CRIL uncovers RelayNFC, a malware leveraging Near-Field Communication (NFC) to intercept and r 2025-11-25 06:31:12 Author: cyble.com(查看原文) 阅读量:21 收藏
CRIL uncovers RelayNFC, a malware leveraging Near-Field Communication (NFC) to intercept and relay contactless payment data.
Executive Summary
Cyble Research and Intelligence Labs (CRIL) has uncovered an active and evolving phishing campaign targeting users in Brazil. Dubbed RelayNFC, this Android malware family is designed specifically to perform NFC relay attacks for fraudulent contactless payments.
RelayNFC is a lightweight yet highly evasive malware because of its Hermes-compiled payload. This makes detection significantly harder, enabling it to stealthily capture victims’ card data and relay it in real time to an attacker-controlled server.
Key Takeaways
- RelayNFC implements a full real-time APDU relay channel, allowing attackers to complete transactions as though the victim’s card were physically present.
- Distribution relies entirely on phishing, tricking users into downloading RelayNFC malware.
- The malware is built using React Native and Hermes bytecode, which complicates static analysis and helps evade detection.
- A related variant attempts to implement Host Card Emulation (HCE), showing that the threat actor is exploring alternate NFC relay techniques.
- VirusTotal detections remain at zero, indicating very low visibility across the security ecosystem, and the code suggests a high likelihood of continued development.
Overview
While contactless payments were traditionally viewed as secure, however, this perception has shifted as threat actors are actively exploiting them.
Malware strains such as Ngate, SuperCardX, and PhantomCard highlight this accelerating trend. These threats abuse Near-Field Communication (NFC) capabilities to intercept or relay contactless payment data, often delivered through phishing or imposter sites disguised as trusted services.
Recently, Cyble Research and Intelligence Labs (CRIL) identified an ongoing campaign distributing a new variant of NFC-based attack malware, which Cyble Research and Intelligence Labs (CRIL) has named “RelayNFC”, derived from the indicators found in its code. The campaign targets users in Brazil and utilises a convincing Portuguese-language page that prompts victims to install an app under the guise of “securing” their payment cards. The malicious application is designed to capture the victim’s card details and relay them to attackers for fraudulent transactions.
We identified five sites with a similar user interface and all distributing the same malicious app, indicating a coordinated and ongoing operation targeting Brazilian users (see Figure 1).
- hxxps://maisseguraca[.]site/
- hxxp://proseguro[.]site/
- hxxps://test.ikotech[.]online/
- hxxps://maisseguro[.]site/
- hxxp://maisprotecao[.]site/

RelayNFC appears to be a newly developed variant built using the React Native framework to facilitate NFC relay fraud. The campaign has been active for at least a month, and the samples currently show zero detections on VirusTotal, highlighting its freshness and potential for widespread misuse.

A detailed technical analysis of the RelayNFC malware is provided in the next section.
Technical Analysis
RelayNFC is designed to operate with minimal permissions and components as indicated in its manifest file (see Figure 3).

The RelayNFC malware is developed using the React Native framework, which means that much of its functionality is packaged within the index.android.bundle file rather than traditional Java or Kotlin source code.
Instead of storing readable JavaScript, this bundle is compiled using the Hermes JavaScript engine, resulting in Hermes bytecode. This bytecode format makes it significantly harder to analyse and obfuscates the underlying logic, making static inspection challenging.
Reader Role
RelayNFC operates as a ‘reader’, enabling the malware to capture the victim’s card data and relay it to the attacker’s server. After installation, the app immediately displays a phishing screen that instructs the user to tap their payment card on the device, as shown in the figure below (see Figure 4).

Once the card data is read, RelayNFC presents another phishing screen prompting the victim to enter their 4- or 6-digit PIN. This behaviour is reflected in the code extracted from the index.android.bundle file (see Figure 5).

The RelayNFC code is built around a real-time relay channel that connects the victim’s smartphone to the attacker’s command server. This channel utilizes a persistent WebSocket connection to forward APDU (Application Protocol Data Unit – Communication unit between a card reader and a card) commands between the attacker and the victim’s NFC subsystem, effectively turning the infected device into a remote NFC “reader” for the attacker.
Once the WebSocket connects, the malware immediately sends an identification packet:
{
“type”: “hello”,
“role”: “reader”,
“id”: “<device-uuid>”
}
Here, the “role”: “reader” is critical — the attacker expects this device to act as the APDU source, meaning the side that communicates with the physical NFC card (see Figure 6).

After the WebSocket connection is active, RelayNFC listens for incoming messages from the server. It supports two main message types: a ping-pong exchange to maintain the session, and APDU commands that drive the card-reading and relaying process (see Figure 7).

When the attacker initiates a transaction from their POS-emulator device, the C&C server sends a specially crafted message of type “apdu” to the infected phone. This message contains a unique request ID, a session identifier, and the APDU command encoded as a hexadecimal string.
{
"type": "apdu",
"id": 1,
"sessionId": "abc",
"data": "00A40400"
}Upon receiving this instruction, RelayNFC parses the packet, extracts the APDU data, and forwards it directly to the victim device’s NFC subsystem, effectively acting as a remote interface to the physical payment card.
The NFC controller processes the command and generates a genuine APDU response exactly as the card would during a legitimate transaction. RelayNFC captures this output and immediately returns it to the C&C in an “apdu-resp” message, preserving the original request ID and session ID so the attacker’s device can continue the EMV transaction seamlessly.
{
"type": "apdu-resp",
"id": 1,
"sessionId": "abc",
"data": "9000"
}This real-time, bidirectional relay of APDU commands and responses is what enables the attacker to execute a full payment flow remotely, as if the victim’s card were physically present at their POS terminal.
Host-based Card Emulation Relay
During our analysis of the campaign, we identified an additional phishing site, hxxps://test.ikotech[.]online, which uses a similar interface and distributes a malicious APK named “cartao-seguro.apk” (SHA-256: 5905aa58853a05e860c87e9feeeea7c32b43859c8e703485e233429cec8d38dc).
This application includes a component called RelayHostApduService, which extends Android’s HostApduService and implements Host-based Card Emulation (HCE).

HCE allows an Android device to emulate a payment card and exchange small amounts of data over NFC. The malware overrides the processCommandApdu method and uses a WebSocket channel to forward APDU commands and responses externally. This mechanism effectively enables a real-time NFC relay attack, allowing a victim’s card interactions to be relayed between a legitimate payment terminal and an attacker-controlled device.

A similar pattern was recently observed in the NGate malware analysed by CERT.PL. Although the malware includes HCE-related code, the threat actors did not register the HCE service in the manifest, rendering it non-functional. This suggests the malware is still under development and that the operators are experimenting with different NFC relay attack techniques.
Conclusion
The RelayNFC campaign highlights the rapid evolution of NFC relay malware targeting payment systems, particularly in Brazil. By combining phishing-driven distribution, React Native–based obfuscation, and real-time APDU relaying over WebSockets, the threat actors have created a highly effective mechanism for remote EMV transaction fraud.
The discovery of a secondary variant attempting to implement HCE-based card emulation further indicates ongoing experimentation and active development within this malware family.
As mobile and contactless payments continue to grow in adoption and become increasingly digitized, the BFSI sector’s attack surface also expands proportionately. This emphasizes the need for stronger device-level protections, user awareness, and enhanced monitoring by financial institutions.
Cyble’s Threat Intelligence Platforms continuously monitor emerging threats, infrastructure, and activity across the dark web, deep web, and open sources. This proactive intelligence empowers organizations with early detection, impersonation, infrastructure mapping, and attribution insights. Altogether, these capabilities provide a critical head start in mitigating and responding to evolving cyber threats.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
- Install Apps Only from Trusted Sources:
Download apps exclusively from official platforms, such as the Google Play Store. Install third-party app stores or links received via SMS, social media, or email. - Be Cautious with Permissions and installs:
Never grant permissions and install an application unless you’re certain of an app’s legitimacy. - Watch for imposter Pages:
Always verify the URL and avoid suspicious links and websites that ask for sensitive information. - Enable Multi-Factor Authentication (MFA):
Use MFA for banking and financial apps to add an extra layer of protection, even if credentials are compromised. - Report Suspicious Activity:
If you suspect you’ve been targeted or infected, report the incident to your bank and local authorities immediately. If necessary, reset your credentials and perform a factory reset. - Use Mobile Security Solutions:
Install a mobile security application that includes real-time scanning. - Keep Your Device Updated:
Ensure your Android OS and apps are updated regularly. Security patches often address vulnerabilities that malware exploits. - Disable Tap-to-Pay / NFC When Not in Use
Keep NFC turned off on your device unless actively making a payment. This prevents unauthorised NFC access and reduces exposure to relay-based attacks.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Procedure |
| Initial Access (TA0027) | Phishing (T1660) | Malware is distributed via a phishing site |
| Discovery (TA0032) | System Information Discovery (T1426) | Malware collects device information |
| Credential Access (TA0031) | Input Capture: GUI Input Capture (T1417.002) | Malware loads the phishing page to enter the PIN |
| Command and Control (TA0037) | Application Layer Protocol: Web Protocols (T1437.001) | Malware uses http protocol |
| Command and Control (TA0037) | Non-Standard Port (T1509) | Malware establishes a WebSocket connection over port 3000 |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
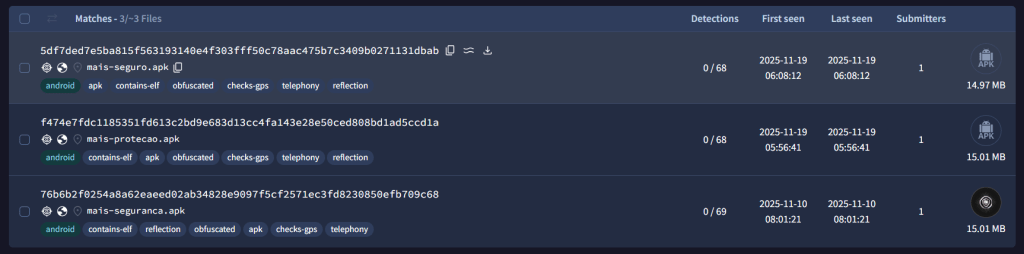
| 5df7ded7e5ba815f563193140e4f303fff50c78aac475b7c3409b0271131dbab f474e7fdc1185351fd613c2bd9e683d13cc4fa143e28e50ced808bd1ad5ccd1a 76b6b2f0254a8a62eaeed02ab34828e9097f5cf2571ec3fd8230850efb709c68 5905aa58853a05e860c87e9feeeea7c32b43859c8e703485e233429cec8d38dc 4124d196a5c7706c7d03d0da6fc19df5833793e30716b04f2259f5faa9816b45 | SHA256 | RelayNFC Hashes |
| hxxps://maisseguraca[.]site/ hxxp://proseguro[.]site/ hxxps://test.ikotech[.]online/ hxxps://maisseguro[.]site/ hxxp://maisprotecao[.]site/ | URL | Phishing URLs |
| hxxp://31.97[.]17.73:3000 hxxp://72.60[.]255.182:3000 hxxp://82.25.70[.]65:3000 hxxp://72.60[.]146.139:3000 hxxp://72[.]61.55.178:3000 | URL | C&C server |
如有侵权请联系:admin#unsafe.sh