好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。用户的要求是直接写文章描述,不需要特定的开头。 首先,我得仔细阅读文章内容。文章讲的是一个名为DroidLock的新发现的安卓恶意软件。它能锁定屏幕索要赎金,并访问短信、通话记录、联系人等信息,甚至删除数据。 接下来,文章提到DroidLock通过VNC系统完全控制设备,并通过屏幕叠加窃取设备锁屏模式。研究人员指出,该恶意软件主要针对西班牙语用户,通过恶意网站分发伪装成合法应用的假应用。 感染过程开始于欺骗用户安装包含实际恶意软件的二次负载。恶意应用会请求设备管理权限和辅助功能服务权限,以执行欺诈活动,如擦除设备、更改PIN码或生物数据等。 分析显示,DroidLock支持15个命令,包括发送通知、静音设备、重置到出厂设置等。赎金信息通过WebView显示,威胁24小时内不支付就销毁文件。 虽然DroidLock不加密文件,但通过威胁达到勒索目的。此外,它还能窃取锁屏模式,并允许远程访问设备。Zimperium作为Google应用防御联盟成员,与安卓安全团队共享发现,Play Protect检测并阻止威胁。 最后,建议用户不要从非Google Play来源安装APK,并检查应用权限。 现在我需要将这些信息浓缩到100字以内。重点包括:恶意软件名称、功能(锁定屏幕、窃取信息)、传播方式(伪装应用)、攻击目标(西班牙语用户)、功能(15个命令、赎金威胁)、防范建议(不安装外部APK)。 确保语言简洁明了,直接描述内容。 </think> 一种名为DroidLock的新安卓恶意软件可锁定屏幕索要赎金,并窃取短信、通话记录等信息或删除数据。该恶意软件伪装成合法应用分发给西班牙语用户,并通过VNC系统远程控制设备。它支持15种操作命令,并利用WebView显示赎金信息威胁删除文件。专家建议用户避免从非官方渠道安装应用以防范此类威胁。 2025-12-10 22:0:22 Author: www.bleepingcomputer.com(查看原文) 阅读量:5 收藏

A newly discovered Android malware dubbed DroidLock can lock victims’ screens for ransom and access text messages, call logs, contacts, audio recordings, or even erase data.
DroidLLock allows its operator to take complete control of the device via the VNC sharing system and can steal the device lock pattern by placing an overlay on the screen.
According to researchers at mobile security company Zimperium, the malware targets Spanish-speaking users and is distributed through malicious websites promoting fake applications that impersonate legitimate packages.
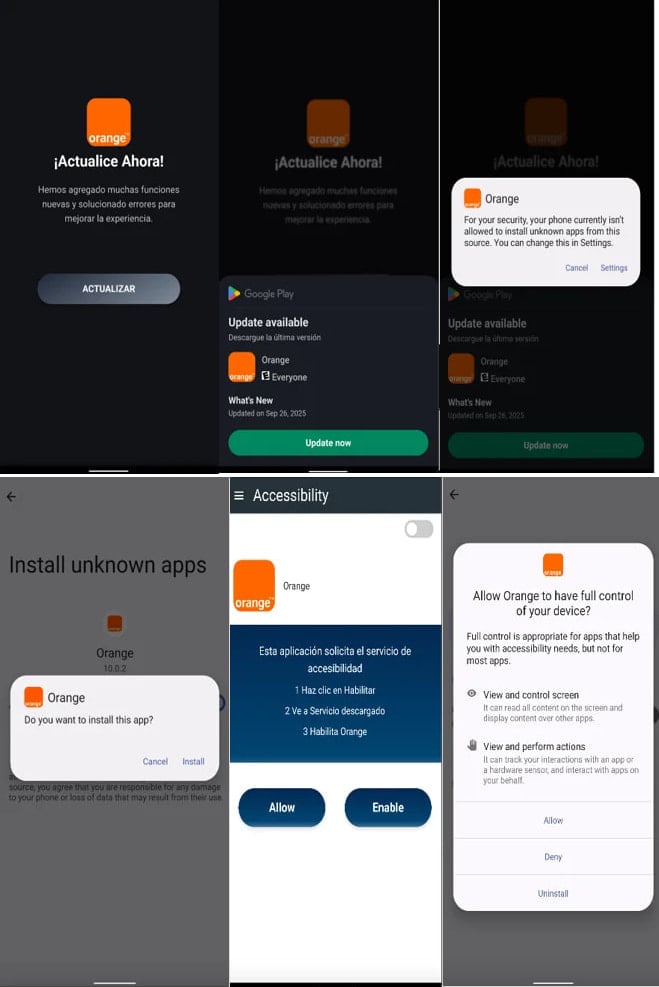
In a report today, Zimperium says that the "infection starts with a dropper that deceives the user into installing the secondary payload that contains the actual malware."
Source: Zimperium
The malicious apps introduce the main payload via an update request and then ask for Device Admin and Accessibility Services permissions, which let it to perform fraudulent activities.
Some of the actions it can take are wiping the device, locking it, changing the PIN, password, or biometric data to prevent the user from accessing the device.
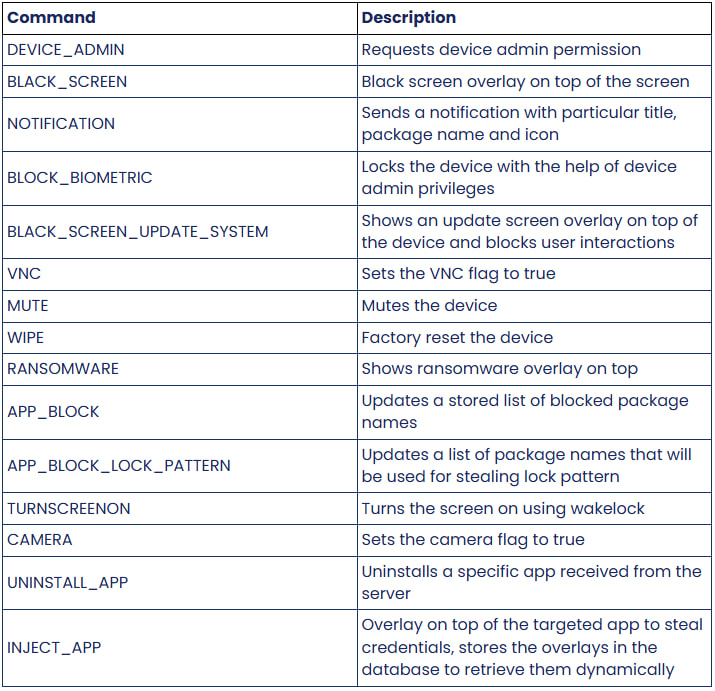
Zimperium's analysis discovered that DroidLock supports 15 commands that let it send notifications, place an overlay on the screen, mute the device, reset it to factory settings, start the camera, or uninstall apps.
Source: Zimperium
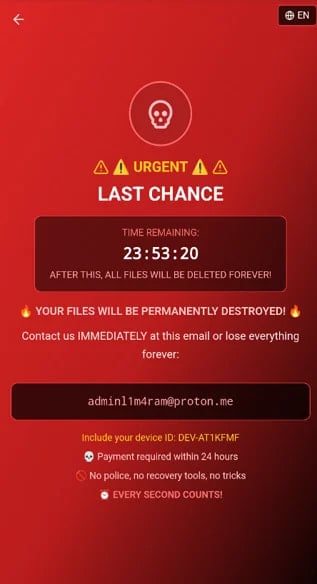
The ransomware overlay is served via WebView immediately after the corresponding command is received, instructing the victim to contact the threat actor at a Proton email address. If the user does not pay a ransom in 24 hours, the actor threatens to permanently destroy the files.
Source: Zimperium
Zimperium clarifies that DroidLock does not encrypt files, but by threatening to destroy them unless a ransom is paid, the same purpose is achieved. Additionally, the threat actor can deny access to the device by changing the lock code.
DroidLock can steal the lock pattern through another overlay loaded from the malicious APK's assets. When the user draws the pattern on the cloned interface, they send it directly to the attacker. The purpose of this feature is to allow remote access to the device through VNC at idle times.
Being a member of Google’s App Defense Alliance, Zimperium shares new malware findings with the Android security team, so Play Protect detects and blocks this threat from up-to-date devices.
Android users are advised not to side-load APKs from outside Google Play unless the publisher is a trusted source. They should always check if the permissions required by an app serve its purposes, and periodically scan their device with Play Protect.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh
