2022-4-12 00:44:51 Author: www.sentinelone.com(查看原文) 阅读量:19 收藏
A Guest post by Jamie Cowper, VP of Marketing, Noetic Cyber
As Gartner identified in their recent report on the ‘Top Trends in Cybersecurity 2022’, organizations need to protect an ‘ever-expanding digital footprint.’ The report points out that a ‘dramatic increase in attack surface is emerging from changes in the use of digital systems…’.
This expanding attack surface reflects many changes in how we have adopted and use technology, including the continuing shift to cloud services, use of SaaS applications, and a hybrid workforce. All these factors are expected to continue to grow and mean that security teams need to adapt to address external and internal coverage gaps.
A fundamental challenge for security teams here is understanding what they need to protect. Asset management for cybersecurity, or as Gartner refers to it, Cyber Asset Attack Surface Management (CAASM), has evolved to address the problem faced by security. To understand and mitigate their attack surface, they need to understand what assets they have and their current security posture.
This is not a problem of insufficient security data. The reality is that security has enough tools, but the insights they need are fragmented and siloed across different security, DevOps, and IT management systems, and currently hard to access. As a result, 71% of global IT leaders admit to finding new endpoints in their environment on a weekly basis. Noetic Cyber’s partnership with SentinelOne is intended to address this problem.

XDR and CAASM Deliver Integrated Cyber Asset Detection, Inventory, and Remediation
The integration of SentinelOne Singularity XDR and the Noetic Continuous Cyber Asset and Controls platform enables security teams to extend the visibility, detection, and endpoint insights of SentinelOne into a wider asset inventory and management architecture, maximizing the value of their investment in SentinelOne and other security tools.
To build a complete coverage map of all cyber assets in an organization, across cloud and on-premises, the Noetic platform leverages high-value data from existing security and IT management tools, which each have their own perspective on cyber posture, network access, and business criticality. SentinelOne’s endpoint, cloud telemetry, and incident data are high-fidelity sources of data that help security teams understand security coverage gaps and system misconfigurations.
By integrating the SentinelOne data with information from other systems, such as Configuration Management Databases (CMDB), Vulnerability Management (VM), and Identity & Access Management (IAM), Noetic can provide security teams with a correlated, aggregated visualization of all cyber assets in the organization, and more importantly, the cyber relationships between them which help prioritize critical security coverage gaps based on risk and business criticality.
How It Works
The Noetic Connector for SentinelOne is an agentless integration that uses the OpenAPI spec to create a bi-directional link between the two platforms. Noetic customers simply enable the connector in their platform, provide it with API credentials and perform an initial configuration. The Noetic connector will then ingest relevant information from SentinelOne, looking for information indicating new, updated, or removed assets. This information is aggregated and correlated with information from various other data sources into a graph database in Noetic and updated regularly.
At this point, we have an incredibly rich source of security insights instantly available to security teams to query, but the connector also contains more pre-packaged capabilities to deliver immediate value.
Common security use cases, resources, and dashboards are included in the integration, so security teams can quickly understand and remediate them.
The Noetic connector for SentinelOne is bi-directional, which is critical, as Noetic has a highly flexible automation and workflow engine as part of the platform, so as Noetic and SentinelOne uncover security problems, the necessary remediation can be identified and automated for ongoing purposes.
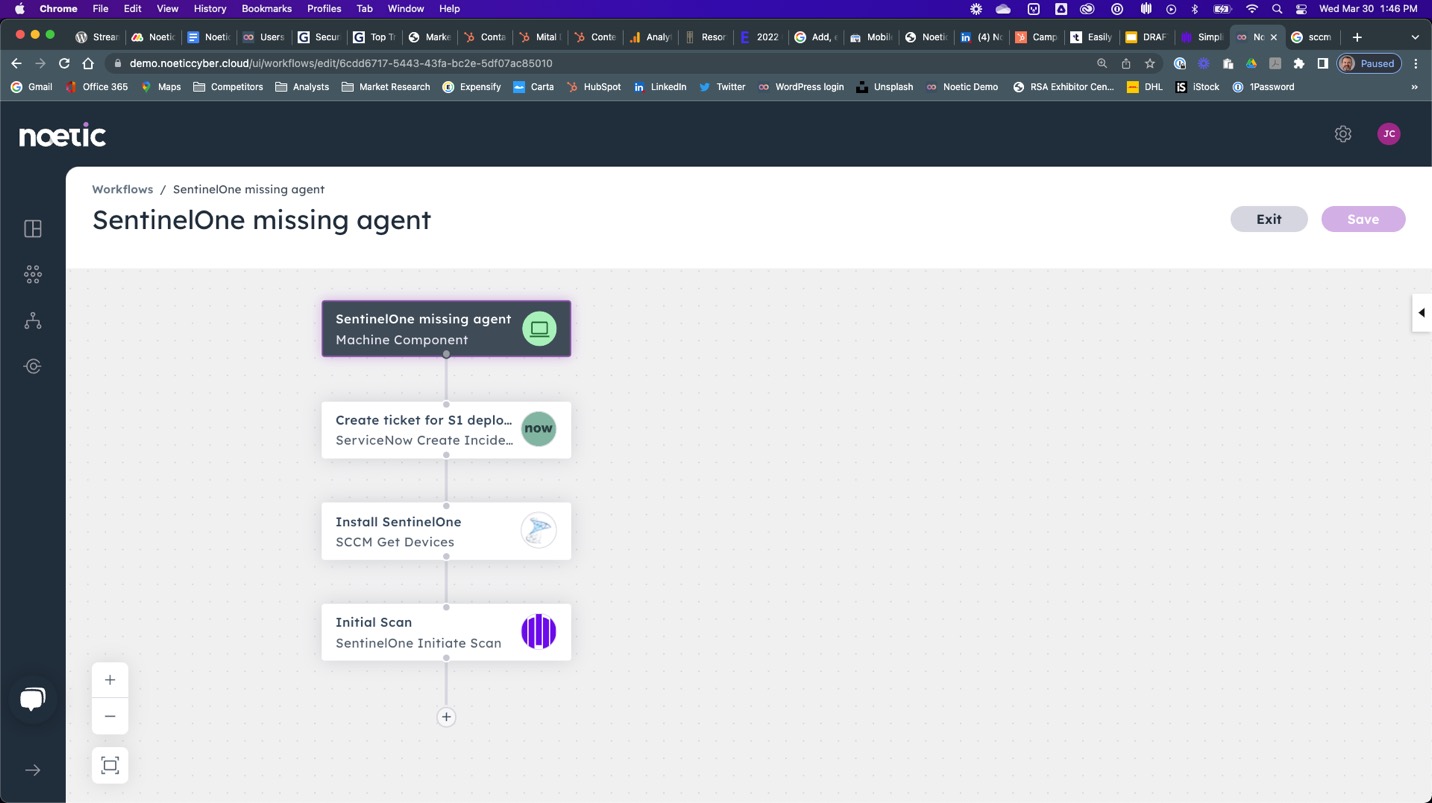
Common Use Case | Missing Endpoint Security Agents
Organizations will typically have a policy that SentinelOne must be installed on all virtual or physical machines, but in the real world, machines can be deployed without the correct security policies. The challenge for SentinelOne, as with any security tool, is to understand where this is happening.
The Noetic platform has an abstract model where we have standard security concepts, one of those is ‘machine’, so that when it ingests information from SentinelOne, AWS, Microsoft Active Directory, ServiceNow, or any other technology, we are identifying and correlating different perspectives of the same machine based on the information we receive.
A simple, repeatable task in Noetic is therefore to run the query ‘All Machines without EDR’, this will present us with a list of all machines identified within other tools, but not known to SentinelOne.

This query can be automated to run on a weekly, daily, or hourly basis to continuously uncover rogue machines without the SentinelOne agent deployed. It can also be modified to identify misconfigured or outdated versions of the SentinelOne agent.
Once Noetic identifies machines missing the required agent, it is a simple automated workflow to trigger their enrolment, either via the SentinelOne console or through a systems management software like Microsoft SCCM or AWS SSM.

For organizations with large numbers of unprotected machines, Noetic can also help with workload prioritization. If there are hundreds or even thousands of missing endpoint agents, then it may not be practical to roll out the software immediately. By understanding other cyber factors associated with the machines – what sensitive information they may have access to, the presence of any unpatched critical vulnerabilities, etc., security can then align with the IT organization to focus on a prioritized software roll-out program to minimize the risk to the business.
Parting Thoughts
The partnership between SentinelOne and Noetic is designed to help improve the cybersecurity posture for our customers. These initial use cases are the first step in leveraging SentinelOne’s extensive cloud, endpoint, network, and vulnerability data as a high-fidelity ‘source of truth’ to feed into the wider cybersecurity model.
Noetic’s bi-directional connector allows security teams to quickly take advantage of existing workflows and remediation processes that are already defined and active within their SentinelOne deployment and extend them to new cybersecurity use cases, improving cyber hygiene and reducing risk. To learn more about SentinelOne and Noetic Cyber, attend the upcoming webinar or read the joint solution brief.
如有侵权请联系:admin#unsafe.sh