嗯,用户让我总结这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”之类的开头。我得先仔细阅读文章,抓住主要信息。 文章主要讲的是欧盟的《网络安全弹性法案》(CRA),它从2024年12月10日开始生效。这个法案对制造商、进口商和分销商有严格的要求,比如产品设计必须考虑安全性,风险管理,漏洞管理,支持周期至少五年,还有必须报告漏洞和事件。Sekoia公司作为欧洲的网络安全技术提供商,他们分析了CRA的影响,并且介绍了他们如何帮助客户符合这些规定。 所以总结的时候,我需要涵盖CRA的主要内容和Sekoia的角色。控制在100字以内的话,得简洁明了。 可能的结构:欧盟通过CRA法案,要求制造商确保产品安全设计、风险管理、漏洞管理、支持周期至少五年,并报告漏洞和事件。Sekoia提供工具帮助客户合规。 这样大概就能在100字以内了。 </think> 欧盟通过《网络安全弹性法案》(CRA),要求制造商确保产品安全设计、风险管理、漏洞管理,并提供至少五年的支持周期。该法案还要求制造商及时报告漏洞和事件。Sekoia作为欧洲网络安全技术提供商,分析了CRA的影响,并提供工具帮助客户合规。 2025-12-11 08:16:57 Author: blog.sekoia.io(查看原文) 阅读量:11 收藏
Introduction
The European Union (EU) continues to solidify its cybersecurity landscape through ambitious, horizontal regulations. In addition to the NIS 2 Directive and the Digital Operational Resilience Act (DORA), the Cyber Resilience Act (CRA) establishes a comprehensive framework aimed at securing products with digital elements (PDEs) placed on the internal market.
The CRA, which entered into force on December 10, 2024, addresses two major concerns: the historically low level of cybersecurity in digital products and the lack of accessible information for users to make secure choices. Its primary objective is to ensure that hardware and software products are developed with fewer vulnerabilities and that manufacturers uphold security throughout the product’s lifecycle.
At Sekoia, a leading European cybersecurity technology provider, we recognize the CRA as a fundamental shift toward accountability and resilience, complementing the existing requirements faced by critical entities under NIS 2 and DORA. This blog post serves as a preliminary implementation guide, designed to provide clarity on the CRA’s practical application. We begin by enumerating the known requirements, follow this with an internal assessment by checking these requirements against our current operational processes, and conclude by detailing which aspects of our solution can assist our customers in meeting specific CRA obligations.
At the end of the blogpost, enjoy also a short CRA quiz to test your knowledge!
The core mandate of the Cyber Resilience Act
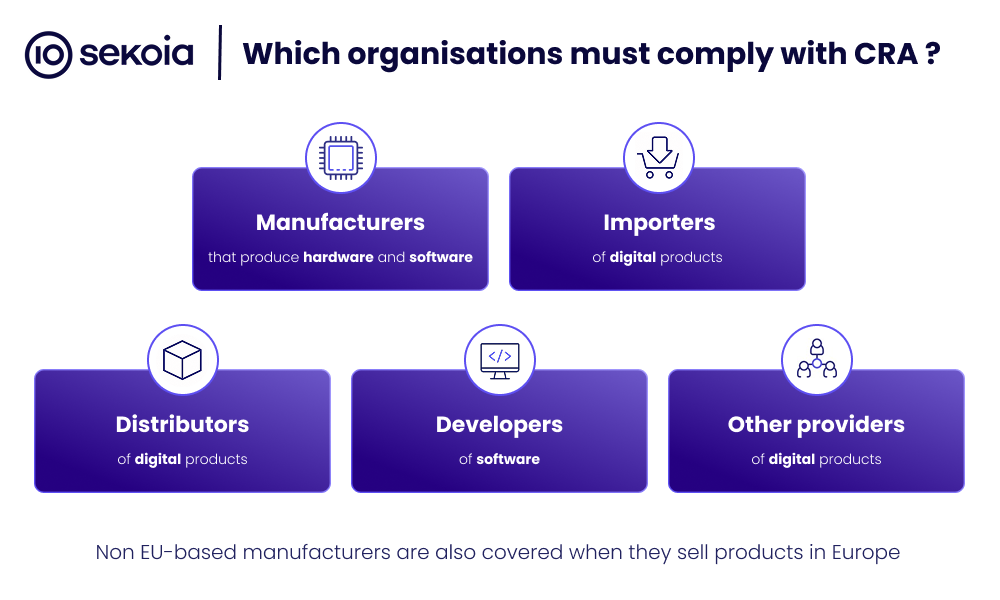
The CRA directly impacts manufacturers, importers, and distributors of products with digital elements (PDEs). It establishes essential cybersecurity requirements that must be met before a product is placed on the market, and maintained throughout its predetermined support period.

Key obligations for manufacturers include:
1. Security by design and risk assessment
Manufacturers must design, develop, and produce PDEs to ensure an appropriate level of cybersecurity based on identified risks. This mandatory cybersecurity risk assessment must be documented and continuously updated throughout the support period. Products must, where applicable, be made available without known exploitable vulnerabilities and include a secure by default configuration.
2. Comprehensive vulnerability management
A robust vulnerability handling process is mandatory. This includes identifying and documenting vulnerabilities and components, notably by producing a Software Bill of Materials (SBOM) in a machine-readable format. Manufacturers must address and remediate vulnerabilities without delay and provide security updates, generally free of charge, for the entire support period.
3. Defining the support period
Manufacturers must determine a support period reflecting the product’s expected use time. This period must be at least five years, unless the product’s expected lifetime is shorter. Security updates must be available throughout this period.
4. Mandatory reporting of incidents and vulnerabilities (VAEs)
A crucial provision, applicable starting September 11, 2026, mandates manufacturers to simultaneously notify actively exploited vulnerabilities (VAEs) and severe incidents impacting the product’s security:
- An early warning notification must be submitted within 24 hours of becoming aware of the VAE or severe incident.
- A comprehensive notification follows within 72 hours.
- A final report must be provided within 14 days (for VAEs after the fix is available) or one month (for severe incidents).
Notifications must be submitted via national CSIRT and the Single Reporting Platform (SRP) administered by ENISA- currently under development. For certain cases involving for instance national security and defense, delayed notifications are provided under specific conditions.
5. Conformity and certification
All products must undergo a conformity assessment and affix the CE marking before being placed on the EU market. Depending on the product’s criticality, this assessment may require third-party verification by a Notified Body or certification.

Sekoia’s position under the CRA
As a European-based cybersecurity company providing an AI SOC platform, Sekoia is directly concerned by the CRA. According to first analysis and pending further legal analysis, our offering falls under the definition of a PDE.
Based on the categorization criteria set out in Annex III of the CRA, Security Information and Event Management (SIEM) systems are specifically listed as Important Products, Class I. As our AI SOC platform is the fusion of SIEM, XDR, SOAR and CTI, this classification subjects Sekoia to stricter requirements regarding conformity assessment compared to general products, unless compliance is demonstrated through certification.
Among other products in the Important / Class I category are browsers, VPN, anti-malicious software, IAM, but also routers and operating systems… Important products Class II includes firewalls, IDPS and tamper-resistant microcontrollers, while Critical products are Hardware Devices with security boxes, smart meter gateways and smartcards (see Implementing regulation, Dec 2025).
Our first internal assessment indicates that Sekoia already adheres to many of the new obligations introduced by the CRA, due to previous regulatory and compliance works (ISO72001, SOC2, PCI, NIS2, etc). Our existing governance and platform controls, underpinned by strict standards, ensure robustness:
- Established security assurance: Sekoia maintains certifications such as ISO27001 and PCI-DSS, which demonstrates compliance with rigorous cybersecurity rules, particularly those derived from the banking sector.
- Vulnerability disclosure: We maintain a continuous vulnerability reporting process and have an internal CERT supporting vulnerability management.
- Transparency: Our commitment to transparency (see
trust.sekoia.io) means we already publish comprehensive documentation and maintain an effective vulnerability management program, aligning with the CRA’s requirements for technical documentation and coordinated vulnerability disclosure (CVD) policies.
Note that as of December 2025, we are still waiting for the implementation details for some of the requirements
How Sekoia.io empowers CRA compliance
Sekoia’s unified cybersecurity platform is designed to provide the necessary tools and processes for manufacturers to meet and maintain the stringent obligations of the CRA, particularly in incident response and vulnerability handling.
1. Meeting mandatory reporting deadlines (24/72h)
The requirement for an early warning notification within 24 hours is perhaps the most immediate operational challenge for manufacturers. To meet this, speed and accuracy in detection are paramount.
- Rapid detection (MTTD): Our AI SOC Platform ensures real-time monitoring and detection of security events. This drastically reduces the Mean Time to Detect (MTTD), providing manufacturers with the necessary performance indicators and technical clarity to comply with the tight 24-hour reporting window.
- Automated response (SOAR): The integrated SOAR features facilitates the automation of playbooks and incident response processes. This helps manufacturers categorize incidents (especially VAEs) swiftly, collect evidence, and initiate mitigation measures, enabling the timely preparation of the required formal notifications and reports to the designated CSIRT and ENISA.
2. Enhancing risk assessment and supply chain resilience
The CRA mandates continuous risk assessment, particularly concerning components sourced from third parties and known vulnerabilities.
- Actionable Threat Intelligence (CTI): Sekoia Intelligence provides contextualized Indicators of Compromise (IOCs) and high-quality threat reports derived from Sekoia Threat Detection & Research (TDR) team. This intelligence offers a comprehensive perspective for manufacturers (strategic and operational levels) to better understand the risks faced by their PDEs and components.
- Testing resilience: For organizations that fall under both CRA and other regulations (like DORA in the financial sector), our CTI is crucial. It supports threat-led penetration testing (TLPT/Red Teaming), ensuring that attack simulations are based on relevant identified threats, thereby validating product resilience against real-world adversaries.
3. Supporting robust vulnerability management
The CRA’s Part II Annex I mandates effective and timely vulnerability management, including regular security tests and sharing information about vulnerabilities.
- Testing and review: Our platform supports security testing and reviews by providing rich data (logs, events) and detection capabilities that continuously monitor and log relevant internal activities for security purposes.
- Information sharing: Sekoia facilitates the sharing of threat information by modeling data using standardized frameworks like ATT&CK and STIX, making incident reporting and collaboration with authorities and partners easier, a core goal of the CRA and NIS 2.
Conclusion: A partner in cyber resilience
The Cyber Resilience Act reinforces the principle that cybersecurity is a collective responsibility, starting at the product level. By imposing clear security-by-design and vulnerability handling requirements, the CRA elevates trust in the digital products that underpin the EU economy.
For manufacturers navigating the CRA, particularly those developing complex systems like SIEM/SOC platforms classified as Important Products, Sekoia.io is committed to leading by example in compliance while providing powerful tools that integrate into your security development lifecycle.
Our next-generation AI SOC Platform and CTI capabilities offer immediate, tangible benefits in meeting the CRA’s stringent operational demands—from achieving ultra-fast detection metrics essential for the 24-hour reporting mandate, to informing the robust risk assessments required throughout the minimum five-year product lifecycle.
Partner with Sekoia to ensure not just compliance, but genuine cyber resilience, reinforcing the security of your digital supply chain.
Bonus Quiz: Test your knowledge on the CRA!

Ready to assess your understanding of the new EU regulations for digital product security? Answer these five questions based on the key mandates of the CRA.
Question 1: What is the primary purpose of the Cyber Resilience Act (CRA)?
Correct Answer: A. Of course, B refers to DORA and C to the NIS 2 Directive.
Question 2: Which CRA product category specifically includes core network protection systems such as Firewalls ?
Correct answer: C. Important Class II products, due to their cybersecurity-related function, carry a significant risk of adverse effects in terms of disruption or damage. Important Products, Class I include devices such as Security Information and Event Management (SIEM) systems but also VPN or browsers.
Question 3: What is the mandatory maximum timeframe for a manufacturer to submit an early warning notification regarding an actively exploited vulnerability or a severe incident impacting the product’s security?
Correct answer: C. The manufacturer must submit an early warning notification (alerte précoce) of an actively exploited vulnerability (VAE) or severe incident without undue delay, and in any event within 24 hours of becoming aware of it. This initial alert must be followed by an incident notification within 72 hours.
Question 4: What is the minimum support period during which manufacturers must ensure effective vulnerability handling and provide security updates for a Product with Digital Elements?
Correct answer: B. The manufacturer must determine the support period to reflect the time the product is expected to be in use. The support period shall be at least five years, unless the product is expected to be in use for less than five years, in which case the support period must correspond to that expected use time. Manufacturers must handle vulnerabilities effectively and in accordance with the essential requirements throughout this support period.
Question 5: Which crucial component of product transparency and supply chain security does the CRA mandate manufacturers to create and keep updated?
Correct answer: C. Manufacturers must identify and document vulnerabilities and components contained in products, including by drawing up a Software Bill of Materials (SBOM) in a commonly used and machine-readable format. (While B and D are also required, the SBOM is the document explicitly focused on detailing software components for supply chain transparency.)
Congratulations for completing the quiz! Would you like to discuss on the CRA, and better understand how Sekoia can support your compliance journey? Contact our experts today by clicking here.
Read also
- Official legal text, summary and FAQ from the European Commission.
- White papers on the CRA from the European Cybersecurity Organization (EU) and Alliance pour la Confiance Numérique (France).
- Navigating the NIS2 Directive: Key insights for cybersecurity compliance and how Sekoia.io can help
- Navigating DORA: How Sekoia.io can support your compliance journey
Disclaimer: This article provides general insights into the Cyber Resilience Act (CRA) and how Sekoia’s services align with its objectives. Compliance requirements should always be verified against the official text of Regulation (EU) 2024/2847 and guidance from relevant national authorities.
如有侵权请联系:admin#unsafe.sh