Cybersecurity researchers have shed light on a cybercriminal group called Jingle Thief that has been observed targeting cloud environments associated with organizations in the retail and consumer services sectors for gift card fraud.
"Jingle Thief attackers use phishing and smishing to steal credentials, to compromise organizations that issue gift cards," Palo Alto Networks Unit 42 researchers Stav Setty and Shachar Roitman said in a Wednesday analysis. "Once they gain access to an organization, they pursue the type and level of access needed to issue unauthorized gift cards."
The end goal of these efforts is to leverage the issued gift cards for monetary gain by likely reselling them on gray markets. Gift cards make for a lucrative choice as they can be easily redeemed with minimal personal information and are difficult to trace, making it harder for defenders to investigate the fraud.
The name Jingle Thief is a nod to the threat actor's pattern of conducting gift card fraud coinciding with festive seasons and holiday periods. The cybersecurity company is tracking the activity under the moniker CL‑CRI‑1032, where "CL" stands for cluster and "CRI" refers to criminal motivation.
The threat cluster has been attributed with moderate confidence to criminal groups tracked as Atlas Lion and Storm-0539, with Microsoft describing it as a financially motivated crew originating from Morocco. It's believed to be active since at least late 2021.
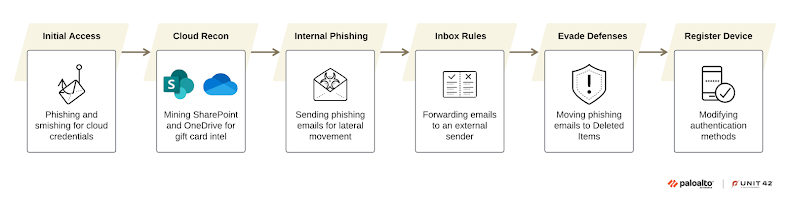
Jingle Thief's ability to maintain footholds within compromised organizations for extended periods, in some cases for over a year, makes it a dangerous group. During the time it spends with the environments, the threat actor conducts extensive reconnaissance to map the cloud environment, moves laterally across the cloud, and takes steps to sidestep detection.
Unit 42 said it observed the hacking group launching a wave of coordinated attacks targeting various global enterprises in April and May 2025, using phishing attacks to obtain credentials necessary to breach victims' cloud infrastructure. In one campaign, the attackers are said to have maintained access for about 10 months and broken into 60 user accounts within a single organization.
"They exploit cloud-based infrastructure to impersonate legitimate users, gain unauthorized access to sensitive data, and carry out gift card fraud at scale," the researchers noted.
The attacks often involve attempts to access gift‑card issuance applications to issue high‑value cards across different programs, while simultaneously ensuring these actions leave minimal logs and forensic trails.
 |
| Jingle Thief phishing attack chain across Microsoft 365 |
They are also highly targeted and tailored to each victim, with the threat actors carrying out reconnaissance before sending persuasive phishing login pages via email or SMS that can fool victims and trick them into entering their Microsoft 365 credentials.
As soon as the credentials are harvested, the attackers waste no time logging into the environment and carry out a second round of reconnaissance, this time targeting the victim's SharePoint and OneDrive for information related to business operations, financial processes, and IT workflows.
This includes searching for gift card issuance workflows, VPN configurations and access guides, spreadsheets or internal systems used to issue or track gift cards, and other key details related to virtual machines and Citrix environments.
In the next phase, the threat actors have been found to leverage the compromised account to send phishing emails internally within the organization to broaden their foothold. These messages often mimic IT service notifications related to IT service notifications or ticketing updates by making use of information gleaned from internal documentation or previous communications.
Furthermore, Jingle Thief is known to create inbox rules to automatically forward emails from hacked accounts to addresses under their control, and then cover up traces of the activity by moving the sent emails immediately to Deleted Items.
In some cases, the threat actor has also been observed registering rogue authenticator apps to bypass multi-factor authentication (MFA) protections and even enrolling their devices in Entra ID so as to maintain access even after victims' passwords are reset or the session tokens are revoked.
Besides their exclusive focus on cloud services rather than endpoint compromise, another aspect that makes Jingle Thief's campaigns noteworthy is their propensity for identity misuse over deploying custom malware, thereby minimizing the chances of detection.
"Gift card fraud combines stealth, speed and scalability, especially when paired with access to cloud environments where issuance workflows reside," Unit 42 said. "This discreet approach helps evade detection while laying the groundwork for future fraud."
"To exploit these systems, the threat actors need access to internal documentation and communications. They can secure this by stealing credentials and maintaining a quiet, persistent presence within Microsoft 365 environments of targeted organizations that provide gift card services."
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.