All software has bugs — but some bugs can lead to serious security vulnerabilities that can impact your website and traffic. Vulnerabilities can be especially dangerous when your software is running over the web, since anyone can reach out and try to attack it. That’s why keeping your website up-to-date with the latest patches and security updates is so important.
The reality is there is no shortage of websites running outdated WordPress, Joomla, or Magento software. There are also plenty of websites using plugins, themes and other extensible components with known vulnerabilities — all of which give attackers the opportunity to exploit and infect a website or harvest sensitive customer information.
The #1 excuse we hear from our clients for keeping these web applications outdated is that their websites will break.
Common justifications for not patching or updating website software include:
- “My theme was heavily modified, so I can’t update it.”
- “I’m afraid it will break some functionality if I update this plugin.”
- “I modified some of my core files so now I’m stuck.”
- “My web developer left us and nobody knows how this piece of code works.”
If you are in a situation where you can’t update your website software, then lists of CVE’s and known plugin vulnerabilities probably scare you. But in this post, we’ll highlight some ways you can mitigate risk and virtually patch known vulnerabilities on your site.
Contents:
- What is virtual patching?
- What happens to unpatched websites?
- How does virtual patching work?
- What’s an example of virtual patching?
- Virtual patching solutions
- Key takeaways about patching software vulnerabilities
What is virtual patching?
According to OWASP, virtual patching is defined as:
A security policy enforcement layer which prevents the exploitation of a known vulnerability.
The virtual patch works since the security enforcement layer analyzes transactions and intercepts attacks in transit. This means malicious traffic never reaches the web application. The resulting impact of virtual patch is that, while the actual source code of the application itself has not been modified, the exploitation attempt does not succeed.
Virtual patching helps websites that are outdated (or contain known vulnerabilities) to be protected from attacks by preventing exploitation of vulnerabilities on the fly. It basically fills the security hole until you have time to patch. This is usually done with a web application firewall.
What happens to unpatched websites?
When a website contains unpatched security vulnerabilities, it can put not only your website but also your visitors and customer data at risk.
As seen in our latest report, automated attacks targeting known software vulnerabilities are one of the leading causes of compromise and infection. Bad actors regularly scan websites big and small for any known vulnerabilities. They often use automated scripts to help identify targets and exploit vulnerable websites.
Some attacks rely on a single access point to inject malicious content into the vulnerable environment. But privilege escalation can also occur — and once a foothold has been established, the attacker can then deploy other tools which can lead to a full website takeover, stolen data, website backdoors, SEO spam, phishing, and other malware.
Another recent report by Ivanti revealed that unpatched vulnerabilities are one of the most prominent attack vectors actively exploited by ransomware groups. Furthermore, thirty-seven percent of these vulnerabilities were actively and repeatedly exploited by bad actors. This data clearly highlights the importance of patching your website to protect against the threat of distributing ransomware.
How does virtual patching work?
When a website patches their software, they upgrade it to the latest most secure version — and in the process, patch any security issues and known vulnerabilities.
But when a site isn’t able to patch in time, virtual patching can help close these security “holes” through the use of a web application firewall or intrusion detection system. These services employ security policies or rules that focus on preventing exploits and vulnerabilities at the network level before they reach your website.
Virtual patching can help address the following scenarios:
- Prevents the risk of attacks against known website vulnerabilities in core CMS, plugins, themes and other extensible software.
- Removes the risk of software conflicts since website code is not changed.
- Prevents downtime and financial losses due to a website being taken offline from malware.
- Reduces the risk of sensitive data exposure.
- Reduces cost of time or money spent to patch during an emergency.
- Mitigates risk of impact to your website’s reputation.
Virtual patching is especially crucial for securing your website, customer data and purchase process. In the event that your website software contains a vulnerability, you’ll have ample time to update and patch your components to protect your traffic and revenue
What’s an example of virtual patching?
One common example of virtual patching employed by our firewall is preventing known exploits. As attackers launch large-scale attacks against severe vulnerabilities, security companies deploy rules to prevent these exploits from working. This ensures the website is not impacted by the attack.
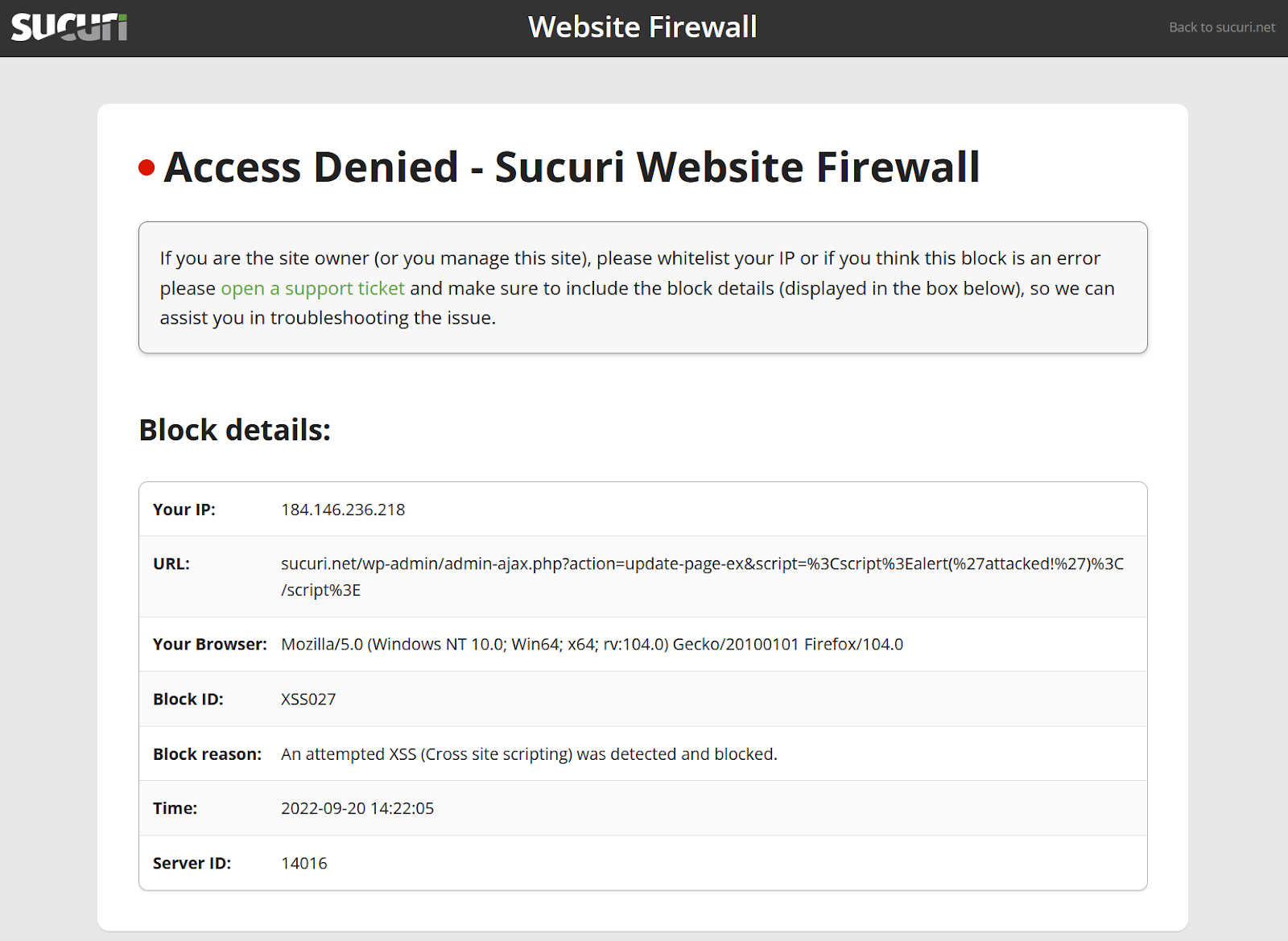
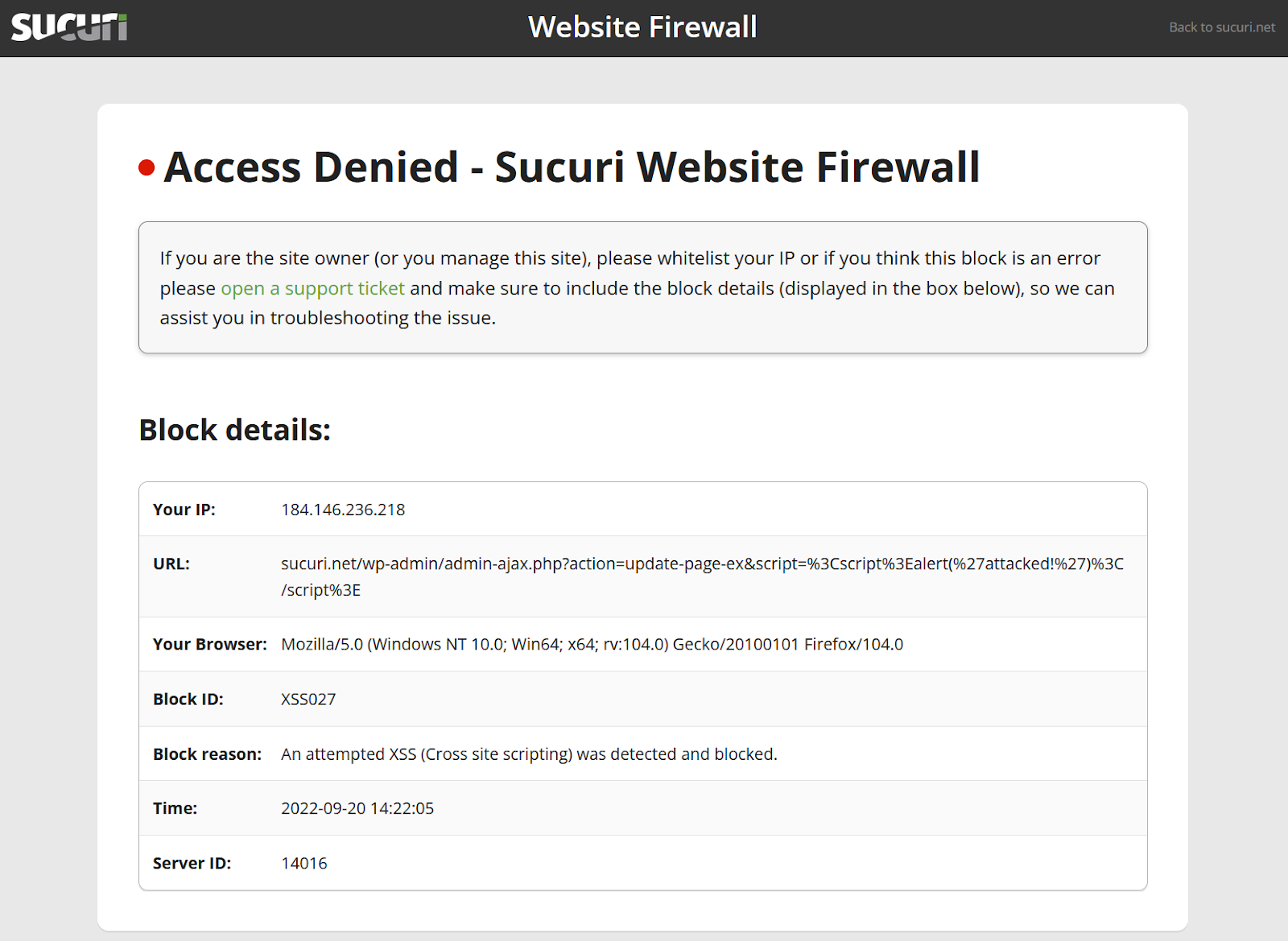
When an attacker tries to send a malicious request to a website, the firewall blocks the request. This prevents it from reaching and damaging the website.
Virtual patching solutions
To assist our customers with proactive security measures, we’ve built our Web Application Firewall (WAF) plus Intrusion Detection System (IDS) — the Sucuri Firewall. It’s an in-the-middle proxy that sits between your websites and the internet allowing us to filter and block attacks before they reach your websites.
Our Firewall patches known vulnerabilities and adds multiple layers of hardening/prevention, along with log analysis to prevent websites from being hacked, infected with malware, or reinfected.
Here are a few of the features you’ll find in the Sucuri Firewall:
- Virtual patching
- Traffic filtering to block malicious requests
- WAF (web application firewall) to prevent SQL injections, XSS, RFI, CSRF and other vulnerabilities
- IDS/IPS (intrusion detection/prevention system)
- Extended access Control (whitelisting of IP’s allowed to access administrative pages)
- OSSEC HIDS integration (full log analysis and traffic monitoring)
- Improved performance and caching
- Fully managed cloud solution
Key takeaways about patching software vulnerabilities:
- Vulnerabilities can lead to website malware and compromised customer information.
- It’s essential to patch website software as soon as possible. However, this is not always possible unless the website leverages virtual patching.
- Virtual patching makes it easy to temporarily prevent hackers from exploiting known software vulnerabilities until a patch is properly applied to the software.