好的,用户让我用中文总结一下这篇文章,控制在100字以内,不需要特定的开头。首先,我需要通读整篇文章,抓住主要内容。 文章主要讲的是2025年圣诞节期间网络欺诈活动激增的情况。恶意机器人攻击显著增加,尤其是AI驱动的攻击手段。文章详细描述了攻击的不同阶段,比如漏洞扫描、 credential stuffing、假账户创建、数据抓取、倒票和支付欺诈等。 接下来,我需要提炼这些信息。重点包括:攻击的增加幅度(135%)、攻击手段的变化(利用AI隐藏行为)、以及不同行业的具体案例。 然后,我要确保总结简洁明了,不超过100字。可能的结构是先说明时间、现象,然后提到攻击手段的变化和影响。 最后,检查语言是否流畅,信息是否准确全面。 </think> 2025年圣诞节期间,网络欺诈活动激增135%,AI驱动的恶意机器人攻击显著增加。攻击者利用漏洞扫描、 credential stuffing、假账户创建、数据抓取、倒票和支付欺诈等手段,在节日期间对各行业发起大规模攻击。 2026-1-8 18:28:20 Author: securityboulevard.com(查看原文) 阅读量:0 收藏
The final two weeks of December are a time for rest and celebration for many, but in the world of cyberfraud, they represent a high-stakes window of opportunity for AI-driven bot attacks. While people enjoyed their holiday time and businesses managed their peak seasonal operations, the DataDome team and our AI models remained vigilant in the trenches to defend our customers.
In 2025, the ‘season of taking’ for fraudsters reached unprecedented heights. When comparing year-over-year data for the month of December, we observed a 135% surge in malicious bot requests.
Let’s go behind the scenes of these holiday battles to examine the lifecycle of year-end bot campaigns:
- Probing for gaps (vulnerability scanning): How attackers used reconnaissance to identify system weaknesses during busy shipping deadlines.
- Breaching existing trust (credential stuffing): The relentless use of stolen logins to hijack customer accounts, peaking during the quietest family moments of Christmas Eve and Christmas Day.
- Fabricating identities (fake account creation): The strategic creation of thousands of fraudulent “sleeper” profiles to hoard limited-time promotions and facilitate post-holiday gift card laundering.
- Monitoring & exhausting inventory (scraping & scalping): How bots tracked high-demand items in real-time before launching massive “add-to-cart” raids on luxury goods and event tickets.
- The final heist (payment fraud): The surge in fraudulent transactions on Christmas Day and New Year’s Eve as attackers looked to cash out while defenders were away.
A 135% surge in malicious bot requests YoY
The scale of the 2025 holiday activity reached levels significantly higher than the previous year. Comparing global traffic data from December 2024 to December 2025 reveals a year-over-year increase of 135% in bad bot activity.
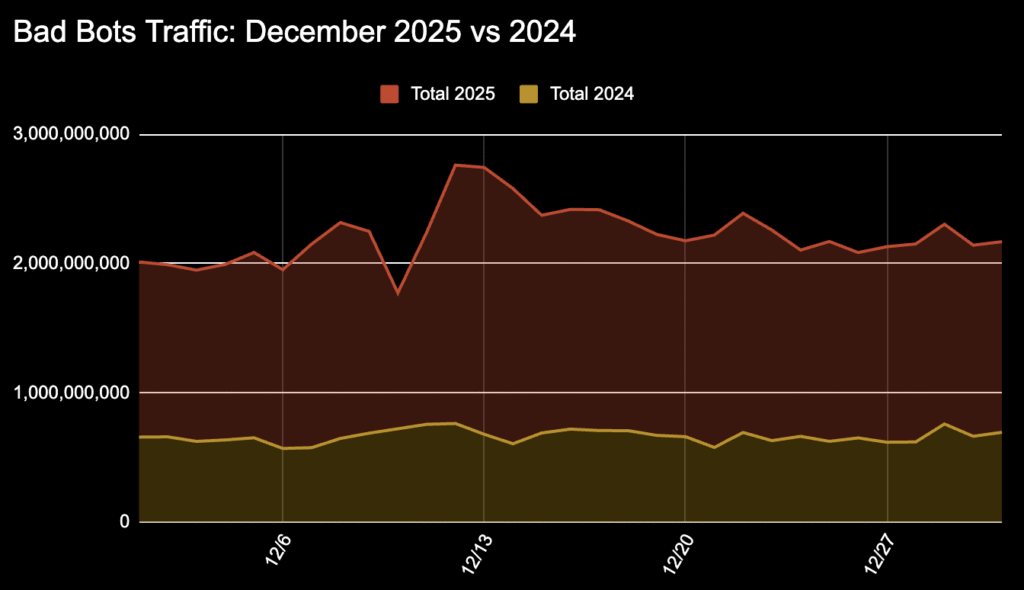
The 135% surge in malicious requests observed this season isn’t just a matter of volume, it reflects a fundamental shift in how bots bypass security. While our data captures the massive scale of these battles (from the vulnerability scans hitting the marketplace to the Christmas Day payment fraud peaks), it is the invisible role of AI that makes these attacks so dangerous.
AI has fundamentally changed the “rules of engagement” in three key ways:
- Mimicking the human “noise”: Fraudsters now use AI Agents to simulate realistic human behaviors (i.e., natural mouse movements and varied browsing patterns) allowing bots to “hide in the noise” of peak holiday traffic.
- High-fidelity identities: GenAI can be used to create synthetic profiles that appear indistinguishable from legitimate customers, allowing thousands of “sleeper” accounts to evade detection until the moment they launch an attack.
- Adaptive reconnaissance: AI-driven bots no longer follow a linear script. They can perform high-speed reconnaissance to identify system gaps in real-time, pivoting their tactics instantly when they encounter a defensive barrier.
In this AI-native landscape, the distinction between a genuine user and a sophisticated bot is blurrier than ever. Defenses must be as autonomous and adaptive as the threats they face.
From high activity to sudden spikes
For many of our customers, the early part of December already maintained a consistently high level of automated traffic, as we were coming off a busy Black Friday and Cyber Monday period in November. In addition, as the world moved into the heart of the festivities, the digital landscape shifted from predictable high volume to aggressive, sudden spikes for some businesses that had been somewhat spared until then.
Vulnerability scanning
Vulnerability scanning is an automated process (OWASP OAT-014) that uses bots or web crawlers to systematically probe a website’s underlying architecture, network devices, or applications to identify exploitable security weaknesses.
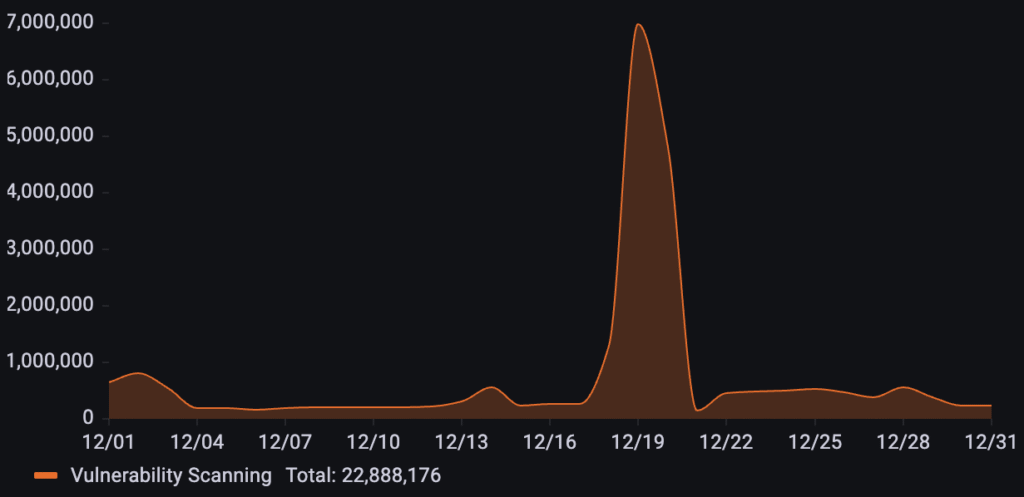
A leading online marketplace was targeted by over 22.8M vulnerability scanning requests throughout December. The attack pattern remained relatively dormant for the first half of the month before escalating into a massive, isolated peak on December 19th.
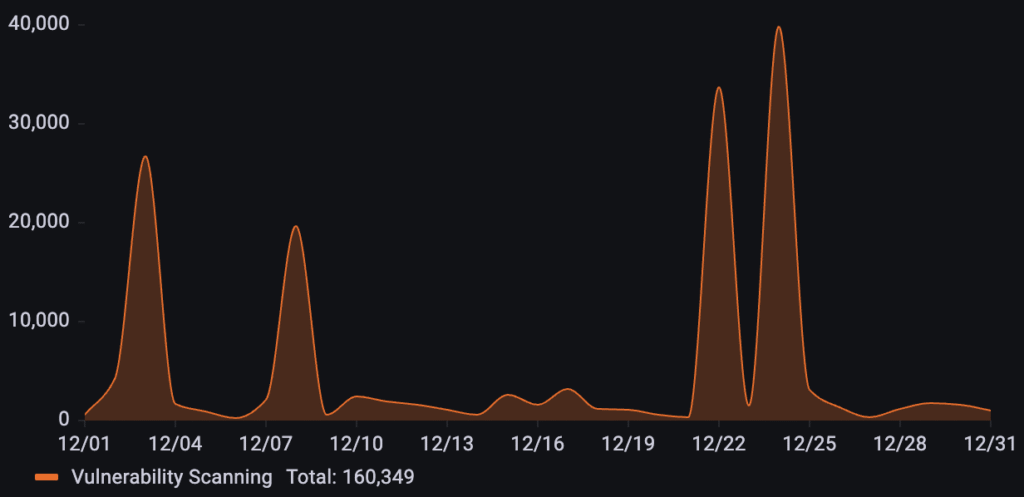
For a popular online grocer, “only” 160k vulnerability scanning requests were recorded in December, but the attack pattern was highly erratic, characterized by several sharp, isolated spikes rather than a steady baseline. These reconnaissance efforts reached distinct peaks on December 3rd, 8th, 22nd, and 24th.
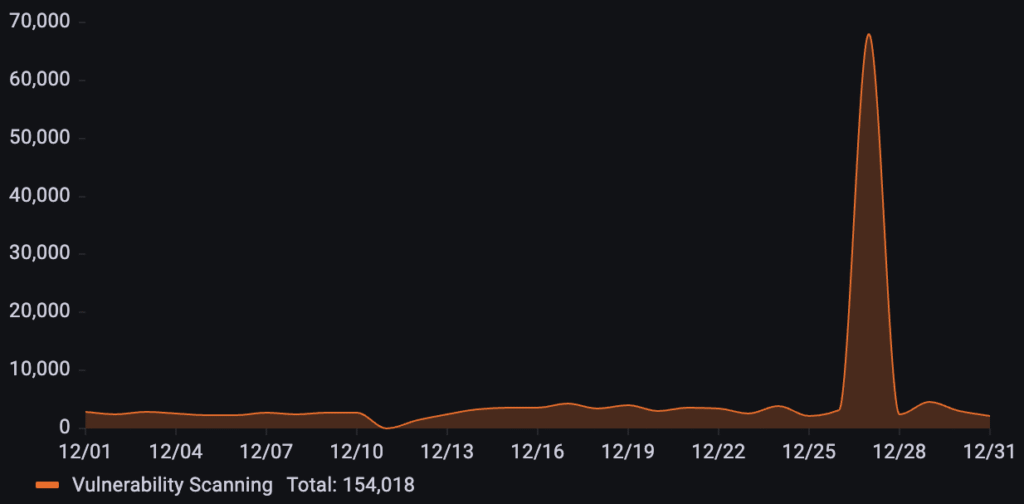
Targeting a business in the luxury retail industry, over 154k vulnerability scanning requests were recorded in December. The attack pattern remained at a low, steady baseline for the majority of the month until an isolated peak on December 27th.
Credential stuffing
Credential stuffing (OWASP OAT-008) is an automated cyberattack where malicious bots “stuff” known combinations of stolen usernames and passwords into online login pages. The primary goal of these attacks is Account Takeover (ATO), allowing fraudsters to hijack legitimate user accounts to drain gift cards, exploit stored payment data, or steal personal identities.
Facing over 1.8M credential stuffing requests throughout the month, a business in the retail and grocery industry experienced heightened activity with a significant and sharp peak occurring right after Christmas Day.
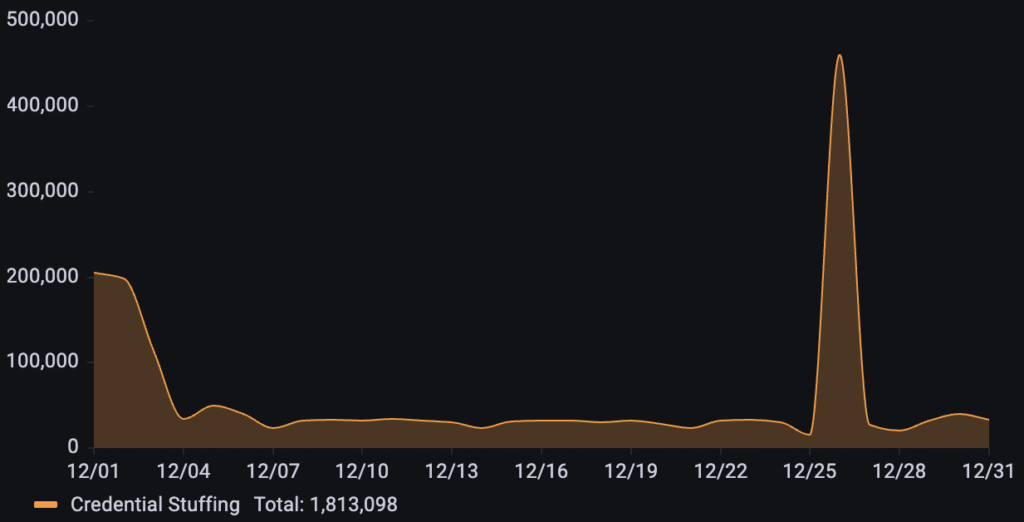
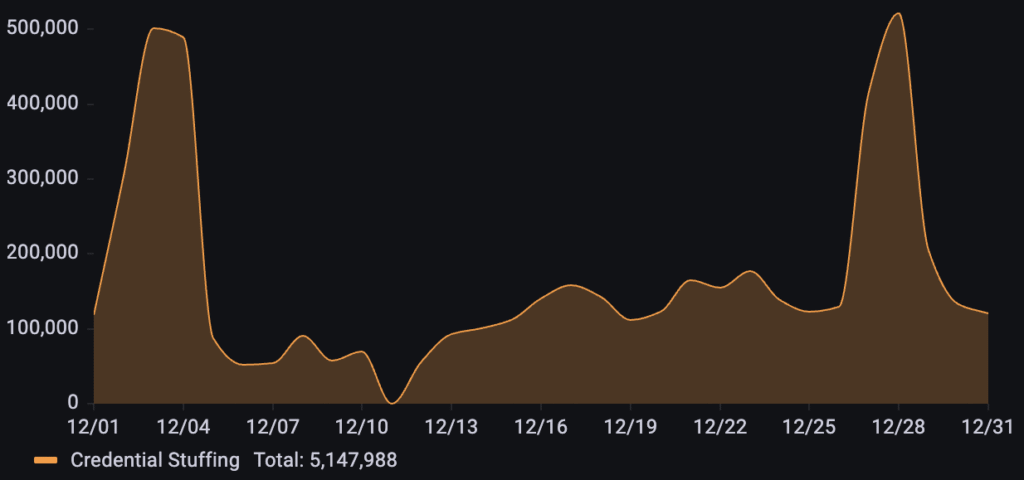
Targeting a popular classifieds platform, over 5.1M credential stuffing requests were detected throughout the month of December. The attack pattern was characterized by two major phases: an initial surge that peaked on December 3rd, followed by a period of sustained moderate activity that culminated in a large spike on December 28th.
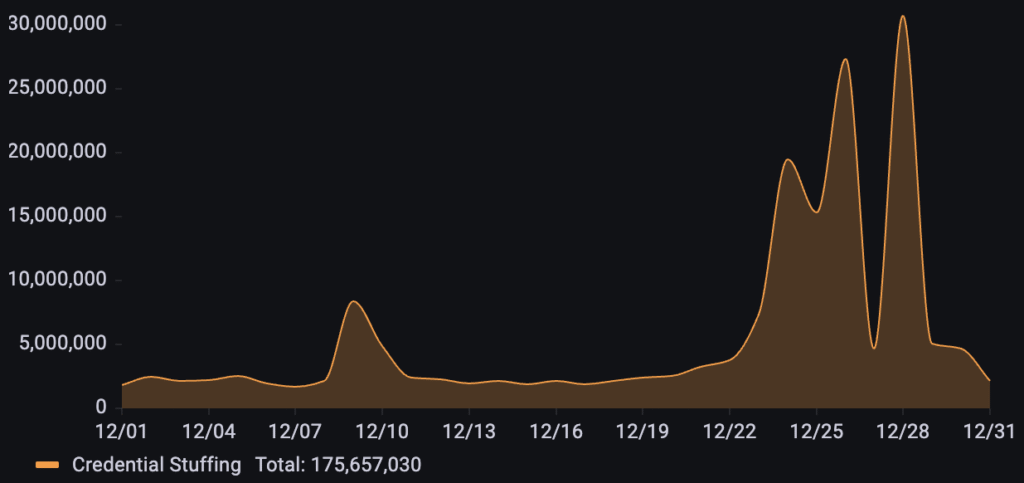
A business in the financial services industry was targeted by over 175M credential stuffing requests throughout December. The attack timeline shows a distinct, moderate surge on December 9th, followed by a period of relative stability before escalating into a massive campaign late in the month.
Fake account creation
Fake account creation (OWASP OAT-019) is a form of automated fraud where malicious bots or fraudsters generate new user accounts at scale using synthetic, fabricated, or stolen identity data. Unlike credential stuffing, which targets existing accounts, fake account creation focuses on building a fraudulent “sleeper” infrastructure of accounts that appear legitimate.
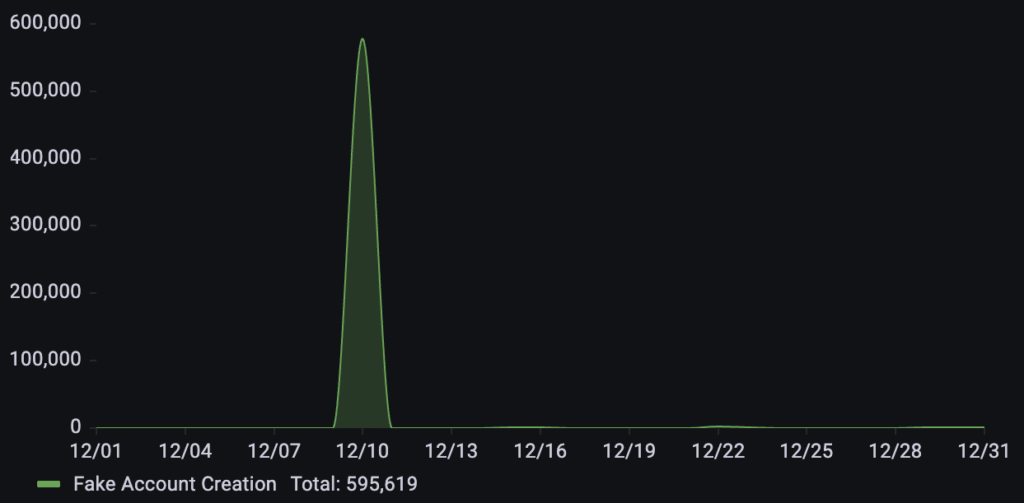
Targeting a business in the financial services industry, over 595k fake account creation requests were detected in December. The activity was marked by a sudden, massive escalation that reached a sharp peak on December 10th.
For this business in the sports industry, we detected over 5.2M fake account creation requests during December. The attack pattern was highly strategic, maintaining a low baseline before escalating into several moderate waves early in the month. This activity culminated in a massive surge that peaked on December 17th.
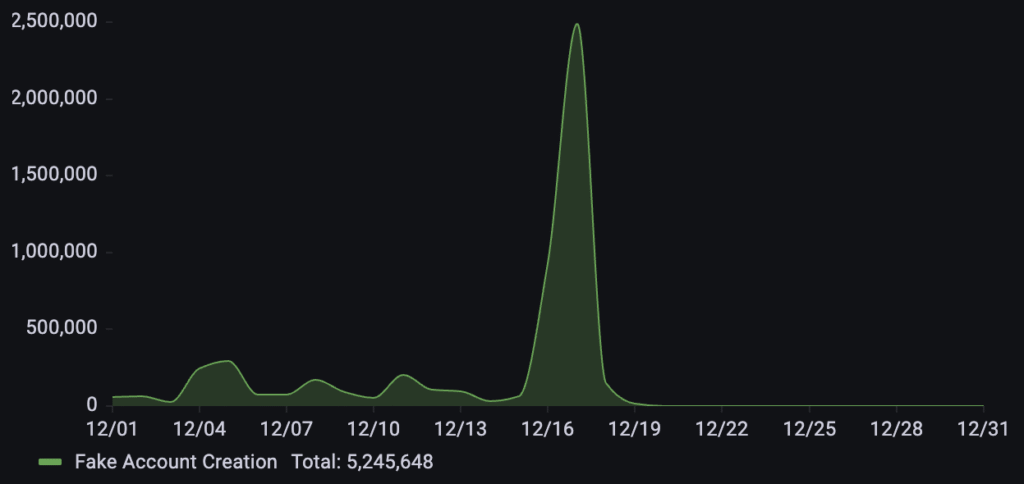
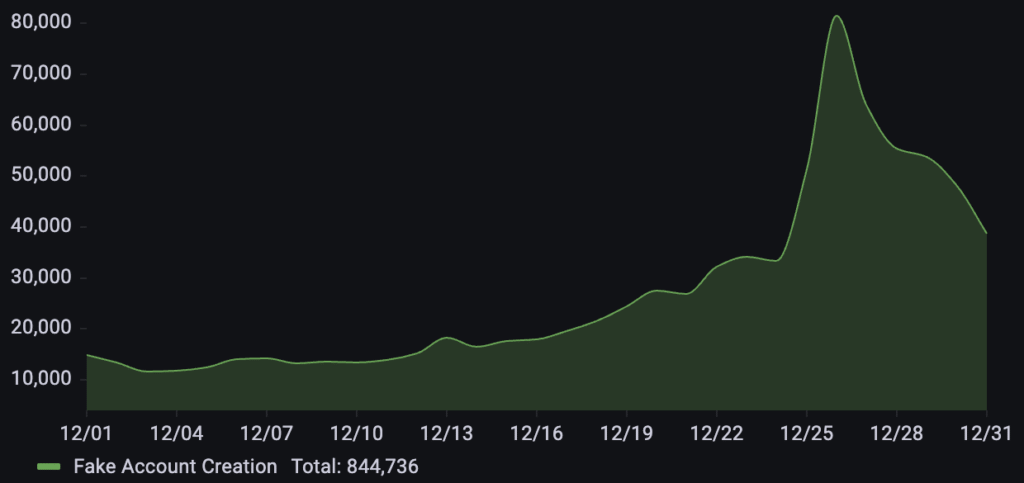
A business in the gift card industry experienced over 840k fake account creation requests during December. The attack pattern showed a gradual escalation starting mid-month, leading into a sustained surge that peaked on December 26th.
Scraping
Web scraping (OWASP OAT-011) is the automated extraction of data from websites, mobile apps, or APIs by bots simulating human browsing behavior. While some scraping is performed by “good bots” like search engine crawlers, malicious scraping aims to steal high-value content, product descriptions, reviews, or prices for competitive undercutting and reselling.
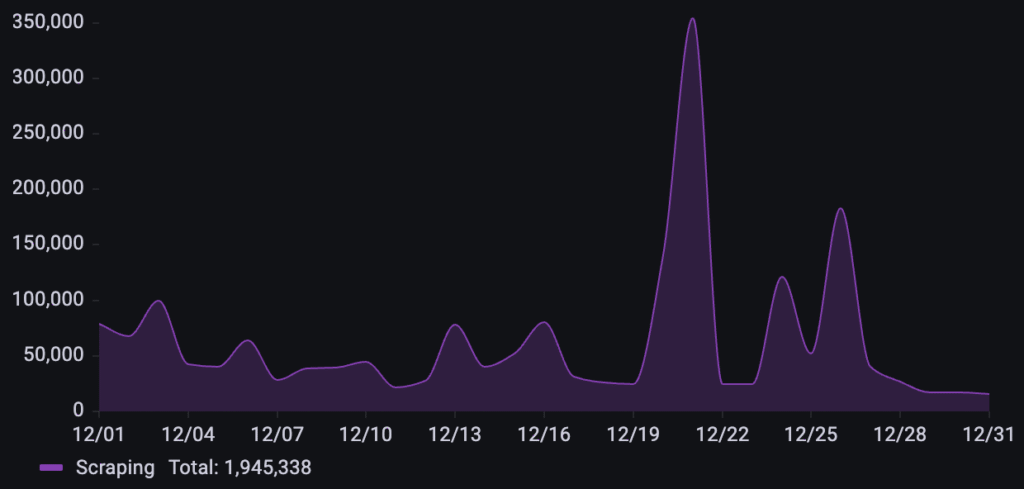
Throughout the month of December, a business in the online gaming and digital entertainment industry was targeted by over 1.9M scraping requests. The activity followed a highly volatile pattern with multiple distinct surges: a primary, massive spike on December 21st, followed by secondary waves on December 24th and 26th.
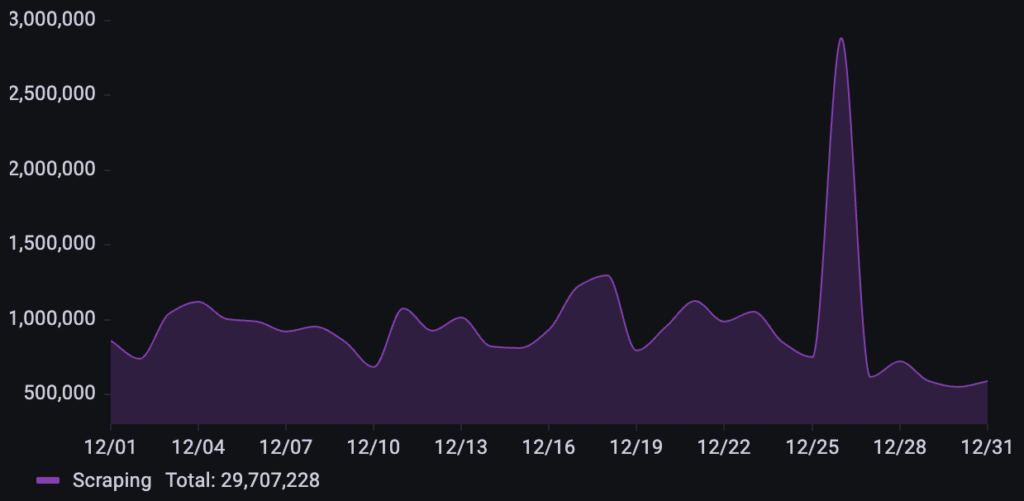
This business in the ticketing industry was targeted by over 29.7M scraping requests. While automated activity maintained a significant and relatively steady baseline for most of the month, the campaign reached an isolated peak on December 26th.
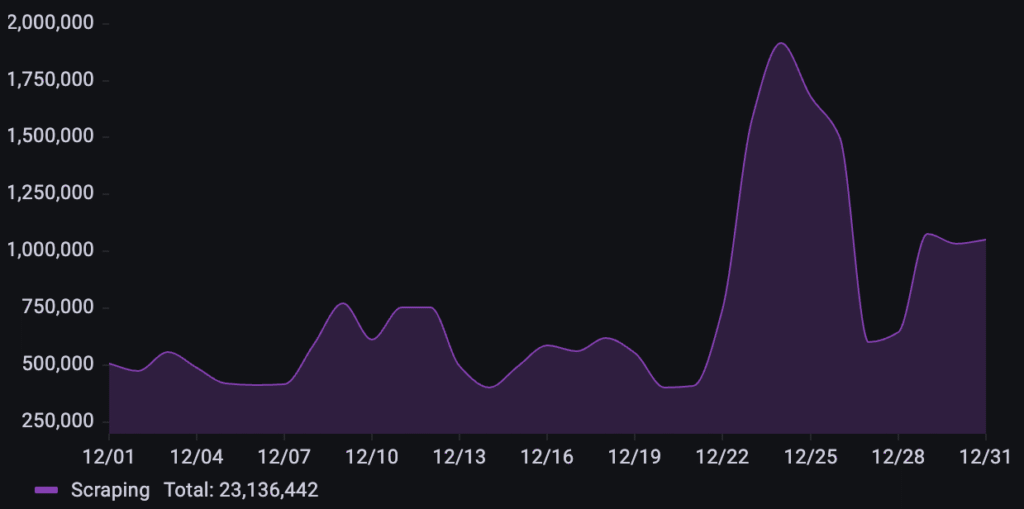
A business in the events industry was targeted by over 23M scraping requests throughout December. The traffic pattern remained relatively stable with moderate fluctuations during the first three weeks of the month, followed by a massive, sustained surge that peaked on December 24th.
Scalping
Scalping (OWASP OAT-005) is the automated process of using bots to purchase high-demand, limited-availability goods or services faster than any human could. These scalper bots exhaust inventory for legitimate customers and force them to buy from secondary markets at significantly inflated prices.
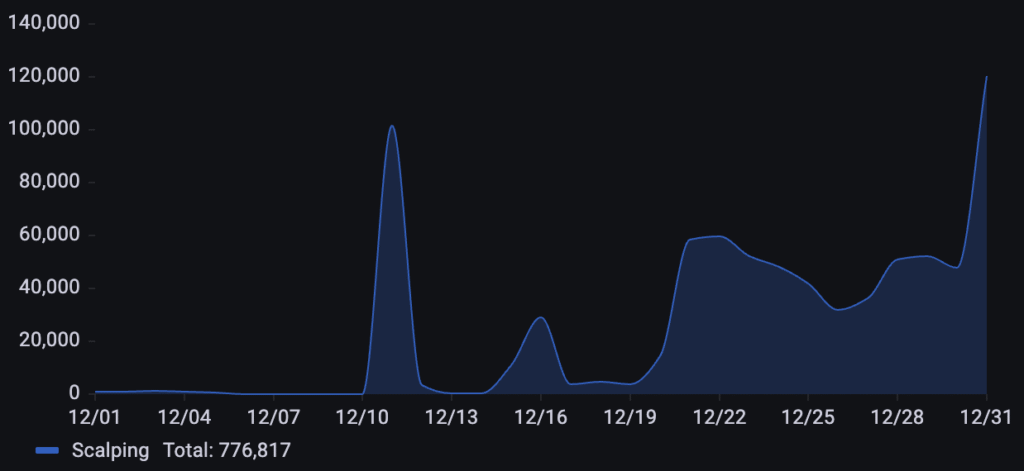
Targeting a business in the sports industry, over 776k scalping requests were detected throughout December. The attack pattern was nearly non-existent at first, followed by a sudden and aggressive spike on December 11th. After this initial surge, activity remained at an elevated baseline with consistent waves of automated traffic, ultimately culminating in a significant year-end peak on December 31st.
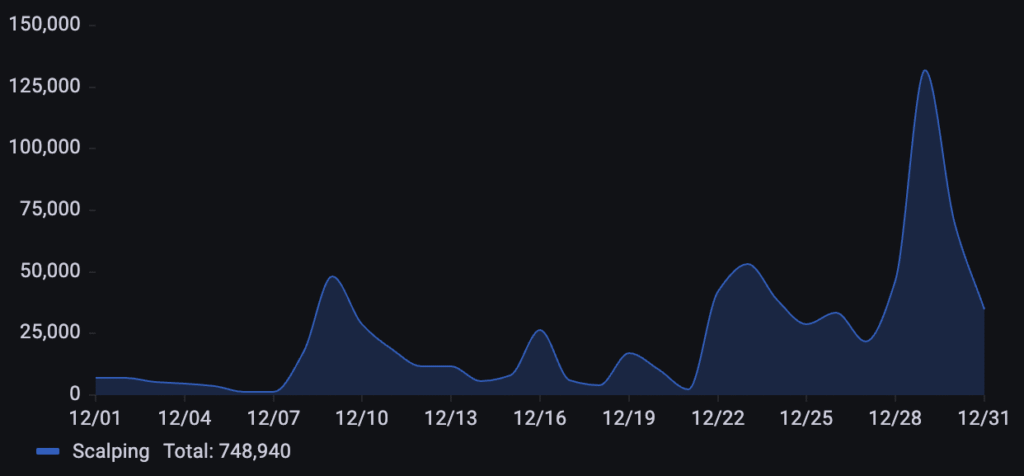
For this business in the ticketing and events industry, over 748k scalping requests were detected throughout December. The attack pattern was characterized by minor surges appearing on December 9th and December 23rd. This culminated in a sharp peak on December 29th, representing the most intense period of automated inventory exhaustion.
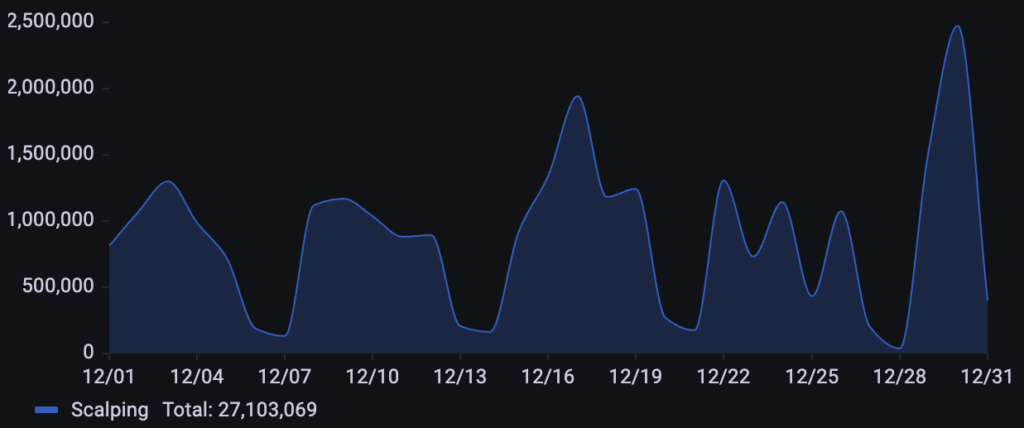
Targeting a business in the luxury retail industry, over 27M scalping requests were detected throughout December. The attack pattern was highly persistent, characterized by constant, high-frequency waves of activity. These automated surges reached a significant peak on December 17th before escalating into a final, month-high spike on December 30th.
Payment fraud
Payment fraud, AKA carding (OAT-001), is the unauthorized use of a payment method (i.e., stolen credit cards, gift cards, or digital wallets) to complete a transaction or to perform card cracking, where bots systematically test thousands of card numbers and CVV codes to find valid combinations.
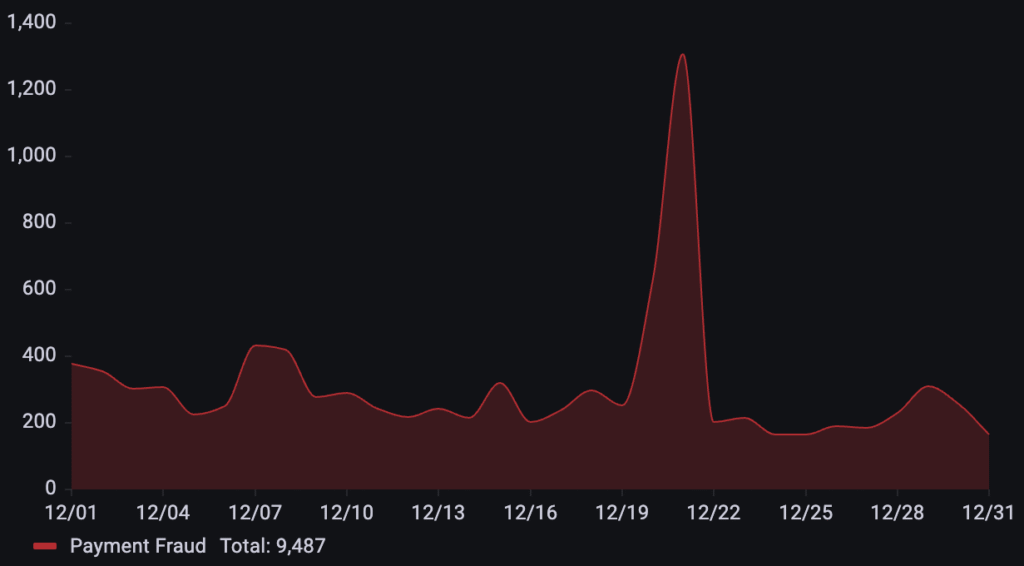
Targeting a business in the home improvement and retail industry, over 9k payment fraud requests were detected during the month of December. The activity was characterized by a sharp, isolated increase that peaked on December 21st, standing out significantly from the relatively low baseline of fraudulent traffic observed throughout the rest of the month.
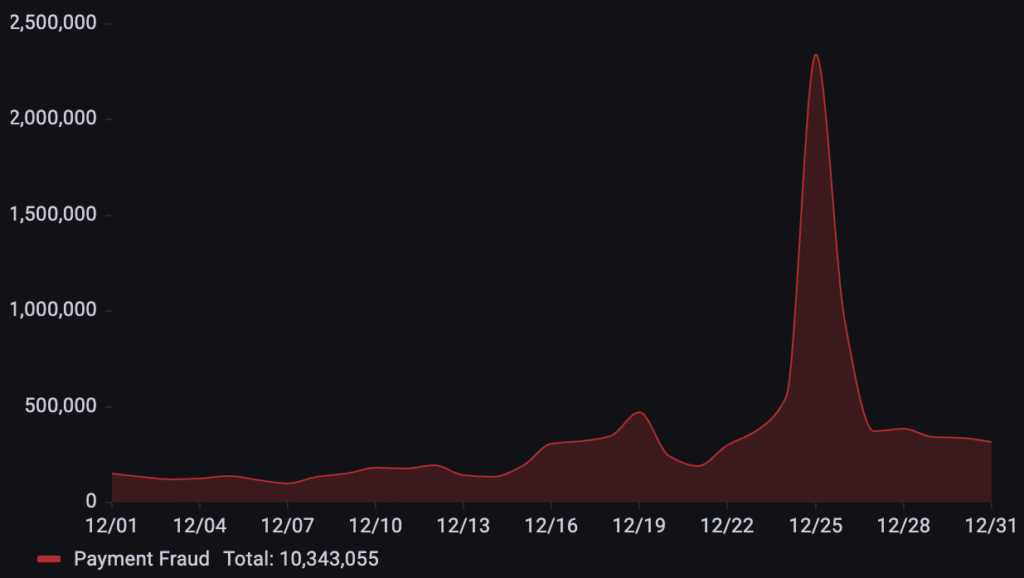
Focused around the holiday peak, a business in the gift card industry was hit by over 10.3M payment fraud requests in December. The attack timeline remained fairly steady until mid-month, when activity began to climb, eventually driving a massive, isolated peak on December 25th.
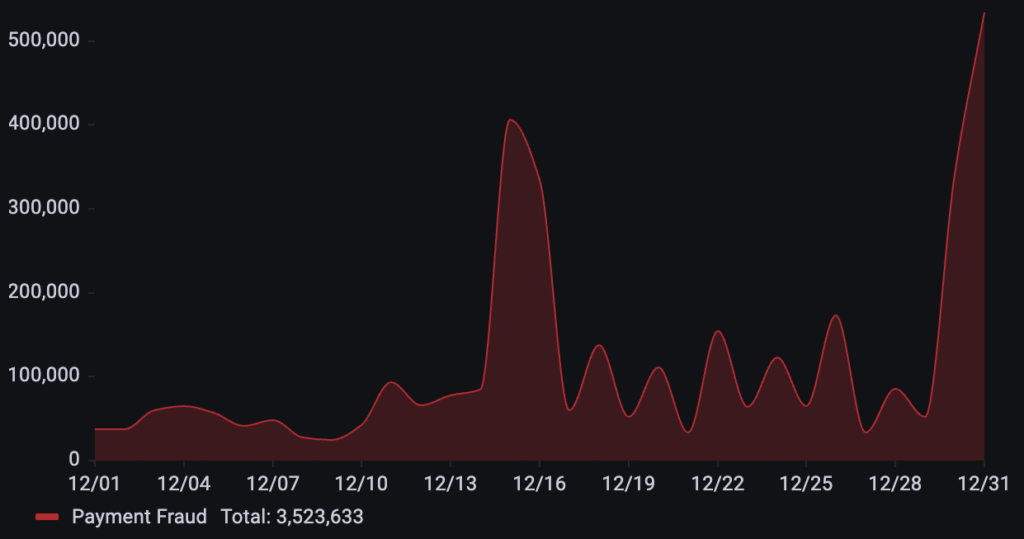
Targeting a business in the media and publishing industry, over 3.5M payment fraud requests were detected in December. The attack pattern was highly volatile, featuring a series of escalating surges that peaked sharply on December 15th, with a significant secondary spike following on December 31st.
如有侵权请联系:admin#unsafe.sh