嗯,用户让我总结一篇文章,控制在一百个字以内,而且不需要特定的开头。首先,我需要理解文章的主要内容。文章讲的是多个勒索软件团伙使用名为Shanya的打包服务来部署禁用EDR解决方案的有效载荷。 接下来,我得确定关键点:Shanya是什么,它如何工作,哪些勒索软件团伙使用了它,以及它的影响范围。用户可能需要一个简洁明了的总结,所以我要确保涵盖这些要点。 然后,我要注意字数限制,大约100字左右。这意味着每个关键点只能用一两句话概括。例如,Shanya是一个打包服务,帮助隐藏恶意代码;它在2024年底出现,并被多个团伙使用;它通过加密和内存操作禁用EDR工具。 最后,我要确保语言简洁流畅,不使用复杂的术语,让读者一目了然。这样用户就能快速抓住文章的核心内容了。 </think> 多个勒索软件团伙利用名为Shanya的打包服务部署有效载荷以禁用目标系统的EDR工具。该服务通过加密和压缩隐藏恶意代码,并将有效载荷注入内存中的Windows DLL文件中。Sophos发现Shanya已在全球多国被用于攻击活动,并被Medusa、Qilin等勒索软件团伙采用。 2025-12-9 00:0:20 Author: www.bleepingcomputer.com(查看原文) 阅读量:10 收藏

Multiple ransomware gangs are using a packer-as-a-service platform named Shanya to help them deploy payloads that disable endpoint detection and response solutions on victim systems.
Packer services provide cybercriminals with specialized tools to package their payloads in a way that obfuscates malicious code to evade detection by most known security tools and antivirus engines.
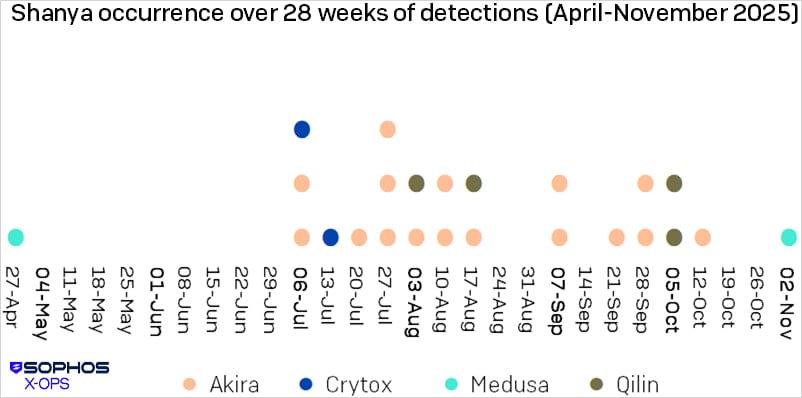
The Shanya packer operation emerged in late 2024 and has grown in popularity significantly, with malware samples using it being spotted in Tunisia, the UAE, Costa Rica, Nigeria, and Pakistan, as per telemetry data from Sophos Security.
Among the ransomware groups confirmed to have used it are Medusa, Qilin, Crytox, and Akira, with the latter being the one that uses the packers service most often.

Source: Sophos
How Shanya works
Threat actors submit their malicious payloads to Shanya, and the service returns a “packed” version with a custom wrapper, using encryption and compression.
The service promotes the singularity of the resulting payloads, highlighting the “non-standard module loading into memory, wrapper over the system loaderStub uniqueization,” with “each customer receiving their own (relatively) unique stub with a unique encryption algorithm upon purchase.”

Source: Sophos
The payload is inserted into a memory-mapped copy of the Windows DLL file ‘shell32.dll.’ This DLL file has valid-looking executable sections and size, and its path appears normal, but its header and .text section have been overwritten with the decrypted payload.
While the payload is encrypted inside the packed file, it is decrypted and decompressed while still entirely in memory, and then inserted into the ‘shell32.dll’ copy file, never touching the disk.
Sophos researchers found that Shanya performs checks for endpoint detection and response (EDR) solutions by calling the ‘RtlDeleteFunctionTable’ function in an invalid context.
This triggers an unhandled exception or a crash when running under a user-mode debugger, disrupting automated analysis before full execution of the payload.
Disabling EDRs
Ransomware groups typically seek to disable EDR tools running on the target system before the data theft and encryption stages of the attack.
The execution usually occurs via DLL side-loading, combining a legitimate Windows executable such as ‘consent.exe’ with a Shanya-packed malicious DLL like msimg32.dll, version.dll, rtworkq.dll, or wmsgapi.dll.
According to the analysis from Sophos, the EDR killer drops two drivers: a legitimately signed ThrottleStop.sys (rwdrv.sys) from TechPowerUp, which contains a flaw enabling arbitrary kernel memory writing, and the unsigned hlpdrv.sys.
The signed driver is used for privilege escalation, while hlpdrv.sys disables security products based on commands received from user mode.
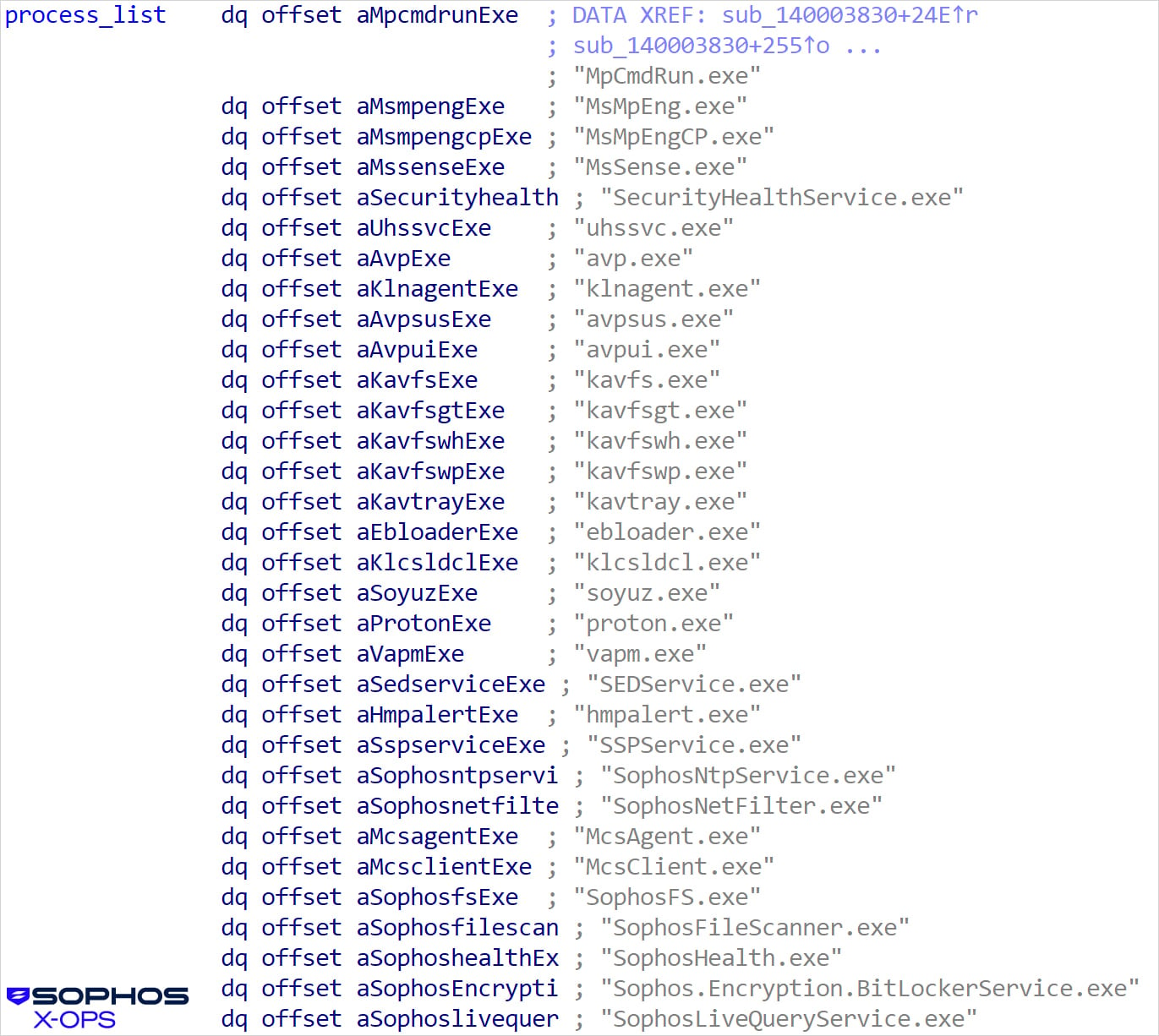
The user-mode component enumerates running processes and installed services, then compares the results against entries in an extensive hardcoded list, sending a “kill” command to the malicious kernel driver for each match.
Source: Sophos
Apart from ransomware operators focused on EDR disabling, Sophos has also observed recent ClickFix campaigns employing the Shanya service to package the CastleRAT malware.
Sophos notes that ransomware gangs often rely on packer services to prepare EDR killers for being deployed undetected.
The researchers provide a detailed technical analysis of some of the payloads packed with Shanya.
The report also includes indicators of compromise (IoCs) associated with Shanya-powered campaigns.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh
