
嗯,用户让我用中文总结一篇文章,控制在100字以内,而且不需要特定的开头。首先,我得仔细阅读这篇文章,抓住主要内容。 文章讲的是Ivanti公司的Endpoint Manager软件存在漏洞,CVE-2025-10573,这是一个严重的问题,可以让攻击者远程执行代码。影响挺大的,全球4万多公司使用这个软件。然后提到修复版本已经发布了,但很多实例暴露在互联网上,可能被攻击。 还有其他三个高危漏洞也被修复了,同样需要用户交互才能利用。虽然目前还没发现被利用的情况,但之前CISA也警告过类似的漏洞。 总结的时候要包括:Ivanti软件有漏洞,允许远程攻击,修复版本发布,但很多实例暴露在线上。还有其他漏洞被修复了。 控制在100字以内的话,可能需要简化一些细节。比如提到修复版本和暴露的实例数量。 最后检查一下有没有遗漏的重要信息,比如漏洞的类型(XSS)、影响范围、修复情况以及潜在风险。 </think> Ivanti警告客户修复其Endpoint Manager(EPM)软件中的新漏洞(CVE-2025-10573),该漏洞允许未认证攻击者通过低复杂度跨站脚本攻击执行任意JavaScript代码。尽管已发布修复版本EPM 2024 SU4 SR1以缓解风险,但仍有数百个EPM实例暴露于互联网上。此外,Ivanti还修复了三个高危漏洞(CVE-2025-13659、CVE-2025-13662和另一个未公开),这些漏洞同样需要用户交互才能被利用。 2025-12-9 17:15:22 Author: www.bleepingcomputer.com(查看原文) 阅读量:7 收藏

American IT software company Ivanti warned customers today to patch a newly disclosed vulnerability in its Endpoint Manager (EPM) solution that could allow attackers to execute code remotely.
Ivanti delivers system and IT asset management solutions to over 40,000 companies via a network of more than 7,000 organizations worldwide. The company's EPM software is an all-in-one endpoint management tool for managing client devices across popular platforms, including Windows, macOS, Linux, Chrome OS, and IoT.
Tracked as CVE-2025-10573, this critical security flaw can be exploited by remote, unauthenticated threat actors to execute arbitrary JavaScript code through low-complexity cross-site scripting attacks that require user interaction.
"An attacker with unauthenticated access to the primary EPM web service can join fake managed endpoints to the EPM server in order to poison the administrator web dashboard with malicious JavaScript," explained Rapid7 staff security researcher Ryan Emmons, who reported the vulnerability in August.
"When an Ivanti EPM administrator views one of the poisoned dashboard interfaces during normal usage, that passive user interaction will trigger client-side JavaScript execution, resulting in the attacker gaining control of the administrator’s session."
Ivanti released EPM version EPM 2024 SU4 SR1 to address the issue, and noted that the risk of this vulnerability should be significantly reduced because the Ivanti EPM solution is not intended to be exposed online.
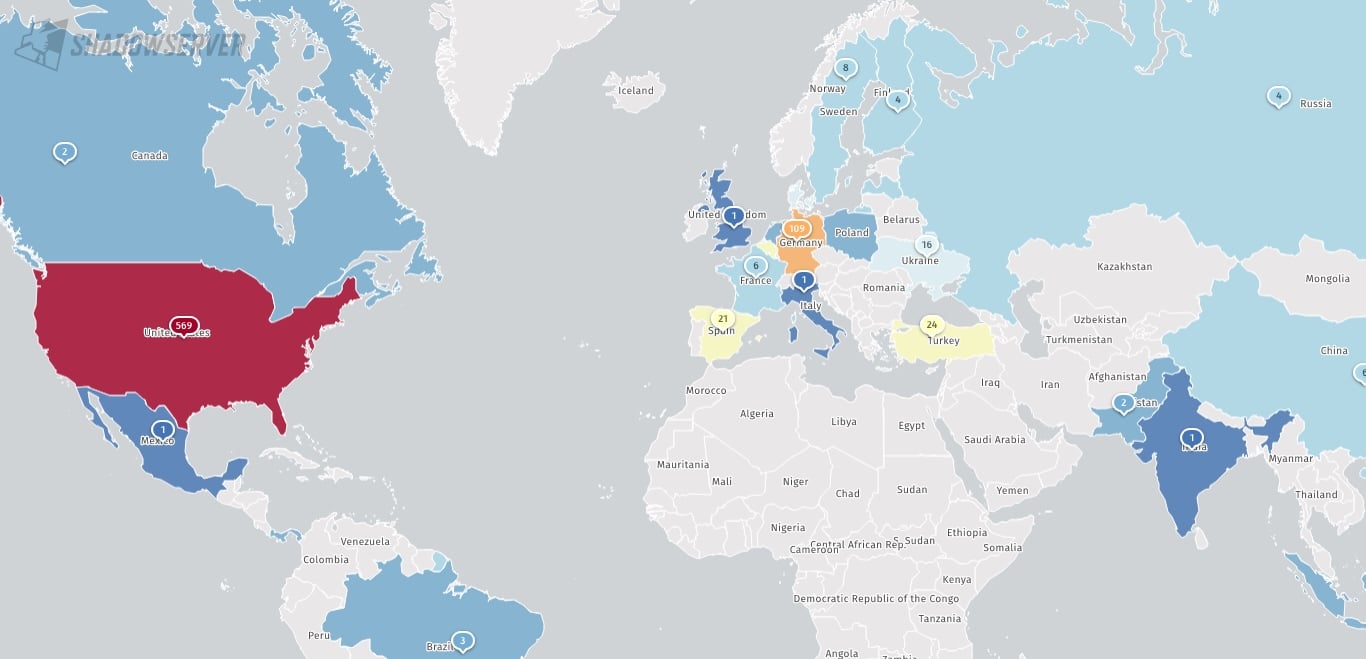
However, the Shadowserver threat monitoring platform currently tracks hundreds of Internet-facing Ivanti EPM instances, most of which are in the United States (569), Germany (109), and Japan (104).
Today, Ivanti also released security updates to address three high-severity vulnerabilities, two of which (CVE-2025-13659 and CVE-2025-13662) could allow unauthenticated attackers to execute arbitrary code on unpatched systems.
Luckily, successful exploitation also requires user interaction and the targets to either connect to an untrusted core server or import untrusted configuration files.
"We are not aware of any customers being exploited by these vulnerabilities prior to public disclosure. These vulnerabilities were disclosed through our responsible disclosure program," Ivanti said.
While Ivanti has yet to discover evidence of exploitation in attacks, Ivanti EPM security flaws are often targeted by threat actors.
Earlier this year, in March, CISA tagged three critical vulnerabilities affecting EPM appliances (CVE-2024-13159, CVE-2024-13160, and CVE-2024-13161) as exploited in attacks and warned U.S. federal agencies to secure their networks within three weeks.
The U.S. cybersecurity agency ordered government agencies to patch another actively exploited EPM flaw (CVE-2024-29824) in October 2024.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh
