
2020-10-20 - Hancitor infection with something and Cobalt Strike
2020-10-20 - HANCITOR WITH SOMETHING AND COBALT STRIKEASSOCIATED FILES:2020-10-20-Hancitor-IO 2020-10-22 10:57:00 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:229 收藏
2020-10-20 - HANCITOR WITH SOMETHING AND COBALT STRIKEASSOCIATED FILES:2020-10-20-Hancitor-IO 2020-10-22 10:57:00 Author: www.malware-traffic-analysis.net(查看原文) 阅读量:229 收藏
2020-10-20 - HANCITOR WITH SOMETHING AND COBALT STRIKE
ASSOCIATED FILES:
- 2020-10-20-Hancitor-IOCs.txt.zip 2.6 kB (2,574 bytes)
- 2020-10-20-Hancitor-malspam-9-examples.zip 19 kB (19,006 bytes)
- 2020-10-20-Hancitor-infection-traffic.pcap.zip 4.4 MB (4,444,385 bytes)
- 2020-10-20-Hancitor-and-follow-up-malware.zip 760 kB (759,603 bytes)
NOTES:
- All zip archives on this site are password-protected with the standard password. If you don't know it, see the "about" page of this website.
IMAGES
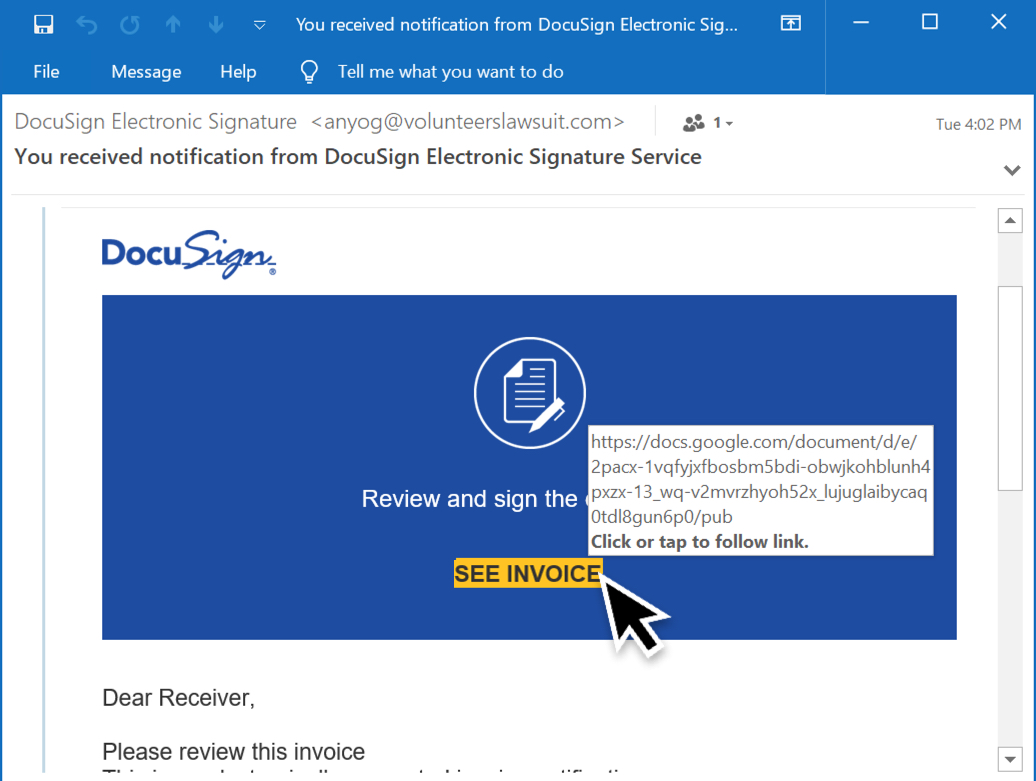
Shown above: Screen shot from an example of malspam pushing Hancitor.

Shown above: Screenshot from one of the Google Docs pages leading to the spreadsheet.

Shown above: Screenshot from one of the Excel files downloaded through the Google Docs pages.
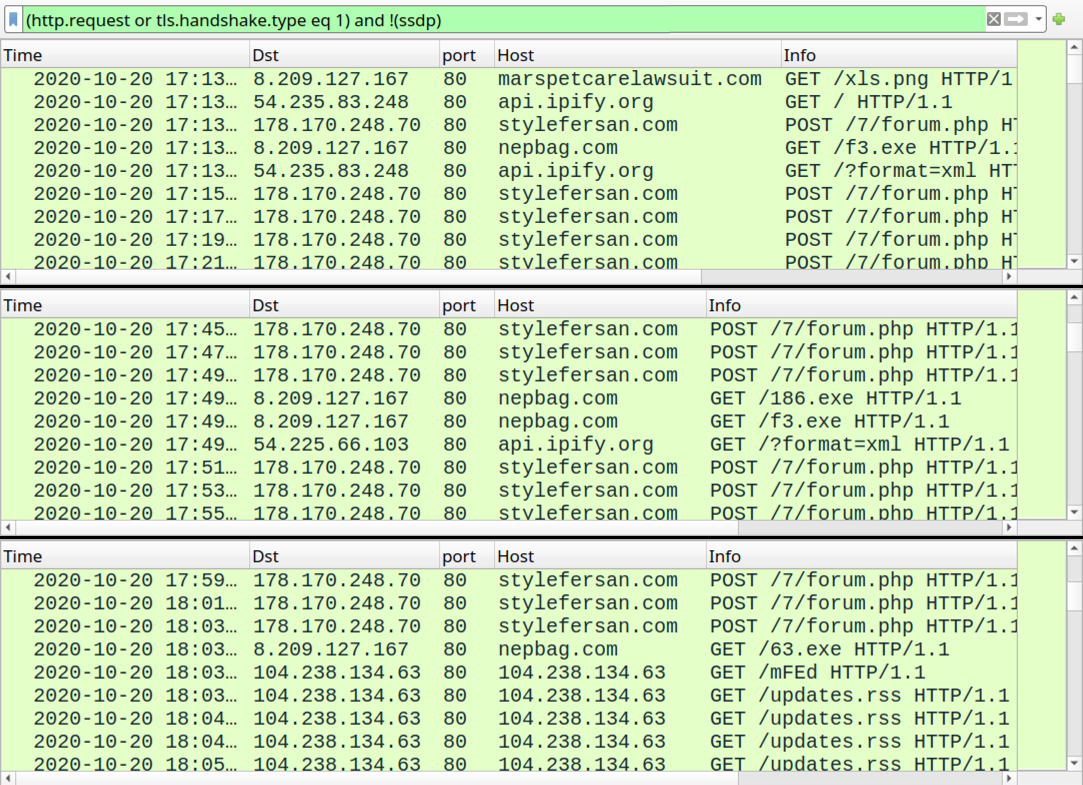
Shown above: Traffic from an infection filtered in Wireshark.
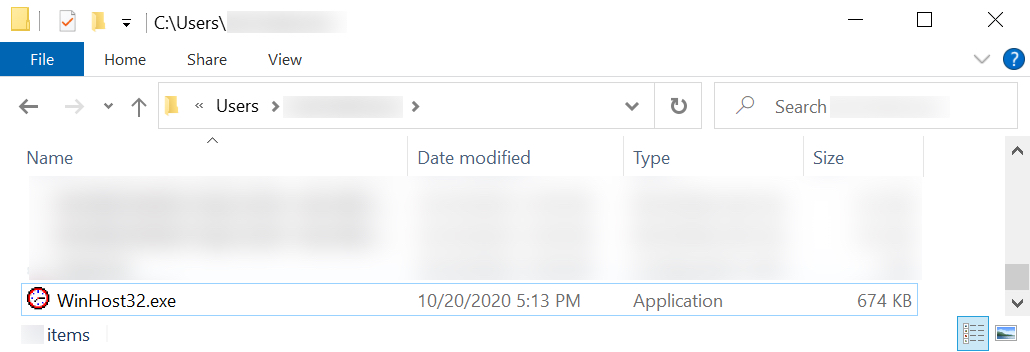
Shown above: The initial Hancitor EXE.
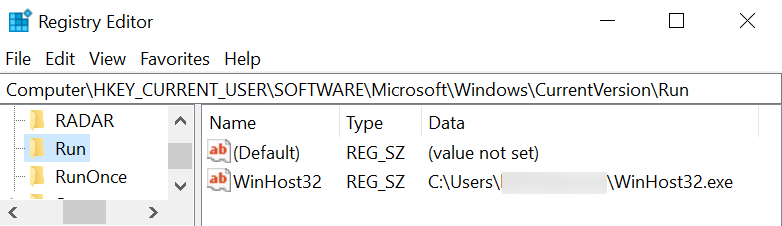
Shown above: Registry update to make the Hancitor EXE persistent.
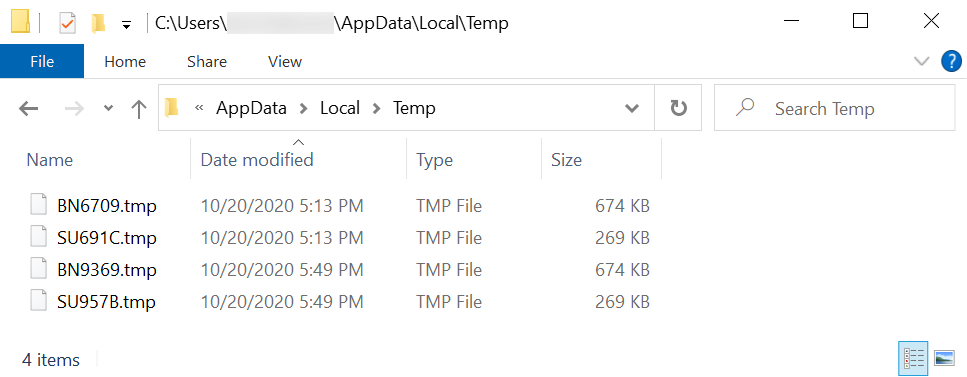
Shown above: Malware binaries in the infected user's AppData\Local\Temp directory.
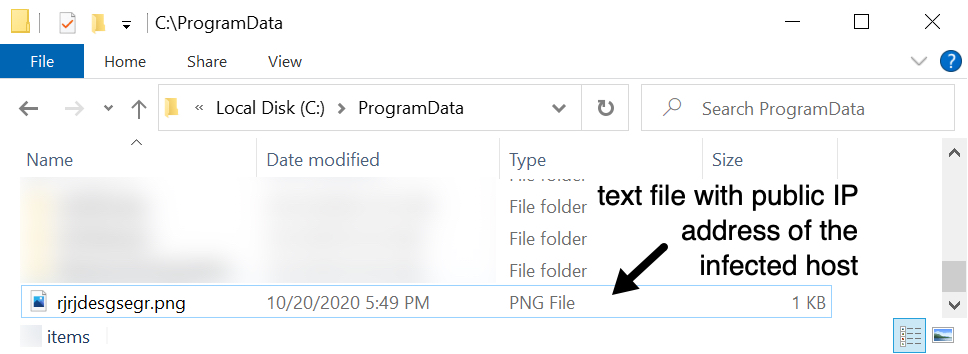
Shown above: This appeared after the Cobalt Strike activity started.
Click here to return to the main page.
文章来源: https://www.malware-traffic-analysis.net/2020/10/20/index.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh