Welcome to Day One of Pwn2Own Ireland 2025! We have 17 attempts today with some exciting research on display. We’ll be posting results here as we have them, and follow us on Twitter, Mastodon, and Bluesky.
SUCCESS - Team Neodyme used a stack based buffer overflow to exploit the HP DeskJet 2855e. They earn $20,000 and 2 Master of Pwn points.

Daniel Kilimnik of Team Neodyme shows off his successful exploitation
SUCCESS - Nguyen Hoang Thach (@hi_im_d4rkn3ss), Tan Ze Jian, Lin Ze Wei, Cherie-Anne Lee, Gerrard Tai of STARLabs (@starlabs_sg) used a heap based buffer overflow to exploit the @CanonUSA imageCLASS MF654Cdw. They earn themselves $20,000 and 2 Master of Pwn points.

A successful attempt against the Canon printer
SUCCESS - @Tek_7987 & @_Anyfun (@Synacktiv) used a stack overflow to achieve rootlevel code execution on the Synology BeeStation Plus. They earn $40,000 and 4 Master of Pwn points in the process.
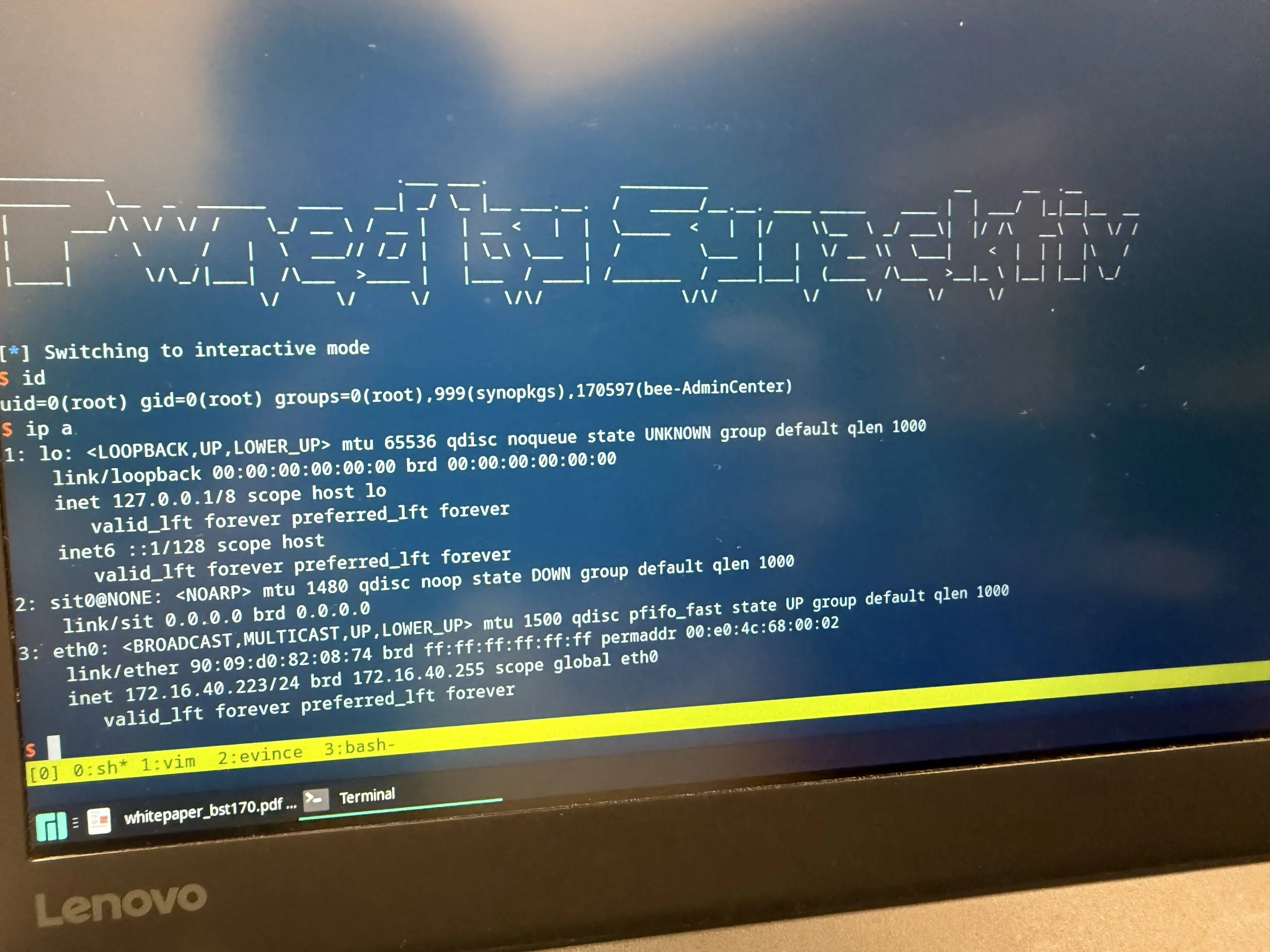
Pwned by Synactiv
SUCCESS - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS used a magnificent eight different bugs - including multiple injections - to complete their SOHO Smashup of the QNAP Qhora-322 + QNAP TS-453E. They earn $100,000 and 10 Master of Pwn points.
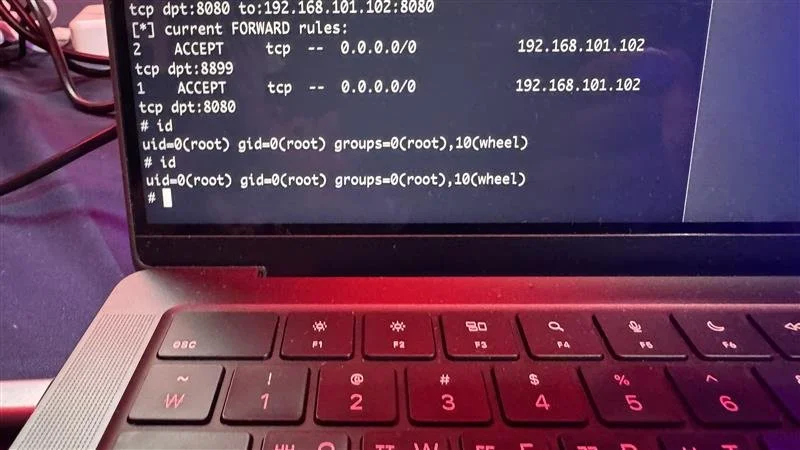
Demonstrating root level access

ZDI Analysts Neal Brown (left) and Mat Powell observe Bongeun Koo and Evangelos Daravigkas of Team DDOS
WITHDRAW - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS was withdrawn their attempt of the Philips Hue Bridge.
SUCCESS - SHIMIZU Yutaro (@shift_crops) of GMO Cybersecurity by Ierae, Inc. used a stack based buffer overflow to exploit the Canon imageCLASS MF654Cdw. Their seconf round win earns them $10,000 and 2 Master of Pwn points.

Nyan cat makes an appearance courtesy of GMO Cybersecurity
