Phishing used to be easy to spot. Now it looks clean, trusted, and almost perfect. Behind it are phishkits; ready-made attack platforms built to steal credentials, bypass MFA, and hijack live sessions in seconds.
For SOC teams, one click starts the countdown. What looks like a routine alert can already be a live account takeover.
Here’s how these attacks actually work, and how advanced SOC teams catch them before they spread.
What Is a Phishing kit?
A phishing kit, aka phishkit, is a ready-made toolkit that attackers use to launch phishing campaigns fast and at scale. Instead of building fake pages and infrastructure from scratch, they buy or rent a kit and deploy a full attack setup in minutes.
Most phishkits come with:
- Fake login pages for popular services
- Reverse proxy scripts to quietly intercept traffic
- Built-in MFA bypass
- Admin panels for harvesting credentials
- Tools to filter out bots and security scanners
What makes phishkits especially dangerous is how little skill they now require. Even low-experience attackers can run advanced phishing operations using these packaged platforms; with the infrastructure, automation, and data collection already built in.
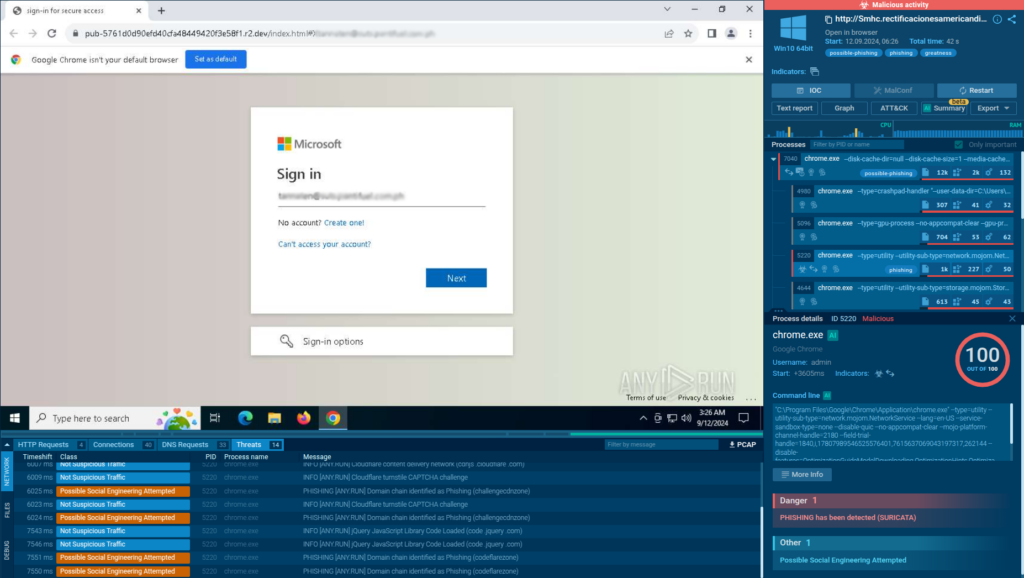
Detecting phishkits early comes down to understanding what happens after the click. With an interactive sandbox like ANY.RUN, analysts can safely open suspicious links, interact with phishing pages like a real user, and observe the full execution chain as it unfolds. This makes it possible to expose reverse proxy behavior, MFA capture, and credential theft in real time, often within seconds.
Why Phishkits Are So Dangerous for Businesses
Phishkits quietly remove the barriers that businesses rely on for protection. By sitting between the employee and the real service, these tools capture logins, MFA codes, and active sessions in real time. The result is immediate, legitimate-looking access to corporate systems.
Once attackers get inside, the impact spreads fast. A single compromised account can open access to email threads, internal tools, cloud platforms, customer data, and even financial systems. From there, attackers blend in, send messages from trusted inboxes, reset passwords, and move deeper without triggering obvious alarms.
What makes phishkits especially dangerous is how clean the entry point often looks. There’s no malware dropped right away or a suspicious attachment. Just a normal login that isn’t normal at all. This makes early detection hard and gives attackers valuable time to act before security teams even realize something is wrong.
For businesses, phishkits often lead to:
- Silent data leaks from email, cloud apps, and internal systems
- Business disruption caused by locked accounts and broken workflows
- Direct financial losses from fraud and unauthorized transactions
- Follow-up attacks launched from trusted employee inboxes
- Long investigations and recovery efforts that stretch on for weeks
- Reputational damage and loss of customer trust
Key Detection Challenges for SOC Teams
| Challenge | What It Looks Like in Practice | Why It’s a Problem |
|---|---|---|
| Clean phishing emails | Messages pass basic filters and look legitimate | No early warning at the email layer |
| Reverse proxy behavior | Users log in through a live proxy | Logs show a “normal” successful login |
| Short-lived domains | Phishing domains disappear quickly | Blocklists don’t update in time |
| Valid credentials & sessions | Attackers use real usernames, passwords, and MFA | No brute-force or obvious abuse signals |
| No malware at first stage | No attachment, no payload, just a web login | File-based detection is bypassed |
| Rapid attacker response | Access is used seconds after credentials are stolen | SOC has almost no reaction window |
How SOC Teams Can Detect Phishkit Attacks Faster
Speed matters with phishkits. The sooner a team can see the full phishing chain in action, the sooner they can contain access, block infrastructure, and stop the same kit from hitting more users. A fast investigation comes from combining interactive sandboxing with real-time threat intelligence.
Step 1: Send suspicious links straight to the sandbox
Instead of only blocking the URL, run it in an isolated environment to see what actually happens after the click, redirects, proxy behavior, and the final phishing page.
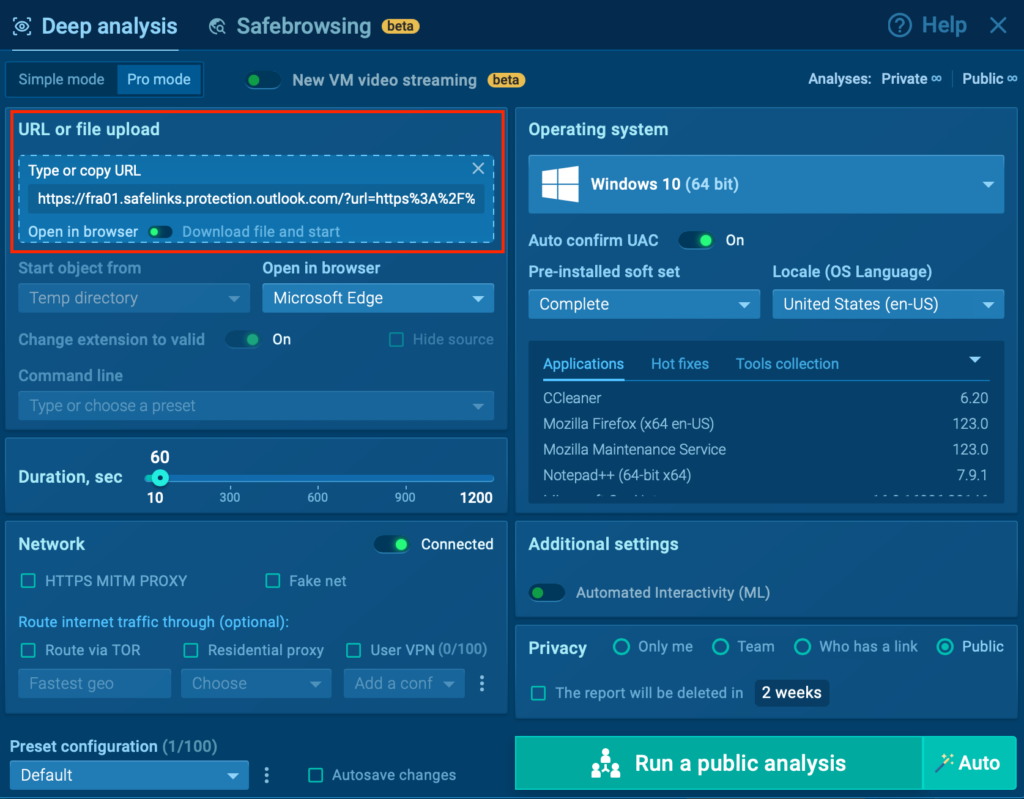
Step 2: Interact with the page like a real user
Phishkits stay quiet until someone behaves like a victim. Clicking buttons, entering test credentials, and moving through the flow helps trigger session theft, MFA capture, and hidden scripts.
Step 3: Watch the full chain unfold in real time
A live sandbox session shows every redirect, outbound connection, script call, and credential capture attempt, not just the final page.
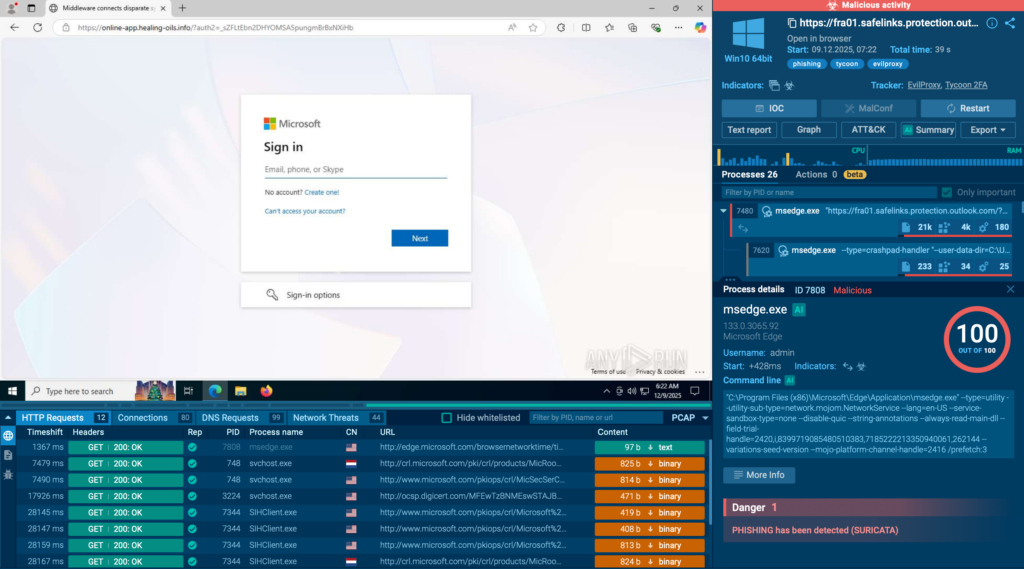
Step 4: Pull fresh IOCs as the attack runs
Domains, IPs, URLs, scripts, and proxy infrastructure can be extracted immediately and pushed into blocking rules and hunting queries.
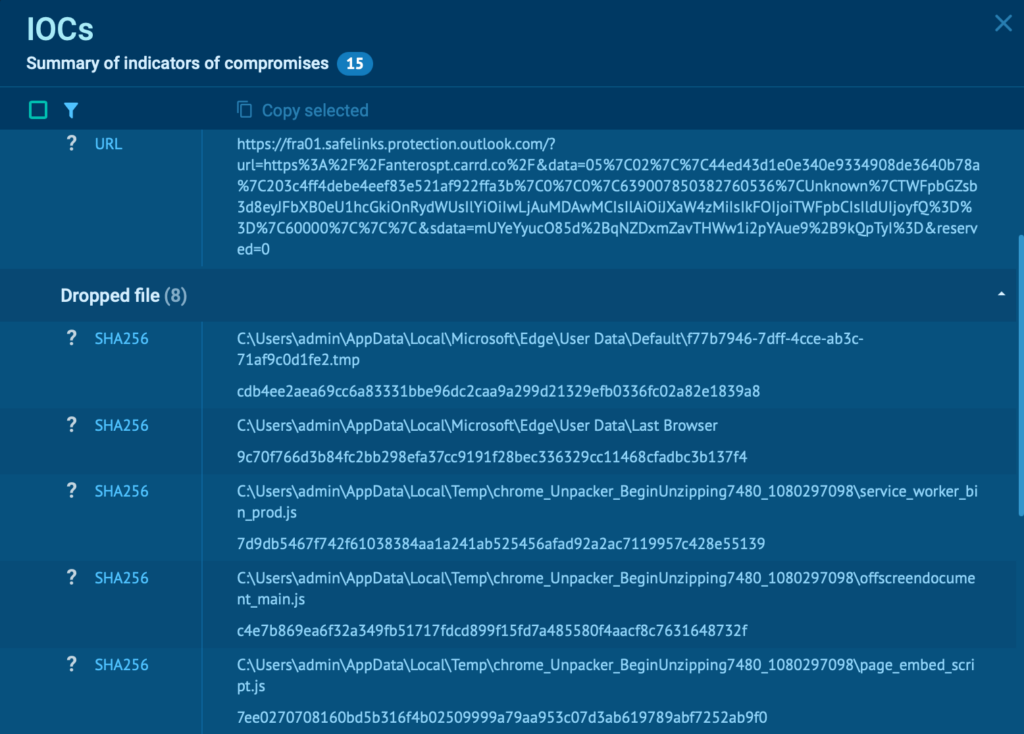
Step 5: Enrich indicators with TI Lookup
With ANY.RUN TI Lookup, analysts can instantly check whether the same domains, IPs, scripts, or redirect patterns were seen in past phishing or malware campaigns. This helps confirm phishkit families and link related activities.
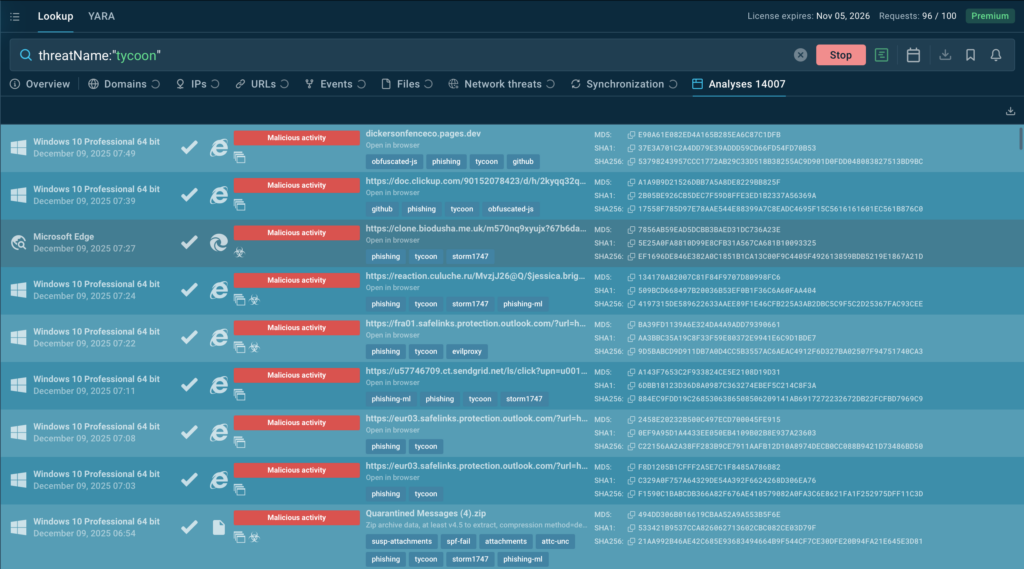
Using indicators from both the sandbox and TI Lookup, teams can quickly:
- Identify related infrastructure across past and current cases
- Detect active waves using the same phishkit
- Validate whether a campaign is isolated or part of a larger operation
This workflow turns phishing from a slow, reactive task into a fast, repeatable investigation process, with confirmation in minutes.
Step 6: Track new infrastructure with Threat Intelligence Feeds
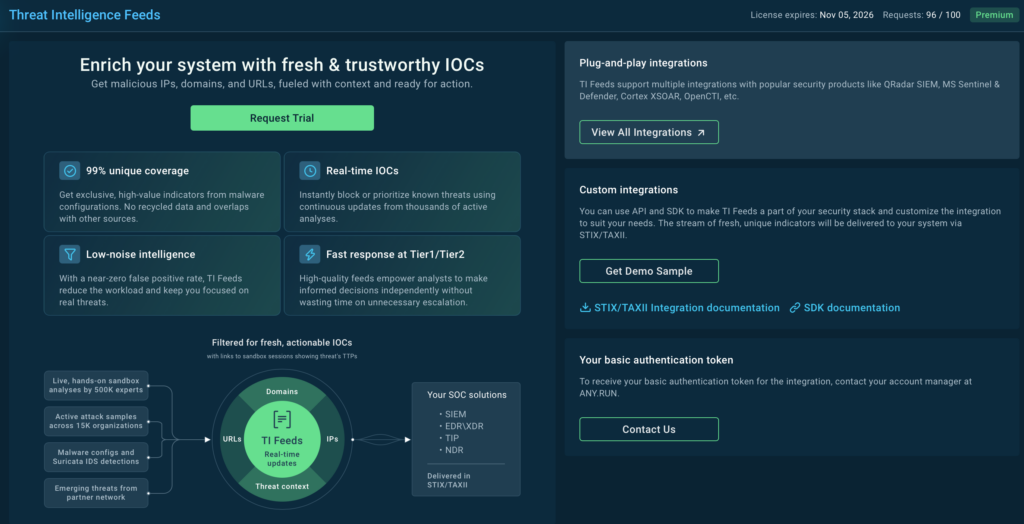
ANY.RUN’s Threat Intelligence Feeds deliver fresh, actionable indicators of compromise (IOCs) sourced directly from live attack data across 15,000 SOCs, ensuring your security infrastructure stays ahead of emerging threats.
With only 1% overlap with other sources, your team gains access to previously undiscovered threat intelligence that competitors miss. Every IOC comes enriched with detailed sandbox reports and contextual metadata, providing the forensic depth needed for rapid incident response and threat hunting. Real-time updates deliver a live view of the threat landscape as attacks unfold, enabling proactive defense before threats reach your perimeter.
Integration is seamless. TI Feeds connects directly to your existing SIEM, TIP, and SOAR platforms via popular standards (STIX/TAXII) or through dedicated API and SDK, minimizing implementation overhead while maximizing threat coverage across your entire security stack.
Real Phishkit Examples Analyzed inside the ANY.RUN Sandbox
The following examples come from real attacks and show how different phishkits operate in live environments:
TyKit: A Multi-Stage Microsoft 365 Phishkit in Action
TyKit is a multi-stage phishing kit built to steal Microsoft 365 credentials at scale. It spreads through malicious SVG files that silently redirect victims to fake login pages protected by CAPTCHA and anti-bot checks. Once credentials are entered, they’re sent straight to the attackers through a structured C2 API.
View analysis session with Tykit
The kit has been active since at least mid-2025 and has targeted organizations across finance, IT, government, telecom, and professional services worldwide. Its strength is simplicity: clean delivery, fast credential theft, and infrastructure that’s easy to rotate.
TyKit shows how modern phishkits don’t need malware to succeed, just one clean login flow is enough.
Tycoon 2FA: A Phishkit Built to Bypass MFA
Tycoon 2FA is a phishing-as-a-service platform designed to steal Microsoft 365 and Gmail accounts even when MFA is enabled. It works as an adversary-in-the-middle (AiTM) kit, using a reverse proxy to capture credentials, MFA codes, and active session cookies in real time.
View real attack exposed inside ANY.RUN sandbox
What sets Tycoon 2FA apart is its constant evasion upgrades. Over time, it has added:
- Rotating CAPTCHA systems
- Browser and sandbox fingerprinting
- Multi-layer obfuscation (Base64, XOR, AES)
- Fake 404 pages and legitimacy checks
- Long redirect chains to hide the true entry point
Once access is captured, attackers log in using a fully valid session. From a SOC view, it often looks like a normal user login until damage is already unfolding.
Mamba2FA: A Persistent Corporate Phishkit
Mamba2FA is a widely used phishkit built to steal corporate credentials, with repeated campaigns observed against organizations in the finance and manufacturing sectors. Like TyKit and Tycoon, it relies on clean phishing flows, fast infrastructure rotation, and live credential capture to move quickly before defenders can react.
What makes Mamba2FA especially useful as an example is how clearly it shows the value of tracking phishkits as ongoing campaigns, not one-off incidents. If your organization has already encountered a specific kit, the worst mistake is treating it as “closed.”
Using ANY.RUN’s Threat Intelligence Lookup, analysts can instantly surface:
- New sandbox analyses tied to the same phishkit
- Fresh phishing domains and URLs
- Recently reused infrastructure and scripts
To find recent Mamba2FA activity, teams can use a simple query like:
threatName:”mamba” AND domainName:””
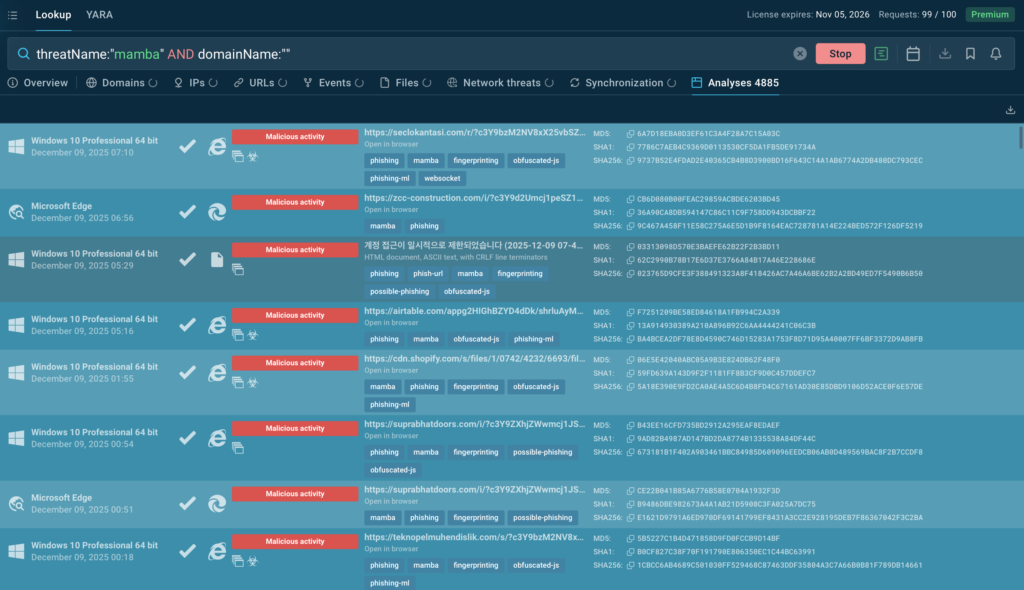
This immediately reveals both new attacks and network indicators observed during live sandbox analysis.
Instead of chasing isolated alerts, this approach turns phishkits like Mamba2FA into continuously monitored threats, making it much easier to spot repeat campaigns early and shut them down faster.
Phishkit Evolution: Hybrid Threats
Phishkits are no longer operating in isolation. One of the most worrying shifts is the rise of hybrid phishing chains, where multiple kits are combined into a single attack. These blended campaigns mix different infrastructures, redirect logic, and credential-theft methods to make detection and attribution far more difficult.
In recent enterprise-focused attacks, analysts have observed Tycoon 2FA and Salty working together in the same chain. One kit handles the initial lure and proxying, while the other takes over at later stages for credential capture, session hijacking, or follow-up delivery. For SOC teams, this breaks many traditional assumptions about how a “single” phishing campaign should look.
Check real-world analysis with Tycoon and Salty
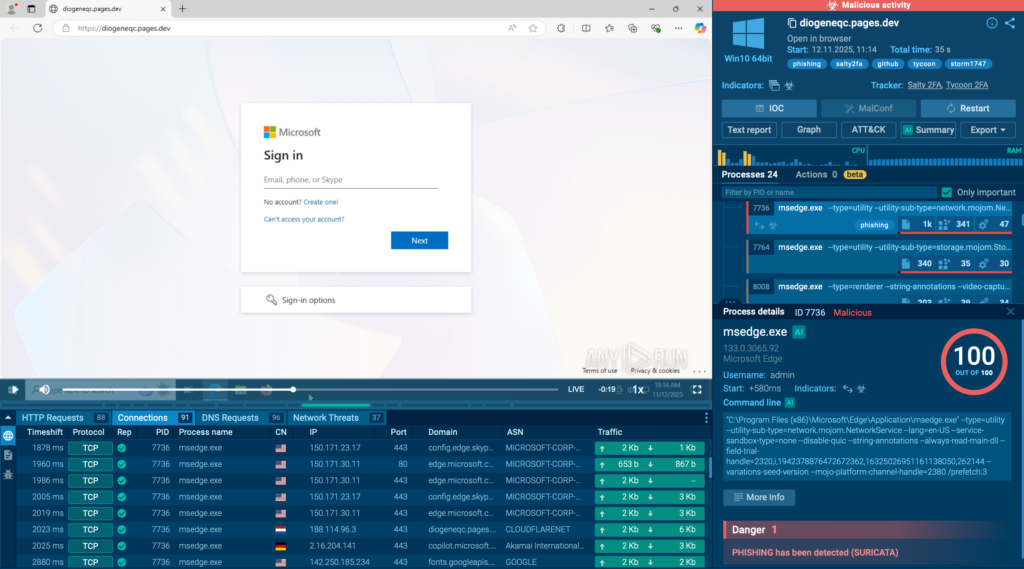
Hybrid chains create several challenges at once:
- Indicators belong to different kits, not just one
- Redirect paths change mid-attack
- Infrastructure overlaps across separate actor groups
- Detection rules based on one kit alone often miss the full picture
This evolution shows where phishing is heading: modular, flexible attack chains built from multiple commercial kits. For defenders, that means investigations must focus on behavior and execution flow, not just kit names or static indicators.
Key Takeaways for SOC Readiness in 2026
Phishkits now shape how real-world phishing attacks are built, delivered, and scaled against organizations.
- Phishing is now a real-time intrusion, not just a user mistake. Once a link is clicked, the compromise may already be underway.
- MFA alone is no longer enough: Session hijacking turns traditional MFA into a speed bump, not a barrier.
- Hybrid phishing chains are becoming common: When multiple kits are combined in one attack, single-family detections fall short.
- Behavior matters more than static indicators: Clean emails, short-lived domains, and valid sessions leave very little to flag at first glance.
- Speed defines outcome: Minutes often decide whether an incident stays contained or escalates.
- Evasion must be assumed by default: CAPTCHA abuse, fingerprinting, layered redirects, and sandbox checks are now standard tactics.
See It for Yourself
Phishkits behave very differently from what logs alone can show. A live run-through exposes even the most complex phishing chains, from redirects and proxy logic to live credential theft, often within the first 60 seconds of analysis in over 90% of cases. That speed alone can cut investigation time dramatically and help teams act before access spreads.
Explore interactive phishkit analysis with ANY.RUN
About ANY.RUN
ANY.RUN supports more than 15,000 organizations worldwide, including leaders in finance, healthcare, telecom, retail, and tech, helping them strengthen security operations and respond to threats with greater confidence.
Designed for speed and visibility, the solution blends interactive malware analysis with live threat intelligence, giving SOC teams instant insight into attack behavior and the context needed to act faster.
By integrating ANY.RUN’s Threat Intelligence suite into your existing workflows, you can accelerate investigations, minimize breach impact, and build lasting resilience against evolving threats.
Frequently Asked Questions (FAQ)
How is a phishkit different from regular phishing?
Traditional phishing often just steals usernames and passwords. Phishkits go much further. They can:
– Intercept live sessions
– Bypass MFA in real time
– Rotate domains automatically
– Filter out bots and security scanners
This turns phishing into a full attack platform, not just a fake page.
Can phishkits bypass MFA?
Yes. Many modern phishkits use adversary-in-the-middle (AiTM) techniques through reverse proxies. They capture credentials, MFA codes, and session cookies at the same time. Attackers then reuse the stolen session to log in without triggering MFA again.
Do phishkit attacks use malware?
Often, no. Many phishkit campaigns start with no malware at all. The compromise happens entirely through web-based credential theft. Malware may appear later for persistence or lateral movement, but the initial access is usually “clean.”
What are the most common signs of a phishkit attack?
Early warning signs may include unusual redirect chains before a login page appears, very short-lived phishing domains, CAPTCHA on unexpected login flows, new mailbox forwarding rules, or login activity from unfamiliar locations immediately after authentication.
Is blocking phishing domains enough to stop phishkits?
No. Domain blocking alone is not enough because phishing domains rotate quickly, redirect chains change constantly, and infrastructure is reused across campaigns. Behavioral detection and live analysis are now essential.
Will phishing get worse with phishkits in 2026?
Yes. Phishkits are becoming more automated, more modular, harder to attribute, and better at evading scanners and sandboxes. Hybrid chains that combine multiple phishkits in one attack are already becoming common.
What is the best long-term defense against phishkit attacks?
A strong long-term defense combines phishing-resistant MFA such as FIDO2 or certificate-based authentication, live sandbox analysis, continuous IOC enrichment, threat intelligence feeds, and SOC playbooks built around behavioraldetection. Because phishkits evolve constantly, defense must be continuous; not one-time.