微软发现名为SesameOp的新后门程序,利用OpenAI Assistants API作为隐蔽命令控制通道,在被入侵系统中进行窃取活动。该后门通过恶意注入和内部网络壳维持持久性控制。微软与OpenAI合作禁用恶意API密钥,并强调攻击者滥用新兴AI技术的风险。 2025-11-4 17:6:46 Author: securityaffairs.com(查看原文) 阅读量:6 收藏
SesameOp: New backdoor exploits OpenAI API for covert C2
Pierluigi Paganini
November 04, 2025

Microsoft found a new backdoor, SesameOp, using the OpenAI Assistants API for stealthy command-and-control in hacked systems.
Microsoft uncovered a new backdoor, named SesameOp, that abuses the OpenAI Assistants API for command-and-control, allowing covert communication within compromised systems.
Microsoft Incident Response – Detection and Response Team (DART) researchers discovered the backdoor in July 2025 while investigating a major intrusion where attackers stayed hidden for months. The hackers used malicious .NET AppDomainManager injections within Visual Studio utilities to maintain persistence and control via internal web shells.
The investigation found internal web shells executing commands from malicious processes hidden in compromised Visual Studio utilities using .NET AppDomainManager injection.
SesameOp leveraged the OpenAI Assistants API as a command-and-control channel for espionage. Microsoft and OpenAI jointly investigated, disabling the malicious API key and confirming limited API use. The case highlights evolving attacker tactics and misuse of emerging AI technologies.
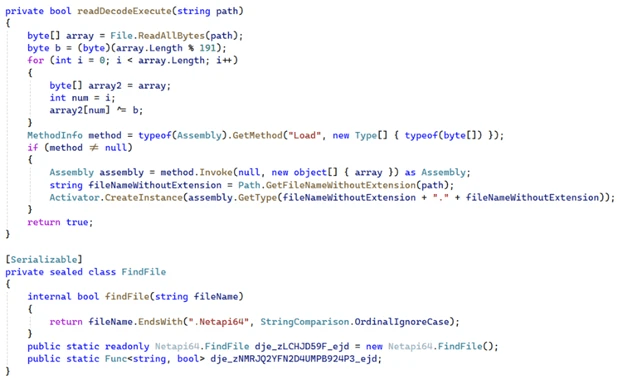
The custom implant has two components: a heavily obfuscated loader (Netapi64.dll) and a .NET backdoor (OpenAIAgent.Netapi64).

The loader XOR-decodes a .Netapi64 payload from %TEMP%, creates markers and a mutex, and injects the DLL into a host via .NET AppDomainManager. The backdoor reads a three-part config (<OpenAI_API_Key>|<Dictionary_Key>|<Proxy>), optionally routes through a proxy, and identifies the infected host (Base64 hostname).
“The dynamic link library (DLL) is heavily obfuscated using Eazfuscator.NET and is designed for stealth, persistence, and secure communication using the OpenAI Assistants API. Netapi64.dll is loaded at runtime into the host executable via .NET AppDomainManager injection, as instructed by a crafted .config file accompanying the host executable.” reads the report published by Microsoft.
SesameOp queries OpenAI for vector stores and Assistants, using Assistants’ description fields as simple command flags (SLEEP, Payload, Result). For Payloads the backdoor fetches messages by thread and message IDs; each message contains a Base64 AES key (RSA-encrypted) and an AES/GZIP-compressed payload. The implant decrypts, decompresses and parses the payload into a dictionary, then dynamically loads an embedded .NET module (via reflection) and executes commands through a JScript engine (Eval). Results are compressed, AES-encrypted, RSA-wrapped, Base64-encoded and posted back to OpenAI as messages. The backdoor then creates or updates an Assistant and vector-store entries to signal readiness.
Overall, SesameOp combines layered encryption, compression, reflective loading and living-off-the-land injection to hide C2 traffic inside legitimate OpenAI Assistants functionality and maintain stealthy, persistent control.
The origin of the malware is still unclear. Microsoft shared its findings with OpenAI, which then disabled the attackers’ API key and account.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, SesameOp)
如有侵权请联系:admin#unsafe.sh