![]()
Why FIM Add-Ons Aren’t Integrity Monitoring (& Why EDR Still Isn’t Enough)
嗯,用户让我用中文总结一篇文章,控制在100字以内,而且不需要特定的开头。首先,我得理解文章的内容。文章主要讲的是EDR平台的优势和局限性。EDR擅长检测和应对恶意活动,比如可疑进程、行为、横向移动和妥协指标。但它的不足之处在于无法确定系统是否处于已知和受信任的状态。它只能从端点遥测的角度观察,无法建立和强制执行环境的权威基线。
接下来,我需要把这些信息浓缩到100字以内。要确保涵盖EDR的优点和缺点。可能的结构是先说EDR的重要性及其擅长的部分,然后指出其不足之处,即无法确保系统状态的可信度。
然后,检查是否有关键词需要保留,比如“检测和响应恶意活动”、“可疑进程”、“横向移动”、“妥协指标”、“已知受信任状态”、“端点遥测”、“权威基线”。这些关键词有助于准确传达文章的核心内容。
最后,组织语言,使其简洁明了。例如:“EDR平台在检测和响应恶意活动方面表现出色,但无法确保系统处于已知受信任状态。它只能从端点遥测角度观察环境,并不能建立或强制执行文件、配置、身份和基础设施的权威基线。”
这样既涵盖了主要观点,又符合字数限制。
</think>
EDR平台在检测和响应恶意活动方面表现出色,但无法确保系统处于已知受信任状态。它只能从端点遥测角度观察环境,并不能建立或强制执行文件、配置、身份和基础设施的权威基线。
2026-1-8 15:15:0
Author: securityboulevard.com(查看原文)
阅读量:0
收藏
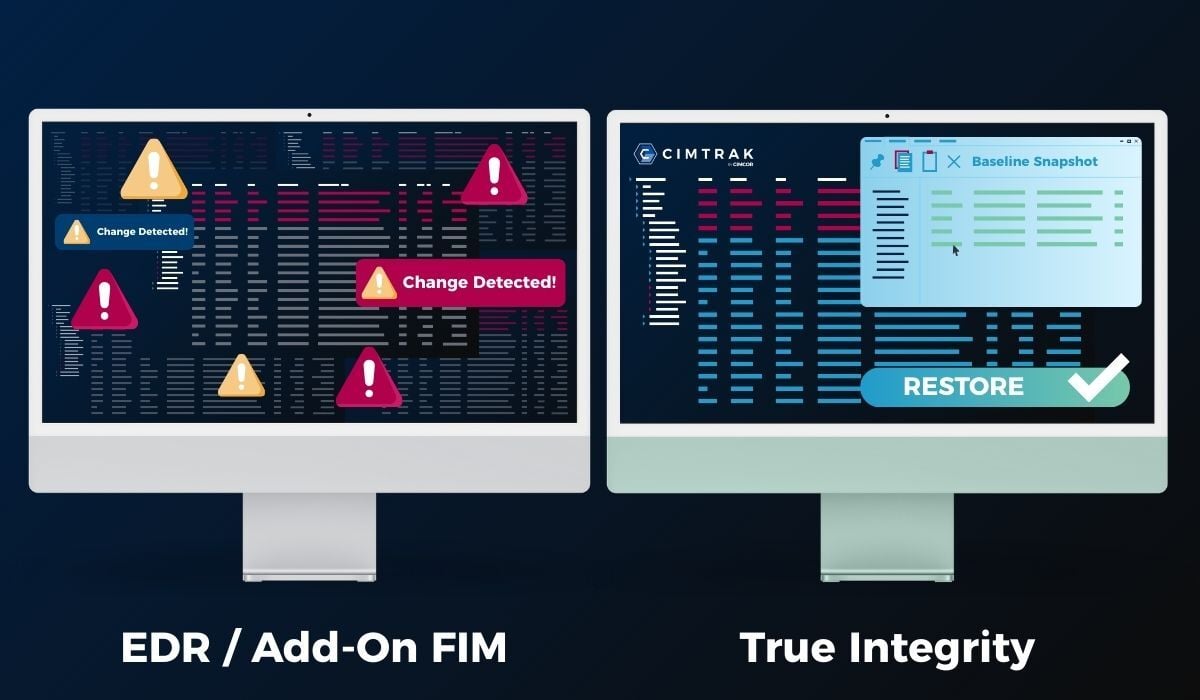
If you are running a strong EDR platform, you’re doing something right. EDR is essential. It’s great at detecting and responding to malicious activity: suspicious processes, behaviors, lateral movement, and indicators of compromise.
But here’s the uncomfortable truth: EDR does not tell you, with certainty, whether your systems are still in a known and trusted state. EDR tells you what it can observe from an endpoint telemetry perspective. It does not establish and enforce an authoritative baseline for your environment across files, configurations, identities, and infrastructure.

*** This is a Security Bloggers Network syndicated blog from Cimcor Blog authored by cimcoradmin. Read the original post at: https://www.cimcor.com/blog/fim-add-ons-arent-integrity-monitoring
文章来源: https://securityboulevard.com/2026/01/why-fim-add-ons-arent-integrity-monitoring-why-edr-still-isnt-enough/
如有侵权请联系:admin#unsafe.sh
![]()
