好的,我现在需要帮用户总结一篇文章的内容,控制在100个字以内。首先,我得仔细阅读用户提供的文章内容,理解其主要信息。 这篇文章是TG Soft CRAM的每周报告,关注意大利的恶意垃圾邮件活动。时间范围是从2025年12月1日到7日。报告指出,全球的恶意软件活动有所下降,但意大利的活动却增加了。主要涉及的恶意软件家族包括AgentTesla、PhantomStealer、Remcos、VIPKeylogger和XWormRAT。 接下来,我需要提取关键点:报告的时间范围、全球和意大利活动的变化趋势、涉及的恶意软件家族以及主要的主题类型如支付、订单等。 然后,我要把这些信息浓缩成一句话,确保不超过100个字,并且不使用“文章内容总结”或“这篇文章”这样的开头。要直接描述文章内容。 最后,检查语言是否简洁明了,确保所有关键点都被涵盖。 </think> TG Soft CRAM报告指出,在2025年12月1日至7日期间,全球恶意垃圾邮件活动有所减少,但意大利相关活动增加。主要恶意软件家族包括AgentTesla、PhantomStealer等,主题多为支付、订单等。 2025-12-2 15:4:12 Author: www.tgsoft.it(查看原文) 阅读量:0 收藏
Weekly report by the TG Soft CRAM, concerning Italian malspam campaigns.
Below are the details of the campaigns released during from 01 December to 07 December 2025.
During the monitored week, global campaigns decreased compared to the previous week, while campaigns in Italian increased.The week was characterized by Password Stealer of the Familiies: AgentTesla, PhantomStealer, Remcos, VIPKeylogger, and XWormRAT.
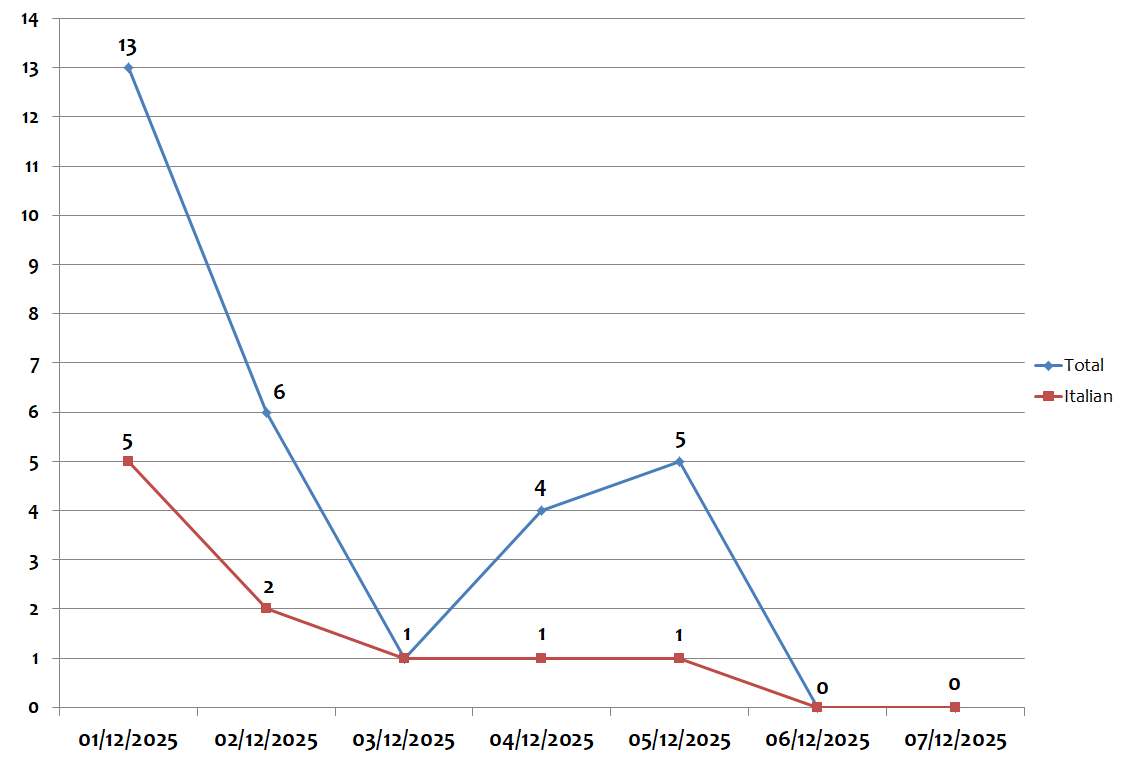
The blue bar shows the total number of campaigns monitored in Italy in each week, while the red bar concerns campaigns in Italian (and targeting Italy).
We monitored 29 campaigns during the week, 10 of which used Italian as their language.
In order to understand how the various weeks are divided, below is a small table showing the breakdown of the considered period:
| Week | from | to |
| Week_46 | 10/11 | 16/11 |
| Week_47 | 17/11 | 23/11 |
| Week_48 | 24/11 | 30/11 |
| Week_49 | 01/12 | 07/12 |
During the week, the peak in global campaigns was recorded on Monday 01 December, with 13 different campaigns per day. The peak in Italian campaigns was recorded on Monday 01 December, with 5 campaigns per day, as shown in the graph below:
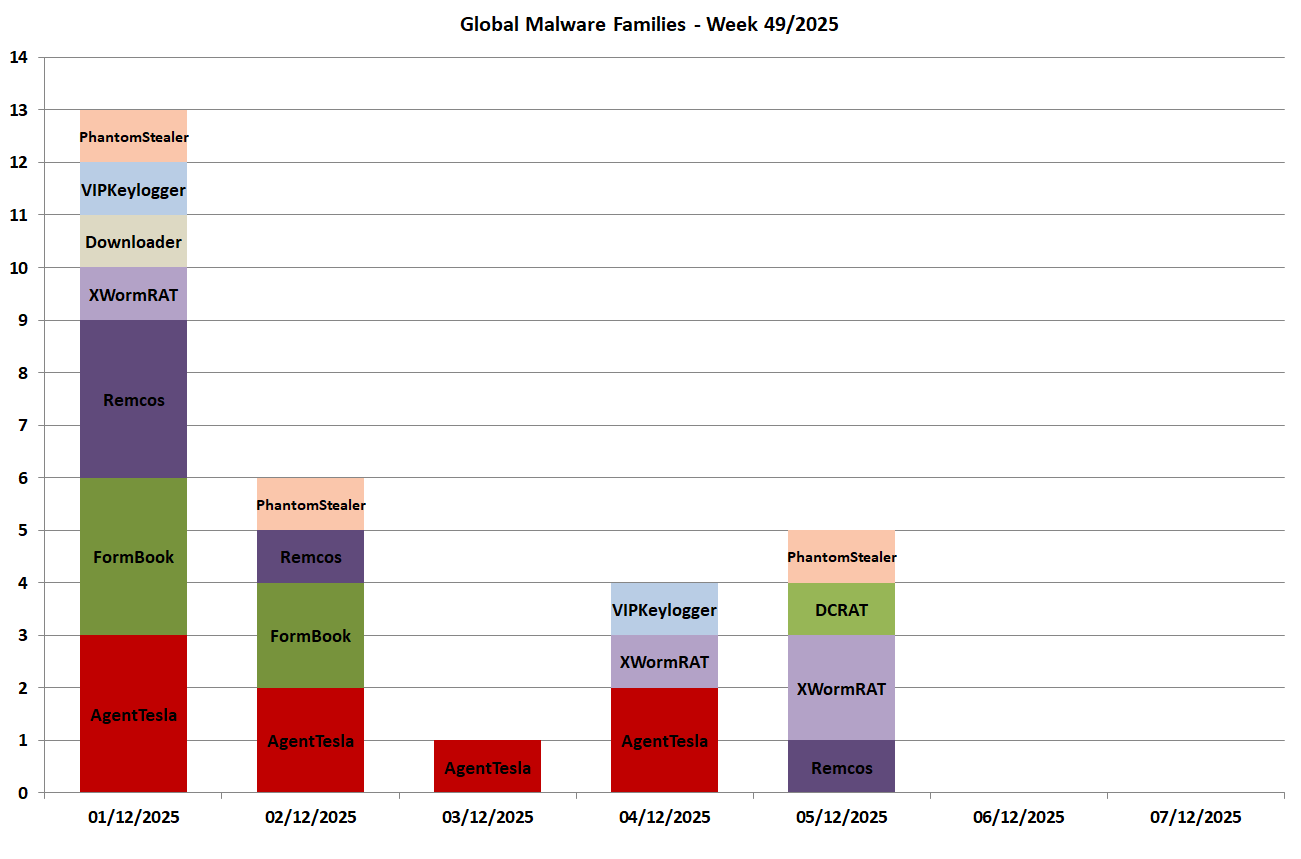
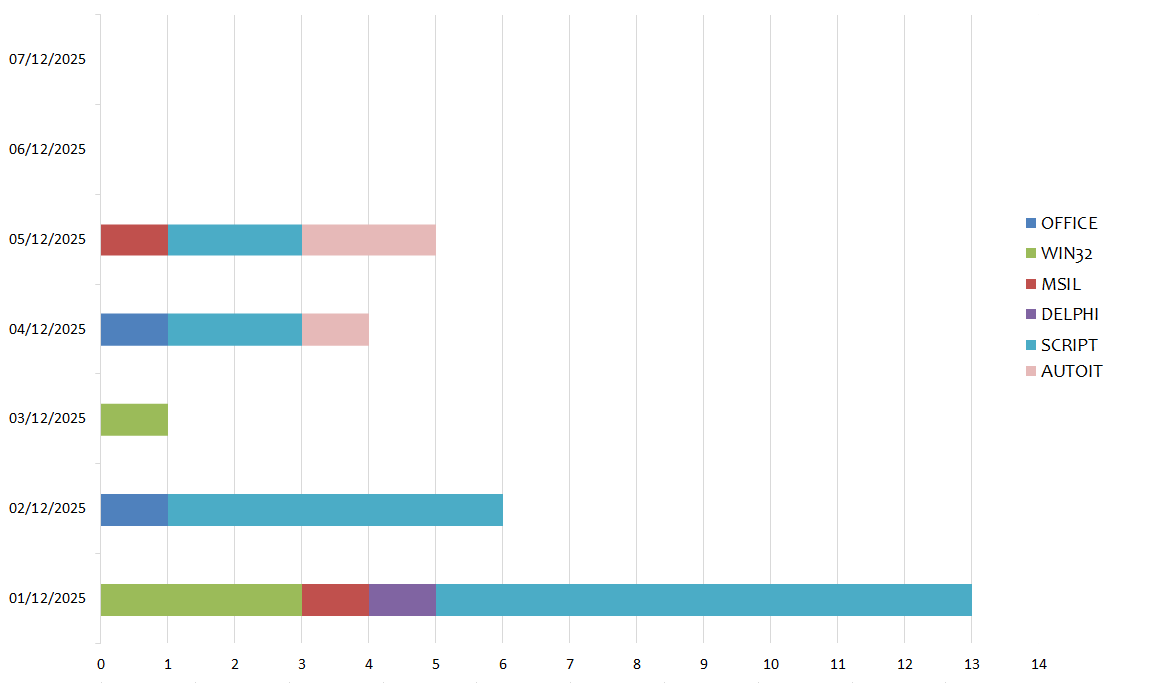
In the following chart we see the malware families spread globally for each day of the week:
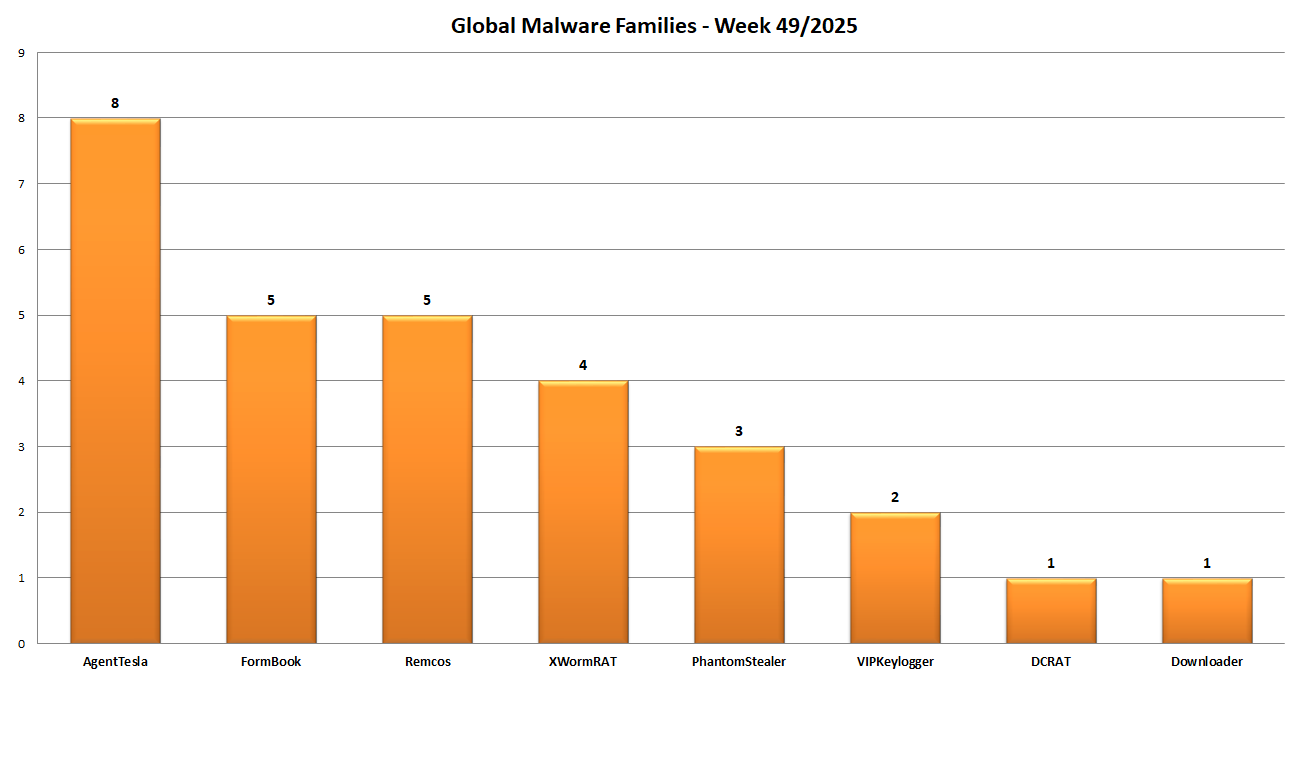
Instead in this graph we see the distribution based on malware family. In the past week 8 different families were detected:
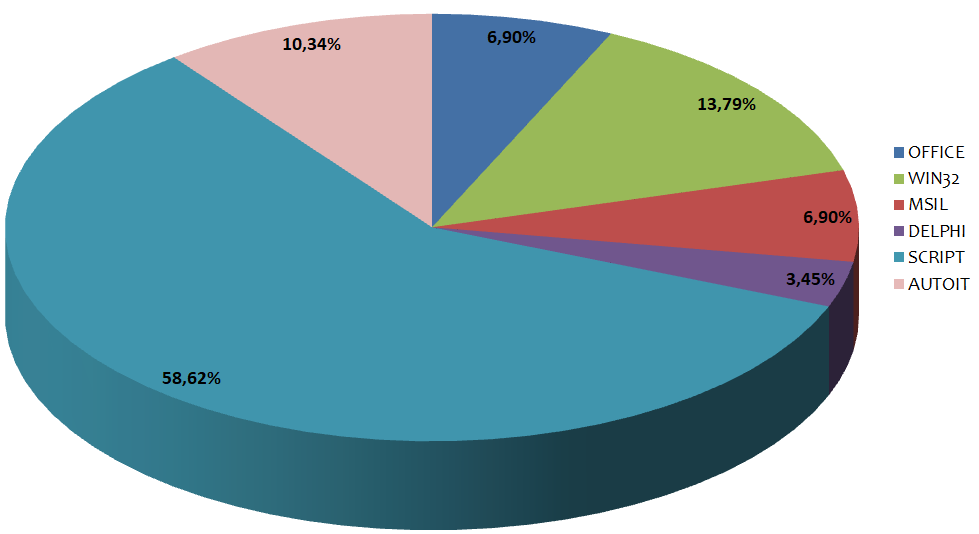
The samples that ranked first this week are Script files with 58.62%.
In second place are WIN32 executable files with 13.79%.
In third place are AutoIT executable files with 10.34%.
In the chart below we can see the various types of language used to develop malware:
In the following graph we see the distribution of the various types of languages divided by day:
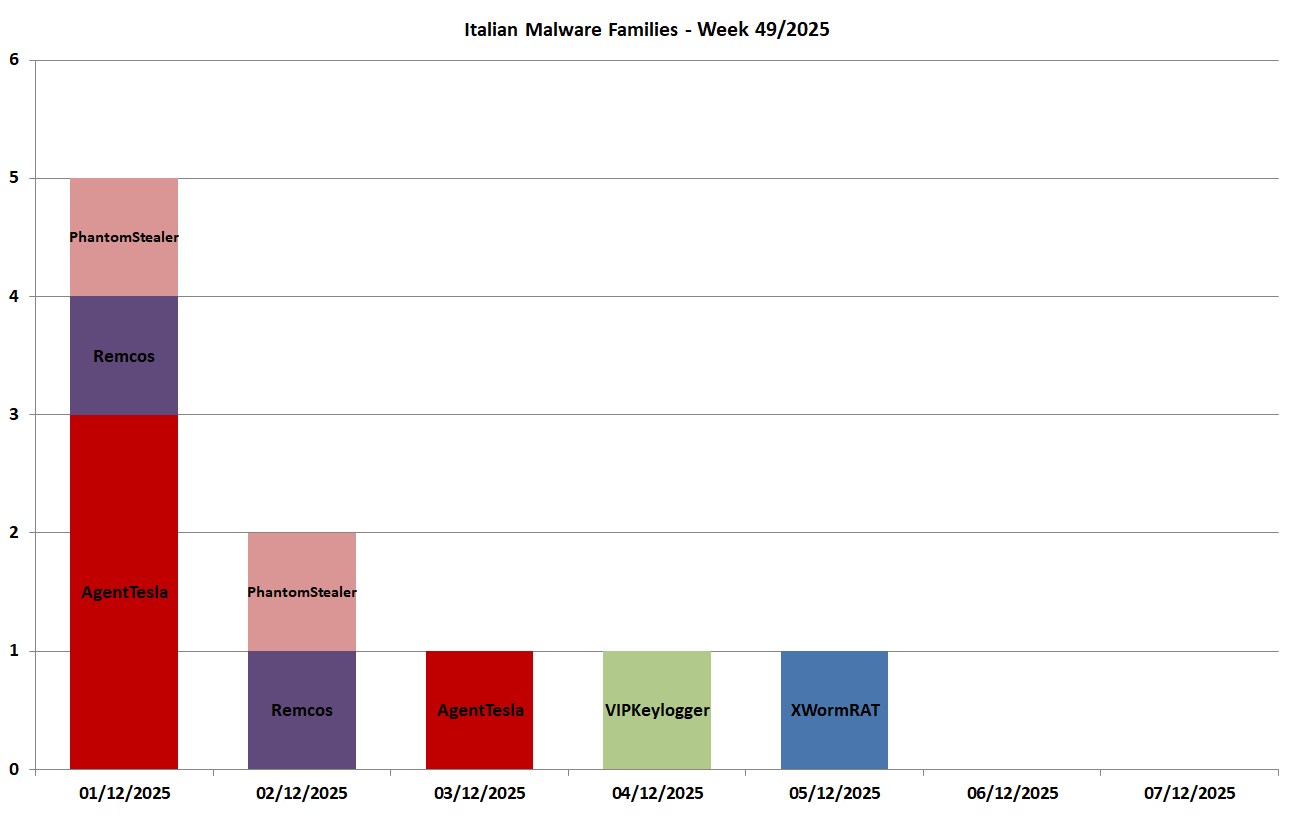
In this graph we can see the malware families spread during the week with target Italy (in Italian) and composed of 5 families:
The Italian campaigns analyzed by the TG Soft C.R.A.M. were grouped according to macro categories, obtained from the subject of the email message used for malware distribution (malspam). Below we see the subjects used in the various campaigns divided by day and type of malware.
01/12/2025
AgentTesla - spread through 3 campaigns, the first themed "Payments", the second themed "Purchases" and the third themed "Orders".
PhantomStealer - spread through a campaign themed "Payments".
Remcos - spread through a campaign themed "Payments".
02/12/2025
PhantomStealer - spread through a campaign themed "Receipts".
Remcos - spread through a campaign themed "Payments".
03/12/2025
AgentTesla - spread through a campaign themed "Orders".
04/12/2025
VIPKeylogger - spread through a campaign themed "Orders".05/12/2025
XWormRAT - spread through a campaign themeda "Payments".
Check out the November campaigns
We invite you to check out the November 2025 reports, to stay up-to-date on the malspam campaigns circulating in Italy:
Any information published on our site may be used and published on other websites, blogs, forums, facebook and/or in any other form both in paper and electronic form as long as the source is always and in any case cited explicitly “Source: CRAM by TG Soft www.tgsoft.it” with a clickable link to the original information and / or web page from which textual content, ideas and / or images have been extrapolated.
It will be appreciated in case of use of the information of C.R.A.M. by TG Soft www.tgsoft.it in the report of summary articles the following acknowledgment/thanks “Thanks to Anti-Malware Research Center C.R.A.M. by TG Soft of which we point out the direct link to the original information: [direct clickable link]”
如有侵权请联系:admin#unsafe.sh