文章探讨了网络安全问责制的重要性,强调CISO需将所有权分散至企业各部门,使安全成为日常活动的一部分。通过明确责任、优化流程和量化成果,企业可实现更快的补救、更少的审计问题及风险降低。文章还提供了实施步骤和工具支持。 2025-10-24 07:25:53 Author: securityboulevard.com(查看原文) 阅读量:0 收藏
The sharing of ownership is more secure within the company. There are still standards set by the CISO and the core program being executed, but business owners, product team, IT, data stewards, legal, procurement, and finance each have well defined responsibilities. This model transforms security into anything but a side task and makes it an everyday activity in relation to actual assets, services, and vendors. You have quicker remediation, less outdated content, less unexpected audit traces, and evidence of a risk reduction.
This blog describes the steps to construct that model in an easy manner. You will observe functions, procedures, and numbers that you can implement in a quarter. This is also where you will see how to relate the work to value using Cybersecurity Accountability and cybersecurity accounting so that the leaders can view cost, exposure, and outcome from the same perspective. The material is geared towards groups that desire less noise and more progress.
The Core Problem in Cybersecurity Accountability
When security sits only with the CISO, progress slows because the work does not live with the people closest to the systems, code, data, and vendors. Ownership blurs, queues grow, and audits become rework instead of a by-product of everyday activity. This section states the symptoms you can observe across teams.
- Tickets pile up because owners are unclear.
- Tool count grows while priorities fade.
- Auditors ask for evidence scattered across many systems.
- Releases slip due to late discoveries.
- Third-party risks get accepted without full context.
- This is not a tooling shortage. The real issue is weak ownership and an inconsistent operating rhythm.
These patterns slow delivery and raise exposure because handoffs, rules, and roles are loose. A single finding often spawns three tickets in three tools with no clear owner. Teams argue about severity instead of fixing the most exploitable issues first. Evidence gets rebuilt for audits rather than being captured as work happens. Vendor issues bounce between procurement, legal, and security without an agreed SLA, so nothing moves until someone escalates.
Shared ownership explained
Shared ownership implies that the business possesses its risks, and they are backed up by the security team. The CISO establishes the standard, writes risk rules, facilitates the weekly review and maintains the system of record. It is up to the business owners to either remediate or accept risk in their territory or not. This is an easy and feasible method.
Key principles of Cybersecurity Accountability:
- Service and asset ownership. Associate all risks with a product, service, dataset, vendor or control. Outside security, there is a named owner of each item.
- Product-centric work. Organize security tasks around products and services, not only around tools. This matches how teams plan sprints and budgets.
- Measurable outcomes. Track time to acknowledge, time to remediate, verification rates, and aging. Show these by team and product.
- Evidence as you work. Capture evidence inside normal workflows. Do not bolt on paperwork later.
- Clear handoffs. Define when security hands off to owners and when owners hand back after fixes or exceptions.
- Finance view. Apply cybersecurity accounting to connect exposure, remediation cost, run rate, and ROI. This is how leaders judge trade-offs.
Responsibility map that works
Use a short, unambiguous map that fits on one page. Keep job titles flexible. What matters is clarity.
- Product and engineering. Own secure design and release readiness. Keep defect SLAs by severity. Fix exposed and vulnerable bugs.
- IT and cloud. Own baselines for images, IaC modules, networks, and identity configs. Run change control and rollback plans. Keep guardrails active to prevent drift.
- Data owners. Sort data, authorize access, establish data retention, and verify data key management in services running on them.
- Procurement and legal. Trigger vendor evaluations, include data terms, and keep DPAs up to date. Track vendor remediation SLAs by tier.
- FinOps and PMO. Align budgets with risk work. Reserve capacity for remediation. Track the cost of delay using cybersecurity accounting.
- Security team. Write risk rules, correlate signals, validate true risk, run the weekly review, and operate the system of record.
A simple RACI pattern for top activities:
- Asset and service inventory. Responsible IT or platform. Accountable product owner. Consulted security. Informed finance.
- Intake and correlation. Responsible security. Accountable CISO. Consulted product teams.
- Prioritization rules. Responsible security. Accountable CISO. Consulted product, IT, legal.
- Remediation. Responsible product or IT owner. Accountable owner’s manager. Consulted security.
- Verification and retesting. Responsible security or pentest partner. Accountable CISO. Consulted product.
- Exception management. Responsible owner. Accountable business sponsor. Consulted legal and security.
- Vendor risk tracking. Responsible procurement. Accountable vendor manager. Consulted security and legal.
- Guardrails and drift control. Responsible platform. Accountable head of platform. Consulted security.
- SDLC quality gates. Responsible product team. Accountable engineering lead. Consulted security.
- Leadership reporting. Responsible CISO. Accountable CEO. Consulted finance, PMO, and product.
Operating model for day-to-day work
A predictable seven-step flow keeps the program moving.
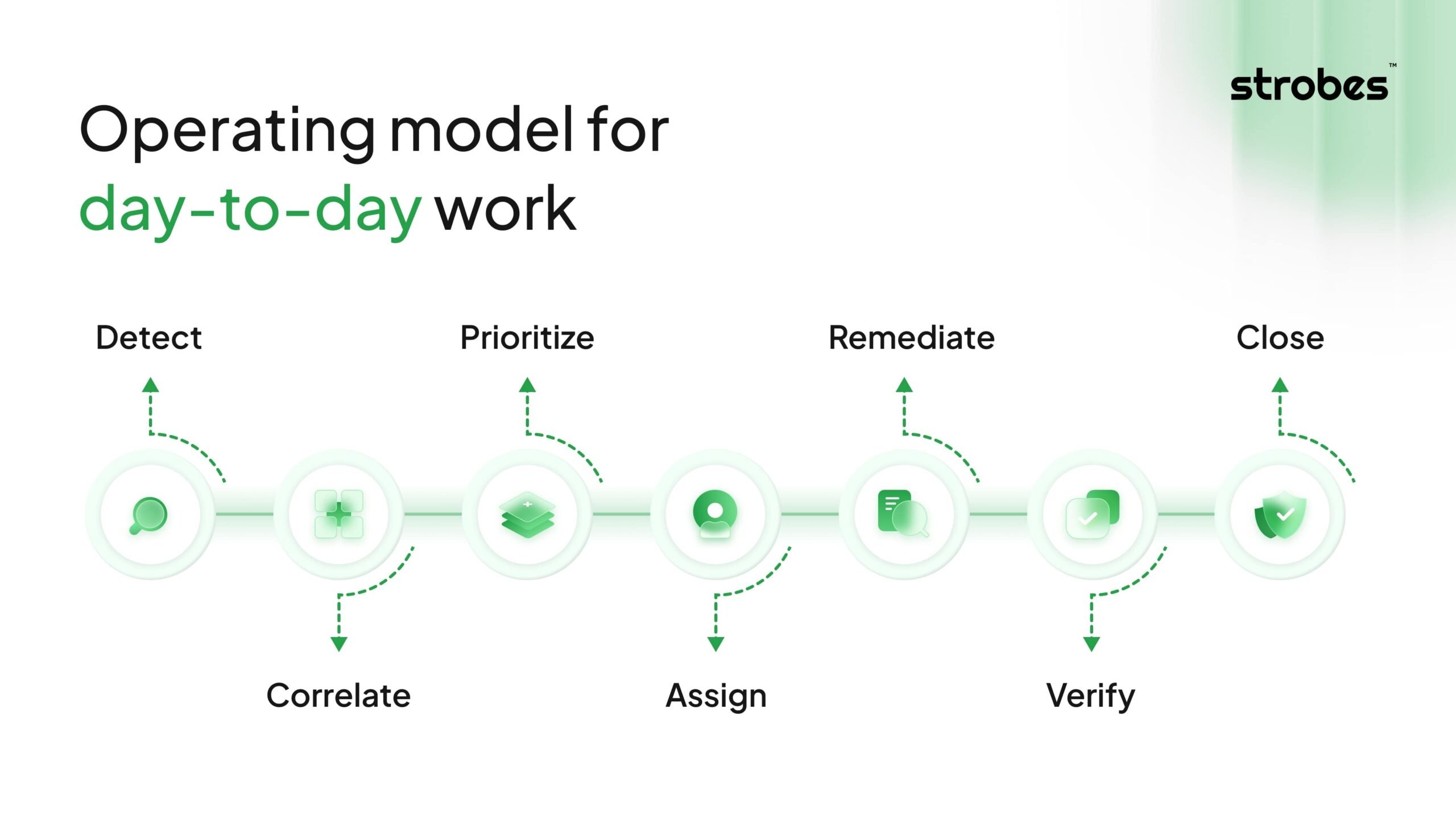 Detect:
Detect:
Ingest findings from all relevant sources so nothing falls through the cracks. Pull data from scanners, cloud providers, repositories, container registries, external attack surface monitors, bug bounty programs, and pentests. Normalize fields such as asset ID, service name, severity, timestamp, and evidence links at intake. Tag each item with the source and environment, for example prod or staging, so later analysis is easier. A good intake stream is reliable, timestamped, and lossless with clear error logs.
Correlate:
Reduce noise before you ask anyone to act. Deduplicate identical or near-duplicate items, then merge related findings and group them by asset and service. Use stable keys from your CMDB or service catalog, such as cloud account, cluster, namespace, repo, or app ID. Tie each group to a single owner so there is no debate on who moves first. Flag conflicts, for example two owners for one service, and resolve them in your weekly review.
Prioritize:
Focus teams on work that meaningfully reduces risk. Apply risk rules that consider reachability, real exploit intelligence, business impact, data sensitivity, and control gaps. Raise priority for items with public exploit code, internet exposure, or weak authentication. Lower priority for issues proven unreachable in production paths. The output should be a short, ranked list per owner. If the list is long, your rules need tuning.
Assign:
Meet owners where they already work. Create tickets in the owner’s system, not a separate queue. Include the affected assets, clear steps to exploit, probable impact, links to logs and evidence, and SLA targets by severity. Add acceptance criteria for closure so the owner knows what proof to attach. Keep the ticket readable, not a dump of raw scan output.
Remediate:
Give owners two clear paths. Fix the issue within the SLA or request an exception with an expiry date and compensating controls. Provide playbooks and sample fixes for common issues like dependency upgrades, misconfigurations, or IAM hardening. Track blockers such as missing test data or change windows so they can be cleared quickly. Exceptions should auto-notify stakeholders and appear on the monthly scorecard.
Verify:
Turn claims into proof before closure. Security or a pentest partner retests using the same steps to exploit, or an equivalent method, and records the result. Unit tests, integration tests, or safeguard rules can serve as evidence if they reliably prevent the issue from returning. For critical items, require a second check or monitored runtime validation. Closed means verified closed with evidence attached to the record.
Close:
Keep the system of record current and usable. Update status, link the verifying evidence, and record the root cause category to help future prevention. Roll up metrics by team and product, including time to acknowledge, time to remediate, verification rate, and aging. Feed insights back into risk rules, playbooks, and guardrails. Share a short summary in your weekly working review and publish a simple monthly scorecard so progress stays visible.
This flow makes Cybersecurity Accountability real. It also supports cybersecurity accounting, because each step can log time, cost, and impact. Over time, you will see which actions produce the most risk reduction per unit of spend.
Metrics that drive the right behavior
Choose a small set of outcome metrics and leading indicators. Keep them visible and stable.
Outcome metrics:
- Mean time to acknowledge by severity. Shows whether owners see and accept work quickly.
- Mean time to remediate by severity. Shows how long fixes take once accepted.
- Verification rate for critical items. Percentage of closed items that passed retest.
- Exposure burn-down by the team. Count of open exploitable issues over time.
- Vendor SLA adherence. Percentage of vendor findings fixed within the target.
Leading indicators:
- Discovery coverage. Percentage of assets, services, and repos in the inventory.
- Inventory freshness. Percentage updated within the last 30 days.
- SBOM availability. Percentage of services with current SBOMs.
- Validation ratio. Percentage of high-risk items with exploit intel or pentest proof.
- Quality gate pass rate. Percentage of builds passing SAST, SCA, secrets, IaC, and container checks.
Now add cybersecurity accounting:
- Risk-to-value ratio. Exposure cost divided by service revenue or business value.
- Cost-to-risk reduction ratio. Remediation cost divided by verified risk reduction.
- Exceptional cost of delay. Modeled loss per day for accepted risk beyond SLA.
- Vendor total risk cost. Vendor license cost plus risk cost minus mitigation value.
- Control ROI. Cost of a control divided by cumulative verified reduction in incidents and exposure.
These numbers help leaders make choices. They also show why Cybersecurity Accountability matters to budgets, not only to audits.
Governance cadence that actually works
Meet briefly and often, not rarely and long. Use the system of record, not slides.
- Weekly working review. Security and owners review aged items, blocked fixes, and upcoming releases. Limit to 30 minutes. The goal is to unblock an assignment.
- Monthly risk committee. Business heads review trends, exceptions, vendor performance, and funding gaps. Decide on people, budgets, and timelines.
- Quarterly board update. Share top risks, progress on outcomes, exceptions nearing expiry, and decisions needed. Keep it short and factual.
This cadence builds trust. It also keeps cybersecurity accounting current because you attach costs and returns to decisions as they happen.
Build security into the SDLC
Security in the SDLC works when it matches the developer flow.
- Plan. Threat model high-risk features. Assign owners for each service. Define non-functional requirements that reflect risk appetite.
- Build. Run SAST, SCA, and secrets scanning on commits and pull requests. Use policies that look at reachability and exploit likelihood, not raw counts.
- Test. Run DAST, API checks, IaC scanning, container scanning, and dependency checks in pre-release stages. Reduce noise with contextual rules.
- Release. Gate reachable high-severity flaws. Approve exceptions with expiry dates and compensating controls.
- Operate. Monitor runtime. Link alerts to services and owners. Feed incidents back into risk rules and backlogs.
Automatic capture of evidence ought to be taken. To illustrate, a pull request can be linked to a tracked finding, evidence of successful policy is recorded, and closed after retest. This assists in Cybersecurity Accountability and reduces the audit burden. Show the cost savings of preventing rework and preventing incidents using cybersecurity accounting.
How Strobes Security helps you operationalize this
Strobes Security provides an AI-driven Continuous Threat Exposure Management platform that acts as the coordination layer for shared ownership. Here is how it maps to the model in this article.
- CTEM orchestration. Intake across scanners and sources, correlation, risk rules, and verified closure. One place to track risks by product, service, dataset, or vendor.
- Risk-Based Vulnerability Management. Prioritization based on reachability, exploit intel, asset value, and control gaps. Owners see only what matters and where to act.
- Application Security Posture Management. SDLC guardrails that align with developer flow. Evidence captured as part of normal work.
- Attack Surface Management. External visibility connected to internal owners. New assets auto-assigned to the right teams.
- Pentesting as a Service. On-demand testing and retesting tied to releases and high-risk changes. Proof attached to tickets and risks.
Reporting and cybersecurity accounting
- Exposure and closure trends by team and product.
- SLA tracking for internal owners and vendors.
- Cost and time logs that show risk reduction per dollar.
- Scorecards for weekly, monthly, and quarterly reviews.
With Strobes Security, Cybersecurity Accountability becomes daily practice. Workflows are visible. Owners are clear. Results show up in the scorecard and in finance reports.
Action checklist
- Assign owners for your top 20 applications and top 20 vendors.
- Publish SLAs by severity and vendor tier.
- Turn on risk rules that include reachability and exploit intel.
- Route prioritized work into team backlogs.
- Start a weekly 30 minute working review using the system of record.
- Launch one pentest for a high-risk service and plan retesting.
- Map vendor remediation to SLAs and escalate misses.
- Build a monthly scorecard with outcomes and leading indicators.
- Start cybersecurity accounting with a simple table linking cost, exposure, and results.
Conclusion
Shared ownership turns security from scattered tasks into a routine, measurable program that your company can run with confidence. The CISO sets the rhythm and the rules, business owners act on their services, and validation proves outcomes so audits become simpler and budgets map to results through cybersecurity accounting. If you put this model to work, you will reduce aged items, shorten time to remediate high-impact issues, and track progress with clear scorecards that leadership can trust.
Ready to make Cybersecurity Accountability real across your products, cloud, and vendors? Book a 30 minute working session with Strobes to map owners, SLAs, and metrics for your top services, or explore how Strobes CTEM, RBVM, ASPM, ASM, and PTaaS can help you run this model at scale starting this quarter.
The post Cybersecurity Accountability: Why CISOs Must Share Ownership Across the Enterprise appeared first on Strobes Security.
*** This is a Security Bloggers Network syndicated blog from Strobes Security authored by Likhil Chekuri. Read the original post at: https://strobes.co/blog/cybersecurity-accountability-why-cisos-must-share-ownership-across-the-enterprise/
如有侵权请联系:admin#unsafe.sh
