From early 2022 through late 2024, a group of threat actors publicly known as APT28 exploited known vulnerabilities, such as CVE-2022-38028, to remotely and wirelessly access sensitive information from a targeted company network. The attack first compromised less secure Wi-Fi networks of multiple organizations that were in close physical proximity to the intended target. This incident brings to light the critical role that software plays in the security of modern-day wireless communication systems, both military and civilian. This attack did not require any hardware to be placed in the vicinity of the targeted company’s network as the attackers were able to execute remotely from thousands of miles away.
With the ubiquity of Wi-Fi, cellular networks, and Internet of Things (IoT) devices, the attack surface of communications-related vulnerabilities that can compromise data is extremely large and constantly expanding. Anyone who holds digital—bank account information to corporate intellectual property, to national security information—should be aware of the roles of software and cybersecurity in wireless systems and how to protect against software-based attacks.
In this blog post, we review common radio frequency (RF) attacks and investigate how software and cybersecurity play key roles in these exploitations. We start with an overview of the Open System Interconnection (OSI) model. Then we will delve into security aspects of modern wireless communication systems with examples of vulnerabilities, exploitations, weaknesses, and how these might impact the wireless system. We will conclude with software and security mitigations.
Overview of the OSI Stack
The concept of layering is a form of functional modularity that is useful in communication systems. The motivation of a layered approach is to decompose a complex design problem into more manageable ones and facilitate standardization. Similar to data representations in computing, a natural layering exists in wireless communication networks. Broadly speaking, the lowest layers relate to the physics of connectivity (i.e., wireless, copper wire, fiber optical, and so on). Layered on top of this are encodings to support the representation of binary bits and their assembly into binary strings. Above this are layers that relate to the transfer of binary strings. Above these are layers that give application-specific meanings to the binary strings. Attack surfaces and potential vulnerabilities exist at every level. As we explore layers of the OSI model throughout this section, we also look at several examples of potential software-enabled attacks at each layer.
The International Organization for Standardization (ISO) defines the OSI model as “a common basis for the coordination of standards development for the purpose of systems interconnection.” While the OSI stack is applicable to both physically wired and wireless networks, this blog post will focus on the layers of the stack from the wireless communication perspective. The OSI model is a very widely adopted scheme used to describe and manage the layering. The bottom three layers (Physical, Data Link, and Network) represent hardware aspects of connectivity. The Transport Layer serves as the central mechanism for controlling data transfer. As shown in Figure 1 below, the top three layers (Session, Presentation, and Application) are often referenced as the software layers; however, it is important to note that in modern wireless communication systems, software is prevalent in all seven layers of the OSI model stack.

Figure 1: Summary of OSI Layers derived from Stallings
Physical Layer
The Physical Layer, also called the PHY or layer 1, is the lowest layer of the OSI stack and addresses interactions of hardware, transmission, and signaling mechanisms. In modern wireless systems, the PHY is typically supported using digital, analog, and/or mixed-signal RF chips, as well as a digital baseband chip for digital signal processing (DSP) and communication algorithm processing such as channel coding. Channel coding techniques, such as Forward Error Correction (FEC), are employed in digital communications and add controlled redundancy to data to detect and correct errors introduced by interference or noise on the communication channel. At the transmitter, the encoder adds redundant bits to the original data that will be sent. At the receiver, the decoder will use these redundant bits to identify and correct errors. We will go into greater detail about error detection and correction in the Data Link Layer section below.
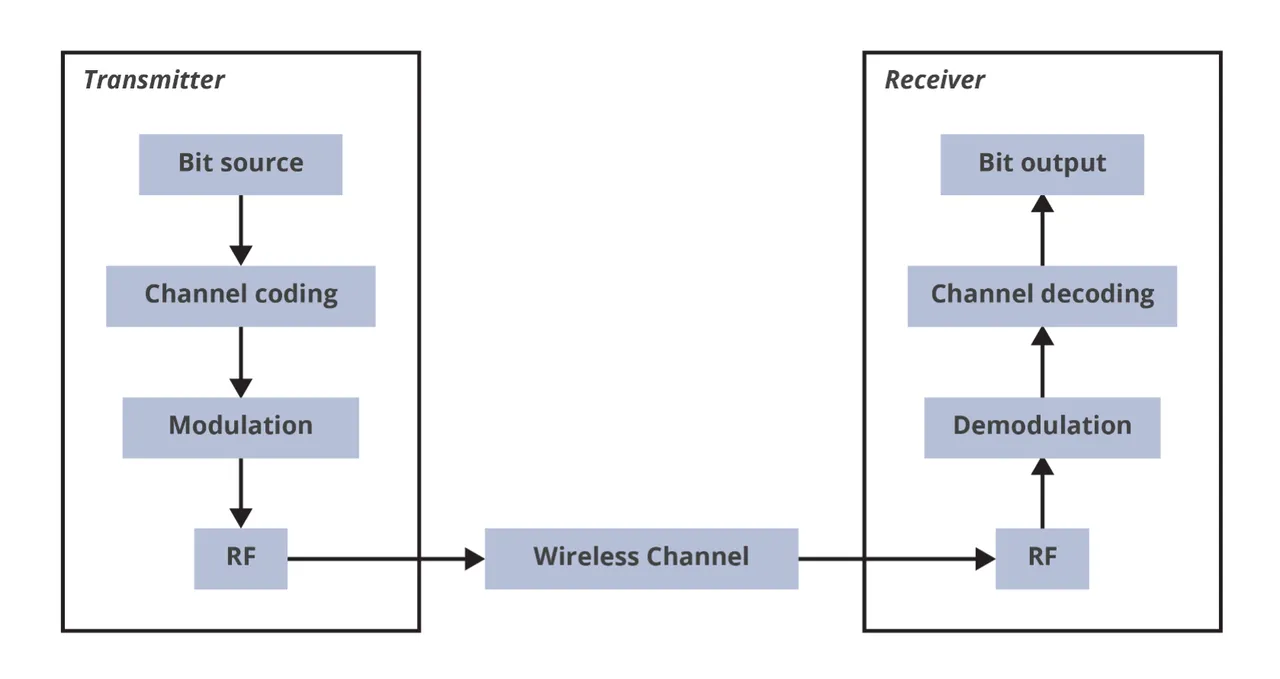
In the context of wireless communication systems, the PHY layer is responsible for sending and receiving radio frequency signals. The PHY defines the methods for transmitting raw bits over a wireless data link connecting network nodes and devices. The PHY interfaces with the Data Link Layer, which hands over the data in the form of bits that will be transmitted by the PHY. The PHY layer also manages the transition between processing the bitstream in the computational digital realm to the frequencies and emissions that are the RF realm. A common version of a binary numerical definition of a waveform gets converted into a radiating electromagnetic wave (RF wave) in the PHY. As opposed to a wired network, no particular physical medium is required; however, RF propagation characteristics vary based on the environment of the wireless transmission. A specific RF signal transmitted at a particular frequency in a particular environment is known as a channel. Depending on the system, a single channel or simultaneous multiple channels may be used. The PHY of the receiving device captures the radiated modulated RF signal and converts it back into time-sampled digital binary numbers representing the raw transmitted signal, including possible noise and errors inherited from the shared environment of the channel. For most wireless systems, frame synchronization occurs at the PHY after demodulation and ensures alignment of the receiver clocks with corresponding transmitter clocks. Frame synchronization specifies how a receiver identifies the start and end of data frames in the received bitstream by locating a unique synchronization pattern, such as a preamble, embedded in the beginning of each frame.
The bits are further organized and processed in the Data Link Layer. Figure 2 depicts a generalized Physical Layer architecture of a transmitter and receiver pair. The PHY concerns point-to-point or point-to-multipoint (i.e., broadcast) connections, as opposed to multi-hop networks, such as wireless mesh networks, which is the concern of upper layers in the OSI stack.
At the PHY Layer, an example of a software-enabled attack vector is data contamination, via signal sniffing. In this type of attack, the attacker broadcasts a signal that is stronger (i.e., higher power) than the legitimate and intended signal and is falsified to corrupt the legitimate communications link. This stronger, falsified signal at the physical layer can be employed such that the software in the wireless network that handles device connection and traffic routing is tricked into rerouting traffic to the attacker. An attacker could also disrupt or deny wireless communications by targeting synchronization signals to disrupt frame synchronization. Jamming attacks such as synchronization signal jamming and burst jamming aim to override or trick the legitimate synchronization signals of a wireless system. Another approach is to spoof or manipulate signals to mislead the receiver. For example, an attacker could inject into a Wi-Fi network forged preambles that precede the actual data frame. By spoofing the preamble in this way, the attack can force devices to wait for the expiration of an announced data frame duration, effectively silencing the channel. In another attack approach, the threat actor could spoof the well-known time synchronization standard of a Global Navigation Satellite System (GNSS), such as GPS. This attack broadcasts counterfeit GNSS signals at a higher power level than legitimate satellite signals causing the target receiver synchronization and tracking to lock onto the fake signal. This could allow the attacker to manipulate the targeted device’s perception of time or location disrupting or denying its ability to receive and decode data.
Data Link Layer
Layer 2 of the OSI model stack, the Data Link Layer (DLL), manages physical addressing (as opposed to network addressing) and access control to the PHY to detect and/or prevent data collisions in a channel. The DLL also handles error correction, data flow control, and the assurance of reliable data frame transfer across the wireless channel. On a typical wireless network, such as those defined by IEEE802, this layer is divided into two sublayers: Logical Link Control (LLC) and the Media Access Control (MAC). Every connected device is meant to have a unique MAC address, which is 48 bits long for IEEE 802 MAC addresses but could be different lengths for other standards. The DLL-MAC layer utilizes these unique addresses to manage how devices gain access to the network using protocols. The MAC address is also utilized to identify intended recipients of the data frames.
Error detection and correction is also handled in the Data Link Layer. Error-correcting codes can be used to improve the performance of a digital communication system. The typical measure of performance is the bit error rate (BER) versus energy per bit to noise density ratio (Eb/No). The BER is the probability of the reception of an incorrect bit. In the simple example shown in Figure 3, we see that the 12th bit in the stream (highlighted in blue) sent from a transmitter (Tx) was received incorrectly at the receiver (Rx). By adding controlled redundancy to the data at the transmitter before sending to the receiver, loss of data (bits) due to interference or noise encountered on the channel can be detected at the receiver and reconstructed to prevent the loss of information in the transmission. The DLL also handles the rate of data transfer (data flow) to prevent the transmitter from overwhelming the receiver(s) by sending too much data or sending data too quickly.

Figure 3: Simple Bit Error Example
The Data Link Layer is susceptible to software-enabled attack vectors including fake access point nodes, MAC address spoofing, and Wireless Local Area Network (WLAN) driver attacks.
In a fake access point attack, also known as an evil twin, the attacker establishes a malicious access point (AP) with the same Service Set Identifier (SSID) as the legitimate AP to trick user devices into connecting to a fake network. Once a device is connected to this fake network, the attacker can execute a person-in-the-middle attack to capture the device’s wireless network traffic and the data being sent and received.
MAC spoofing occurs when an attacker changes a device’s MAC address to impersonate another legitimate device on the wireless network. This can be used to bypass MAC address filtering that may be in place or to execute other types of network attacks.
To conduct a WLAN driver attack, the threat actor exploits software vulnerabilities in the wireless network card drivers of a connected device. These exploitations can expose routes to the attackers on which they can execute malicious code and gain control over wireless network or system.
Network Layer
The third layer is the Network Layer, which handles inter-network connections including managing routes for data packets, pinging servers in other networks to confirm availability, and addressing and receiving packets from other networks. Routing determines the best path for data packets to travel from a source to a destination, even across multiple networks, by using routing protocols and algorithms. Packet forwarding moves data packets from one network to another based on routing decisions, connecting different networks.
In a multi-node wireless network, data/communication packets are moved across the network from node to node, which is referred to as hopping. While wired networks more commonly have static routes due to the physical wiring between nodes, wireless routing can be either static or dynamic in nature. A wireless mesh network (WMN) is typically comprised of end node devices/clients combined with routes and gateways. If the mobility of mesh clients is minimal, the network topology tends to be mostly static. Often WMNs rely on static nodes to function as gateways and, in this way, they are similar to wired networks. By comparison, a decentralized mobile ad hoc network (MANET), is designed to not rely on pre-existing or fixed infrastructure such as routers, gateways, or wireless access points. Rather, each MANET node actively participates in traffic routing by relaying data for other nodes in the network. The decision of which nodes forward data is executed dynamically based on network connectivity and the network’s routing algorithm. Due to the dynamic nature of the routing, each node in the MANET can move independently of the other nodes, and the links to other devices may be updated frequently.
Packet sniffing or capturing and observing over-the-air data packets, is an example of a Network Layer software-enabled attack vector. Due to the over-the-air broadcast nature of wireless signals, an attacker can passively capture packets from the network and potentially gather information or intercept sensitive traffic, even below encryption layer. From this information, the attacker may be able to determine the pattern of life of the signal (i.e., how often it transmits, power levels, frequencies, etc.). As an example, packet sniffing and capturing data can be detrimental to the decentralized MANET previously discussed. To establish and maintain efficient and dynamic network routing in a MANET, metadata about each node has to be constantly sent to other nodes across the network. This creates potential information leakage if this metadata is captured via packet sniffing. Once an attacker has captured information related to the MANET message routing, they may be able to exploit vulnerabilities by focusing attacks on the routing algorithms, by isolating targeted nodes from the network, or by inserting a false node on the network with malicious intent.
Transport Layer
The Transport Layer (TL), or layer 4, resides above the Network Layer and is responsible for ensuring data packets arrive reliably and accurately between applications running on devices within the network. The transmitter TL accomplishes this by breaking large data streams into smaller, manageable segments, and the receiver TL reassembles these segments. At the TL, the most common protocols utilized to exchange messages over a network are the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). TCP is generally used for data streams that are highly reliable and must be fully and accurately communicated at the potential cost of latency. UDP can be used for lower latency data streams where the value of a missed packet might have a negligible effect, such as media streams and real-time data transmission. Once the packets and segments have been reassembled, they are pushed up to the Session Layer for the corresponding program/application on the end device. While TCP and UDP are designed to work on both wired and wireless networks, wireless versions also include additional security layers such as the Wireless Transport Layer Security (WTLS) to protect data. This additional layer of security is not typically required at the same level of protection in wired networks where physical access is a barrier to ingress. In wireless networks, the Transport Layer may also require more aggressive error control techniques than wired networks due to the higher likelihood of packet loss and corruption based on interference.
TCP hijacking is a common software-enabled attack in the Transport Layer of the OSI model stack. TC/IP hijack attacks intercept and take control of the TCP session established between two wireless devices on a network by predicting or capturing the sequence numbers used to synchronize and organize legitimate connection and interaction. With control of the TCP/IP session, the attacker can take over a user session by stealing or predicting the session token. This allows legitimate user impersonation, access to sensitive data, and ability to execute unauthorized actions on the device or network.
Session Layer
Layer 5 in the OSI model stack is the Session Layer. In a wireless system, the Wireless Session Protocol (WSP) implements the Session Layer functionality and is responsible for the establishment, maintenance, and termination of communication sessions between connected devices on the wireless network. The WSP will also manage the allocation and subsequent release of network resources during the established session.
In a similar approach to the hijacking discussed in the previous section, session fixation attacks are an example of Session Layer software-enabled attacks. In a session fixation attack, the threat actor forces an authorized user’s session ID to a predictable value then, once the user provides authentication information, the attacker can use the same ID to hijack that session with similar results to the previous layer.
Presentation Layer
The Presentation Layer, the sixth layer of the OSI model stack, is responsible for preparing data for the receiving application on the device. This layer handles tasks such as data translation, compression, and encryption (although encryption can also be done at other layers as well). In wireless systems, this layer is crucial in ensuring interoperability between different devices and systems, especially when those devices may utilize differing data formats or encoding methods. Data translation converts data between different formats, for example Unicode or its predecessor, the American Standard Code for Information Interchange (ASCII). Unicode implemented a dramatic expansion from ASCII’s original 7-bit encoding of characters to formats of 8, 16, or 32 bits, allowing for very large character sets. There are also legacy formats such as Extended Binary Coded Decimal Interchange Code (EBCDIC), still used on some mainframe computers. Data compression is employed to improve efficiency and latency by reducing the amount of information that is transmitted over the network. Encryption can also be done at the Presentation Layer, allowing for confidentiality and security of the data. The transmitter encrypts the data before transmission, and it is decrypted upon reception at the receiver node.
At the Presentation Layer, a buffer overflow attack exploits software vulnerabilities in the locations where a program writes data to a memory buffer that is not sufficiently large enough to hold all the written data. This excess data “overflows” the target memory buffer to overwrite adjacent memory locations which can be manipulated by an attacker to cause the program to crash, leak information, or execute arbitrary or malicious code. The malicious code can execute with the same level of privileges as the vulnerable application, potentially granting full access to the system. Overflowing the buffer can also corrupt important data or expose sensitive information stored in adjacent memory. Encryption implementation flaws in the Presentation Layer could also expose a vector for attacks. Exploitation of weak or improperly implemented encryption protocols can allow unintended decryption and access to sensitive data.
Application Layer
The seventh and highest layer in the OSI model stack is the Application Layer. This layer serves as the interface between the end user and applications to access the wireless network services. The Application Layer handles tasks such as email services and protocols utilized for web browsing including the Simple Mail Transfer Protocol (SMTP) and Hypertext Transfer Protocol (HTTP). This layer ensures that a given application can effectively communicate with other applications on different devices and networks. However, it is important to note that the Application Layer is not an application itself.
Given that the Application Layer is almost entirely composed of software, there are many attack vectors and vulnerabilities that can be exploited. Specific examples include Structured Query Language (SQL) Injection, Cross-Site Scripting, and Border Gateway Protocol (BGP) Hijacking.
SQL is a domain-specific language used for database management systems. In an SQL injection attack, malicious SQL code is injected into the input fields of the target application, potentially leading to unauthorized access, data theft, or data corruption.
Cross-site scripting employs malicious software scripts that are injected into web applications that are then executed by a user’s web browser, often without their knowledge. Execution of these malicious cross-site scripts can lead to session hijack, as previously discussed, or to unauthorized data exfiltration.
In a BGP hijack attack, the attacker misrepresents ownership of a target website’s IP address to maliciously reroute incoming and outgoing traffic, allowing for the interception or manipulation of data.
Software Implications for Security of Wireless Communications System
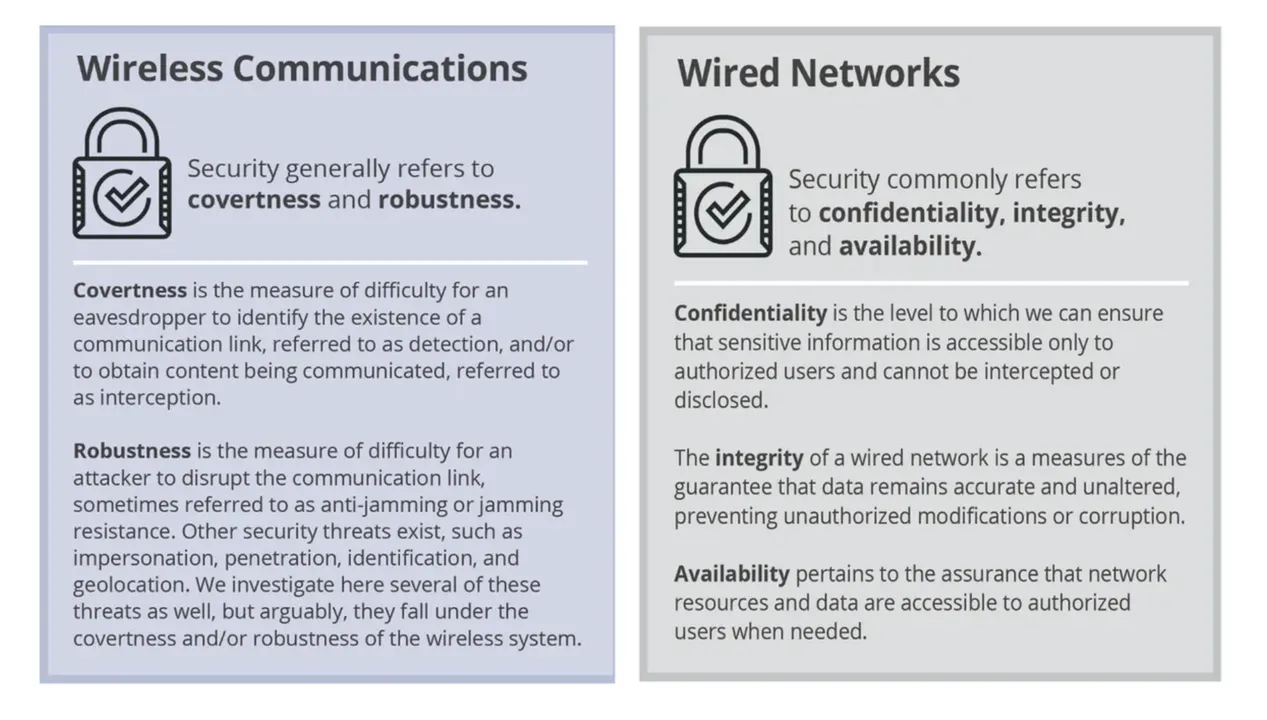
Figure 4: Contrasting Wireless and Wired Network Security
From the security and data protection perspective, it is important to contrast several characteristics of wired versus wireless networks. Figure 4 provides as quick summary of how security is typically defined for both types of networks. Both communication networks need to do channel coding and signal processing, however the approaches and techniques need to be fundamentally different. For example, in a wired Gigabit Ethernet connection, the quality of the copper wire and winding techniques in the Ethernet wire determine how channel coding and signal processing on the network can be done. The most reasonable way for an attacker to intercept and exfiltrate data is to physically access (tap) the wire. This is a substantial contrast to wireless networks where the channel and signal is potentially more publicly available due to the over-the-air, wireless nature of the links and connections. In the wireless case, the implementation needs to have robustness incorporated in the design of the signal and connection to hinder unintentional or malicious interception and exploitation. Table 1 summarizes similarities and differences between wireless and wired networks with respect to the OSI model layers.
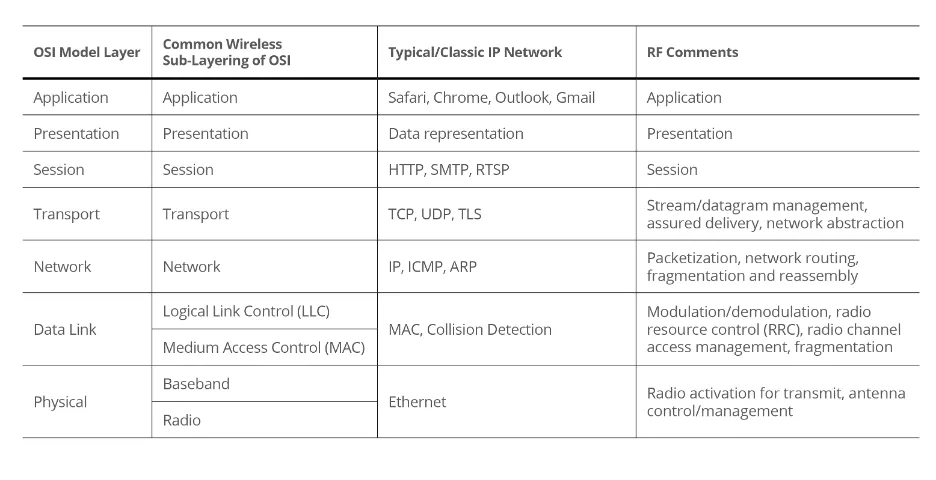
Table 1: Summary Comparison of Wireless and Wired OSI Model Layers
Software plays many critical roles in modern implementation of both wired and wireless communication systems. With respect to wireless systems, the role of software in the top three layers (Session, Presentation, and Application) should be obvious; however, what may be less discernible is the role of software in the hardware layers of the OSI stack (PHY, DLL, and Network). As previously discussed, the PHY layer is primarily focused on hardware. However, with the rise of software-defined radios, software is becoming more prevalent at the lower layers of the OSI stack as well. A software-defined radio (SDR) is a radio communication device or system that implements traditional radio hardware components (e.g., filters, mixers, modulators/demodulators, amplifiers, etc.), either on a computer or as part of an embedded system. Figure 4 below shows a simplified representation of the SDR concept for a radio receiver. The top image shows a typical analog receiver comprised of traditional hardware components, and the bottom image shows a SDR receiver with components implemented in software.
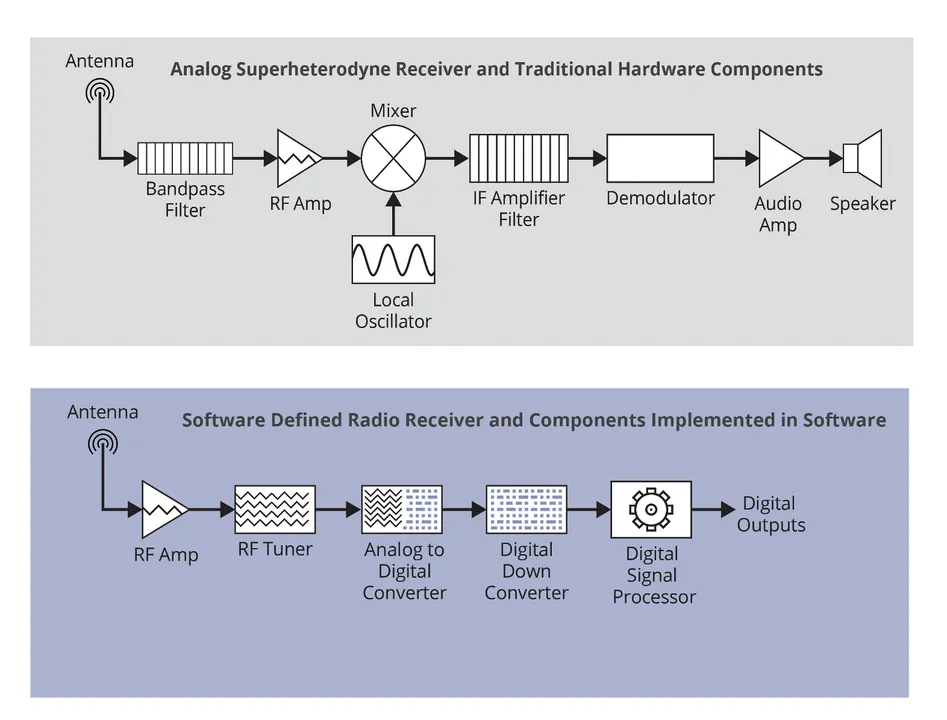
Figure 5: Top: Analog Receiver with Hardware Components; Bottom: SDR Receiver with Software Implemented Components
One of the key advantages of SDR is the use of software, which enables agile reprogrammability and reconfiguration, allowing for increased flexibility and improved performance. This enables the user to alter functionality by downloading and running new software at will. It also facilitates rapid prototyping exercises. Significant portions of the signal processing are handled by a general-purpose processor rather than special-purpose analog hardware (e.g., tubes, transistors, chips, and electronic circuits).
Often SDRs are full-duplex, which means they allow a single device to both transmit and receive simultaneously. The use of software makes it possible for a single SDR to support a variety of protocols and/or waveforms. In addition, an onboard field-programmable gate array (FPGA) can be used to encode/decode data from a variety of wireless standards as well as to encrypt or scramble data before transmission. These things can also be done directly in software; however, this approach typically requires a tradeoff in speed and latency. The ability to meet communication timing requirements, especially with fast turnaround, cannot be easily done in a general-purpose process, however it is possible to create greater flexibility in the protocol to allow for latencies in the general-purpose processor approach. Alternatively, the system can employ an FPGA or Application Specific Integrated Circuit (ASIC) to reduce the timing overhead and get more efficient use of the RF spectrum.
These configurations offer new kinds of vulnerabilities. For example, malicious software can be used to affect or reprogram an FPGA to alter the behavior of a wireless communication system. A compromised FPGA could enable attackers to modify configurations or functionality to disrupt, degrade, or usurp wireless communication systems. For example, attackers could reconfigure an FPGA to intercept and manipulate data transmitted over wireless links, jam legitimate communication signals, inject false information into the network traffic, or exploit vulnerabilities in adjacent devices or networks.
In a previous blog, RF 101: Can You Really Hack a Radio Signal?, we reviewed several of the most common types of RF attacks that can be employed to exploit vulnerabilities and intercept, disrupt, or manipulate wireless communication systems and associated protocols. Here we revisit several of these RF attacks, as well as some new concepts, to investigate how software and cybersecurity play key roles in these exploitations.
Replay Attack
Replay attacks occur when a valid transmission is captured and retransmitted to impersonate a legitimate device or user. This attack exploits vulnerabilities in the way that software systems handle data transmission, authentication, and authorization. Sensitive data that might be captured can include session tokens or login credentials. Figure 5 depicts an example of a basic replay attack. The attacker captures a valid authentication message sent by a legitimate user and then retransmits that message at a later time to gain access to the network.

Figure 6: Replay Attack
An example of a replay attack is found in the security flaws of the Wi-Fi Protected Setup (WPS), a feature designed to simplify the methods of connecting devices to existing Wi-Fi networks via configuration possibilities such as push-button or PIN-code entry. Once initiated, the push-button method relies on the user to push a button on both the client device and the Wi-Fi router simultaneously within a set timeframe. An attacker could intercept and retransmit (replay) the legitimate client device’s signals, tricking the router into accepting an unauthorized connection.
From a software and cybersecurity perspective, there are several key techniques that can be employed to mitigate these exploitations. One step is to improve software authorization methods by using role- or attribute-based access controls, which limit user permissions, access to information, and level of interaction with the system based on their user role or user profile attributes. Other mitigation steps include enforcing least privilege to users, denying access by default, validating or re-validating permissions on every access request, encrypting sensitive data, and enforcing strong password policies.
Relay Attack
A relay attack occurs when the attacker serves as an intermediary by intercepting and relaying communications between the transmitter and intended receiver without explicitly manipulating the messages. A relay attack in a wireless network is analogous to a person-in-the-middle attack for a wired network and is sometimes referred to this way in a wireless network as well. This type of attack can be used to gain access to systems or services or to bypass security measures that are in place. Without proper validation of the origin of communications, software applications and protocols relying on authentication and encryption can be exploited by relay attacks. Figure 6 shows an example of a relay attack by way of an intercepted and transferred key fob used to unlock a car. In this example, one person could intercept to key fob signal, which is always transmitting, and relay the signal to a second person that is close to the car thus bypassing the need for the key fob to be in close proximity to the car to unlock it. Similarly, the signal to start the car can also be captured and relayed to the second person.

Figure 7: Relay Attack
Like the Wi-Fi replay attack discussed in the previous section, an attacker could utilize a relay attack to gain unauthorized access to Wi-Fi network. In this case, the attacker could use devices, such as an SDR, to relay the push-button signals between the legitimate client device and the router, thus bypassing physical proximity requirements.
While there are some physical mitigation approaches in the utilization of physical security keys (e.g., YubiKey), software security has an important role as well. Robust authentication methods, such as multi-factor authentication (MFA), metric verification, and one-time passcodes, can help to mitigate exploitations from relay attacks. However, some of these physical mitigation approaches still require wireless communications that can be spoofed. For example, attackers may be able to intercept and then send a false passcode to a cellular phone or spoof the key exchanges on a wireless multi-factor authentication device.
The APT28 nearest neighbor attack presented in the introduction is an excellent example of the ability to sidestep MFA devices. APT28 were able to utilize brute force password-spray attacks to obtain valid credentials to access the target network. However, due to MFA implementation at the targeted company, the attackers could not directly access the network with the stolen credentials. Using Remote Desktop Protocol (RDP) from several companies in proximity, the attackers were able to compromise and use privileged authentication credentials to connect to the targeted company network. The assailants were able to get around the intended company MFA devices by daisy-chaining together less secure access points from nearby companies and exploiting a multihomed network in combination with the CVE-2022-38028 vulnerability allowing Windows Operating System privilege elevation via the print spooler software. A multihomed network is one that connects a host, device, or computer simultaneously to more than one network. In the case of this multihomed network, Internet connectivity was provided via a wired Ethernet connection, however, it also provided a Wi-Fi network adapter that could be used simultaneously. While Internet-facing resources required MFA, the Wi-Fi was not protected with MFA. As a result, APT28 were able to scan for available networks within range of the Wi-Fi network adapter and connect to the target company enterprise Wi-Fi utilizing the compromised credentials. As mentioned previously, this attack did not require hardware to be placed in the vicinity of any one of the compromised networks or the companies’ physical spaces. The fully remote attack was executed in its entirety from the other side of the globe using only software vulnerabilities and exploitations to obtain privileged credentials and access the targeted company network and data that it contained.
Mitigations of such exploitations should include implementation of strong encryption and secure wireless channels for MFA codes and device communications, employment of multi-device MFA strategies, establishment of robust access controls, activity monitoring, incident response processes for MFA devices and systems, and regular updates to MFA software and firmware to address known vulnerabilities. Extensive consideration should also be given related to potential risks that Wi-Fi networks may present to security.
Applications and Considerations for National Defense
For defense applications, the role of software security in wireless communication systems is crucial. Modern warfare requires wireless communications for command and control (C2), situational awareness, autonomy, and distributed engagement in a wide range of environments. Loss of communication capabilities will almost certainly result in mission failure. To thwart C2, adversaries will aggressively seek ways to deny communications. With increasing scope, complexity, distribution, and connectivity of wireless communication systems and systems-of-systems, the potential attack surface continues to expand dramatically. An accurate understanding of the software that makes up those systems is increasingly important, from low-level code and libraries to software-defined radios and networks, up to and including the application layer interfaces, and all parts in between.
For defense applications, there are additional considerations such as
- adversarial threats: Adversaries might deliberately interfere with communication systems to deny, degrade, or disrupt connectivity as well as seek means to extract critical information/data.
- resource constraints: With increasing amounts of data required for modern-day warfare, mission tactics, techniques, and procedures must be sufficiently efficient to execute on edge devices with limited connectivity, computing power, and storage.
- impact: Communication system failures, either via connectivity or loss/theft of information, can have substantial impact on critical operations, potentially resulting in loss of data, resources, and lives.
Work with the SEI
Understanding the role of software and security in wireless communication systems is the first step towards mitigation to ensure covertness and robustness. Here at the SEI, we have expertise and experience in both software and RF engineering, and we are continuously evolving processes and tools to identify, assess, and strengthen the security of wireless communication systems. For example, we are researching the application of machine learning and artificial intelligence techniques across each layer of the OSI stack including
- PHY layer propagation prediction and channel estimation
- slice management of software-defined networks
- wireless communication system autonomy
- optimizing end-to-end communications and Quality of Service
- data compression and encryption optimization for wireless.
In addition, SEI researchers are constructing wireless experimentation ranges that provide processes, tools, and data pipelines to identify and investigate potential security risks across all layers of the wireless OSI stack. This work will be increasingly important as the disciplines of traditional cybersecurity operations and wireless communications continue to move towards convergence. To learn more about our work researching, testing, and evaluating software and security in wireless communication systems or to collaborate with us, please email [email protected].