Google issued an extra patch addressing two security vulnerabilities in Chrome, both of which can be triggered remotely by an attacker when a user visits a specially crafted, malicious web page.
Chrome is by far the world’s most popular browser, with an estimated 3.4 billion users. That makes it a massive target. When Chrome has a security flaw that can be triggered just by visiting a website, billions of users are exposed until they update.
That’s why it’s important to install these patches promptly. Staying unpatched means you could be at risk just by browsing the web. Attackers often try to exploit browser vulnerabilities quickly, before most users have a chance to update. Always let Chrome update itself, and don’t delay restarting it, as updates usually fix exactly this kind of risk.
How to update Chrome
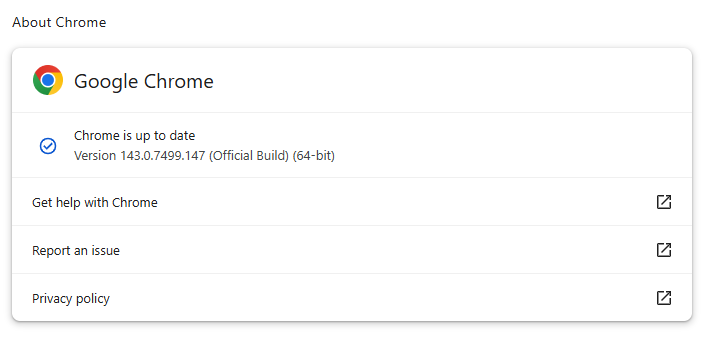
The latest version number is 143.0.7499.146/.147 for Windows and macOS, and 143.0.7499.146 for Linux. So, if your Chrome is on version 143.0.7499.146 or later, it’s protected from these vulnerabilities.
The easiest way to update is to allow Chrome to update automatically, but you can end up lagging behind if you never close your browser or if something goes wrong—such as an extension stopping you from updating the browser.
To update manually, click the More menu (three dots), then go to Settings > About Chrome. If an update is available, Chrome will start downloading it. Restart Chrome to complete the update, and you’ll be protected against these vulnerabilities.
You can also find step-by-step instructions in our guide to how to update Chrome on every operating system.
Technical details
One of the vulnerabilities was found in the WebGPU web graphics API, which allows for graphics processing, games, and more, as well as AI and machine learning applications. This vulnerability, tracked as CVE-2025-14765 is a use-after-free vulnerability that could allow a remote attacker to potentially exploit heap corruption via a crafted HTML page.
Use-after-free is a class of vulnerability caused by incorrect use of dynamic memory during a program’s operation. If, after freeing a memory location, a program does not clear the pointer to that memory, an attacker may be able to use the error to manipulate the program.
Heap corruption occurs when a program inadvertently damages the allocator’s view of the heap, which can lead to unexpected alterations in memory. The heap is a region of memory used for dynamic memory allocation.
The other vulnerability, known as CVE-2025-14766 was—once again—found in the V8 engine as an out-of-bounds read and write.
V8 is the engine that Google developed for processing JavaScript, and it has seen more than its fair share of bugs.
An out-of-bounds read and write vulnerability means an attacker may be able to manipulate parts of the device’s memory that should be out of their reach. Such a flaw allows a program to read or write outside the bounds the program sets, enabling attackers to manipulate other parts of the memory allocated to more critical functions. Attackers could write code to a part of the memory where the system executes it with permissions that the program and user should not have.
In this case, the vulnerability could be exploited when the engine processes specially crafted HTML content, such as a malicious website.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
