好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。首先,我得仔细阅读文章,理解其主要内容。 文章讲的是最近注意到一些新的HTTP请求头,比如X-Request-Purpose: Research,以及X-Hackerone-Research、X-Bugcrowd-Ninja和X-Bug-Hunter这些头。这些头的目的是标识请求是作为漏洞赏金活动的一部分发送的。有些公司要求在漏洞赏金中使用这些头,比如Web.com在Bugcrowd上的页面就有提到。 作者提到他们在蜜罐中也看到了这些头,虽然有点奇怪,但可能是因为蜜罐属于企业网络的一部分,在漏洞赏金范围内。如果这些头是真实的,那么研究人员的用户名应该是“plusultra”,但也不能保证真实性,因为任何人都可以发送这些头。 从防御角度看,作者建议忽略这些请求,不要区别对待有无这些头的请求。同时,作者还建议网站设置/.well-known/security.txt文件。 现在我需要把这些信息浓缩到100字以内。重点包括:新HTTP请求头用于标识漏洞赏金活动、部分公司要求使用、蜜罐中出现的情况、防御建议以及设置security.txt的重要性。 可能的结构:介绍新HTTP头及其用途,提到蜜罐中的情况和防御建议,最后提到设置security.txt文件。 检查字数是否符合要求,并确保语言简洁明了。 </think> 文章描述了近期发现的新HTTP请求头(如X-Request-Purpose: Research和X-Hackerone-Research等),用于标识漏洞赏金活动。这些头可能由研究人员发送以表明身份。尽管蜜罐中出现此类请求有些异常,但从防御角度看应正常处理。文章还建议网站设置/.well-known/security.txt文件以提高安全性。 2025-10-30 13:22:19 Author: isc.sans.edu(查看原文) 阅读量:6 收藏
This week, I noticed some new HTTP request headers that I had not seen before:
X-Request-Purpose: Research
and
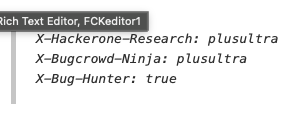
X-Hackerone-Research: plusultra
X-Bugcrowd-Ninja: plusultra
X-Bug-Hunter: true
The purpose of these headers appears to be to identify them as being sent as part of a bug bounty. Some companies request the use of these headers as part of their bug bounty. For example, see Web.com's Bugcrowd page [1]. If you see these headers, there is a good chance that the request was sent as part of a bug bounty. At the same time, it is a bit odd that we see these in our honeypots. But some of our honeypots are part of corporate networks, and it is possible that they are in scope for a bug bounty. If the header is genuine, the username of the researcher would be "plusultra". On the other hand, there is no guarantee. Anybody may send this header.
The idea of sending a header like this makes some sense. This way, it is easier for a company to contact a researcher in case the scans are causing any issues. From a defensive point of view, you should probably just ignore these requests. I would not treat them any differently from any request without the header. Blocking requests with these headers does not make a lot of sense, nor does allowing them. Just block (or allow them) based on the remainder of the request.
And, for any website out there that doesn't have it yet: Setting up a /.well-known/security.txt file makes a lot of sense [2].
[1] https://bugcrowd.com/engagements/webdotcom-vdp
[2] https://datatracker.ietf.org/doc/rfc9116/
--
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
如有侵权请联系:admin#unsafe.sh