AttackIQ推出Ransom Tales计划,通过模拟REvil、DarkSide和BlackMatter等勒索软件家族的战术、技术和程序(TTPs),帮助组织测试和增强其安全控制能力。 2025-11-6 20:12:44 Author: securityboulevard.com(查看原文) 阅读量:62 收藏
On July 22, 2025, AttackIQ introduced Ransom Tales, an initiative focused on routinely emulating the Tactics, Techniques, and Procedures (TTPs) associated with the prolific ransomware families currently dominating the threat landscape. Each volume in this series is designed to dissect the operational behaviors of multiple ransomware families and translate them into realistic emulations that defenders can employ to rigorously challenge their security controls and enhance resilience against disruptive and extortive threats.
In this fifth volume, AttackIQ’s Adversary Research Team (ART) revisits historical ransomware operations with the introduction of three new attack graphs that emulate the Tactics, Techniques, and Procedures (TTPs) associated with the REvil, DarkSide, and BlackMatter ransomware families. These groups pioneered sophistication in ransomware operations and were responsible for large-scale incidents worldwide, profoundly shaping the threat landscape and serving as precursors to many of today’s active ransomware strains.
Validating your security program performance against these behaviors is vital in reducing risk. By employing these assessment templates in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against baseline behaviors associated with historic and sophisticated ransomware strains.
- Assess their security posture against opportunistic and financially motivated adversaries that do not discriminate when selecting their targets.
- Continuously validate detection and prevention pipelines against a playbook similar to those of many of the adversaries currently focused on ransomware activities.
[Malware Emulation] REvil Ransomware – 2021-07 – Associated Tactics, Techniques and Procedures (TTPs)

This emulation replicates the sequence of behaviors associated with the deployment of REvil ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
REvil, also known as Sodinokibi and Sodin, is a ransomware strain operated under the Ransomware-as-a-Service (RaaS) model that emerged in April 2019. It has been associated with the developers of the GandCrab ransomware, which at the time accounted for nearly 40% of all global ransomware infections.
Since its emergence, REvil has been primarily distributed through exploit kits, spam campaigns, scan-and-exploit attacks, Remote Desktop Protocol (RDP) brute-force activity, and malicious software installers.
REvil gained significant notoriety for its supply-chain attack against Kaseya’s Virtual System Administrator (VSA) remote management software in July 2021, which exploited a zero-day vulnerability to deploy ransomware across Managed Service Providers and their downstream clients. The operators claimed to have compromised over a million systems worldwide and demanded $45,000 USD per device or a $70 million USD universal decryption key payable in Bitcoin.
REvil encrypts victim files and displays ransom notes demanding payment in cryptocurrency. It was among the first ransomware families to implement double extortion, exfiltrating sensitive data before encryption and threatening public release on its dedicated onion site if victims refused to comply.
Following a series of high-profile attacks, including the Kaseya compromise and intrusions against critical infrastructure, the Russian Federal Security Service (FSB) announced in January 2022 that it had dismantled REvil’s infrastructure and arrested several of its members. Despite this reported takedown, the REvil codebase and operational playbook have continued to influence multiple successor ransomware operations, reinforcing its legacy as one of the most impactful ransomware families of the modern era.
Execution & Persistence – REvil Ransomware Deployment

This stage begins with the deployment of the REvil ransomware which is executed through the DLL Search Order Hijacking technique. Once operational, it attempts to detect the presence of a debugger using the IsDebuggerPresent API.
Subsequently, it creates the registry key HKLM\SOFTWARE\WOW6432Node\BlackLivesMatter as part of its initial execution sequence. For persistence, it attempts to enable automatic login by modifying the AutoAdminLogon registry value under the HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon key, responsible for managing user logon/logoff actions. In case of failure, it falls back to adding an entry under HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce.
2021-07 REvil Ransomware (T1105): The REvil Ransomware sample (SHA256: d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e) is downloaded to memory and saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
DLL Search Order Hijacking (T1574.001): This scenario takes advantage of Microsoft’s Dynamic-Link Library (DLL) search order to load a rogue DLL into a system binary.
Debugger Detection via “IsDebuggerPresent” Native API (T1497): This scenario will execute the IsDebuggerPresent Windows API to detect the presence of a debugger attached to the current process.
Create Registry Entry (T1112): This scenario creates the registry key HKLM\SOFTWARE\WOW6432Node\BlackLivesMatter as part of its initial execution sequence.
Use Registry to Enable Automatic Login to Windows Workstation (T1547.004): This scenario modifies the registry value AutoAdminLogon under the key HKLM\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon to automatically login with an administrative account.
Persistence Through Registry Run and RunOnce Keys (T1547.001): This scenario creates an entry under HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce to establish persistence on the system.
Discovery – Local System Reconnaissance

This stage focuses on system reconnaissance by collecting system information through the GetSystemInfo API, retrieving the username associated with the current thread via the GetUserNameW API, performing process enumeration using the CreateToolhelp32Snapshot, Process32FirstW, and Process32NextW APIs, and gathering service status information through the EnumServicesStatusW API.
System Information Discovery via “GetSystemInfo” Native API (T1082): This scenario executes the GetSystemInfo Windows API call to retrieve information associated to the system.
System Owner/User Discovery via “GetUserNameW” Native API (T1033): This scenario executes the GetUserNameW Windows API call to retrieve the name of the user associated with the current thread.
Process Discovery via Native API (T1057): This scenario uses Windows API to receive a list of running processes by calling CreateToolhelp32Snapshot and iterating through each process object with Process32FirstW and Process32NextW.
Service Status Discovery via “EnumServicesStatusW” Native API (T1007): This scenario executes the EnumServiceStatusW Windows API to gather critical information regarding configured services.
Impact – REvil Ransomware Encryption
This stage begins by identifying drive types through the GetDriveTypeW API, followed by filesystem traversal and file enumeration using the FindFirstFileW and FindNextFileW APIs. It then deletes existing Volume Shadow Copies via the vssadmin.exe utility. Finally, REvil encrypts the identified files using a combination of AES-256 for file encryption with RSA-2048 for key encryption.
Drive Type Discovery via “GetDriveTypeW” Native API (T1680): This scenario retrieves information about the system’s physical disks by executing the GetDriveTypeW Windows API call.
File and Directory Discovery via “FindFirstFileW” and “FindNextFileW” Native API (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows native API calls to enumerate the file system.
Delete created Volume Shadow Copy using “vssadmin.exe” (T1490): This scenario executes the vssadmin.exe utility to delete a Volume Shadow Copy created by the emulation.
REvil File Encryption (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by REvil ransomware.
[Malware Emulation] DarkSide Ransomware – 2021-06 – Associated Tactics, Techniques and Procedures (TTPs)

This emulation replicates the sequence of behaviors associated with the deployment of DarkSide ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
DarkSide is a ransomware strain operated under the Ransomware-as-a-Service (RaaS) model, first observed in August 2020 and updated to v2.0 in March 2021. Believed to be of Russian origin, its operators are likely former affiliates of the REvil ransomware group, as DarkSide was developed using REvil’s base code. Since its emergence, DarkSide has evolved into a high-impact, financially motivated threat that has refined its Tactics, Techniques, and Procedures (TTPs) to maximize disruption and extortion.
Operators behind DarkSide are known for a double-extortion approach, encrypting victims’ systems to block operations while exfiltrating sensitive data and threatening public release to coerce payment. The group publicly stated a preference for high-revenue organizations perceived as able to pay significant ransoms and claimed avoidance of hospitals, schools, non-profits, and governments.
DarkSide affiliates have been observed gaining initial access through phishing, exploitation of externally facing applications and services, and abuse of remote access technologies such as Remote Desktop Protocol (RDP) and Virtual Desktop Infrastructure (VDI). They have also exploited specific vulnerabilities, notably CVE-2019-5544 and CVE-2020-3992, which are Remote Code Execution (RCE) vulnerabilities in VMware ESXi’s Service Location Protocol (SLP) service.
During compromise, DarkSide performs extensive data encryption using a hybrid cryptographic scheme that combines Salsa20 for file encryption and RSA for key protection. Victims receive customized ransom notes and often observe unique file-extension markers applied to encrypted files.
DarkSide gained international notoriety following its involvement in the Colonial Pipeline incident in May 2021, one of the most disruptive ransomware attacks in U.S. history. The attack forced the temporary shutdown of Colonial Pipeline’s operations, halting fuel distribution across the U.S. East Coast for nearly a week and triggering widespread supply shortages. The resulting six-day outage highlighted the critical vulnerabilities in national infrastructure and led to a declaration of emergency by the U.S. government. In the aftermath, DarkSide’s infrastructure was reportedly seized or shut down, and the group announced it would cease operations.
Persistence & Discovery – DarkSide Ransomware Deployment

This stage begins with the deployment of the DarkSide ransomware, which establishes persistence by creating a scheduled task. Once operational, it retrieves the system’s Globally Unique Identifier (GUID), queries the current username via the GetUserNameW API, and collects service status information using the EnumServicesStatusW API.
Subsequently, it uses Windows Management Instrumentation (WMI) queries to enumerate installed endpoint defenses, including antivirus, antispyware, and local firewall products.
2021-05 DarkSide Ransomware Sample (T1105): The DarkSide Ransomware sample (SHA256: 156335b95ba216456f1ac0894b7b9d6ad95404ac7df447940f21646ca0090673) is downloaded to memory and saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
Persistence Through Scheduled Task (T1053.005): This scenario acquires persistence through the creation of a new scheduled task using the schtasks utility.
Obtain MachineGUID from Cryptography Registry Key using “reg query” Command (T1012): This scenario queries the MachineGUID value located within the HKLM\SOFTWARE\Microsoft\Cryptography registry key which contains the unique identifier of the system.
System Owner/User Discovery via “GetUserNameW” Native API (T1033): This scenario executes the GetUserNameW Windows API call to retrieve the name of the user associated with the current thread.
Service Status Discovery via “EnumServicesStatusW” Native API (T1007): This scenario executes the EnumServiceStatusW Windows API to gather critical information regarding configured services.
Discover Security Software (AntiVirusProduct) using WMI Command (T1518.001): This scenario executes a Microsoft Windows Management Instrumentation Command (WMIC) to determine the installed antivirus software using the AntiVirusProduct class.
Discover Anti Spyware Software via WMI Command (T1518.001): This scenario executes a Microsoft Windows Management Instrumentation Command (WMIC) to determine the installed antispyware product using the AntiSpywareProduct class.
Discover Local Firewall Software via WMI Command (T1518.001): This scenario executes a Microsoft Windows Management Instrumentation Command (WMIC) to determine the installed firewall product using the FirewallProduct class.
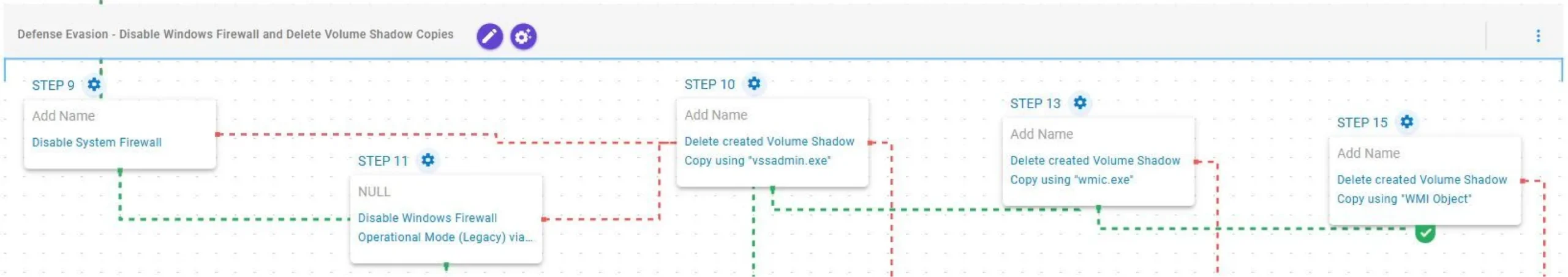
Defense Evasion – Disable Windows Firewall and Delete Volume Shadow Copies

This stage begins by attempting to disable the Windows Firewall using the netsh utility. If unsuccessful, it retries through the legacy firewall operational mode (opmode) implementation. Next, it attempts to delete Volume Shadow Copies through vssadmin.exe, wmic.exe, or WMI objects.
Disable System Firewall (T1562.004): This scenario executes the netsh advfirewall utility to check the local firewall status and disable it for the system.
Disable Windows Firewall Operational Mode (Legacy) via Netsh (T1562.004): This scenario executes the netsh firewall legacy utility to disable the local firewall for the system.
Delete created Volume Shadow Copy using “vssadmin.exe” (T1490): This scenario executes the vssadmin.exe utility to delete a Volume Shadow Copy created by the emulation.
Delete created Volume Shadow Copy using “wmic.exe” (T1490): This scenario executes the wmic shadowcopy delete command to delete a Volume Shadow Copy created by the emulation.
Delete created Volume Shadow Copy using “WMI Object” (T1490): This scenario executes the Get-WMIObject Win32_ShadowCopy PowerShell command to delete a Volume Shadow Copy created by the emulation.
Impact – DarkSide Ransomware Encryption

This stage begins by enumerating logical drives using the GetLogicalDriveStringsW API and determining drive types via GetDriveTypeW. Next, it enumerates available volumes through the FindFirstVolumeW and FindNextVolumeW APIs, followed by filesystem traversal and file enumeration using FindFirstFileW and FindNextFileW. Finally, DarkSide encrypts the identified files using Salsa20 for file encryption and RSA-1024 for key protection.
Logical Drive Discovery via “GetLogicalDriveStringsW” Native API (T1680): This scenario executes the GetLogicalDriveStringsW Windows API call to retrieve information regarding the system’s physical drives.
Drive Type Discovery via “GetDriveTypeW” Native API (T1680): This scenario retrieves information about the system’s physical disks by executing the GetDriveTypeW Windows API call.
Volume Discovery via “FindFirstVolumeW” and “FindNextVolumeW” Native API (T1680): This scenario executes the FindFirstVolumeW and FindNextVolumeW Windows API calls to iterate through the available volumes of the system.
File and Directory Discovery via “FindFirstFileW” and “FindNextFileW” Native API (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows native API calls to enumerate the file system.
DarkSide File Encryption (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by DarkSide ransomware.
[Malware Emulation] BlackMatter Ransomware – 2021-11 – Associated Tactics, Techniques and Procedures (TTPs)

This emulation replicates the sequence of behaviors associated with the deployment of BlackMatter ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
BlackMatter is a ransomware strain operated under the Ransomware-as-a-Service (RaaS) model that emerged in July 2021. Since its appearance, BlackMatter has positioned itself as a Big Game Hunter (BGH) operation, targeting large enterprises while publicly claiming to avoid critical infrastructure such as hospitals, energy facilities, and government entities.
Its first appearance on dark web forums advertised the ransomware as a combination of features from DarkSide, BlueCrab, and LockBit ransomware. BlackMatter exhibits strong technical and operational similarities to both DarkSide and REvil, suggesting shared personnel, code reuse, or direct collaboration between the groups.
The Kaseya supply-chain compromise in early July 2021, attributed to the REvil ransomware group, is widely regarded as a catalyst for the emergence of BlackMatter. Among the Indicators of Compromise (IOCs) observed during this intrusion was a “BlackLivesMatter” registry entry, which may have served as an early indicator of BlackMatter’s formation. Following the massive global impact of the Kaseya attack, which exploited managed service providers to deliver ransomware to hundreds of downstream victims, REvil abruptly disappeared from the dark web, likely to evade intensified law enforcement scrutiny, creating the conditions for BlackMatter’s rise.
In its initial months of activity, BlackMatter distributed ransomware to at least 28 organizations, demanding ransoms ranging from $80,000 to $15 million payable in Bitcoin or Monero. Early victims included a U.S.-based architecture firm, compromised less than a month after the Kaseya supply-chain attack attributed to REvil ransomware.
The Windows variant of BlackMatter uses previously compromised administrative or user credentials to authenticate via Lightweight Directory Access Protocol (LDAP) and Server Message Block (SMB) for network-wide discovery and lateral movement. It leverages APIs such as NtQuerySystemInformation and EnumServicesStatusExW to enumerate processes and services, then remotely encrypts accessible network shares, including ADMIN$, C$, SYSVOL, and NETLOGON.
The group also developed dedicated payloads for Linux and ESXi environments, enabling targeting of Linux-based systems and encryption of virtual machines. In certain instances, the Linux variant operated as a Remote Access Trojan (RAT) to facilitate movement toward Windows assets rather than encrypting data directly. Unlike other ransomware operations, BlackMatter affiliates often wiped or reformatted backup storage systems instead of encrypting them, ensuring maximum operational disruption.
Despite its stated avoidance of critical sectors, BlackMatter’s operations mirrored those of its predecessors in sophistication, reach, and extortion methodology. By October 2021, heightened law enforcement pressure reportedly led to the dismantling or abandonment of the group’s infrastructure, marking the end of a short-lived but highly impactful ransomware operation.
Persistence & Discovery – BlackMatter Ransomware Deployment

This stage begins with the deployment of the BlackMatter ransomware, which, once operational, retrieves the system locale using the GetLocaleInfoW API and establishes persistence through the registry RunOnce key.
Next, it retrieves the system’s Globally Unique Identifier (GUID), queries the current username via the GetUserNameW API, performs process information discovery by invoking the NtQuerySystemInformation API with the SystemProcessInformation parameter, and collects service status information using EnumServicesStatusW API.
2021-10 BlackMatter Ransomware Sample (T1105): The BlackMatter Ransomware sample (SHA256: 706f3eec328e91ff7f66c8f0a2fb9b556325c153a329a2062dc85879c540839d) is downloaded to memory and saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
Obtain System Locales Information via “GetLocaleInfoW” Windows API (T1614): This scenario executes the GetLocaleInfoW Windows API to retrieve the user’s default country locale code from the system.
Persistence Through Registry Run and RunOnce Keys (T1547.001): This scenario creates an entry under HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce to establish persistence on the system.
Obtain MachineGUID from Cryptography Registry Key using “reg query” Command (T1012): This scenario queries the MachineGUID value located within the HKLM\SOFTWARE\Microsoft\Cryptography registry key which contains the unique identifier of the system.
System Owner/User Discovery via “GetUserNameW” Native API (T1033): This scenario executes the GetUserNameW Windows API call to retrieve the name of the user associated with the current thread.
System Process Information Discovery via “NtQuerySystemInformation” Native API (T1057): This scenario executes NtQuerySystemInformation API with the SystemProcessInformation argument to enumerate system processes.
Service Status Discovery via “EnumServicesStatusW” Native API (T1007): This scenario executes the EnumServiceStatusW Windows API to gather critical information regarding configured services.
Impact – BlackMatter Ransomware Encryption

This stage begins by attempting to delete Volume Shadow Copies through WMI objects. Then, it enumerates logical drives using the GetLogicalDriveStringsW API and determines drive types via GetDriveTypeW. Subsequently, it enumerates available volumes through the FindFirstVolumeW and FindNextVolumeW APIs, followed by filesystem traversal and file enumeration using FindFirstFileW and FindNextFileW. Finally, BlackMatter encrypts the identified files using Salsa20 for file encryption and RSA-1024 for key protection. Following encryption, it attempts to clear Windows event logs via the OpenEventLogW and ClearEventLogW APIs.
Delete created Volume Shadow Copy using “WMI Object” (T1490): This scenario executes the Get-WMIObject Win32_ShadowCopy PowerShell command to delete a Volume Shadow Copy created by the emulation.
Logical Drive Discovery via “GetLogicalDriveStringsW” Native API (T1680): This scenario executes the GetLogicalDriveStringsW Windows API call to retrieve information regarding the system’s physical drives.
Drive Type Discovery via “GetDriveTypeW” Native API (T1680): This scenario retrieves information about the system’s physical disks by executing the GetDriveTypeW Windows API call.
Volume Discovery via “FindFirstVolumeW” and “FindNextVolumeW” Native API (T1680): This scenario executes the FindFirstVolumeW and FindNextVolumeW Windows API calls to iterate through the available volumes of the system.
File and Directory Discovery via “FindFirstFileW” and “FindNextFileW” Native API (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows native API calls to enumerate the file system.
BlackMatter File Encryption (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by BlackMatter ransomware.
Clear Windows Event Log via Windows API (T1070.001): The scenario executes the OpenEventLogW and ClearEventLogW Windows APIs to delete Windows event logs from the system.
Opportunities to Expand Emulation Capabilities
In addition to the released attack graph, AttackIQ recommends the following scenario to extend the emulation of the capabilities exhibited by DarkSide ransomware:
Domain Controller Remote System Discovery via Powershell Script (T1018): This scenario executes the PowerShell Get-ADComputer cmdlet to get the list of Active Directory computers, showing the name, hostname and installed operating system.
Wrap-up
In summary, these attack graphs will evaluate security and incident response processes and support the improvement of your security control posture against the behaviors exhibited by REvil, DarkSide and BlackMatter ransomware operators. With data generated from continuous testing and use of these assessment templates, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against known and dangerous threats.
AttackIQ, the leading provider of Adversarial Exposure Validation (AEV) solutions, is trusted by top organizations worldwide to validate security controls in real time. By emulating real-world adversary behavior, AttackIQ closes the gap between knowing about a vulnerability and understanding its true risk. AttackIQ’s AEV platform aligns with the Continuous Threat Exposure Management (CTEM) framework, enabling a structured, risk-based approach to ongoing security assessment and improvement. The company is committed to supporting its MSSP partners with a Flexible Preactive Partner Program that provides turn-key solutions, empowering them to elevate client security. AttackIQ is passionate about giving back to the cybersecurity community through its free award-winning AttackIQ Academy and founding research partnership with MITRE Center for Threat-Informed Defense.
如有侵权请联系:admin#unsafe.sh
