
LockBit自2019年作为ABCD ransomware出现以来一直是全球领先的勒索软件即服务(RaaS)团伙之一。尽管面临国际执法行动和内部泄露等挫折,该组织仍持续更新技术、扩展业务并发起跨行业攻击。最新版本LockBit 5.0引入了两阶段部署模型和高级绕过技术,展示了其在压力下的适应能力和持续威胁性。 2025-11-6 15:18:57 Author: flashpoint.io(查看原文) 阅读量:5 收藏
LockBit has remained one of the most dominant ransomware-as-a-service (RaaS) groups in the world since its emergence as ABCD ransomware in 2019 and official launch as LockBit in 2020. Despite high-profile setbacks—including international law enforcement takedowns in early 2024 and a damaging affiliate panel leak in May 2025—the group continues to update its codebase, expand affiliate operations, and launch large-scale attacks targeting organizations across industries.
Flashpoint has tracked LockBit through numerous evolutions, from the early .abcd encryptors to the faster and stealthier LockBit 3.0 and the Conti-inspired LockBit Green. Now, with version 5.0, the group has introduced a refined two-stage ransomware deployment model that aims to maximize evasion, modularity, and destructive impact.
This post outlines how LockBit 5.0 works, what’s changed, and why defenders should treat this latest evolution as a clear signal that even after takedowns and leaks, ransomware groups are investing innovating faster, not backing off.
LockBit 5.0: Key Capabilities and Objectives
Trend Micro first flagged the emergence of LockBit 5.0 in late September 2025. Flashpoint’s analysis confirms that the group is building on the existing v4.0 codebase rather than starting from scratch. Many core functions remain, including familiar file encryption methods, geographic execution limits, and even a recycled ransom note that still misspells “information”.
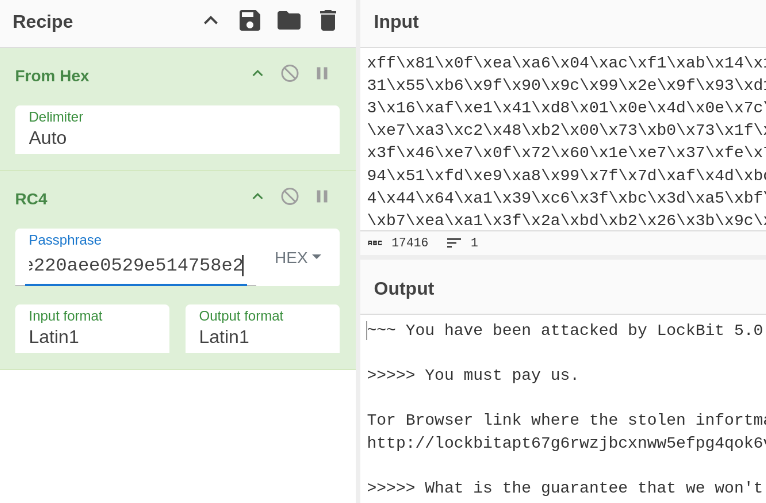
However, LockBit 5.0 introduces several new or upgraded capabilities:
- A modular two-stage architecture that separates the loader from the main payload
- Expanded anti-analysis features, including control flow obfuscation and API hashing
- Aggressive EDR bypass using process hollowing, unhooked libraries, and ETW patching
- Support for stealth execution modes that omit file extensions and ransom notes
These updates demonstrate that LockBit’s developers are focused on staying operational under pressure, iterating on technical defenses while retaining the group’s familiar tooling and affiliate model.
Technical Deep Dive: The Two-Stage Execution Model
At the heart of LockBit 5.0 is its new two-stage execution model:
- Stage one acts as a loader built for stealth and survivability.
- Stage two executes the core ransomware payload, designed for flexible deployment, targeted destruction, and layered evasion.
Stage One: The Stealthy Loader and EDR Evasion
Key features of the loader at stage one include:
- Control flow obfuscation: The code calculates jump destinations dynamically, which makes traditional disassembly and reverse engineering more difficult.
- Dynamic API resolution: The malware avoids hardcoded API names and instead resolves function calls at runtime using a custom hashing algorithm.
- Library unhooking: It reloads clean copies of NTDLL and Kernel32 from disk, overwriting any hooks placed by security tools in memory.
- Shellcode trampolines: The loader constructs custom shellcode that redirects execution to resolved API calls, bypassing standard detection methods.
The loader then creates a suspended instance of defrag.exe and injects the decrypted payload using process hollowing. Flashpoint analysts confirmed that the stage two payload is written into memory using ZwWriteProcessMemory, the instruction pointer is updated, and the process resumes execution—all without triggering default security alerts.
Stage Two: The Destructive Ransomware Payload
Stage two is the main ransomware payload. Flashpoint observed this binary labeled “ChuongDoung Locker v1.01,” a likely nod to researcher Chuong Dong. It contains both familiar LockBit features and new destructive options.
The payload supports various command-line switches and can run with or without visible impact. In “destruction-only” mode, it encrypts files silently without changing extensions or displaying a ransom note, a tactic that may be used for retaliatory or purely disruptive campaigns.
Additional behaviors include:
- Encryption of local drives, specific directories, and network shares
- Multi-threaded encryption using Curve25519 keys and XChaCha20 cipher
- Repeated library unhooking for every DLL loaded
- Disabling of system services such as VSS, WSearch, and Edgeupdate
- File and directory exclusions to preserve OS functionality and evade detection
- Decryption of ransom note text using RC4, written as ReadMeForDecrypt.txt
Before executing, the payload checks the victim machine to ensure it is not in Russia or Russia-allied locations, and, curiously, avoids execution on systems located in the Philippines—a behavior Flashpoint continues to investigate.
Implications for Defenders
LockBit 5.0 reflects a broader shift in ransomware development: professionalization under pressure. Despite sanctions, leaks, and arrests, the group continues to operate at scale.
The release of LockBit 5.0 also follows with other developments, including:
- The May 2025 leak of internal LockBit data, which exposed affiliate accounts, ransomware builds, and ransom negotiations between victims and affiliates.
- A growing ecosystem of access brokers and infostealer distributors who supply LockBit operators with compromised credentials.
- Adoption of new vulnerability exploits and evasion techniques that shorten detection windows
For defenders, this reinforces the importance of tracking ransomware groups not only by IOCs but also by their tooling, TTPs, and underground relationships.
Flashpoint’s Ransomware Defense Framework
As ransomware groups like LockBit evolve, defenders must adapt. Flashpoint’s Ransomware Survival Guide outlines how security teams can protect themselves across the entire attack lifecycle, from early reconnaissance to post-incident recovery.
Key recommendations:
- Monitor illicit forums and breach sites for early warning signals, including chatter about compromised credentials, exploits, or stolen data.
- Correlate vulnerability intelligence with ransomware group preferences to prioritize patching.
- Use behavioral detection to flag evasive actions like ETW patching or library unhooking—tactics increasingly favored by LockBit and its affiliates.
- Prepare a tailored response playbook with negotiation protocols, offline backups, and legal guidance pre-staged before an attack occurs.
LockBit 5.0 is the latest proof that ransomware isn’t going away, it’s adapting. The best way to stay ahead is by fusing primary source intelligence, behavioral analysis, and coordinated readiness.
For more, download our Ransomware Survival Guide or speak with a Flashpoint expert.
LockBit 5.0 Technical Analysis FAQs
Q: What is the primary technical innovation introduced in LockBit 5.0?
A: LockBit 5.0’s primary technical innovation is a modular two-stage deployment model. Stage One is a stealthy loader that performs evasion tactics like library unhooking and process hollowing, while Stage Two is the core, destructive ransomware payload.
Q: What is LockBit 5.0’s most aggressive EDR evasion technique?
A: One of LockBit 5.0’s most aggressive EDR evasion techniques involves library unhooking, where the loader reloads clean copies of core Windows libraries (NTDLL and Kernel32) from disk, overwriting any detection hooks placed in memory by security tools. This is often followed by injecting the payload using process hollowing.
Q: What evidence does Flashpoint have regarding LockBit’s resilience despite takedowns?
A: Flashpoint tracked over 150 known victims attributed to LockBit in the three months following the major law enforcement takedown in February 2024. This data confirms the group’s ability to quickly recover its infrastructure and maintain an active, high-volume affiliate network.
Q: Why does the LockBit 5.0 payload support a “destruction-only” mode?
A: The “destruction-only” mode allows the payload to encrypt files silently without displaying a ransom note or changing file extensions. Flashpoint analysts suggest this tactic may be used for retaliatory or purely disruptive campaigns where the goal is operational damage rather than financial extortion.
如有侵权请联系:admin#unsafe.sh