One of the more common infections that we see are site-wide redirects to spam and scam sites, achieved by attackers exploiting newly found vulnerabilities in popular WordPress plugins. If you’ve ever been redirected to a page that looks something like this, then you’ve fallen victim to such an attack:
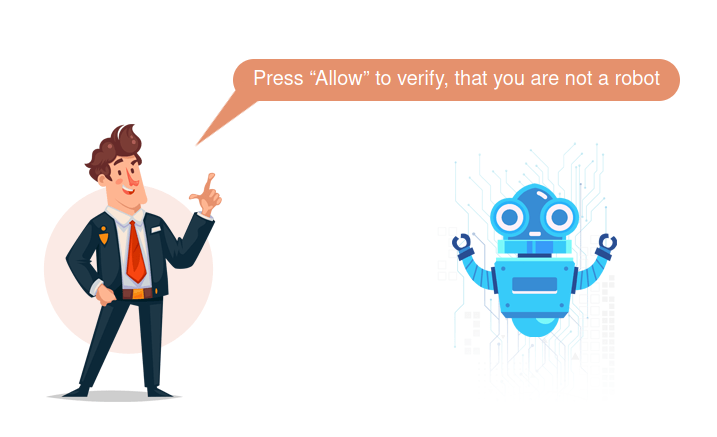
Once the user clicks through the verification process they are sent to a fake CAPTCHA page asking the user to click to prove they are a human:
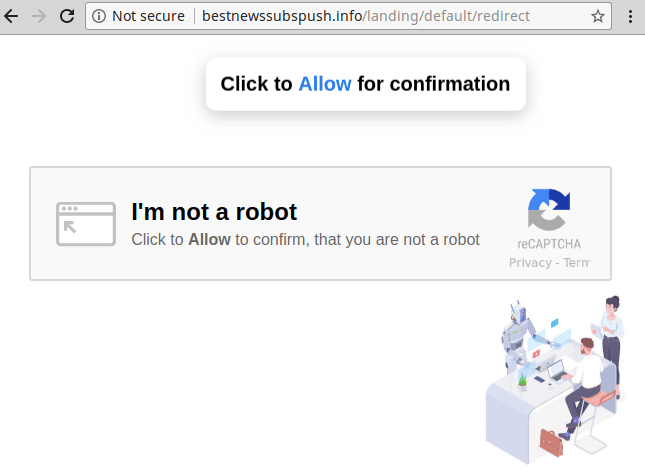
As we have reported in the past on this type of infection:
The goal is to trick visitors into clicking “Allow” when the site asks to subscribe to push notifications. Once the call-to-action has been clicked, the spammers are able to send spam ads to the visitors’ desktops whenever they want — even if the user closes the website and never visits it again.
Other variations of this infection that we have seen previously redirect the victims to fake tech support scams, spam, or any other destination of the attackers’ choosing.
How does the redirect work?
Many vulnerabilities, if left unpatched, can allow attackers to change database values within websites without any authentication. A common infection tactic is to simply change the wp_options values for siteurl and home to a malicious domain, or to inject the wp_posts table entries with malicious JavaScript. These wp_options values are what you see when you first configure your WordPress website:
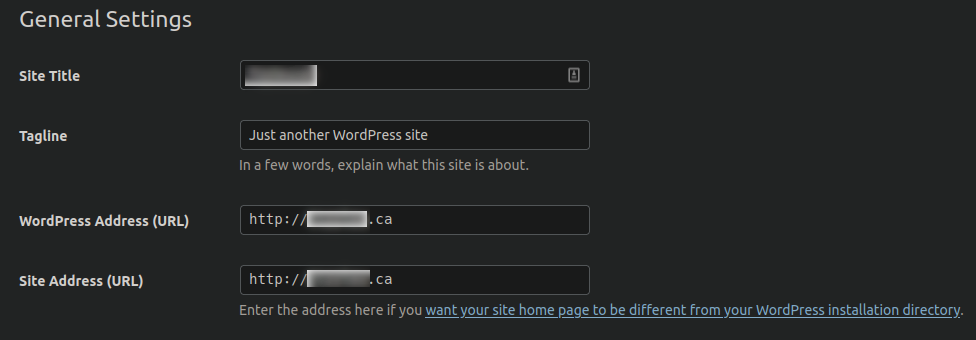
If these values are changed to a different domain then all traffic going to the website gets redirected to that destination. Quite often with these infections the attackers will also leave behind a malicious admin user, so if you’re picking up the pieces after such an attack be sure to check your list of administrators on your website.
In today’s post we are going to review some of the common themes behind these scammy redirects and some trends that we’ve noticed while documenting them in recent years.
Defining Some Key Terms
Before we continue, it’s worth explaining a couple of key concepts here: namely, top-level domains (TLD) and “bulletproof” hosting. The former is the highest level in the domain name system. So, .com is a different top-level domain than .net, or .org and so on. Different top-level domains tend to serve different purposes: .com tends to be for commercial purposes, .net for networks, .org for organisations, and so on.
Top-level domains are also set aside for different countries and geographical regions. Canada’s top-level domain is .ca, South Africa’s is .za, and Brazil’s is .br. The overarching organisation that administers and oversees pretty much all of them is known as ICANN. However, as we’ll get into later, different country’s top-level domains will have slightly different regional administrative rules. For example, in Canada, you must be a Canadian citizen or Permanent Resident in order to register a .ca domain.
“Bulletproof” Hosting
The next concept we’ll need to go over here is that of “bulletproof hosting”. When attackers register a domain or host malicious content it is of course liable to be taken down by the hosting provider or domain registrar. This is of course because malware runs afoul of a litany of laws and regulations, and their hosting provider could find themselves liable for being associated with such activities. This is why hosting providers and domain registrars have Abuse departments, so that they can deal with complaints from the public when websites or domains using their service are breaking laws or engaging in malicious activity.
Enter: Bulletproof hosting. Malware and spam are actually quite huge, black market economies, and there can be a lot of money to be made by those with flexible morals. Malicious domains and content need to be hosted somewhere, and over the years certain players have emerged on the web to cater to exactly these folks.
These hosts and domain registrars tout anonymity, lack of accountability, deference to DMCA takedowns/copyright as well as protection from the American legal system as features of their services. They are often touted as being hosted “offshore”, helping to distance the malicious actor from their payload, and obscuring the legal accountability across multiple, international jurisdictions.
If a potential customer is willing to pay a premium for their service, they can host whatever content they want in a more “secure” way.
Common Trends in Abusive Domains
Let’s bring this all back to the malicious redirects that we were discussing earlier.
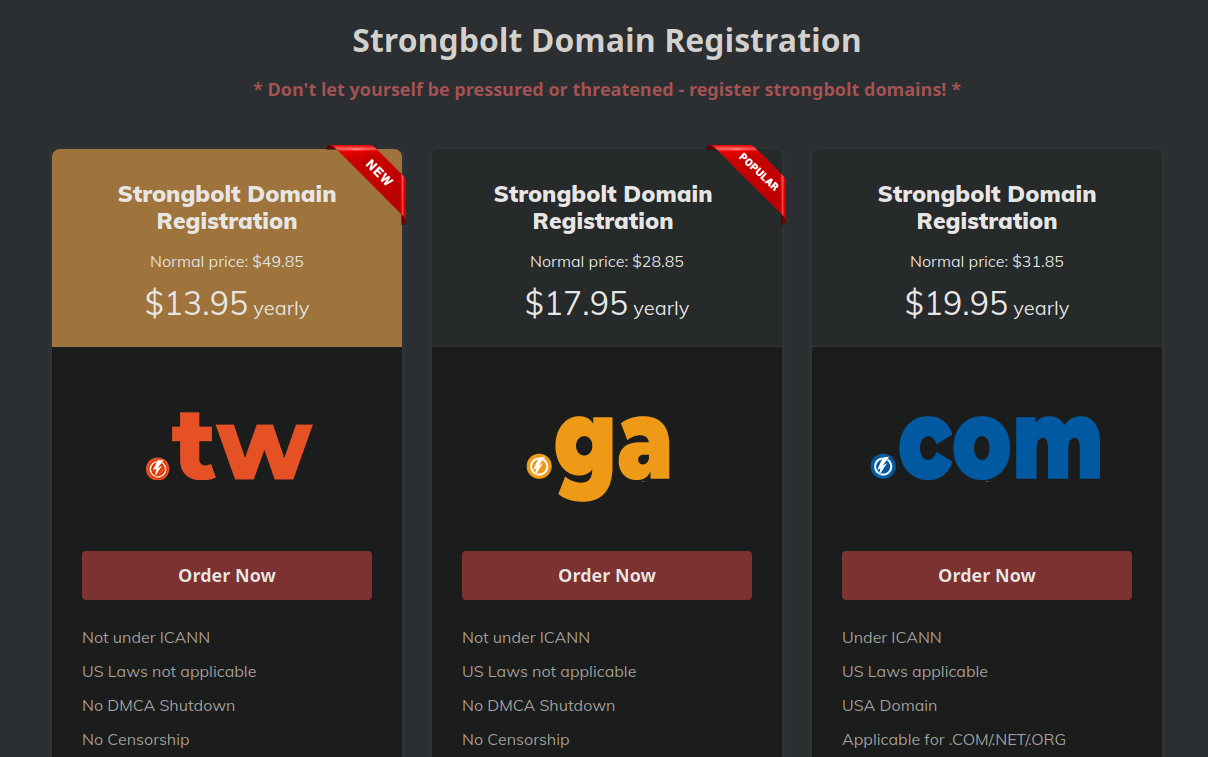
One trend that has been unmistakable in the malicious redirects that we’ve seen over the past year or so has been a gradual shift to certain top level domains used in the attacks. Most often in years past, the ubiquitous .com has been ever present, as well as the occasional .ru (Russia) or .su (Soviet Union) domain. However, .com – being the most well-known and properly regulated top-level domain, can cause issues for malicious actors. These also tend to be comparatively expensive to register, whereas other, less common top level domains have promotions where you can acquire them for cheap or sometimes even for free.
Since 2020 there has been an unmistakable shift towards a small handful of top level domains that were not used as much before: .ga (Gabon) and .tw (Taiwan). In checking the most common blocked domains where websites redirect to we start to see .ga domains start to appear in the last half of 2020:
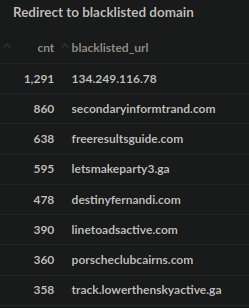
Q3-4 2020 Top Blacklisted Resources detected by Sucuri SiteCheck
Previous to this period it was rare to see these types of domains show up in malicious redirect campaigns.
Taking the full data from the most commonly identified redirects for the year 2021, we see the trend continuing:
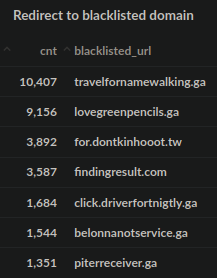
2021 Top Redirects to Blocked Domains
Interestingly, this timeline pairs nicely with a piece of research done by security company RiskIQ, who performed a thorough investigation into one such “bulletproof” hosting provider located in Malaysia. While the domain registration page on their website has since been removed, in checking the web archive we can see that they were touting these exact top-level domains being pushed as part of their registration services:
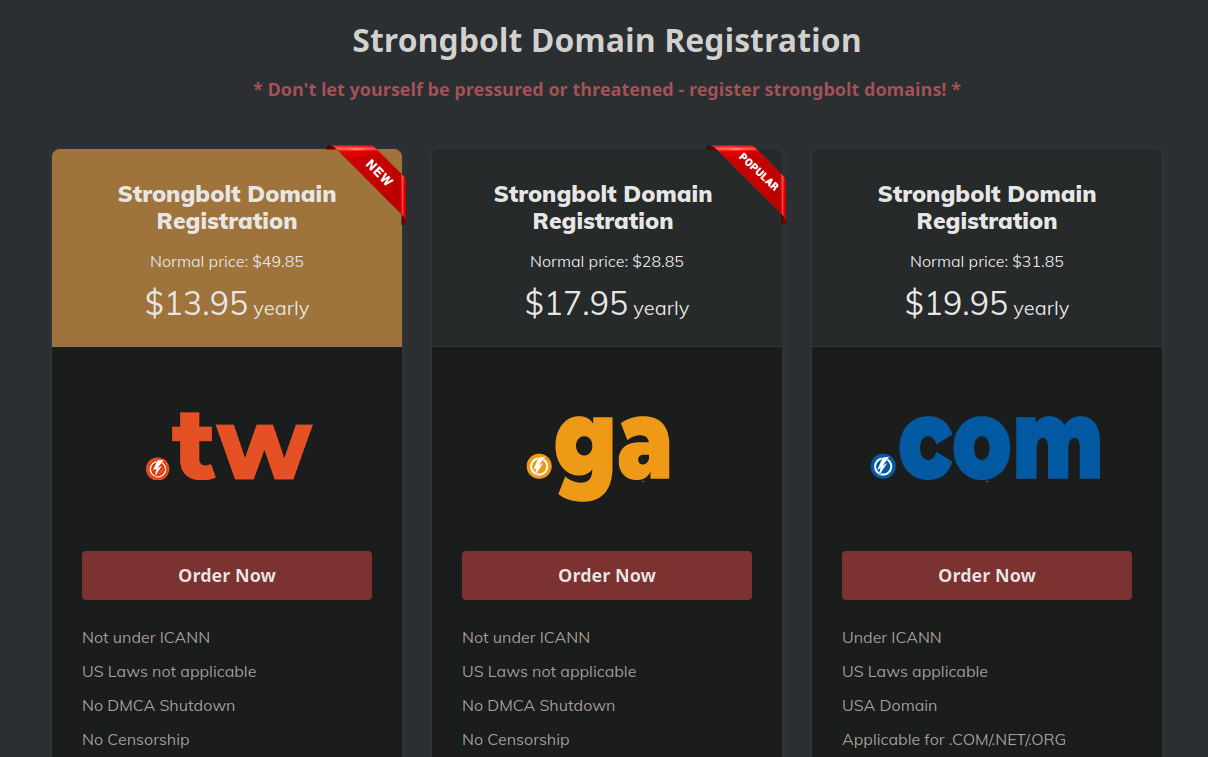
Notice the following marketing points:
- Not under ICANN
- US laws not applicable
- No DMCA shutdown
- No censorship
Unsurprisingly, the host hides behind the fig leaf of being “pro free-speech” and “anti-censorship” to mask their true intentions.
Going back further in the web archive and checking their domain registration page, we can see that roughly around this time (late 2020) is when prices dropped significantly for such domains. In years prior, similar domains would cost double that or more, reflected in the “Normal Price” in the screen capture.
The My GA domain registry website reports some details about .ga domains specifically, which indicates one reason why they’ve gained in popularity by attackers:
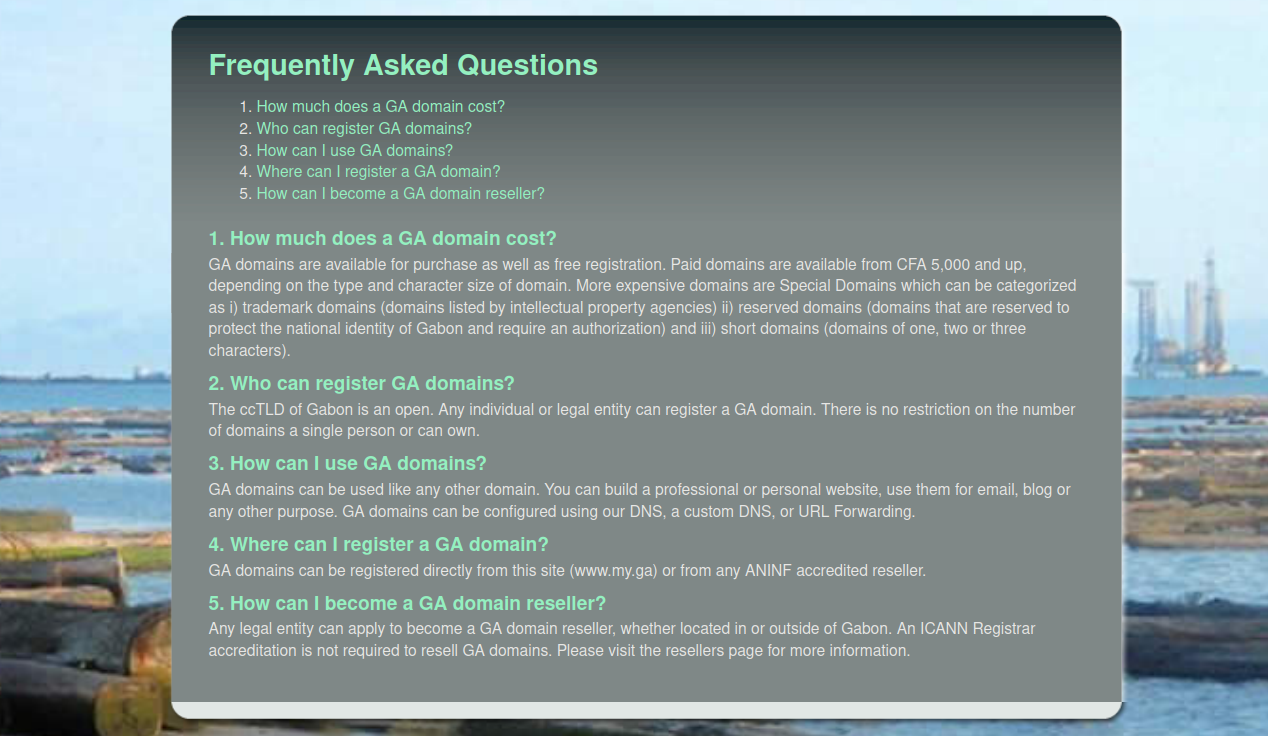
- Who can register GA domains?
The ccTLD of Gabon is an open. Any individual or legal entity can register a GA domain. There is no restriction on the number of domains a single person or can own.
Similarly, very few (if any) restrictions apply for .tw domains. It is not necessary to have any local presence, citizenship or administrative contact within Taiwan to register such domains.
The low price of the domains coupled with non-existent ownership restrictions seem to be making these a lucrative resource for attackers who want quick and cheap access to fresh domains to use in redirect campaigns.
Whether or not the specific aforementioned host was related to such redirect domains we can’t say for sure since many of the malicious redirect domains use anonymous DNS proxies. There are certainly other such registrars selling these domains, with similar promises of anonymity:
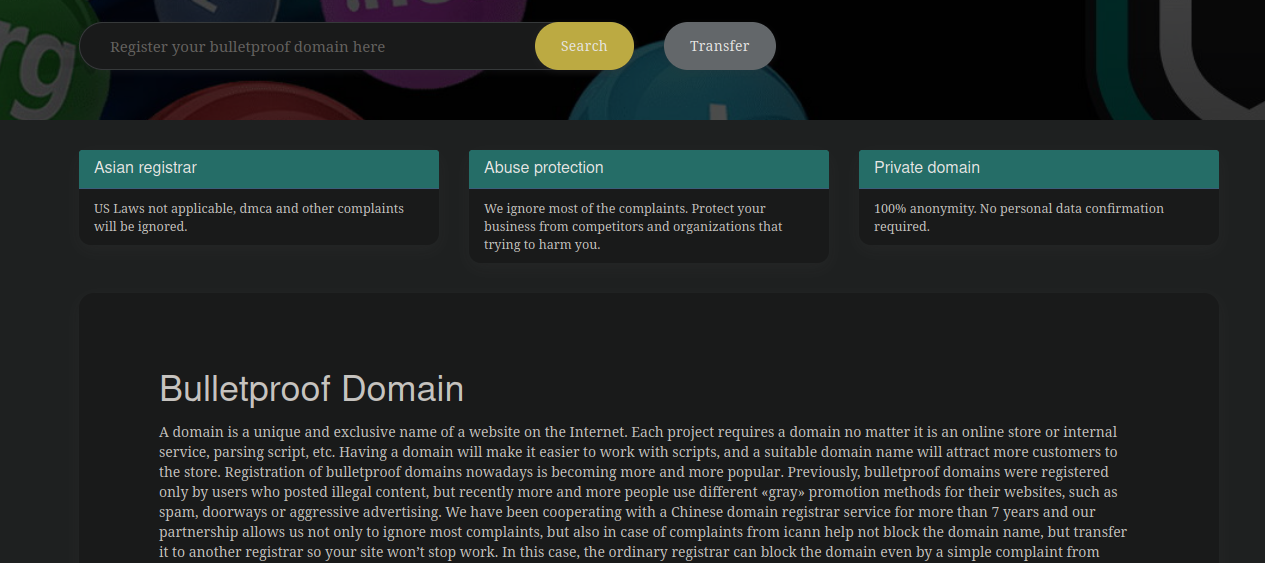
What is certain, though, is that the lack of regulatory authority over certain TLDs make them an asset for the attackers.
Common Trends in Hosting
The attackers are also repeatedly using the same hosting networks to host their payloads, most notably the Swiss NICEIT network:
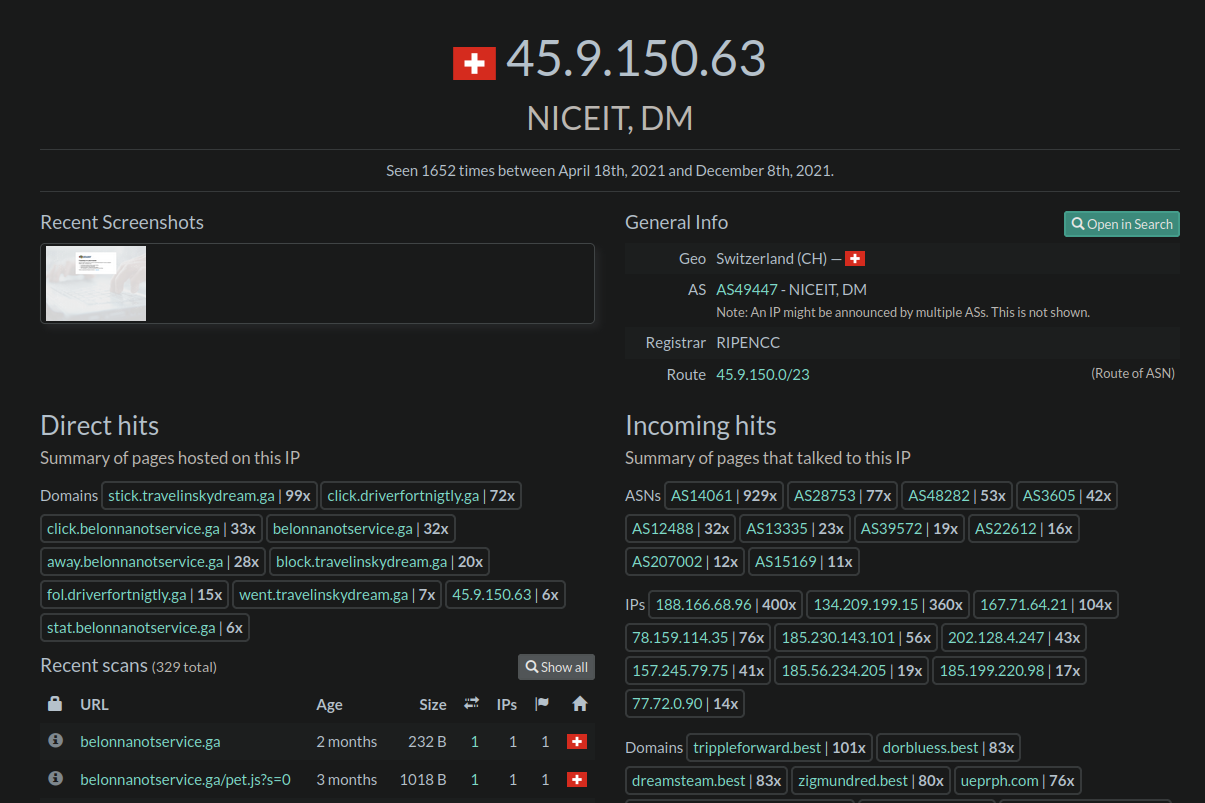
The last three major redirect campaigns that we have been monitoring have all been using this hosting network to host their malicious payload:
https://urlscan.io/ip/45.9.150.78 https://urlscan.io/ip/45.9.150.63 https://urlscan.io/ip/45.9.150.64
With one outlier using OVH hosting (likely an unknowing reseller)
https://urlscan.io/ip/51.89.92.108
We have seen Switzerland pop up quite a bit as a popular location for the attackers. At first glance it seems an odd choice, but they have one of the most robust data privacy regulatory frameworks in the world. That would be an attractive selling point for anybody with an interest in concealing their identity, whether they are up to no good or not.
In Conclusion
What is clear, here, is that for whatever reason, be it a lack of regulatory authority or action over these top level domains, a drop in overall price for them, or questionable domain registrars aggressively selling them while simultaneously promising anonymity, it’s clear that there has been a drastic shift towards them in redirect campaigns in the last period.
We will continue to keep an eye and document these cases of malicious redirects targeting vulnerable plugins. If you are a website owner and want to keep your website protected against such attacks, check out our guide on WordPress hardening or consider placing your website behind our firewall service.