Model Context Protocol (MCP) 是连接 AI 代理与企业工具的行业标准协议,在一年内迅速发展为关键基础设施。然而,其身份验证问题可能导致企业面临安全风险和合规挑战。解决这一问题需选择合适方案:自行开发、使用通用认证服务或采用专门针对 MCP 的解决方案。 2025-12-12 19:34:37 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
The Model Context Protocol (MCP) went from Anthropic's internal project to industry standard in just twelve months. Now governed by the Linux Foundation, backed by OpenAI, Google, Microsoft, and AWS, and downloaded over 97 million times monthly, MCP has become the universal language for connecting AI agents to your enterprise tools.
But here's what the hype cycle isn't telling you: MCP has an authentication problem, and it's one that could derail your AI agent initiatives before they start.
This guide breaks down what MCP is, why authentication is the critical gap, and what your options are for solving it.
What Is MCP and Why Should You Care?
The Model Context Protocol is an open standard that lets AI models—Claude, ChatGPT, Gemini, and others—connect to external tools and data sources through a unified interface.
Think of it as USB-C for AI agents. Before MCP, connecting an AI assistant to your GitHub, Slack, Salesforce, and databases required custom integrations for each combination. Ten AI tools talking to twenty enterprise systems meant potentially 200 different connectors to build and maintain.
MCP changes that equation. Build a connector once, and any MCP-compatible AI agent can use it.
The Numbers That Matter
| Metric | Value |
|---|---|
| Monthly SDK downloads | 97+ million |
| Published MCP servers | 10,000+ |
| Major platform support | Claude, ChatGPT, Gemini, VS Code, Cursor |
| Governance | Linux Foundation (as of December 2025) |
What MCP Enables
When MCP works, it enables powerful workflows:
- An AI coding assistant that can read your codebase, create pull requests, and update Jira tickets—all in one conversation
- A sales assistant that pulls CRM data, drafts emails, and schedules meetings without switching contexts
- An operations bot that queries databases, generates reports, and posts summaries to Slack
The protocol defines three core primitives that AI agents can use:
- Tools — Functions the AI can invoke (create_issue, send_message, query_database)
- Resources — Data the AI can read (files, database records, API responses)
- Prompts — Pre-defined templates for common operations
The Authentication Gap: Why This Matters for Enterprises
Here's where it gets complicated.
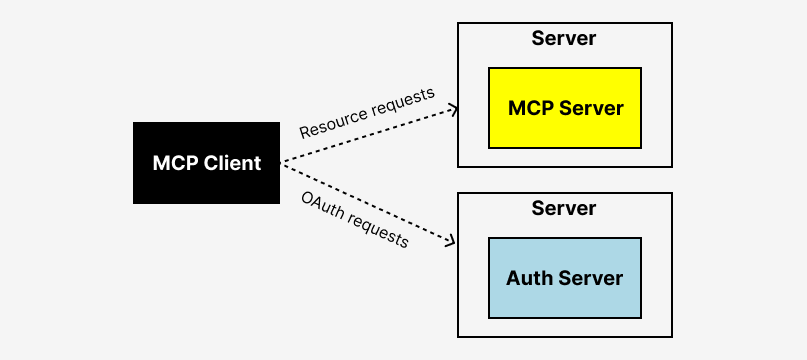
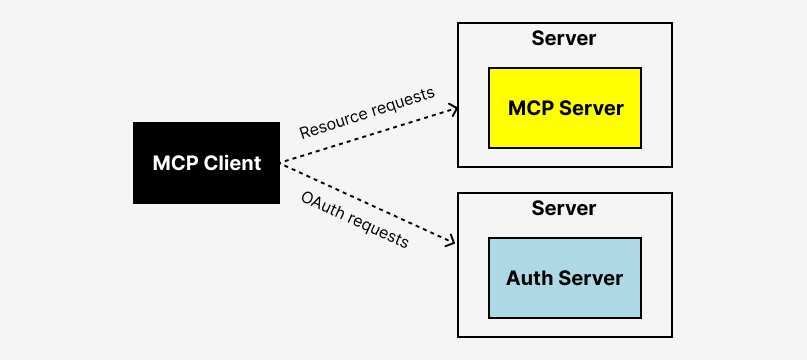
MCP excels at defining how AI agents talk to tools. What it doesn't solve—at least not natively—is who gets to have those conversations and under what conditions.
The Shadow IT Problem
Consider this scenario: An employee installs Claude Desktop and connects it to your company's Slack workspace using an MCP server. From Slack's perspective, there's a valid OAuth token making API calls. But from your identity provider's perspective—Okta, Azure AD, whatever you use—that AI agent connection is completely invisible.
Your IdP sees the user authenticate to Slack. It doesn't see the AI agent connection established afterward. There's no policy check, no audit trail, no way to revoke access to the AI connection without revoking access to Slack entirely.
Security teams call this Shadow IT. When your AI adoption scales beyond a few early adopters, it becomes Shadow IT at machine speed.
The Compliance Question
Every enterprise security questionnaire asks the same questions:
- How do users authenticate to your system?
- How do you integrate with enterprise identity providers?
- What audit trails exist for data access?
- How can we revoke access?
When the AI agent layer sits outside your identity infrastructure, the honest answers aren't good ones.
The Engineering Cost
The MCP authorization specification has evolved rapidly through 2025:
| Spec Version | Key Additions |
|---|---|
| March 2025 | OAuth 2.1 introduced |
| June 2025 | Resource Server separation, RFC 8707 support |
| November 2025 | Cross App Access (XAA), machine-to-machine flows |
Each revision brings new capabilities—and new implementation requirements. Engineering teams that built against the March spec found themselves refactoring for June. Those who waited until November faced a more complete but more complex specification.
Most teams estimate 6-12 weeks of dedicated engineering work to implement spec-compliant MCP authentication. That's 6-12 weeks not spent on your core product.
The Six Authentication Capabilities Enterprises Actually Need
Based on the current MCP specification and enterprise requirements, here's what a complete MCP authentication implementation requires:
1. OAuth 2.1 with PKCE
The foundation. PKCE (Proof Key for Code Exchange) prevents authorization code interception attacks. The MCP spec mandates it—there's no compliant path that skips this.
2. Dynamic Client Registration
AI agents need to register with authorization servers automatically. Manual client registration doesn't scale when you have dozens of MCP servers across your organization.
3. Protected Resource Metadata (RFC 9728)
MCP servers need to advertise their authorization requirements through standardized discovery endpoints. Without this, clients can't figure out how to authenticate.
4. Enterprise IdP Federation
The critical piece. MCP authentication needs to flow through your existing identity provider—Okta, Azure AD, Google Workspace, OneLogin—not around it. This is what gives your security team visibility and control.
5. Cross App Access (XAA)
Added in the November 2025 spec revision. XAA lets enterprise IdPs see and control agent-to-application connections, not just user-to-application authentication. This closes the Shadow IT gap.
6. Token Exchange for Machine-to-Machine Flows
AI agents operating autonomously (scheduled tasks, triggered workflows) need machine-to-machine authentication that doesn't require a human in the loop but still respects your security policies.
The Build vs. Buy Decision
You have three paths forward:
Option 1: Build In-House
Timeline: 6-12 weeks minimum
Team: 2-3 senior engineers with OAuth/identity expertise
Ongoing: Spec tracking, security patches, IdP updates
This makes sense if:
- Authentication is core to your product differentiation
- You have deep identity engineering expertise in-house
- You're comfortable tracking a rapidly evolving specification
The risk: The MCP spec is still maturing. What you build today may need significant revision as the protocol evolves.
Option 2: Use General-Purpose Auth Providers
Auth0, WorkOS, Stytch, and Descope have all released MCP-related offerings in 2025. These provide solid authentication infrastructure but typically:
- Charge per-user, which can be expensive for B2B SaaS with large enterprise customers
- Require meaningful integration work
- May not cover the full MCP authentication stack
Option 3: Use Purpose-Built MCP Authentication
This is the approach SSOJet has taken with our MCP authentication support, announced this week.
What we built:
- Complete MCP authentication stack (OAuth 2.1, PKCE, DCR, RFC 9728, XAA)
- Pre-built federation with major IdPs (Okta, Azure AD, Google Workspace, OneLogin)
- Connection-based pricing that doesn't penalize customer growth
- Deployment timeline measured in days, not weeks
Why we built it:
B2B SaaS companies kept asking us the same question: "Our enterprise prospects want AI agent support, but they also want SSO compliance. How do we deliver both without building an auth team?"
MCP authentication is a natural extension of what we already do—bridging the gap between B2B SaaS products and enterprise identity requirements.
What This Means for Your AI Strategy
The enterprises adopting AI agents fastest aren't the ones with the most sophisticated AI. They're the ones who've figured out how to make AI agents work within their existing security and governance frameworks.
If you're a B2B SaaS company:
- Enterprise customers are starting to ask about AI agent support
- The ones with mandatory SSO requirements (your best customers) will ask how it integrates with their IdP
- Having a compliant answer accelerates deals; not having one stalls them
If you're an enterprise IT leader:
- Your users are already connecting AI agents to your tools—with or without your visibility
- Bringing those connections under your identity infrastructure isn't optional
- The question is whether you do it proactively or reactively
If you're a CTO or VP Engineering:
- MCP authentication is solvable engineering work, but it's not trivial
- Every week your team spends on auth infrastructure is a week not spent on your product
- The build vs. buy math depends on whether identity is core to your differentiation
Getting Started
MCP isn't going away. The Linux Foundation governance, the industry backing, and the adoption numbers all point to MCP becoming permanent infrastructure—the way REST APIs became permanent infrastructure fifteen years ago.
The authentication gap is real, but it's solvable. The question is how you want to solve it.
If you're evaluating options:
- Audit your current AI agent connections—you likely have more Shadow IT than you think
- Map your enterprise customer requirements—what do their security questionnaires actually ask?
- Assess your engineering capacity—do you have 6-12 weeks of identity engineering expertise available?
- Evaluate the build vs. buy tradeoff honestly
If you want to talk to us:
SSOJet's MCP authentication support is available now for Business and Enterprise customers. We offer a free trial for qualified B2B SaaS companies evaluating enterprise SSO requirements.
→ Learn more at ssojet.com
→ Read the technical documentation
→ Contact our team
Key Takeaways
-
MCP is now critical infrastructure — With Linux Foundation governance and support from every major AI platform, MCP is the standard for AI agent connectivity.
-
Authentication is the gap — MCP defines how agents connect to tools, not how those connections integrate with enterprise identity. That's the problem you need to solve.
-
Shadow IT risk is real — AI agent connections that bypass your IdP create compliance and security exposure you can't see or control.
-
The spec is still evolving — Building in-house means committing to track and implement ongoing specification changes.
-
Time-to-market matters — Enterprise customers are asking about AI agent support now. Having a compliant answer is a competitive advantage.
SSOJet provides turnkey enterprise SSO integration for B2B SaaS companies, including support for MCP authentication. We help companies add enterprise authentication capabilities without building identity infrastructure in-house.
Ready to make your product AI-ready and enterprise-compliant?
Start your free trial →
*** This is a Security Bloggers Network syndicated blog from SSOJet - Enterprise SSO & Identity Solutions authored by SSOJet - Enterprise SSO & Identity Solutions. Read the original post at: https://ssojet.com/blog/what-tech-leaders-need-to-know-about-mcp-authentication-in-2025
如有侵权请联系:admin#unsafe.sh