunately, despite Sokolovsky’s arrest and the subsequent dismantling of Raccoon Stealer infrastructure, other members of the gang remain undeterred and have since stood up a new version of the infostealer, continuing to promote it in underground cybercrime forums. The FBI, the Department of Army Criminal Investigation Division (Army CID) and other law enforcement agencies continue to investigate the case.
The Bad
Vice Society, a threat actor group which has been disproportionately targeting the U.S. education sector, continues to be a mounting concern as the threat actor adopts multiple extortion techniques.
A report this week details the TTPs used by this threat actor as it continues its campaigns against school and colleges. The group variously deploys BlackCat, HelloKitty, QuantumLocker and custom versions of Zeppelin ransomware. In some intrusions, Vice Society demands a ransom without deploying ransomware, instead threatening victims with exposure of the leaked data.

As described in a recent report authored by SentinelLabs researchers, data extortion has now evolved into a spectrum of TTPs; Vice Society is just the latest example of a threat actor occupying a fluid position across that spectrum, adapting their approach according to the target.
The researchers note how Vice Society switches between deploying RaaS payloads such as BlackCat to “wholly-owned malware” like Zeppelin and even their own custom variants in different intrusions. In one intrusion, the operators exfiltrated hundreds of gigabytes of data by staging a malicious PowerShell script on a network share.
The threat actors abuse registry commands to disable Windows Defender and often prefer comsvcs.dll and MiniDump over Mimikatz for credential dumping. Vice Society has also been observed exploiting PrintNightmare to elevate privileges in a domain.
Security teams working in the education sector are urged to review Vice Society TTPs as well as bolster their cyber defenses more generally by deploying a robust EDR, reviewing regularly exploited vulnerabilities, and using device discovery to find unmanaged devices on the network.
The Ugly
This week, hacktivists have been busy causing disruption, dismay and offense in two unrelated intrusions. On Thursday, the New York Post reported that it had been the victim of a hack which took over its website and Twitter account. The attackers used their unauthorized access to post offensive content relating to various U.S. politicians, including President Biden and New York Rep. Alexandria Ocasio-Cortez.
The New York Post has been hacked. We are currently investigating the cause.
— New York Post (@nypost) October 27, 2022
Details of the attack so far remain sparse, but it’s not the first time New York Post’s owner, News Corp, has been targeted. A breach in January 2022 was speculatively attributed to a Chinese-linked APT, though it remains unclear at this time whether the cases are connected.
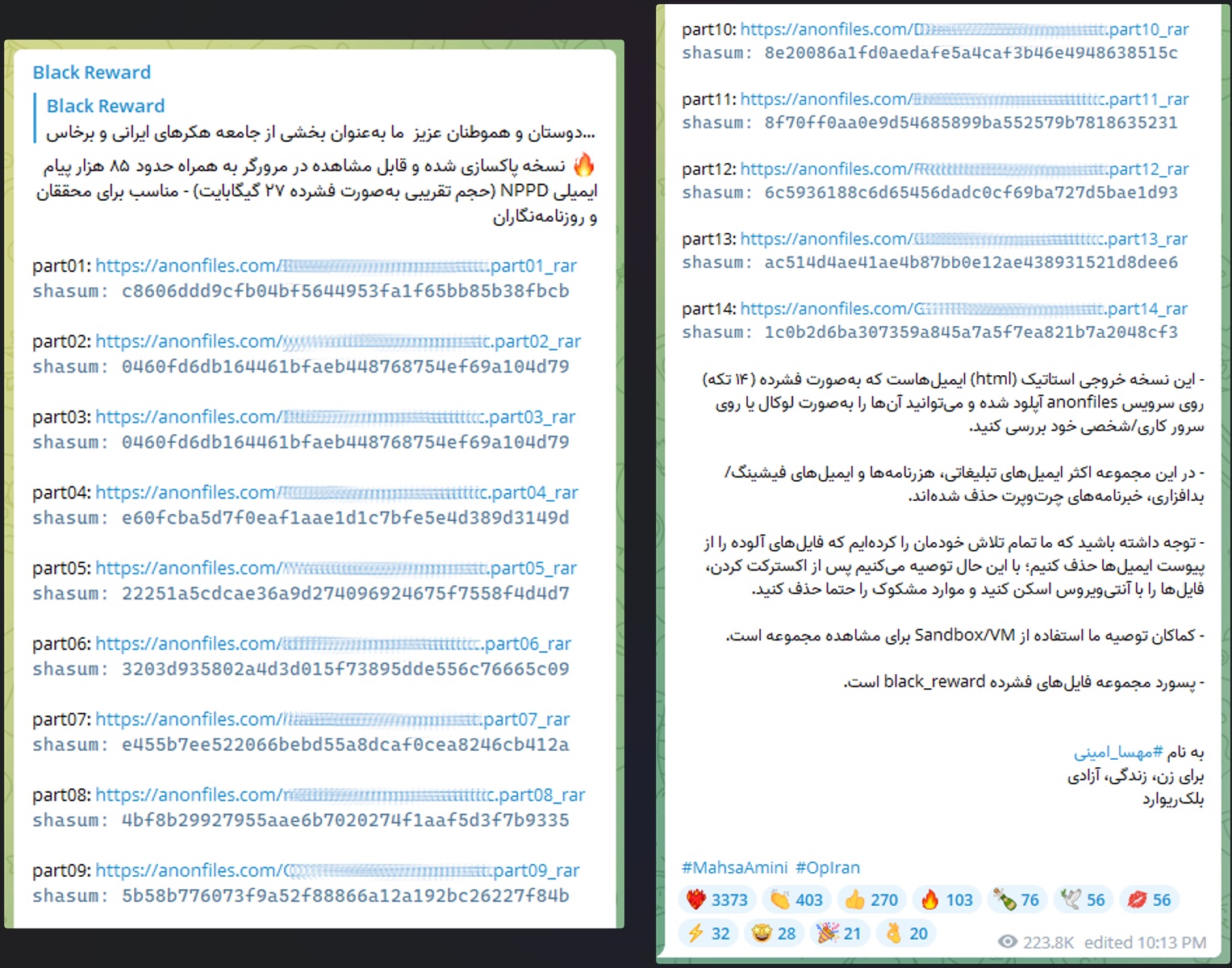
The Iranian Atomic Energy Organization (AEOI) is also investigating a breach apparently in support of the recent nationwide protests following the death of Mehsa Amini in police custody. A hacktivist group calling itself ‘Black Reward’ has leaked 85000 sensitive email messages stolen from servers belonging to one of the AEOI’s subsidiaries. The group says the leaked content contains details of passports and visas of Iranians and Russian nationals who work with the AEIO, as well as contracts, power plant status and technical reports.

Iranian authorities, meanwhile, say that the attackers were from “a specific foreign country” and the purpose was “to attract public attention, create media atmospheres, and psychological operations”, implying that Black Reward is less of a real hacktivist group and more of a state-sponsored knock-off. We’ll have to await further details to emerge before that becomes clear.
如有侵权请联系:admin#unsafe.sh