
嗯,用户让我用中文帮他总结一下这篇文章的内容,控制在一百个字以内,而且不需要以“文章内容总结”或者“这篇文章”这样的开头,直接写描述即可。首先,我需要通读整篇文章,抓住主要观点和关键信息。 文章主要讨论了零日威胁(zero-day threats)的严重性以及传统防御方法的不足。零日威胁指的是尚未被发现或修补的软件漏洞被攻击者利用的情况。传统的基于签名的防御方法在这种情况下无效,因为没有已知的特征可以检测。 接下来,文章介绍了零日攻击的生命周期,并强调了行为分析、机器学习和高级威胁检测平台的重要性。这些技术通过观察行为而非依赖已知特征来识别威胁。文中还提到了一些具体的解决方案,如VMRay、CrowdStrike Falcon等工具,并讨论了如何选择适合组织环境的平台。 最后,文章强调了构建分层防御策略的重要性,并提醒读者避免常见的误区,如过度依赖自动化而忽视人工分析等。 现在,我需要将这些要点浓缩到100字以内。重点包括零日威胁的特点、传统防御的不足、有效检测方法(行为分析和机器学习)以及推荐的解决方案和分层防御策略。 </think> 零日威胁利用未知软件漏洞,在补丁发布前发起攻击。传统基于签名的防御无法检测此类威胁。有效的检测需依赖行为分析、机器学习及先进平台,通过观察异常行为而非已知特征识别威胁。推荐工具包括VMRay、CrowdStrike Falcon等,并需构建分层防御体系以覆盖多个攻击面。 2025-12-18 22:51:15 Author: www.vmray.com(查看原文) 阅读量:9 收藏
You can’t defend against what you can’t see. That’s the brutal reality of zero-day threats (newly discovered vulnerabilities that attackers weaponize before patches exist). While signature-based defenses sit idle, zero-days slip through undetected, quietly establishing footholds in your environment.
For SOC teams, CTI analysts, and security decision-makers, the question isn’t whether you’ll face zero-day attacks but whether your tools can catch them before real damage happens. With average breach costs exceeding $4.45 million and attackers moving faster than ever, waiting for yesterday’s signatures won’t cut it.
So what does work? Let’s cut through the vendor noise and look at what actually matters when you’re building zero-day detection into your security stack.
What Is a Zero-Day Threat?

Before we dive into detection tools, let’s clarify what we’re actually defending against.
A zero-day vulnerability is a security flaw in software that the vendor doesn’t know about yet. It’s called “zero-day” because developers have had zero days to fix it. When attackers discover these vulnerabilities before the good guys do, they can exploit them with zero-day attacks.
Here’s how the timeline typically unfolds:
Day 0: Attacker discovers a vulnerability in widely-used software
Days 1-30 (or longer): Attacker weaponizes the vulnerability and begins exploiting it in the wild
Day 31: Security researchers or the vendor finally discover the active exploitation
Day 45: Vendor releases a patch
Days 46-180: Organizations slowly deploy the patch (if they ever do)
That window between exploitation and patching? That’s when zero-day attacks do their damage. And traditional signature-based defenses can’t help because there’s no signature to detect yet.
Zero-day malware takes this further. It’s malicious code that uses these unknown vulnerabilities to avoid detection entirely. Since antivirus databases don’t have signatures for threats they’ve never seen, the malware executes freely until someone documents it, analyzes it, and creates detection rules.
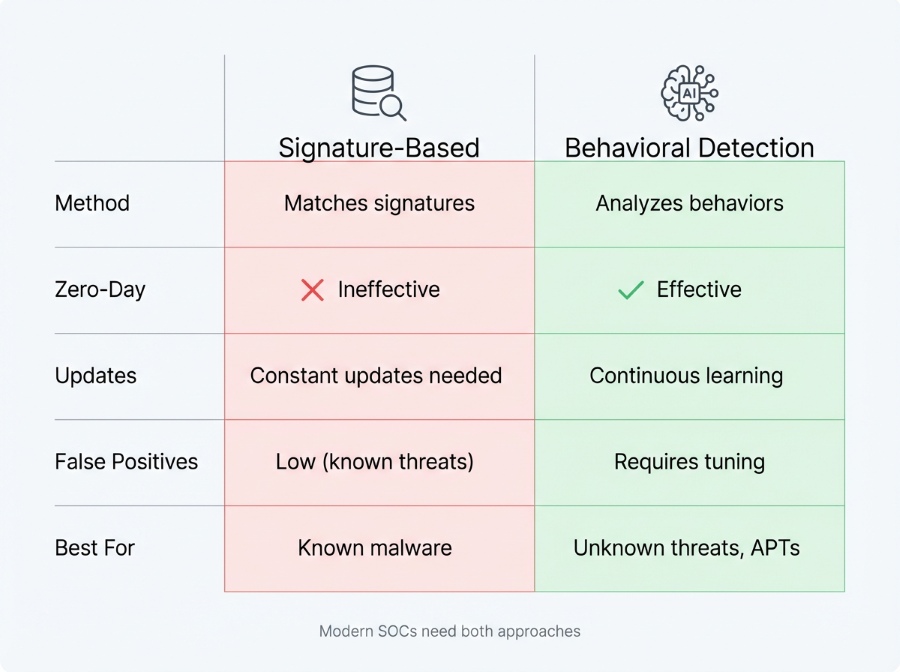
Think of it this way: if signature-based security is like checking IDs against a watchlist, zero-day threats are the people who aren’t on any list yet. You need different tactics (like watching for suspicious behavior) to catch them.
That’s why behavioral analysis, machine learning, and advanced threat detection platforms have become critical. They don’t ask “have we seen this before?” They ask “is this behavior dangerous?” And that question works against both known and unknown threats.
Why Traditional Detection Fails Against Zero-Day Threats
Here’s what keeps happening: An attacker exploits a vulnerability nobody knew existed. Your traditional antivirus looks for known malware signatures. It finds nothing because, well, there’s nothing to find yet. The malware executes, spreads laterally, and you don’t notice until weeks later when the damage is done.
Signature-based tools are great at catching yesterday’s threats. But zero-days? They’re invisible to these systems until threat intelligence vendors document them, analyze them, and push out updates. By then, you’re already compromised.
That’s where behavioral analysis, machine learning, and advanced threat detection platforms come in. Instead of asking “have we seen this exact file before?” these tools ask “is this behavior suspicious?” (Think of it like spotting a burglar not by their face, but by watching someone jimmy a window at 3 AM.)
What Makes a Zero-Day Detection Tool Actually Effective?
Before we jump into specific platforms, let’s talk about what separates the performers from the pretenders. Not all “zero-day protection” is created equal, and plenty of vendors slap AI stickers on legacy tech.
Behavioral Analysis That Goes Beyond Basic Heuristics
You need tools that watch how code behaves, not just what it looks like. Advanced malware sandboxes execute suspicious files in isolated environments so you can observe their actual behavior: registry modifications, network callbacks, process injection, persistence mechanisms. This isn’t about guessing; it’s about watching the attack unfold in a controlled space.
VMRay’s approach stands out here. Their agentless dynamic analysis watches malware at the hypervisor level, which means evasive threats can’t detect they’re being monitored. When malware thinks it’s running on a real system, it shows its true colors. Understanding why sandboxing matters is critical when evaluating tools that claim to detect zero-day threats.
Machine Learning Models Trained on Real Attack Data
AI is everywhere in cybersecurity marketing, but what matters is how it’s used. The best platforms train models on millions of malware samples and real-world attack telemetry. They learn to spot anomalies that human analysts would miss (subtle deviations in process execution, unusual API call sequences, weird memory manipulation).
However, machine learning is only as good as the data feeding it. Platforms like CrowdStrike Falcon and Palo Alto Cortex XDR use cloud-scale machine learning to continuously refine detection models. When one customer gets hit by a new technique, the entire customer base benefits from updated models.
Integration With Your Existing Stack
A standalone detection tool that doesn’t talk to your SIEM, EDR, or SOAR platform is just creating more work. You need connectors that feed high-fidelity alerts into your existing workflows so you can correlate data, automate response, and get context without switching between seventeen browser tabs.
Modern platforms provide REST APIs and pre-built integrations with major security vendors. Check whether the tool plays nice with your Microsoft Defender, Splunk, or whatever else you’re running.
Speed and Accuracy Under Pressure
False positives kill productivity. If your team spends half their day chasing benign alerts, they’ll miss the real threats. Look for platforms that provide clear verdicts with supporting evidence (execution traces, network indicators, file modifications) so analysts can make confident decisions quickly.
This is where building AI-powered defenses on facts, not fiction becomes crucial. You need platforms that deliver explainable results with evidence trails, not just black-box AI verdicts you’re expected to trust blindly.
The Top Zero-Day Detection Solutions for 2026
Let’s break down the platforms actually moving the needle for enterprise SOC teams right now.
1. Advanced Malware Sandboxes
What they do: Execute suspicious files in isolated environments to observe behavior, extract indicators of compromise, and generate detailed analysis reports.
Best for: Deep forensic analysis, phishing response, malware triage, threat intelligence generation.
VMRay DeepResponse & FinalVerdict
VMRay’s sandbox technology uses hypervisor-level monitoring that evasive malware can’t detect or bypass. Unlike traditional sandboxes that rely on in-guest agents (which sophisticated malware can identify and evade), VMRay’s agentless approach captures complete behavioral data.
Their platform excels at detecting advanced persistent threats, fileless malware, and zero-day exploits that slip past endpoint defenses. The analysis reports include execution traces, network traffic, registry changes, and automatically extracted IOCs you can feed directly into your threat intelligence platforms.
Recent updates added computer vision capabilities for phishing detection, making it harder for attackers to use brand impersonation and visual tricks to evade analysis. As AI’s role in cybersecurity continues to expand, VMRay’s approach demonstrates how AI should augment human analysis rather than replace it.
Why SOC teams choose it: High-fidelity verdicts with minimal false positives, detailed forensic evidence for incident response, and strong integration ecosystem with EDR/SIEM/SOAR platforms.
2. EDR/XDR Platforms with Zero-Day Detection
What they do: Monitor endpoint, network, cloud, and identity telemetry in real-time, using behavioral analytics and machine learning to detect and respond to threats across your entire environment.
Best for: Continuous monitoring, automated response, threat hunting, comprehensive visibility.
CrowdStrike Falcon
CrowdStrike crushed the 2025 MITRE ATT&CK evaluations with 100% detection, 100% protection, and zero false positives (yes, zero). Their cloud-native platform uses behavioral AI to catch zero-day exploits, fileless attacks, and advanced threats that signature-based tools miss.
Falcon integrates next-generation antivirus (NGAV) and EDR with real-time threat intelligence for preemptive zero-day defense. Their indicator of attack (IOA) approach focuses on adversary behaviors aligned with MITRE ATT&CK tactics. Instead of waiting for known malware signatures, it watches for suspicious patterns like unusual process execution, lateral movement attempts, or credential dumping.
Why teams choose it: Market-leading threat intelligence, rapid detection and response, strong cloud security coverage, and a proven track record in real-world evaluations.
SentinelOne Singularity
SentinelOne uses advanced AI and machine learning for endpoint protection, stopping unknown threats through deep activity monitoring. Their platform uses deep learning models trained on massive datasets to identify zero-day threats, ransomware, and advanced persistent threats without requiring constant updates.
One standout feature: automated rollback for ransomware attacks. If the platform detects encryption behavior, it can automatically restore affected systems to their pre-attack state.
Palo Alto Cortex XDR
Cortex XDR unifies data from endpoints, networks, cloud workloads, and identity systems into a single platform. It uses behavioral analytics and machine learning to automatically correlate related alerts into prioritized incidents (saving analysts from drowning in individual events).
Their AI-driven root cause analysis helps you understand how an attack happened and what the attacker tried to accomplish. That context is gold for threat hunting and improving defenses.
Cynet
Cynet offers an Advanced Threat Detection platform with AI to detect advanced malware and APTs, even those evading traditional antivirus. Their platform provides comprehensive coverage across endpoints, networks, and user behavior, making it a strong choice for organizations looking for consolidated security operations.
3. Unified Threat Detection and Prevention Platforms
What they do: Combine multiple security capabilities into unified platforms that detect and prevent threats across various attack surfaces.
Best for: Organizations seeking consolidated security operations, proactive threat prevention, and reduced tool sprawl.
Seceon
Seceon leverages AI/ML and Dynamic Threat Modeling (DTM) for proactive, automated detection across network and user activity. Their platform excels at identifying behavioral anomalies that indicate zero-day exploitation, even when the specific vulnerability isn’t documented yet.
Check Point
Check Point focuses on a “prevent-first” approach with evasion-resistant technology to block unknown attacks across all vectors. Their threat prevention architecture stops zero-day exploits before they can execute, combining behavioral analysis with threat intelligence to identify malicious activity patterns.
4. Cloud-Native Application Protection
What they do: Protect cloud workloads and applications from zero-day threats with runtime protection and real-time threat detection.
Best for: Organizations with significant cloud infrastructure, DevSecOps teams, containerized environments.
Upwind Security
Upwind Security offers a Cloud-Native Application Protection Platform (CNAPP) with machine learning for real-time inventory and runtime protection. As workloads increasingly move to cloud environments, having zero-day detection that understands cloud-native architectures becomes critical.
5. Web Application Firewall (WAF) Solutions
What they do: Protect web applications and APIs from zero-day attacks using machine learning to detect and block malicious requests in real-time.
Best for: Organizations with customer-facing web applications, API-heavy architectures, e-commerce platforms.
Open-Appsec
Open-Appsec is an open-source WAF that uses machine learning to detect and block zero-day attacks on web apps and APIs in real-time. Their approach learns normal application behavior and identifies deviations that indicate exploitation attempts, making it particularly effective against novel web-based attacks.
6. Network Detection and Response (NDR) Platforms
What they do: Analyze network traffic to detect anomalous behaviors, lateral movement, command-and-control communications, and data exfiltration attempts.
Best for: Detecting threats that have already bypassed perimeter defenses, identifying lateral movement, catching insider threats.
Vectra AI
Vectra uses AI to detect attacker behaviors across network, endpoint, cloud, and identity layers. Their platform excels at finding threats that have already gotten inside (like compromised credentials being used for lateral movement).
Darktrace
Darktrace’s self-learning AI establishes a baseline of “normal” behavior for your network and alerts on deviations. This unsupervised learning approach can catch novel attacks that don’t match any known patterns.
7. Threat Intelligence Platforms
What they do: Aggregate, enrich, and contextualize threat data from multiple sources to help you prioritize alerts and understand emerging threats.
Best for: Strategic threat awareness, IOC enrichment, proactive hunting, risk assessment.
Recorded Future
Provides real-time threat intelligence by analyzing data from the open web, dark web, technical sources, and finished intelligence reports. Their platform helps you understand which zero-day vulnerabilities are being actively exploited and by whom.
Anomali
Integrates threat intelligence into your security workflows, enriching alerts with context about threat actors, campaigns, and TTPs. Their platform helps you separate signal from noise.
VMRay TotalInsight
VMRay’s threat intelligence offering combines automated malware analysis with curated intelligence feeds. By continuously analyzing new threats in their sandbox environment, they generate fresh IOCs and behavioral signatures you won’t find in commodity threat feeds.
How to Choose the Right Platform for Your Environment
Not every organization needs every tool. Here’s how to think about building your zero-day detection stack:

Start With Your Use Cases
Are you primarily concerned with email-borne threats? Focus on strong sandbox integration with your email security gateway. Worried about ransomware? Prioritize EDR with automated response capabilities. Need to monitor cloud workloads? XDR platforms with native cloud visibility should top your list. Running web applications? Consider WAF solutions that understand application-layer attacks.
Consider Your Team’s Maturity
A small SOC with three analysts has different needs than a 50-person security operations center. Smaller teams benefit from platforms that automate triage and provide clear verdicts. Larger teams might want more granular control and investigation capabilities.
Test Detection Capabilities, Not Marketing Claims
Don’t take vendor word for it. Run proof-of-concept tests with real samples from your environment. The MITRE ATT&CK evaluations provide independent, transparent testing results that show how platforms perform against known adversary techniques.
Factor in Integration Complexity
A powerful tool that takes six months to integrate isn’t helping you now. Look for platforms with pre-built connectors to your existing infrastructure (SIEM, SOAR, ticketing systems, threat intelligence platforms). REST APIs are table stakes.
Building a Layered Zero-Day Defense Strategy
Here’s the uncomfortable truth: no single tool will catch every zero-day threat. (Anyone promising 100% protection is either lying or doesn’t understand the problem.) What works is defense in depth with multiple detection layers that catch different types of threats.
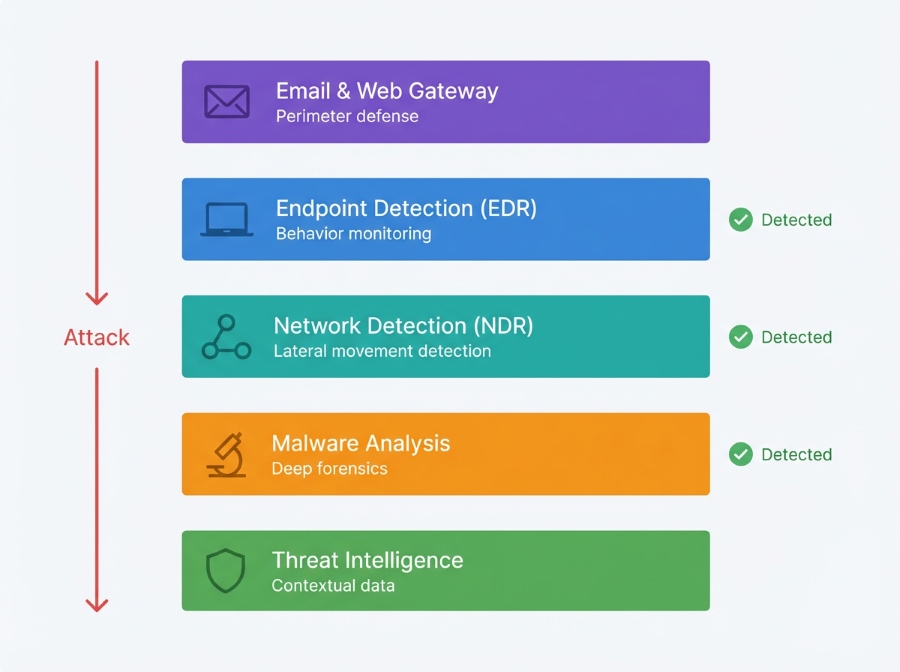
Layer 1: Email and Web Gateway Protection
Catch known threats and obvious phishing at the perimeter. Integrate sandbox analysis for suspicious attachments.
Layer 2: Endpoint Detection and Response
Monitor endpoint behaviors for signs of exploitation, persistence mechanisms, and post-compromise activities.
Layer 3: Network Detection and Response
Watch for lateral movement, command-and-control traffic, and data exfiltration that indicates an active breach.
Layer 4: Deep Malware Analysis
When something makes it through (and something will), you need the ability to perform forensic analysis, extract IOCs, and understand the full scope of what happened. This is where advanced sandboxing platforms like VMRay shine.
Layer 5: Threat Intelligence
Feed context from external threat intelligence into your detection layers so you can prioritize alerts based on real-world threat actor activity and emerging campaigns.
Common Pitfalls to Avoid
Over-relying on automation without understanding limitations: AI and machine learning are powerful, but they’re not magic. You still need skilled analysts who can investigate complex incidents and tune detection rules.
Treating blocked alerts as “mission accomplished”: When your EDR blocks a zero-day exploit, that’s not the end of the story. That’s the beginning of threat hunting. How did it get there? What else might be in your environment? Was this a targeted attack or opportunistic scanning?
Ignoring integration and workflow: A tool that doesn’t fit into your analysts’ workflows creates friction. Friction creates alert fatigue. Alert fatigue means real threats get missed.
Skipping regular testing: Threat actors evolve constantly. Test your detection capabilities regularly with frameworks like MITRE ATT&CK to identify gaps before attackers do.
What’s Coming in 2026 and Beyond
The zero-day detection landscape keeps evolving. Here’s what we’re watching:
AI-powered security operations: Platforms like Prophet Security and Splunk are building AI agents that can autonomously investigate alerts, correlate events, and even execute response actions (with appropriate guardrails).
Deeper cloud integration: As workloads move to AWS, Azure, and GCP, detection platforms are following. Expect tighter integration between traditional endpoint security and cloud-native security posture management.
Behavioral biometrics for user and entity behavior analytics: Moving beyond simple anomaly detection to understand normal patterns for specific users, devices, and applications so deviations stand out more clearly.
Automated threat intelligence generation: Instead of relying solely on commercial feeds, more organizations are generating their own threat intelligence by analyzing blocked attacks and sharing IOCs through platforms like MISP and OpenCTI. VMRay’s approach of automatically extracting behavioral indicators from sandbox analysis is a great example of this trend.
Final Thoughts: Detection Is Only Half the Battle
Having the right zero-day detection tools is essential — but tools alone aren’t enough. You also need skilled analysts who can investigate alerts, prioritize incidents, and carry out response playbooks. Clear processes must define escalation paths and decision-making authority, and regular testing is critical to ensure your defenses work as intended.
Think of detection tools as force multipliers for your team. They handle the heavy lifting (monitoring millions of events, analyzing file behaviors, correlating alerts across systems) so your analysts can focus on the complex investigations that require human judgment.
The best platform for your organization depends on your specific environment, threat model, and team capabilities. Start by understanding your biggest gaps, test platforms against real-world scenarios, and build detection layers that complement each other.
Because when that next zero-day drops (and it will), you want to be the team that spots it in minutes, not months.
如有侵权请联系:admin#unsafe.sh