嗯,用户让我帮忙总结一下这篇文章的内容,控制在一百个字以内。首先,我需要仔细阅读文章,了解其主要内容。文章主要讲述了2025年10月发生的多起重大数据泄露事件,涉及大学、航空公司、医疗机构和企业系统等。这些事件暴露了数百万条记录,并突出了第三方风险、延迟补丁、暴露的凭证和未监控的云存储等问题。 接下来,文章详细列举了几个主要的数据泄露事件,包括西方悉尼大学、澳大利亚航空、西蒙医疗成像公司、Gmail密码泄露以及甲骨文的零日漏洞利用活动等。每个案例都揭示了组织在安全方面的不足以及领导者可以采取的不同措施。 此外,文章还提到了美国多个地方政府遭遇网络攻击,导致关键服务中断;甲骨文E-Business Suite客户受到勒索攻击;F5源代码被窃取等事件。这些事件强调了持续监控、及时漏洞情报和优先处理风险的重要性。 最后,用户要求总结控制在100字以内,并且不需要特定的开头。因此,我需要将所有关键点浓缩到简洁的描述中,确保涵盖主要事件和问题。 </think> 2025年10月发生多起重大数据泄露事件,涉及大学、航空公司、医疗机构和企业系统等。泄露原因包括第三方风险、延迟补丁、暴露凭证及云存储问题。案例包括西方悉尼大学、澳大利亚航空、西蒙医疗成像公司等。这些事件凸显了持续监控和及时漏洞管理的重要性。 2025-10-30 16:12:59 Author: securityboulevard.com(查看原文) 阅读量:10 收藏
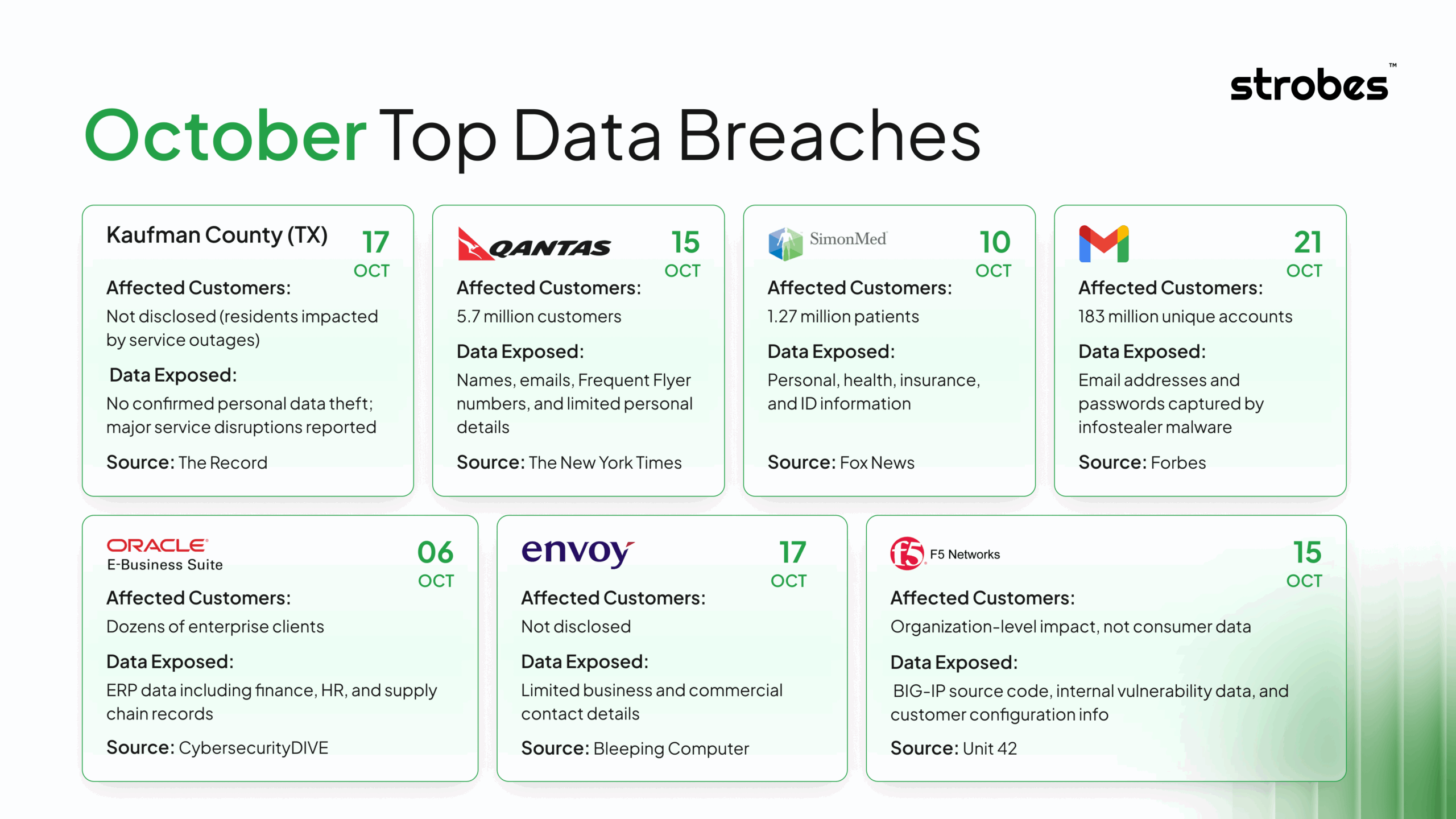
October 2025 brought significant data breaches. From universities and airlines to healthcare providers and enterprise systems, multiple high-impact incidents exposed millions of records across industries. These breaches highlight recurring issues, such as third-party risks, delayed patching, exposed credentials, and unmonitored cloud storage, all of which continue to challenge organizations of every size.
In this blog, we’ve summarized the top data breaches of October 2025, including Western Sydney University, Qantas Airways, SimonMed Imaging, Gmail Infostealer leaks, and Oracle’s zero-day exploitation campaign. Each case reveals critical insights into where organizations went wrong and what security leaders can do differently.
1. Cyber incidents in Texas, Tennessee, and Indiana disrupted key local government services
Incident Overview
Multiple U.S. municipalities reported cyber incidents in October 2025 that took down public-facing systems and slowed routine services. Kaufman County in Texas reported a cyberattack that disrupted several county systems. The City of La Vergne in Tennessee took systems offline after detecting unusual activity and later confirmed outages that affected payments and court operations. DeKalb County in Indiana disclosed a countywide cyber incident that hindered internal access and logins. Emergency services continued operating in all three locations.
What data was exposed
Officials have not confirmed any theft of personal data. Reports focus on service disruption, system lockouts, and payment portal downtime while investigations are ongoing.
Number of affected individuals
Not disclosed. The incidents primarily impacted residents’ ability to access services such as bill payments, property tax payments, and court schedules.
Business impact (service impact)
- Kaufman County, TX: Several county systems were taken down; courthouse computers were affected. Sheriff’s Office and 911 were not impacted.
- La Vergne, TN: City offices closed for several days. Online water and property tax payments were unavailable; the city moved to checks or money orders, paused late fees, and postponed court hearings.
- DeKalb County, IN: Employees could not sign in to systems, phone lines for some offices were affected, and network drives were unavailable; 911 remained operational.
Government response
All three jurisdictions engaged law enforcement and external cybersecurity teams, took affected systems offline, and prioritized continuity of public safety. La Vergne publicly coordinated with the FBI and TBI and issued step-by-step service updates for residents.
Key lesson for public sector teams
City and county networks remain prime targets for disruptive attacks. Practical steps help reduce impact: strict network segmentation for finance and courts, tested offline payment procedures, regular immutable backups, practiced incident runbooks with law-enforcement contacts, and clear resident communications during outages. Strobes can help with continuous exposure management and prioritization across apps, endpoints, and third-party systems so teams fix what matters first and recover faster.
Sources: The Record
Date of breach: October 17, 2025.
2. Qantas Airways Data Breach via Third-Party Contact Centre
Incident Overview
Qantas detected unusual activity on a third-party customer-servicing platform used by one of its contact centres. The airline confirmed a cyber incident that exposed customer information. Core airline systems and safety were not affected. Later, portions of the stolen data were posted on the dark web.
What Data was Exposed
Names, email addresses, Qantas Frequent Flyer numbers, and for a subset of customers, phone numbers, dates of birth, and home addresses. Qantas said payment data, passport numbers, and account passwords were not in the impacted system.
Number of Affected Individuals
Forensic updates indicate about 5.7 million customer records in scope. Initial estimates said up to 6 million.
Business Impact
Operations continued without disruption. The incident triggered regulatory notifications, customer support programs, and ongoing monitoring after threat actors released data publicly months later. Reputational risk and potential compliance exposure remain key concerns.
Company Response
Qantas contained the affected platform, stood up dedicated help pages and lines, began notifying customers, and worked with cybersecurity experts, the Australian Cyber Security Centre, and federal police. It continues to provide updates as analysis progresses.
Key Lesson
Third-party platforms can hold high-value customer data. Enforce vendor security controls, monitor access, segment data, and validate what sensitive fields are stored off-core to limit impact if a vendor is compromised.
Source: The New York Times
Date of Breach: 15 October 2025.
3. SimonMed Imaging Healthcare Data Breach: Medusa Ransomware Claim, 1.27M Impacted
Incident Overview
SimonMed Imaging reported a cyberattack first surfaced via a vendor alert on January 27, 2025. The next day, SimonMed found suspicious activity in its own network. Investigations indicate data was exfiltrated between January 21 and February 5, 2025. The Medusa ransomware group claimed responsibility.
What Data Was Exposed
SimonMed’s notices state that exposed data varies by individual and may include names, addresses, dates of birth, dates of service, provider details, medical record numbers, patient numbers, diagnosis and treatment information, medications, health insurance information, and driver’s license numbers. The threat group additionally claimed it stole ID scans, payment details, account balances, medical reports, and even raw imaging files.
Number of Affected Individuals
Approximately 1.27 million people.
Business Impact
Risks include regulatory scrutiny and reporting obligations, potential class-action litigation, higher incident response and notification costs, and reputational harm due to the nature of PHI exposed. Medusa also claimed theft of more than 200 GB of data and issued ransom demands, amplifying extortion and data-leak risks.
Company Response
SimonMed initiated password resets, enforced multi-factor authentication, deployed enhanced endpoint monitoring, and restricted third-party vendor access. The organization notified authorities and began mailing notification letters, offering identity theft and credit monitoring services to affected individuals.
Key Lesson
Third-party incidents can quickly become enterprise incidents. Continuous monitoring of vendor access, rapid containment, and tested response runbooks are essential to reduce dwell time and limit sensitive PHI exposure. Strobes recommends vendor risk mapping, least-privilege access, and automated alerting tied to data exfiltration signals.
Source: Fox News
Date of Breach: 10 October, 2025.
4. Gmail Passwords Included in 183 Million Account Infostealer Leak
Incident Overview
A large dataset built from infostealer malware logs was found and analyzed, then added to Have I Been Pwned as “Synthient Stealer Log Threat Data.” It contains roughly 183 million unique email accounts with passwords captured from infected devices. This was not a direct breach of Google’s systems. Google has stated there is no Gmail-specific hack and that reports claiming otherwise are inaccurate.
What Data was Exposed
Email addresses, the passwords used with those addresses, and the login site metadata where the credentials were entered, which can include Gmail among many services.
Number of Affected Individuals
183,000,000 unique email addresses. About 16.4 million of these were not seen in prior public breach corpora.
Business Impact
Attackers can attempt account takeover using valid email-password pairs, try the same pairs on other services, and automate further access if users reused passwords. For companies, this increases risk of unauthorized access to mail, cloud, and apps tied to employee email.
Company Response
Google said there was no new Gmail breach, calling reports of “millions of Gmail passwords leaked” inaccurate. Google highlighted existing safeguards, such as automated protections and guidance to use 2-Step Verification or passkeys.
Key Lesson
Compromise often starts on the user device. Infostealers grab credentials at the moment of login. Unique passwords per service plus MFA or passkeys limit blast radius, even when logs leak.
Source: Forbes
Date of Breach: October 21, 2025.
5. Extortion campaign targeting Oracle E-Business Suite customers linked to a zero-day
Incident Overview
From late September to early October 2025, Oracle E-Business Suite (EBS) customers received extortion emails claiming theft of company data. Google’s Mandiant linked the activity to operators using the CL0P brand and to exploitation of an Oracle EBS zero-day, later tracked as CVE-2025-61882. Oracle confirmed the campaign and issued an emergency alert with patch guidance.
What Data was Exposed
Oracle and researchers reported significant data theft at some victims, varying by the EBS modules in use. Because EBS powers finance, HR, supply chain, and order management, exposed data could include ERP records tied to those functions. Specific datasets differ by customer environment.
Number of Affected Individuals
Unknown. Public reporting states “dozens of organizations” were impacted, but no reliable count of individual records is available.
Business Impact
Attackers achieved unauthenticated remote code execution on exposed EBS components, enabling data exfiltration and large-scale extortion. Impact included theft of business records, executive pressure via ransom emails, urgent downtime for patching and investigation, and potential contractual or regulatory exposure.
Company Response
Oracle issued a Security Alert for CVE-2025-61882, urged immediate action, and provided indicators of compromise and version guidance. Researchers published technical analysis and detection tips. Customers were advised to apply the alert, verify supported versions, audit internet exposure of EBS, and hunt for IOCs.
Key Lesson
Treat ERP suites as high-value internet-facing targets. Keep EBS on supported versions, restrict external access, apply Oracle alerts quickly, and monitor for unusual outbound activity from BI Publisher and Concurrent Processing components.
Source: CybersecurityDIVE
Date of Breach: October 6, 2025.
6. American Airlines Subsidiary Envoy Air Confirms Oracle E-Business Suite Data Theft Attack
Incident Overview
Envoy Air confirmed that attackers accessed data from its Oracle E-Business Suite (EBS) environment during an extortion campaign tied to Oracle EBS flaws. Reports link the activity to the Cl0p group and to zero-day CVE-2025-61882 that was exploited from early August 2025 before Oracle issued a patch. Envoy was named after “American Airlines” appeared on Cl0p’s leak site, but the affected system belongs to Envoy.
What Data was Exposed
Envoy stated that a limited amount of business information and commercial contact details may have been compromised. The company said sensitive or customer data were not impacted based on its review.
Number of Affected Individuals
Not disclosed as of the latest public updates.
Business Impact
The incident triggered an internal investigation and law-enforcement notification. Flight operations and customer-facing systems were not reported as affected. Broader industry reporting indicates the campaign hit dozens of Oracle EBS customers.
Company Response
Envoy confirmed the breach, is investigating, and engaged law enforcement. Oracle issued a Security Alert and patch for CVE-2025-61882 and later additional fixes for related issues, urging customers to apply updates promptly.
Key Lesson
Treat ERP and back-office platforms as high-value targets. Apply Oracle EBS security alerts without delay, monitor for abnormal activity in EBS, and restrict access using least privilege and network segmentation.
Source: Bleeping Computer
Date of Breach: October 17, 2025
7. Nation-State Actor Steals F5 Source Code and Undisclosed Vulnerabilities
Incident Overview
On October 15, 2025, F5 disclosed that a highly sophisticated nation-state actor maintained long-term access to certain internal systems. The intruder stole portions of BIG-IP source code, internal details about yet-to-be-disclosed vulnerabilities, and some customer configuration or implementation data. U.S. CISA issued an Emergency Directive requiring rapid mitigation due to the risk this poses to federal and enterprise networks.
What Data was Exposed
• Portions of BIG-IP proprietary source code.
• Internal documentation about undisclosed vulnerabilities.
• Customer configuration and implementation information in some cases.
Number of Affected Individuals
Not a consumer data exposure. Impact is organization-level, affecting environments that deploy F5 BIG-IP and related platforms. Exact customer count not disclosed.
Business Impact
• Elevated risk of exploit development against F5 devices using stolen code and vulnerability intelligence.
• Potential lateral movement, credential and API key exposure, and targeted intrusions against networks that rely on BIG-IP.
• Urgent patching, inventory, and threat-hunting required, with possible downtime and incident-response costs.
Company Response
F5 reported the breach, stated there was no evidence of supply-chain tampering, and released security updates and guidance. The company says the incident’s impact is limited, though investigations continue.
Key Lesson
Treat vendor platform compromises as high-impact third-party risk. Maintain a full asset inventory of F5 devices, apply vendor updates rapidly, rotate sensitive keys, and hunt for unusual access paths tied to BIG-IP.
Source: Unit 42
Date of Breach: October 15, 2025.
Conclusion
Attackers exploit gaps faster than teams can react. Whether it’s a misconfigured third-party platform, exposed credentials, or an unpatched zero-day, every weakness can turn into a large-scale incident if not addressed early.
Organizations need continuous visibility, timely vulnerability intelligence, and smarter prioritization to prevent these outcomes. With Strobes Security, you can proactively identify, assess, and remediate risks before they escalate. Strengthen your exposure management strategy today. Book a demo with Strobes to see how automation and intelligence can simplify your security operations.
The post Top Data Breaches of October 2025 appeared first on Strobes Security.
*** This is a Security Bloggers Network syndicated blog from Strobes Security authored by Likhil Chekuri. Read the original post at: https://strobes.co/blog/top-data-breaches-of-october-2025/
如有侵权请联系:admin#unsafe.sh