A recently disclosed vulnerability affecting MongoDB instances has been reportedly exploited in the wild. Exploit code has been released for this flaw dubbed MongoBleed.
Key takeaways:
- MongoBleed is a memory leak vulnerability affecting multiple versions of MongoDB.
- Exploitation of MongoDB has been observed and exploit code is publicly available .
- Immediate patching is recommended as the combination of public exploit code and a high number of potentially affected internet connected instances make this a flaw attackers will be targeting.
Background
On December 19, MongoDB issued a security advisory to address a vulnerability affecting the zlib implementation of MongoDB.
| CVE | Description | CVSSv3 | VPR |
|---|---|---|---|
| CVE-2025-14847 | MongoDB Uninitialized Memory Leak Vulnerability (“MongoBleed”) | 7.5 | 8.0 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was published on December 29 and reflects VPR at that time.
Analysis
CVE-2025-14847 is a memory leak vulnerability affecting MongoDB instances in which zlib compression is enabled. A flaw in how MongoDB implements zlib decompression could allow unauthenticated attackers to leak uninitialized memory, which can contain sensitive data including credentials, session tokens and API keys. This flaw was dubbed “MongoBleed” by Elastic Security researcher Joe Desimone, who published a proof-of-concept demonstrating the vulnerability. While exploitation does require zlib compression to be enabled and a vulnerable MongoDB version to be internet exposed, reports of in the wild exploitation have already begun.
According to Censys, there are over 87,000 potentially vulnerable instances of MongoDB that have been identified, with the largest concentration being found in the United States.

Source: Censys
Proof of concept
On December 25, a public proof-of-concept (PoC) was released on GitHub. This PoC demonstrates how data can be leaked from uninitialized memory. According to the PoC details, the following data could be leaked:
- MongoDB internal logs and state
- WiredTiger storage engine configuration
- System /proc data (meminfo, network stats)
- Docker container paths
- Connection UUIDs and client IPs
Solution
MongoDB has released patches to address this vulnerability as outlined in the table below:
| Affected Version | Fixed Version |
|---|---|
| MongoDB Server v3.6 (All Versions) | Upgrade to MongoDB 8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32, 4.4.30 or later |
| MongoDB Server v4.0 (All Versions) | Upgrade to MongoDB 8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32, 4.4.30 or later |
| MongoDB Server v4.2 (All Versions) | Upgrade to MongoDB 8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32, 4.4.30 or later |
| MongoDB 4.4.0 through 4.4.29 | Upgrade to MongoDB 4.4.30 or later |
| MongoDB 5.0.0 through 5.0.31 | Upgrade to MongoDB 5.0.32 or later |
| MongoDB 6.0.0 through 6.0.26 | Upgrade to MongoDB 6.0.27 or later |
| MongoDB 7.0.0 through 7.0.26 | Upgrade to MongoDB 7.0.28 or later |
| MongoDB 8.0.0 through 8.0.16 | Upgrade to MongoDB 8.0.17 or later |
| MongoDB 8.2.0 through 8.2.2 | Upgrade to MongoDB 8.2.3 or later |
According to the MongoDB security advisory, if immediate patching is not able to be performed, the workaround suggestion is to disable zlib compression. In addition, we recommend that you limit network access to MongoDB instances to trusted IP addresses only. While this step was not outlined in the advisory, it has been recommended as a security best practice by MongoDB.
Identifying affected systems
A list of Tenable plugins for this vulnerability can be found on the individual CVE page for CVE-2025-14847 as they’re released. This link will display all available plugins for this vulnerability, including upcoming plugins in our Plugins Pipeline.
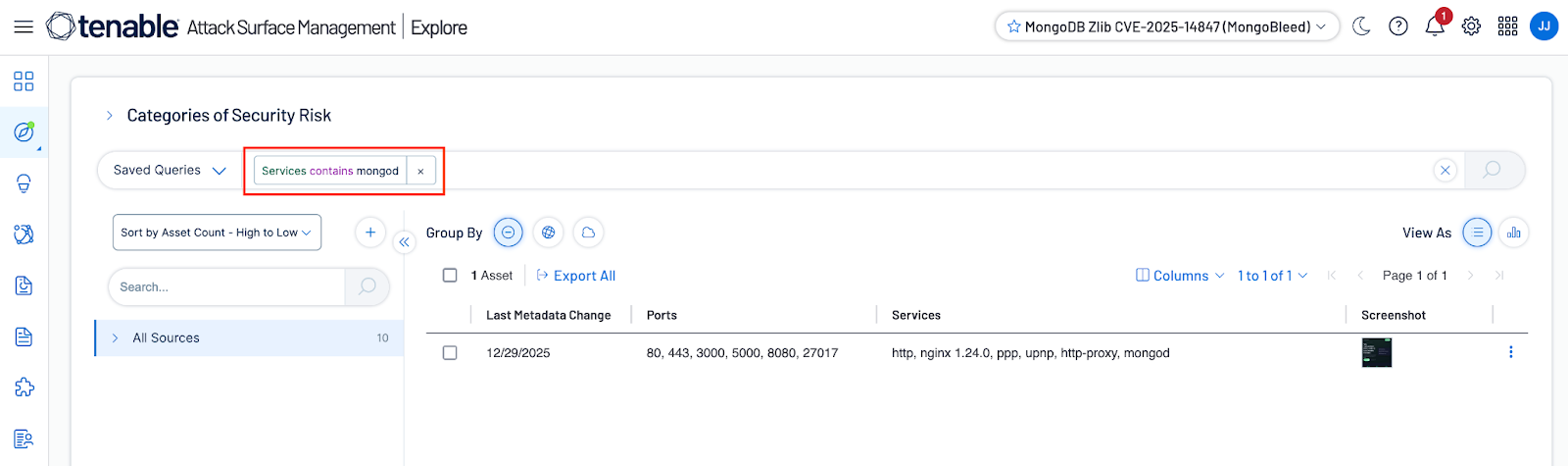
Tenable Attack Surface Management customers are able to identify assets running MongoDB services by using the filter ‘Services contains mongod’ as shown in the screenshot below:

Get more information
Join on Tenable Connect and engage with us in the for further discussions on the latest cyber threats.
Learn more about , the Exposure Management Platform for the modern attack surface.
*** This is a Security Bloggers Network syndicated blog from Tenable Blog authored by Scott Caveza. Read the original post at: https://www.tenable.com/blog/cve-2025-14847-mongobleed-mongodb-memory-leak-vulnerability-exploited-in-the-wild