
嗯,用户让我用中文总结一篇文章,控制在100字以内,而且不需要特定的开头。我得先仔细阅读文章内容。 文章讲的是一个新的钓鱼工具包,叫Spiderman,专门针对欧洲多家银行和加密货币服务。它用高仿真的网站来欺骗用户。这个工具包能收集登录凭证、双重认证代码和信用卡数据。Varonis的研究人员分析了这个工具包,发现它针对五个国家的金融机构,包括德意志银行、ING等大品牌。还能用于金融科技公司如Klarna和PayPal的在线门户,以及 Ledger、Metamask等加密钱包的种子短语。 Spiderman是模块化的,可以添加新的银行和认证方法。研究人员发现它在犯罪分子中很受欢迎,在Signal上有一个群组有750成员。操作者可以通过控制面板实时监控受害者会话,捕捉凭证,导出数据,拦截PhotoTAN/OTP代码,并收集信用卡信息。 PhotoTAN是欧洲许多银行使用的OTP系统,用户需要扫描彩色马赛克图像来获取一次性密码。虽然捕捉PhotoTAN不是新功能,但对于针对欧洲机构的钓鱼工具包来说是必须的。 Varonis警告说,Spiderman收集的数据可能导致银行账户接管、SIM卡交换、信用卡欺诈和身份盗窃。建议用户确认在官方域名输入信息,并注意异常的短信或PhotoTAN提示。 总结的时候要抓住关键点:新钓鱼工具包Spiderman、目标对象、功能、模块化设计、受欢迎程度以及带来的风险。 控制在100字以内的话,可能需要精简一些细节。比如提到模块化设计和针对欧洲机构的功能。 最后总结成:介绍了一个名为Spiderman的新钓鱼工具包,专门针对欧洲多家银行和加密货币服务。该工具包利用高仿网站窃取登录凭证、双重认证代码及信用卡数据,并支持模块化扩展以适应不同目标机构的需求。 </think> 介绍了一个名为Spiderman的新钓鱼工具包,专门针对欧洲多家银行和加密货币服务。该工具包利用高仿网站窃取登录凭证、双重认证代码及信用卡数据,并支持模块化扩展以适应不同目标机构的需求。 2025-12-10 15:0:23 Author: www.bleepingcomputer.com(查看原文) 阅读量:1 收藏

A new phishing kit called Spiderman is targeting customers of numerous European banks and cryptocurrency services using pixel-perfect replicas of legitimate sites.
The platform allows cybercriminals to launch phishing campaigns that can capture login credentials, two-factor authentication (2FA) codes, and credit card data.
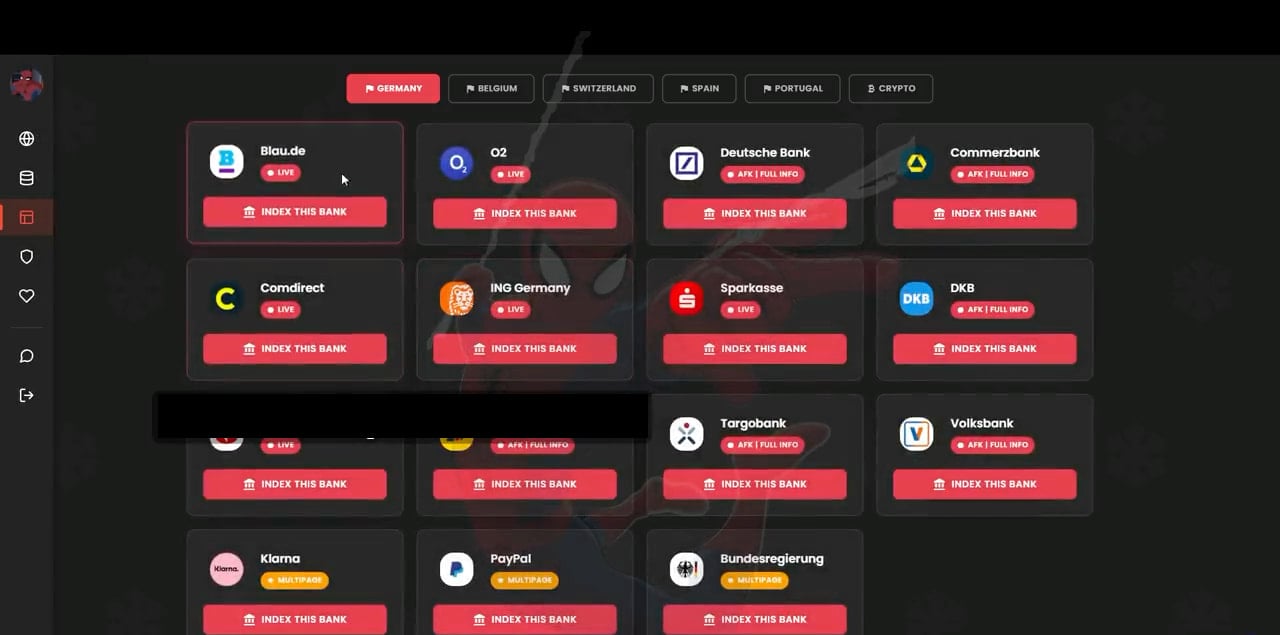
The Spiderman phishing kit, analyzed by researchers at Varonis, targets financial institutions in five countries, including major brands such as Deutsche Bank, ING, Comdirect, Blau, O2, CaixaBank, Volksbank, and Commerzbank.
The researchers observed that it can create phishing pages for online portals of fintech companies, such as the Swedish service Klarna and PayPal. It can also steal seed phrases for Ledger, Metamask, and Exodus cryptocurrency wallets.
Source: Varonis
“Because Spiderman is modular, new banks, portals, and authentication methods can be added. As European countries roll out updated e-banking flows, this kit will likely evolve in parallel,” Varonis says in its report.
The researchers found that Spiderman is popular among cybercriminals, with one of its groups on Signal counting 750 members.
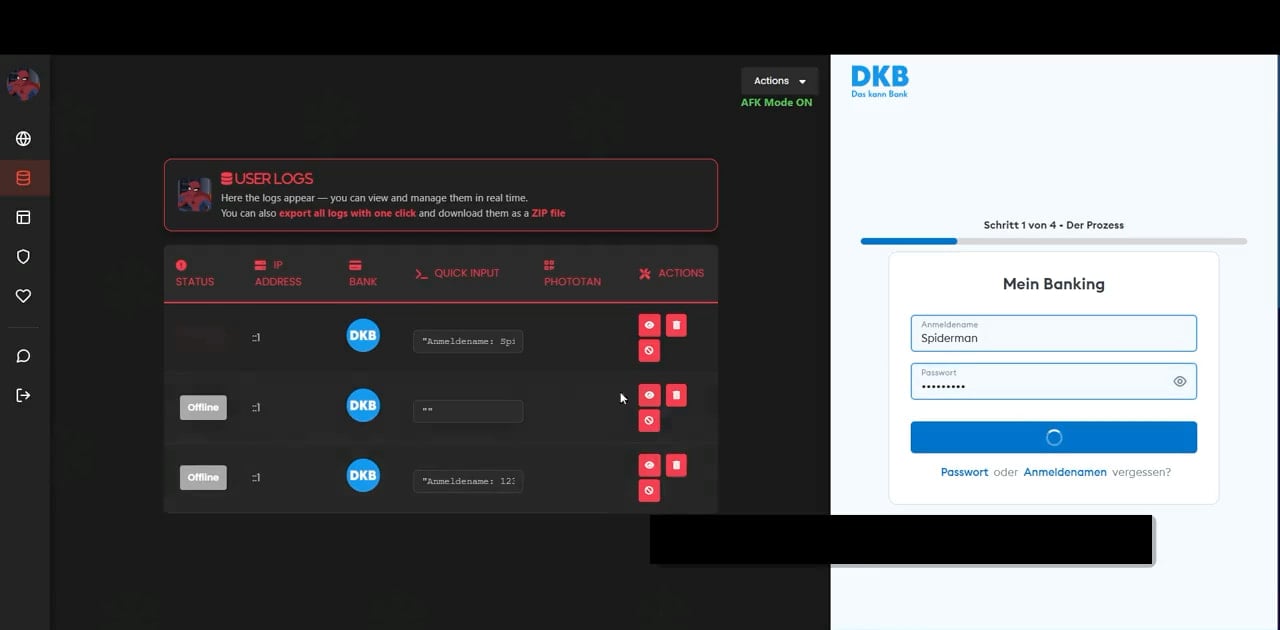
From the dashboard, operators can view victim sessions in real time, capture credentials, perform one-click data export, intercept PhotoTAN/one-time pass (OTP) codes in real time, and harvest credit card details.
Source: Varonis
PhotoTAN is an OTP system used by many banks in Europe, where a colored mosaic image is displayed during login or transaction approval steps, which the user must scan with the bank’s app to proceed.
The app decodes the mosaic and displays a transaction-specific OTP that must be entered back into the banking site.
Although PhotoTAN capture isn’t a novel feature in phishing kits, it is considered a “must-have” for platforms targeting European institutions.
Spiderman operators can configure their targeting scope from the control panel, limiting it to specific countries, adding ISP allowlisting, device-type filters (mobile or desktop users), and setting up redirects for visitors that don’t qualify for phishing attacks.
Varonis researchers warn that the data captured by Spiderman can lead to banking account takeover, SIM swapping, credit card fraud, and identity theft.
All phishing kits rely on victims clicking on a link that takes them to a fake login page, so the best protection is to always confirm you’re on the official domain before entering your credentials, and double-checking for browser-in-the-browser windows that could display the correct URL.
Receiving an SMS or PhotoTAN prompt on your device that is not linked to an action you made is a sign of a takeover attempt and should be reported to the bank immediately.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh
