好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。用户的要求很明确,直接写文章描述,不需要开头语。首先,我得仔细阅读文章内容,抓住关键点。 文章主要讲的是Gogs被零日漏洞攻击,导致700台服务器被黑。Gogs是一个自托管的Git服务,类似于GitHub。攻击者利用了一个未修补的漏洞CVE-2025-8110,实现了远程代码执行。这个漏洞是路径遍历问题,在PutContents API中存在。 Wiz的研究人员发现了这个漏洞,并且他们扫描发现有1400个暴露在互联网上的Gogs服务器,其中700多个被攻破。攻击者利用符号链接绕过了之前的防护措施,进而覆盖敏感文件并执行任意命令。 此外,研究人员指出攻击者使用了Supershell框架,并且Gogs管理员需要采取措施来缓解风险。漏洞在7月被报告,但到10月底才被承认,目前仍未修复。 现在我需要把这些信息浓缩到100字以内。重点包括:零日漏洞、700服务器被黑、Gogs的用途、漏洞细节、研究人员发现的情况、攻击方法以及管理员建议。 可能的结构是:首先说明事件和影响,然后简要描述漏洞和攻击方式,最后提到修复情况和建议。 这样组织起来应该能符合用户的要求。 </think> 黑客利用未修补的Gogs零日漏洞CVE-2025-8110远程控制代码执行,入侵约700台暴露于互联网的服务器。该漏洞源于PutContents API中的路径遍历问题,允许攻击者通过符号链接覆盖敏感文件并执行任意命令。研究人员发现大量暴露实例中过半数已被攻陷,建议管理员限制访问并检查可疑活动。 2025-12-11 21:29:59 Author: securityaffairs.com(查看原文) 阅读量:2 收藏
Critical Gogs zero-day under attack, 700 servers hacked
Pierluigi Paganini
December 11, 2025

Hackers exploited an unpatched Gogs zero-day, allowing remote code execution and compromising around 700 Internet-facing servers.
Gogs is a self-hosted Git service, similar to GitHub, GitLab, or Bitbucket, but designed to be lightweight and easy to deploy. It allows individuals or organizations to host their own Git repositories on their servers, offering features like version control, issue tracking, pull requests, and web-based repository management. Being self-hosted, it gives teams full control over their data and infrastructure.
Threat actors exploited an unpatched Gogs zero-day, tracked as CVE-2025-8110, to achieve remote code execution and compromise about 700 Internet‑exposed servers.
Wiz researchers discovered the flaw while investigating a malware infection on a customer workload.
The flaw, a path‑traversal issue in the PutContents API, lets attackers bypass protections added for a previous RCE bug (CVE‑2024‑55947) by abusing symbolic links. Although newer Gogs versions validate path names, they don’t check symlink destinations.
Threat actors can therefore create repositories containing symlinks to sensitive system files and use PutContents to overwrite files outside the repository.
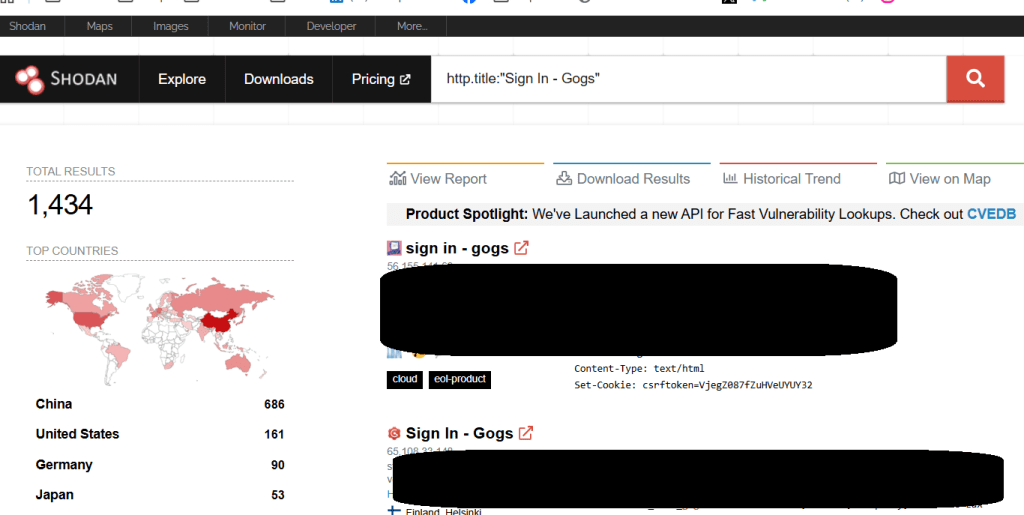
The researchers identified over 700 compromised instances public-facing on the internet.
“In our external scan, we identified over 1,400 Gogs servers publicly exposed to the internet. Many of these instances are configured with “Open Registration” enabled by default, creating a massive attack surface for the vulnerability described below.” reads the advisory published by Wiz.
The researchers explained that attack chain is simple for any user allowed to create repositories, which is enabled by default. An attacker creates a repo, commits a symbolic link to a sensitive file, then uses the PutContents API to write through that symlink, overwriting files outside the repository. By modifying .git/config, especially the sshCommand field, they can trigger execution of arbitrary commands. This flaw continues a recurring pattern in Gogs, where improper symlink handling has led to repeated exploitation in past vulnerabilities.
“Expanding our search via Shodan to review all exposed instances mentioned earlier, we found:
- ~1,400 total exposed instances
- 700+ confirmed compromised instances
In other words, over 50% of the exposed instances we observed showed signs of compromise.” continues the advisory.
All compromised Gogs instances showed a clear pattern: randomly generated 8-character owner/repo names created within the same short window on July 10, pointing to a single actor or group using the same automation tools.
Wiz discovered that attackers deployed malware built with Supershell, an open-source C2 framework that creates reverse SSH shells via web services. The infected systems communicated with a C2 server at 119.45.176[.]196.
Researchers reported the Gogs zero-day on July 17; maintainers acknowledged it only on October 30, however, the flaw has yet to be fixed. A second attack wave emerged on November 1. Gogs administrators are urged to disable open registration, restrict server access via VPN or allow lists, and check for compromise by reviewing suspicious PutContents API activity and repositories with random 8-character names.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, zero-day)
如有侵权请联系:admin#unsafe.sh
