运营技术(OT)管理关键工业基础设施,如能源和制造设施。与IT不同,OT更关注安全性、可靠性和可用性。然而,OT环境面临独特风险:硬件和软件通常过时且资源受限;IT与OT的融合增加了攻击面;物联网引入更多连接系统;密码管理问题如共享账户、远程访问和过时系统加剧了风险。强化密码策略、多因素认证和特权访问工作站是提升OT安全的关键措施。 2025-12-4 15:30:23 Author: www.bleepingcomputer.com(查看原文) 阅读量:7 收藏

Operational technology (OT) interacts with crucial real-world infrastructure, empowering everything from energy plants to manufacturing facilities. Such environments are obvious targets for cyberattacks, but OT security often leaves much to be desired.
OT is a broader concept than IT, describing the systems, both software and hardware, that underpin industrial environments. This means OT works directly with the physical world: things like Supervisory Control and Data Acquisition (SCADA) systems or Industrial Control Systems (ICS).
While there’s significant overlap with IT, the priorities are very different. As the UK’s National Cyber Security Centre (NCSC) notes:
“Where cybersecurity for IT has traditionally been concerned with information confidentiality, integrity and availability, OT priorities are often safety, reliability and availability, as there are clearly physical dangers associated with OT failure or malfunction.”
Key password challenges in OT security
OT environments aren’t just tempting targets for criminals, they are also uniquely vulnerable. For instance, the hardware and software in these environments is often outdated and resource-constrained, notes the World Economic Forum.
And things are growing more complex. IT and OT are increasingly intermingled, creating the potential for a criminal to exploit user credentials or reused passwords and to expand their attacks. The Internet of Things (IoT) introduces a new layer of connected systems that naturally increases the surface area for attack.
There are also unique challenges when it comes to passwords. As in the IT space, passwords remain a core function of security, even when users deploy multi-factor authentication (MFA) and other complementary approaches. However, the OT sector faces exacerbated risks and even unique dangers when compared with IT.
Interested to know how many of your users have weak or breached passwords? Run a read-only scan of your Active Directory today with our free tool: Specops Password Auditor.
Shared accounts and workstations
Sometimes, credential-sharing can enable bad actors to expand their threat, even moving from IT systems to OT, physical infrastructure. Likewise, the nature of OT work, for example, in remote infrastructure, could see people sharing workstations, boosting overall vulnerabilities.
Risks from remote access
Often, vendors and other third parties will need to access the OT environment remotely: this could involve specialists working on support or maintenance contracts, for instance. Such remote access pathways could introduce new vulnerabilities that need to be protected.
Outdated OT systems
Big infrastructure investments in areas like energy or manufacturing are often made with long-term operations in mind, not necessarily the demands of cybersecurity; indeed, some of the systems used in the OT environment may have been put in place years or even decades ago. This could introduce opportunities for sophisticated, modern cybercriminals.
Strengthening OT password security
So how can operators of OT environments mitigate the risk? It’s vital to build robust foundations by adopting best practices for password policies.
Password security is just as important in OT environments as in IT, and in some instances may be even more vital, given the potentially life-threatening consequences that could stem from a shutdown or outage.
Core password best practices for OT
There are some basic, but vital, priorities to keep in mind:
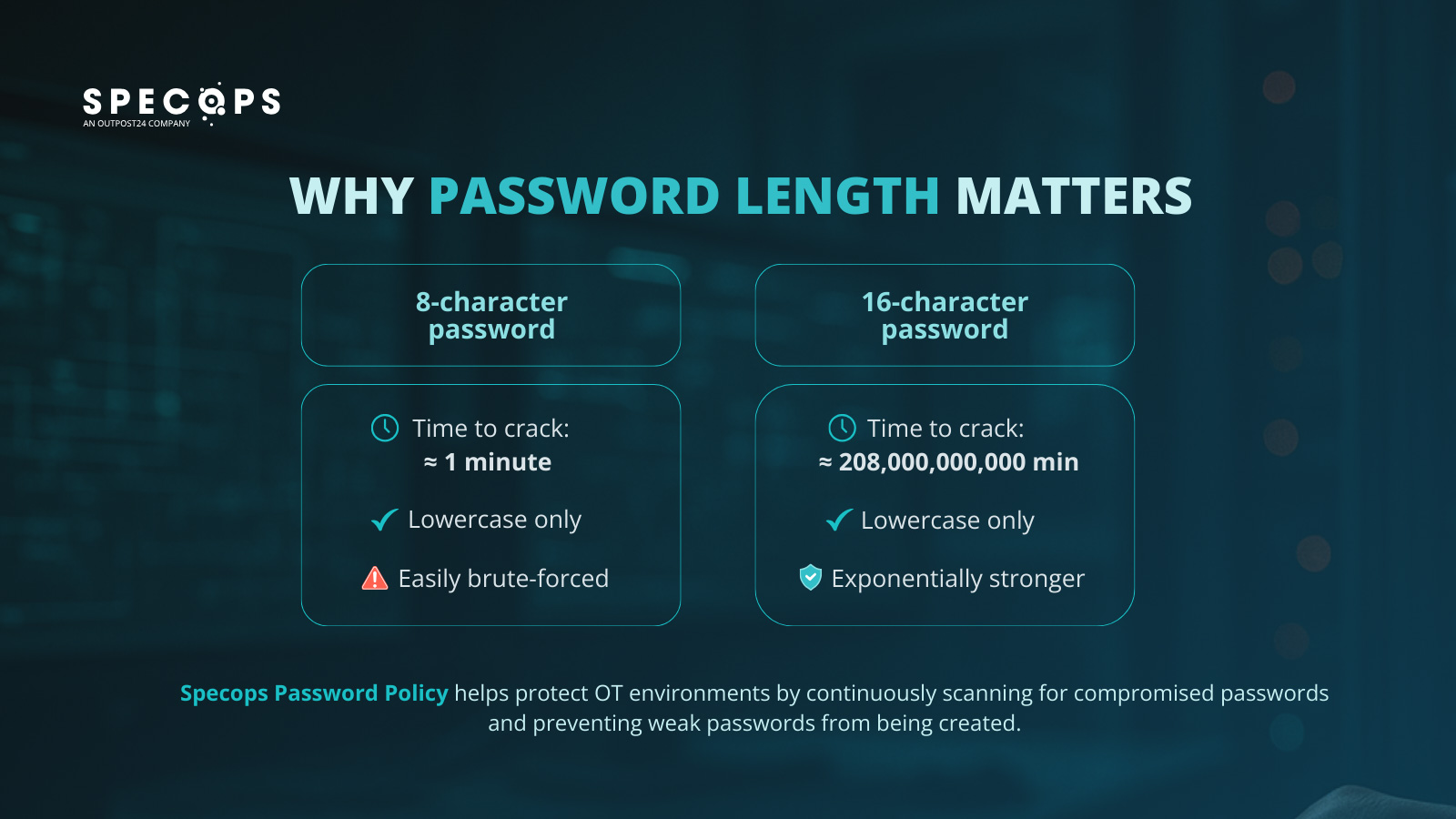
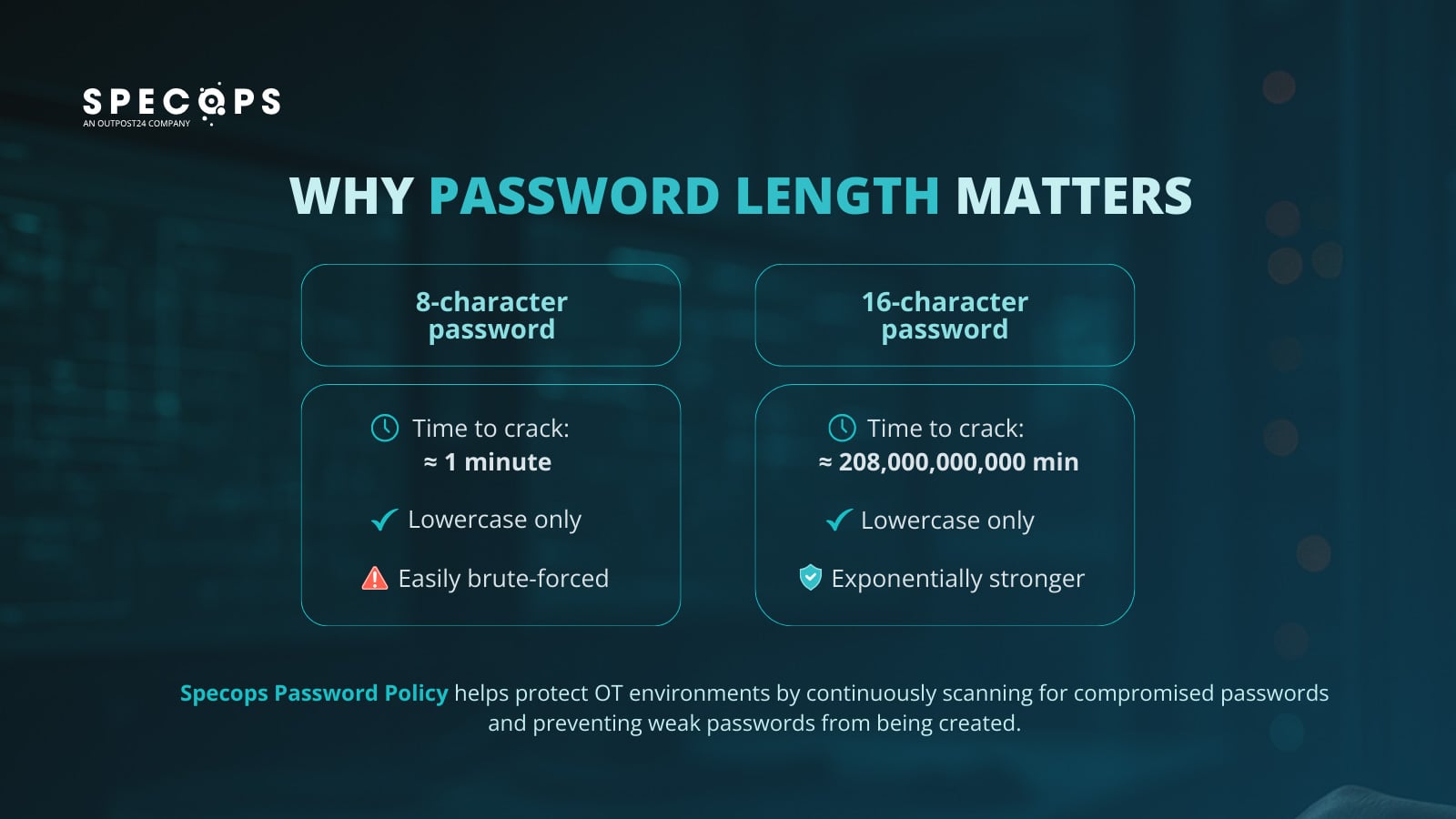
- Password length: This is the single most important factor in password security, particularly as criminals deploy brute force attacks to crack easily guessable selections (such as common words or repeating characters). For example, a powerful computer that might take one minute to guess an 8-character password could take more than 208 billion minutes to guess a password of 16 characters, even when both are all lowercase.
- Rotation: If you leave a password unchanged for long periods of time, you could provide criminals with an extended opportunity to crack it. A password rotation policy is one way to address this issue, though the specific timeframe used will depend on the organization in question. It’s also important to ensure password hygiene: for example, ensuring that old passwords aren’t reused.
- Password vaults: These store information in encrypted format and are often used to protect accounts that cover multiple users. They are usually protected by controls like hardware tokens.
Building a resilient OT security architecture
While passwords remain the linchpin of cybersecurity, they should be used in tandem with other security approaches to build a truly robust OT environment.
For example, MFA is often viewed as the gold standard in security. This boosts the security of OT environments by adding several other layers of security on top of passwords: this could include message-based methods, challenge-based authenticator apps, or FIDO2 authentication.
Some OT environments may also make use of Privileged Access Workstations (PAWs), which essentially separate the infrastructure used for high-risk activities from potentially compromising functions, such as web browsing or email access. However, it’s important to balance security with useability.
Likewise, segmentation and network access controls are important, ensuring that only the right devices (and people) can access designated areas, and that any damage is limited should the worst-case scenario become a reality.
Continuous password protection in OT
Although such security approaches have clear benefits, one thing is clear, poor password security will hugely increase your vulnerability to cyberattack, with potentially serious consequences.
This means it is vital to develop a clear picture of the password security landscape across an OT environment. Specops Password Policy provides this capability. The simple-to-use tool continuously scans for over 4.5 billion compromised passwords in Active Directory, while also blocking users from creating weak passwords in the first place. Book a free trial today.
OT systems interact with some of the most important infrastructure in industry and society, with serious consequences if things go wrong. Robust password security is the cornerstone of resilient OT environments, protecting people and assets for the long term.
Sponsored and written by Specops Software.
如有侵权请联系:admin#unsafe.sh