嗯,用户让我用中文总结一下这篇文章,控制在100字以内,而且不需要特定的开头。首先,我得通读一下文章内容,理解主要信息。 文章讲的是一个钓鱼邮件的案例,邮件的主题在Outlook中看起来很奇怪。打开后发现主题中有不可见字符,具体是软连字符(Unicode U+00AD)。作者分析了邮件头,发现主题被分成了两个MIME编码词,使用了Base64编码。这种技术用于绕过邮件过滤机制,通常用于邮件正文,但用于主题比较少见。 接下来,我需要提取关键点:钓鱼邮件、主题中的软连字符、MIME编码、绕过过滤机制、少见的应用场景。然后把这些点浓缩成100字以内的中文。 可能的结构是:描述现象、技术手段、目的和独特性。这样就能全面覆盖主要内容了。 </think> 文章描述了一起钓鱼邮件案例,其中邮件主题通过MIME编码隐藏了软连字符(Unicode U+00AD),导致Outlook显示异常。此技术用于绕过邮件过滤机制,尽管在邮件正文中常见,但应用于主题较为少见。 2025-10-28 09:38:20 Author: isc.sans.edu(查看原文) 阅读量:9 收藏
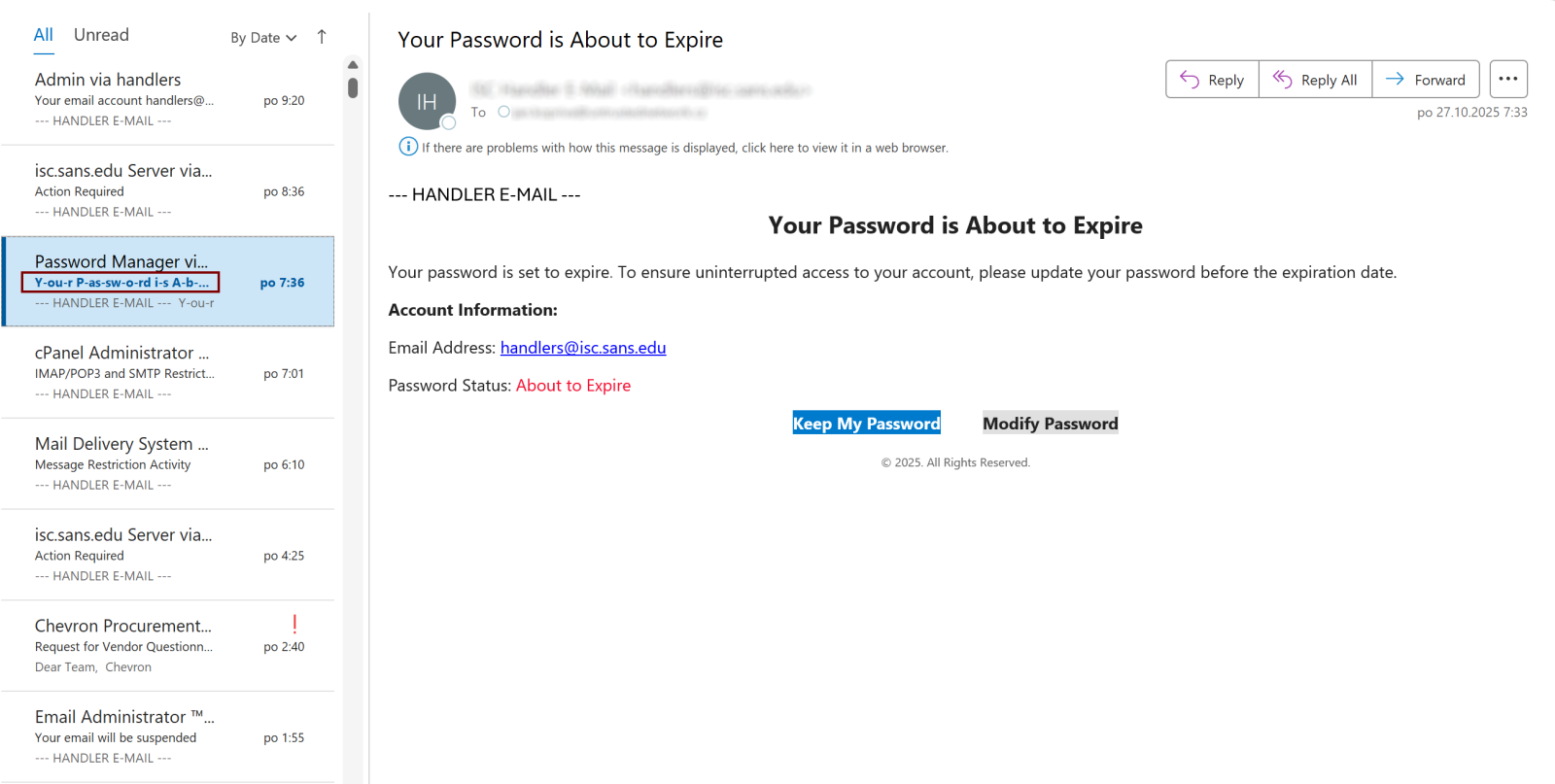
While reviewing malicious messages that were delivered to our handler inbox over the past few days, I noticed that the “subject” of one phishing e-mail looked quite strange when displayed in the Outlook message list…
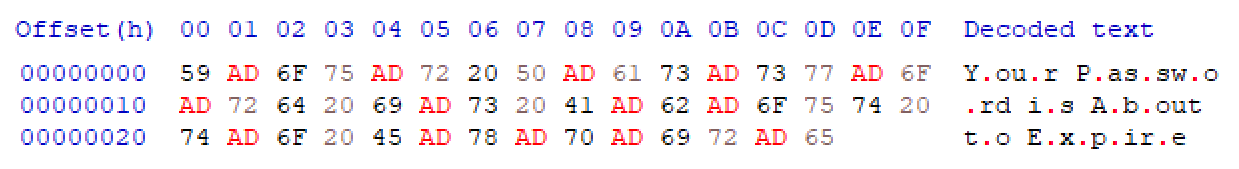
As you can see, once the message was open, the subject was displayed as a normal, readable text. This suggested that some invisible characters were likely present…
A quick look at the e-mail headers proved this to be the case. The subject was composed of the following two lines:
Subject: =?UTF-8?B?WcKtb3XCrXIgUMKtYXPCrXN3wq1vwq1yZCBpwq1zIEHCrWLCrW91dCA=?=
=?UTF-8?B?dMKtbyBFwq14wq1wwq1pcsKtZQ==?=This formatting meant that the subject was included in the message in a MIME “encoded-word” format, which is described in RFC 2047 as having the following structure[1]:
encoded-word = "=?" charset "?" encoding "?" encoded-text "?="In our case, the subject therefore consisted of two encoded words containing text written in the UTF-8 character set, which has been Base64 encoded.
Once both lines were decoded, one could clearly see that an invisible character was indeed being used in multiple places in the strings – specifically the soft hyphen, which has a Unicode code point U+00AD, and which is more commonly used as the ­ HTML entity[2].
Although soft hyphens aren’t – strictly speaking – invisible, Outlook as well as most other e-mail clients don’t render them as visible text in most cases.
The use of the soft hyphen character – combined with splitting the subject into multiple MIME encoded-words – was clearly intended as an attempt at bypassing e-mail filtering mechanisms that are supposed to automatically detect potentially malicious messages.
Why is this approach noteworthy?
Because although the use of invisible characters in phishing e-mails in general (and of the use of the “shy” character in particular[3]) is quite common when it comes to making the contents of e-mail messages less readable to security solutions, it is quite unusual to see it also applied to a subject of a message.
In fact, the only allusion to this technique I’ve been able to find with a quick Google search was a general mention in an article by Microsoft Threat Intelligence from 2021, which states that “In several observed campaigns, attackers inserted invisible Unicode characters to break up keywords in an email body or subject line in an attempt to bypass detection and automated security analysis”[4].
Since the use of invisible characters in e-mail subject lines doesn’t seem to be widely known, I have therefore decided that it would be worthwhile to dedicate this short diary to it.
It should be noted that the subject line wasn’t the only place where the soft hyphen character was used in the message – it was also heavily present in the text itself, where it was used to break up individual words…
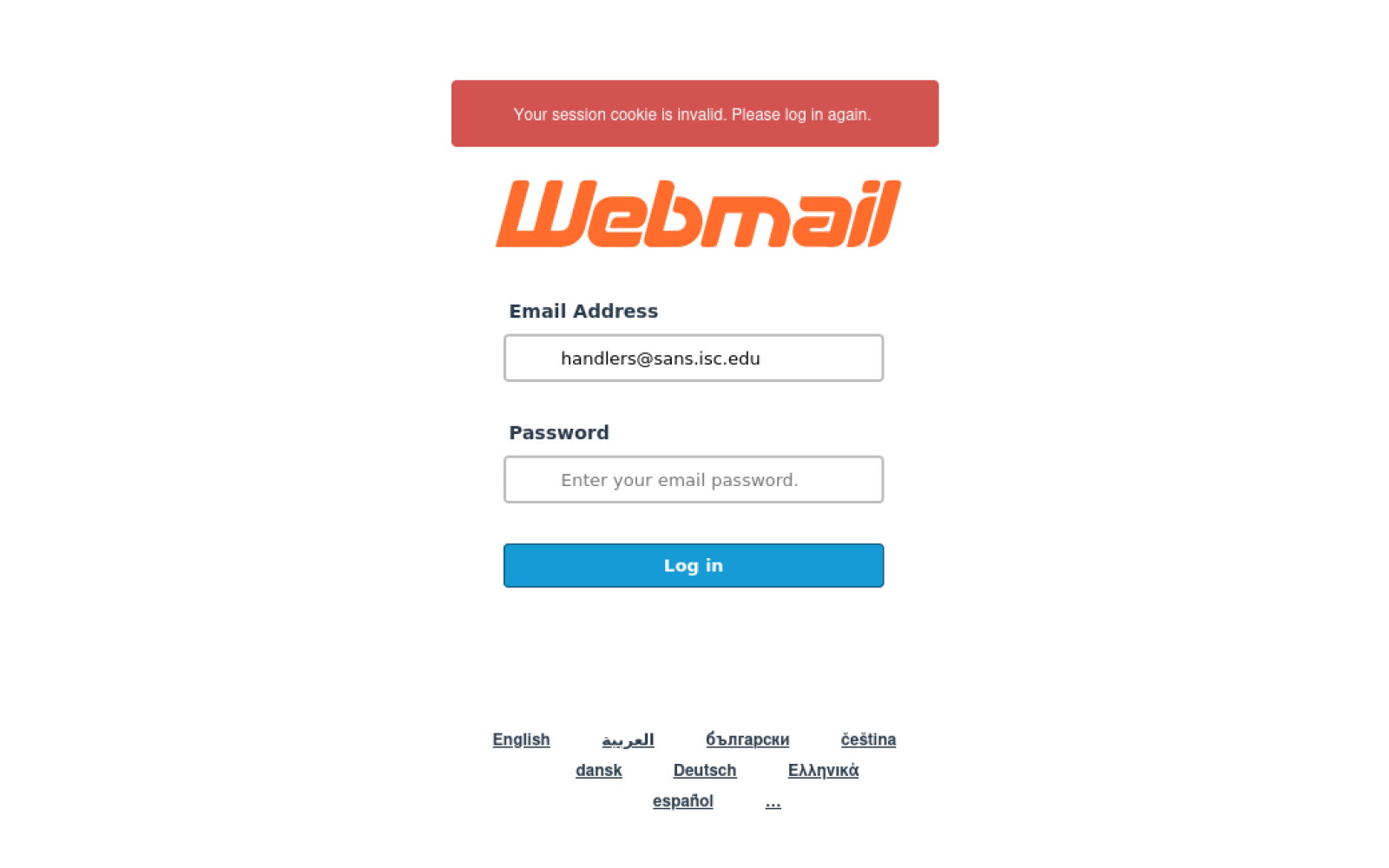
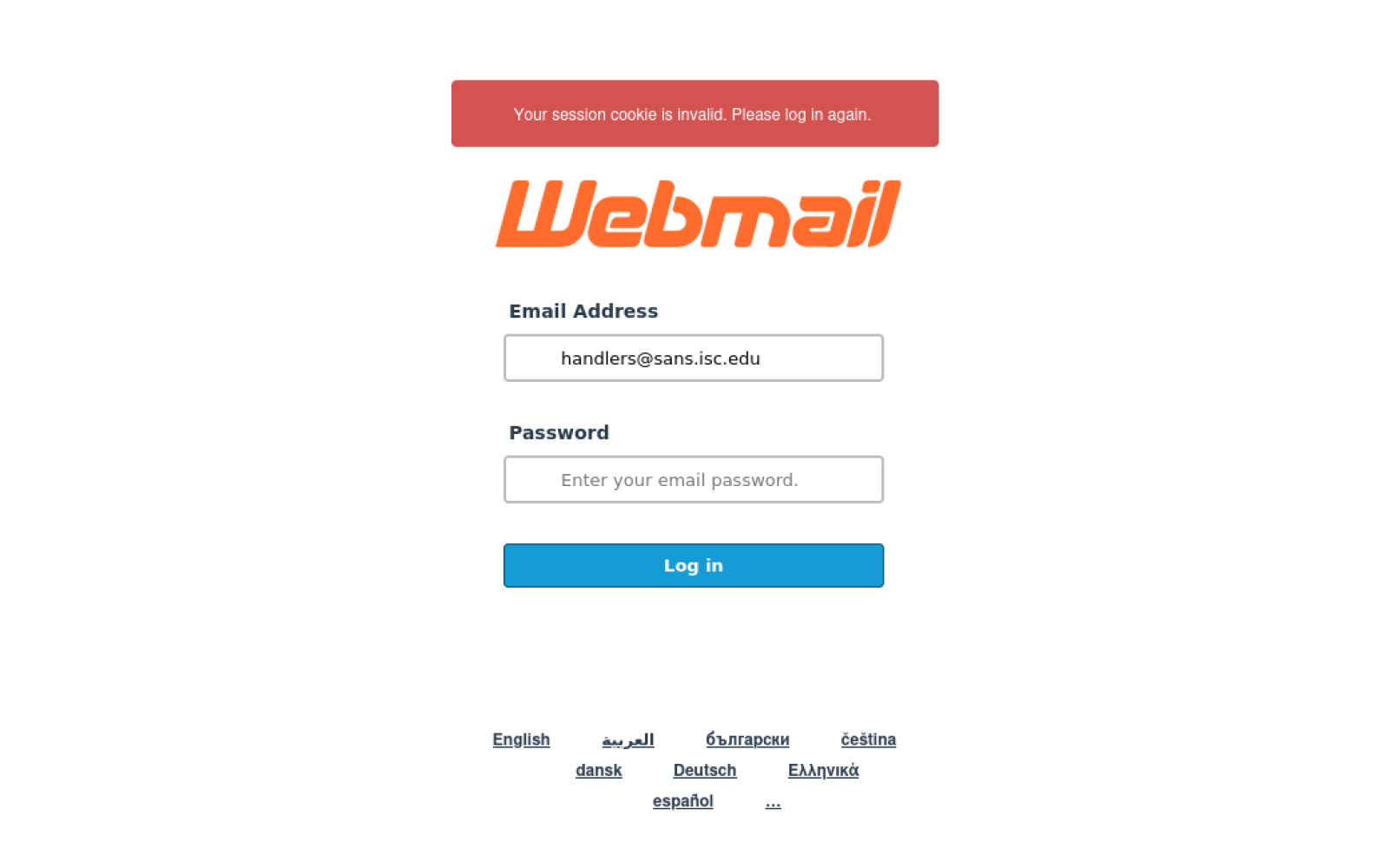
For completeness’s sake, we should also mention that the link in the phishing pointed to the URL hxxps[:]//stopsoriasis[.]co[.]il/Webmail/webmail.php?email=[[email protected]], where a generic “webmail login” credential stealing page was placed…
[1] https://datatracker.ietf.org/doc/html/rfc2047
[2] https://en.wikipedia.org/wiki/Soft_hyphen
[3] https://isc.sans.edu/diary/31626
[4] https://www.microsoft.com/en-us/security/blog/2021/08/18/trend-spotting-email-techniques-how-modern-phishing-emails-hide-in-plain-sight/
-----------
Jan Kopriva
LinkedIn
Nettles Consulting
如有侵权请联系:admin#unsafe.sh