
嗯,用户让我总结一下这篇文章的内容,控制在100字以内,而且不需要特定的开头。首先,我需要通读整篇文章,抓住主要观点。 文章主要讲的是API在现代软件中的重要性,以及它们带来的安全风险。API允许数据在不同系统之间无缝交换,但这也让它们成为攻击者的目标。文章列举了几个常见的API安全攻击向量,比如Broken Object Level Authorization、注入漏洞、数据过多暴露等。 接下来,我需要把这些要点浓缩到100字以内。要确保涵盖API的重要性、带来的安全风险以及具体的攻击类型。同时,语言要简洁明了,直接描述内容。 可能会先写API的重要性,然后提到它们面临的安全威胁,接着列举几个主要的攻击向量,最后提到组织如何防范这些风险。这样结构清晰,信息全面。 最后检查一下字数,确保不超过限制,并且没有使用任何不需要的开头语句。 </think> 文章探讨了API在现代软件生态系统中的重要性及其面临的安全威胁。API通过促进数据交换和系统集成推动了创新和互操作性,但也成为攻击者的目标。常见攻击向量包括对象级别授权不足、注入漏洞、数据过多暴露等。文章强调了加强认证、授权、输入输出验证及持续监控的重要性,并建议组织采用多层次防御策略以保护敏感数据。 2025-10-28 06:0:4 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
APIs have become the critical enablers of modern software ecosystems, powering seamless data exchange and integration across applications, platforms, and devices. From payment processing and social media to healthcare, IoT, and enterprise systems, APIs allow organizations to deliver functionality efficiently while connecting diverse software components. This growing interconnectivity also expands the surface for API security attack vectors, exposing sensitive data and critical business processes to potential exploitation if not properly secured.
At their core, APIs consist of a set of definitions, protocols, and rules that determine how software systems communicate and interact. They don’t just provide connectivity; they govern the flow of information—controlling the types of requests made, how those requests are handled, and which data formats are permitted.
By allowing organizations to share data and functionality with customers, partners, and external systems, APIs have accelerated innovation and interoperability. Whether open, closed, public, or private, most APIs adhere to architectural standards such as REST, SOAP, or GraphQL to ensure consistent communication.
As APIs bridge systems and data sources, they also become prime targets for attackers seeking to exploit misconfigurations, weak authentication, or poor access control. In this blog, we’ll explore the most common API security attack vectors that can expose sensitive data—and how organizations can mitigate these risks to safeguard their digital assets.
API Attack Vectors that lead to Sensitive Data Exposure
APIs are essential for modern software, enabling seamless connectivity and data sharing between applications. However, this increased accessibility also introduces significant security risks. Understanding the most common API security attack vectors is essential to prevent sensitive data from being exposed to attackers.
Broken Object Level Authorization (BOLA/IDOR)
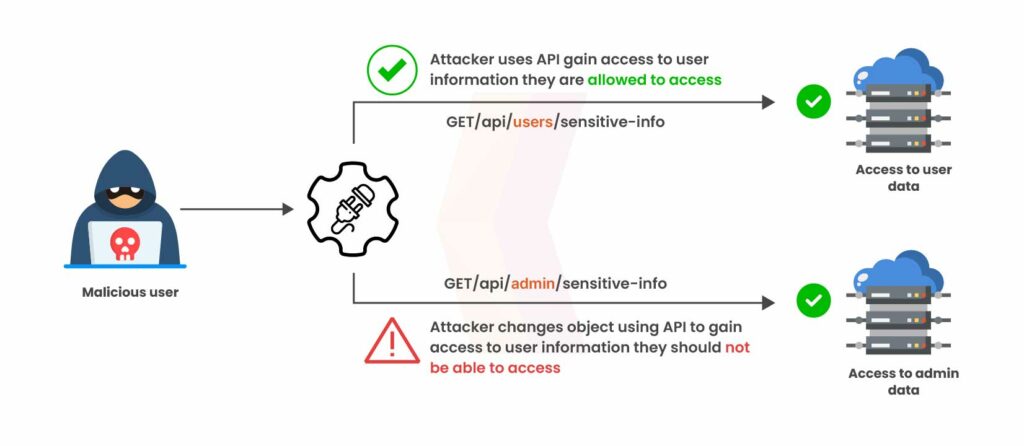
What it is
BOLA occurs when an API trusts client-supplied object identifiers (IDs) without enforcing per-object server‑side authorization. Attackers manipulate IDs to access records that belong to other users.
How it leaks data
Changing /invoices/124 → /invoices/123 (or iterating UUIDs) returns other users’ PII, financials, or confidential documents.
Indicators
Sequential ID access returns valid data; low-entropy IDs (incrementing integers) in responses; absence of access checks tied to the authenticated principal.
Mitigations
Enforce authorization on every request using the authenticated principal and resource owner mapping. Use opaque identifiers or UUIDs, implement allow-lists for fields returned, and include automated tests that iterate IDs to check access controls.
Injection Flaws
What it is
Injection is one of the common API security attack vectors where unsanitized input is embedded into queries or commands, enabling attackers to modify query logic or execute arbitrary statements.
How it leaks data
An injection can allow attackers to retrieve entire tables, bypass filters, or run OS commands that read sensitive files.
Indicators
Unusual query results, error messages revealing SQL/DB structure, abnormal data volumes returned from an endpoint, or suspicious parameter payloads.
Mitigations
Use parameterized queries/prepared statements or safe ORM APIs; validate and canonicalize inputs; apply least-privilege DB roles; sanitize outputs; implement query timeouts and row limits to reduce blast radius.
Excessive Data Exposure
What it is
APIs return more data than required by clients — internal IDs, debug fields, config values, or PII — because response schemas aren’t restricted.
How it leaks data
Endpoints intended for UI consumption might include internal columns (e.g., ssn, internal_notes, debug_info), which get leaked to clients or third parties.
Indicators
Responses contain unexpected keys, stack traces, environment variables, or database identifiers; frontend code accessing more fields than necessary.
Mitigations
Apply strict response schemas and field-level whitelists per endpoint and client type; perform output filtering on the server; conduct code reviews focusing on DTOs and serialization; run automated scans to detect sensitive fields in responses.
Inadequate Rate Limiting and Enumeration Attacks
What it is
APIs without proper throttling let attackers enumerate resources or exfiltrate data in bulk by making massive or distributed requests.
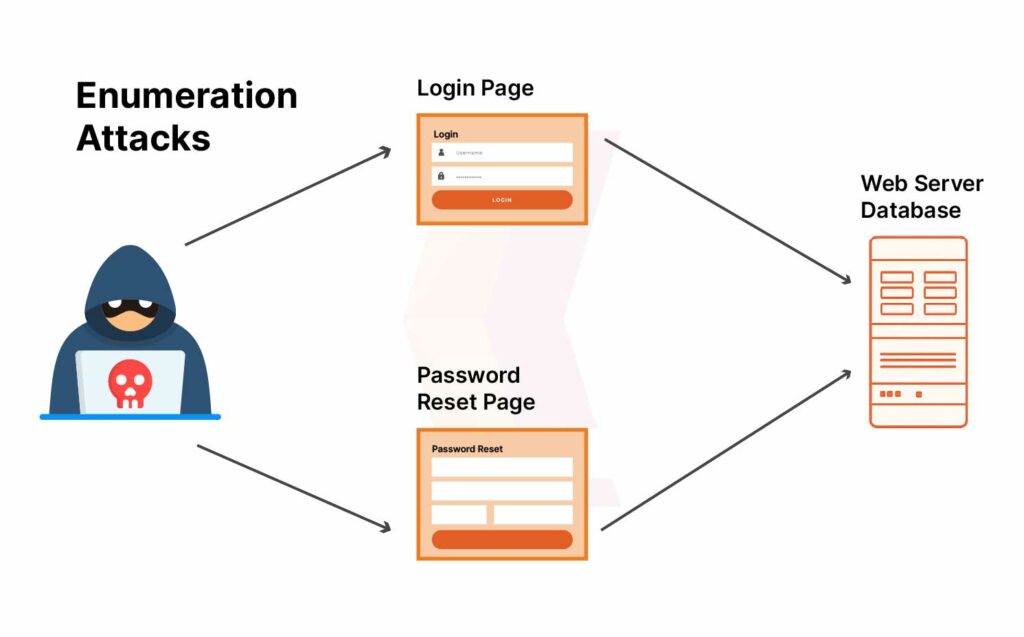
How it leaks data
Automated scripts can iterate user IDs, emails, or endpoints to harvest lists of users, email addresses, or other PII.
Indicators
High request volumes, patterns of sequential or patterned requests, slow credential stuffing or enumeration attempts, sudden uptick in API calls from single or distributed origins.Mitigations
Implement per-user and per-IP rate limits, behavioral usage restriction, CAPTCHA gates for suspicious flows, and back-off strategies. Monitor for enumeration patterns and implement account lockouts.
Insufficient Loggiing, Monitoring and Alerting
What it is
Insufficient logging and monitoring is a key API security attack vector where access to sensitive fields and privileged operations is not logged, allowing data exfiltration to proceed unnoticed.
How it leaks data
Attackers can slowly siphon data without triggering alerts if sensitive endpoints and field access aren’t audited.
Indicators
Lack of audit trails for sensitive API calls, sparse logs for data exports, delayed or no alerts on anomalous access patterns.
Mitigations
Log access to sensitive resources and fields with contextual metadata (actor, IP, user agent, request payload hash); use immutable storage for audit logs; implement automated detection for abnormal access volumes or patterns; integrate SIEM and anomaly detection.
Workflow Tampering
What it is
Attackers exploit legitimate but unintended application flows to access or escalate access to sensitive data — e.g., abusing refund flows to retrieve order details or manipulating approval steps.
How it leaks data
Abuse of logic can bypass normal checks and surface sensitive records without triggering typical security controls.
Indicators
Unusual sequences of API calls that deviate from documented flows, unexpected data exposure during edge-case operations, or combination of valid API calls producing sensitive outputs.Mitigations
Threat model business logic flows, run abuse-case tests, apply transaction-level authorization and validation, and instrument the app to detect atypical sequences of operations.
Why APIs are Prime Targets?
APIs are a prime target for attackers because they provide direct access to backend data, workflows, and business logic, often without the same level of security scrutiny applied to frontend applications. Their complexity, rapid deployment, and constant evolution make them both easier to exploit and harder to secure.
Attackers focus on APIs because they represent high-value entry points, and they know where to look. Key reasons include:
- Exposure of internal logic and data structures: APIs often reveal object IDs, actions, and relationships, giving attackers the exact context they need to exploit API security attack vectors.
- Rapid growth and endpoint sprawl: New API endpoints are added with every sprint, and security reviews frequently lag behind development.
- Under-tested surfaces: Many automated scanners still treat APIs like traditional web pages, missing critical logic flaws that constitute common API security attack vectors.
- Widespread integrations: APIs connect mobile apps, third-party services, and internal tools. A single overlooked integration can significantly expand the attack surface.
- Abundance of edge cases: Rate limits, token refresh flows, and undocumented parameters provide fertile ground for probing and exploitation.
Join our weekly newsletter and stay updated
Conclusion
APIs are the backbone of modern software ecosystems, enabling seamless data exchange and integration, but they also present a wide range of security challenges. As we’ve explored, API security attack vectors—from Broken Object Level Authorization and injection flaws to excessive data exposure, workflow manipulation, and insufficient logging—can lead to the compromise of sensitive data if left unchecked.
Organizations must adopt a defense-in-depth approach, combining strong authentication and authorization, strict input/output validation, rate limiting, thorough logging, and continuous monitoring. Regular testing, including API-specific pentests and business logic abuse simulations, is critical to identify and remediate vulnerabilities before attackers can exploit them.
FAQs
- Which API security attack vectors are most commonly exploited?
The most prevalent API security attack vectors include BOLA/IDOR, mass assignment, broken authentication, excessive data exposure, rate-limiting bypasses, and business logic flaws. These vulnerabilities typically arise from insecure design and weak access control measures rather than purely technical bugs.
- How can I test my API safely without impacting the production environment?
Conduct testing in a staging environment that replicates your production setup, including real authentication and traffic conditions. Utilize API-focused testing tools capable of context-aware, non-intrusive scans to simulate attacks safely without affecting performance or compromising data integrity.
The post API Security Attack Vectors That Expose Sensitive Data appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/api-security-attack-vectors-that-expose-sensitive-data/
如有侵权请联系:admin#unsafe.sh
