文章指出,传统冷邮件在网络安全领域效果不佳,因为安全采购往往由突发事件(如入侵或审计失败)触发而非长期规划。成功策略应包括内容营销、监测购买信号和针对性账户营销,以在关键时刻建立信任并提供解决方案。 2025-10-20 15:14:23 Author: securityboulevard.com(查看原文) 阅读量:16 收藏

A CISO gets 50 sales emails before lunch. Your cold outreach dies with the other 49.
You've heard it before: outbound doesn't work for cybersecurity companies. CISOs don't respond to cold emails. Security tools require careful planning and board approval. Companies spend months researching before they buy.
Here's the problem: that explanation is wrong.
After analyzing data from thousands of cybersecurity deals, buyer surveys, and company filings, we found something that changes everything about how security companies should approach sales.
The real reason your cold emails fail has nothing to do with planned purchases or careful evaluation. In fact, it's the opposite.
The Data That Breaks the Myth
Let's start with what everyone already knows. Cold email in cybersecurity produces terrible results:
- Response rates sit below 1% (down from 5-7% five years ago)
- LinkedIn ads targeting CISOs cost $42-$100 per click
- Cold email converts to deals at just 0.2% (you need 500 emails for one customer)
- Cost per lead jumped 250% between 2019-2023 on LinkedIn alone
These numbers suggest that security purchases happen through careful research and planning. Companies methodically evaluate vendors, build requirements, and allocate budget. Right?
Wrong.
What Actually Triggers Security Purchases
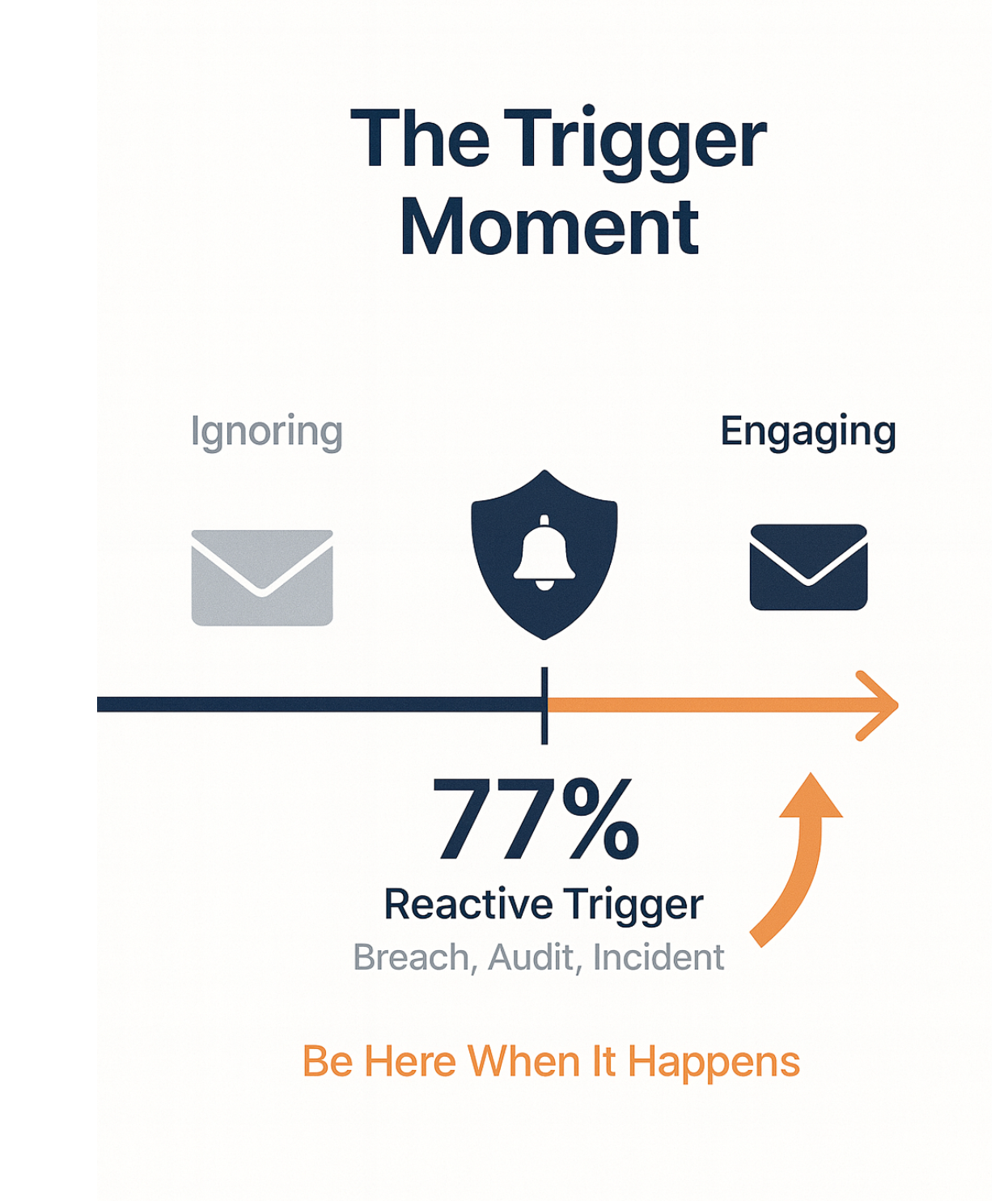
Research from Delinea surveyed hundreds of IT decision-makers about what convinced their boards to approve cybersecurity spending. The answer shocked us:
77% cited security incidents or audit failures as the trigger.
Not strategic planning. Not annual budgets. Not careful evaluation.
Fear.
Companies buy security tools when:
- They get breached
- An audit finds critical gaps
- A compliance deadline hits
- Their insurance requires specific controls
- A competitor's incident makes the board panic
Even better proof: sales cycles that normally take 18-24 months compress to just 6 months when a threat becomes real. Emergency budgets appear out of nowhere. Annual planning processes get overridden.
This explains why your cold email fails. You're sending rational messages to people making emotional decisions. You're pitching solutions when they don't yet feel the pain.
Why This Changes Everything
Think about what this means for your sales approach.
The conventional wisdom says: "Security purchases require long evaluation cycles with multiple stakeholders, so focus on inbound marketing and wait for them to come to you."
The data says: "Security purchases happen fast when triggered by fear, so you need to be positioned as the trusted expert when that trigger occurs."
This creates a completely different strategy.
What Actually Works: The Data
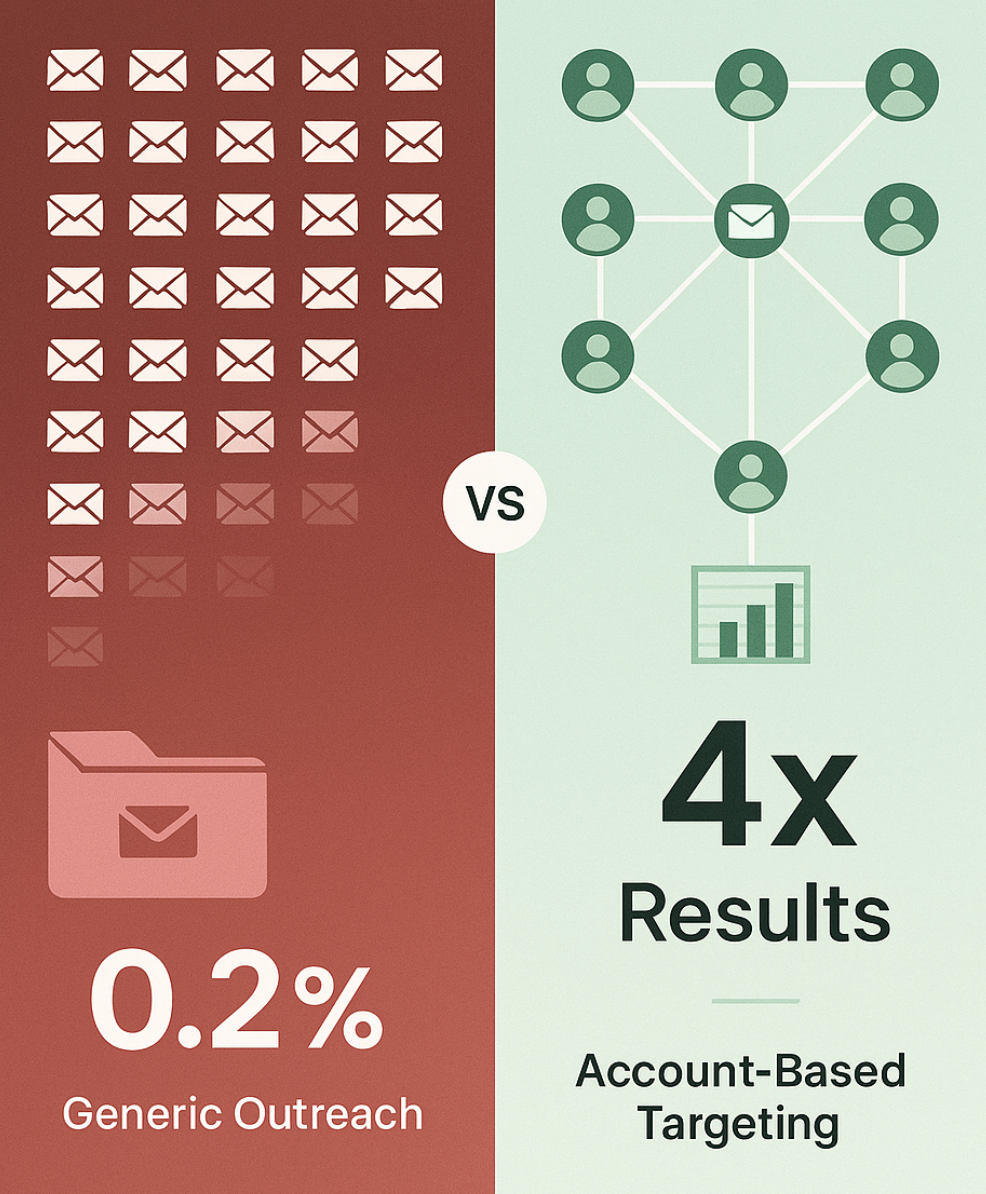
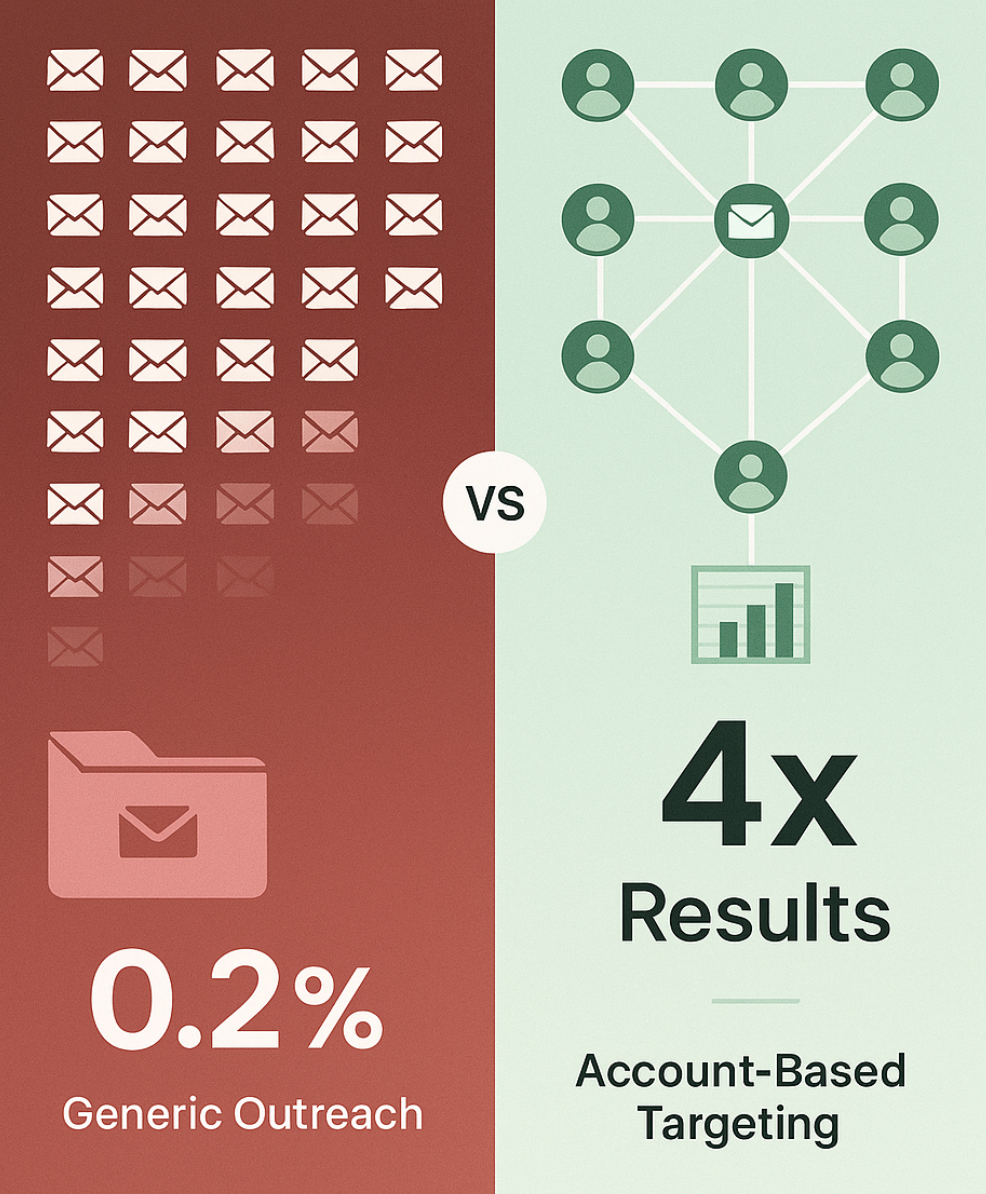
While generic cold outbound fails, targeted account-based approaches succeed:
Trend Micro achieved 4x higher engagement using account-based marketing with intent data (signals showing a company is researching solutions).
SCC's cybersecurity division saw 15% higher open rates and 5% higher click rates through targeted account selection.
T-Mobile for Business reported 3-5x increases in meeting bookings by integrating timing signals with outreach.
The pattern repeats across companies. But notice what changed: they didn't abandon outbound. They made it smarter.
The Winning Strategy: Content + Timing + Targeting
Here's what works in 2025:
1. Build Authority Before You Need It
When a breach happens, companies don't research from scratch. They already know which vendors seem credible. You build this through:
- Technical content that educates (68% of buyers read 3+ pieces before engaging)
- Webinars that teach, not sell (23% conversion rate vs. 12% B2B average)
- Threat intelligence that demonstrates expertise (CrowdStrike's approach)
Palo Alto Networks' Unit 42 reports generate leads through gated content while driving organic traffic through SEO. They don't pitch. They teach.
2. Watch for Buying Signals
Smart vendors track when companies enter reactive buying mode:
- Job postings for security roles (they're building the team)
- Website visits to pricing pages (they're evaluating costs)
- Downloads of compliance content (deadline approaching)
- Executive changes (new CISO needs wins)
- Competitor mentions (they're comparing options)
Tools like 6sense and Demandbase aggregate these signals to identify accounts moving in-market. This is when your outreach actually works.
3. Target Accounts, Not Everyone
Traditional outbound: send 1,000 generic emails, hope for 5 responses.
Account-based outbound: identify 50 accounts showing buying signals, personalize messages to 5-7 stakeholders per account, achieve 4x response rates.
The math works because you're reaching people who already have the problem. You're not creating demand. You're capturing it at the right moment.
4. Segment Your Approach
The research shows clear patterns by company size:
Enterprise (1,000+ employees):
- Need sales-led with heavy ABM
- 6-10 decision-makers involved
- 3-6+ month cycles even with urgency
- Trust analyst reports (Gartner, Forrester)
- Require extensive proof through pilots
Mid-Market ($50M-$1B revenue):
- Respond to hybrid (targeted outbound + product demos)
- 2-4 decision-makers
- 3-6 month cycles
- Trust case studies more than analyst reports
- Want balance of relationship and self-service
Small Business:
- Prefer product-led (free trials, self-service)
- 1-2 decision-makers (often the CEO)
- Quick decisions (weeks to months)
- Trust customer reviews and testimonials
- Hate sales pressure
CrowdStrike proved this pattern. They started enterprise-only, then expanded to SMBs (two-thirds of customers had under 1,000 employees by IPO). Different segments, different approaches.
What CISOs Actually Hate
Steve Ward, former CISO at The Home Depot, lists the fastest ways to lose his business:
- Going around him (pitching his team without his knowledge)
- Pestering (repeated cold calls and calendar invites)
- Lying about capabilities (overpromising, underdelivering)
He emphasizes: "I don't take risks on software. I take risks on people."
Other CISO surveys reveal additional triggers:
- Blind calendar invites (adding meetings without asking)
- Fear-mongering ("Your company is vulnerable right now!")
- Generic mass emails (obvious templates)
- Victimization tactics (rubbing salt in wounds after breaches)
The pattern: CISOs want authentic relationships with people who understand their problems. They hate transactional, pushy selling.
The Cost of Getting This Wrong
Bad outbound doesn't just fail. It costs real money:
- Customer acquisition costs top $10,000 for enterprise security deals using generic outbound
- CAC payback periods stretched from 14 to 18 months between 2023-2024
- Minimum effective spend hits $45,000-$90,000 before you know if campaigns work
Meanwhile, sophisticated ABM platforms cost $30,000-$100,000 annually but deliver measurably better results. The math only works when you stop spraying and start targeting.
A Real Example: How CrowdStrike Does It
CrowdStrike's S-1 filing reveals their approach:
Content First:
- Adversary Universe interactive map (engagement without selling)
- Podcast series (thought leadership)
- Free trials (15 days to test)
Strategic Partnerships:
- AWS Marketplace (low-friction buying)
- Dell hardware integration (embedded distribution)
- 180+ customer Champions (peer advocacy)
Reactive Services:
- Incident Response team generates $2.97 in ARR for every $1 spent
- They show up when companies panic
- Convert crisis response to ongoing platform
Multi-Channel Sales:
- Direct sales for enterprise
- Channel partners for coverage
- Product-led for SMB
- Land-and-expand (47% adopt 4+ modules)
Result: They improved sales payback from 24 to 14 months while scaling from $141M to $313M ARR in under a year.
What You Should Do Monday Morning
Based on this research, here's your action plan:
Immediate:
Stop generic cold outreach. If you're mass-emailing CISOs with templates, you're burning money and reputation.
Start content creation. One technical deep-dive published beats 1,000 cold emails. Write about actual threats, not your product.
Audit your ICP. Who actually buys from you? What triggers their purchase? (Hint: it's probably reactive, not planned.)
Short-Term:
Implement intent monitoring. Use tools to track buying signals. Free options: Google Alerts for company news, LinkedIn Sales Navigator for job changes, industry news for compliance deadlines.
Build account lists. Identify 50-100 ideal accounts. Research each one. Find the trigger events that would make them buy.
Create stakeholder maps. Security purchases involve 5+ people. Map who they are at your target accounts: CISO, CIO, CFO, CEO, compliance lead.
Medium-Term:
Launch ABM pilots. Pick 10-20 accounts showing buying signals. Create personalized campaigns. Track engagement.
Develop educational webinars. Host technical sessions teaching solutions to common problems. Don't pitch products.
Build case studies. 59% of buyers cite these as top-3 decision factors. Document how you solved similar problems.
Test segment approaches. Run different campaigns for enterprise vs. mid-market vs. SMB. Measure what works.
The Market Is Splitting
Right now, the cybersecurity market is dividing into two camps:
Winners: Companies using orchestrated multi-channel ABM with content marketing and intent signals. They achieve 4x engagement, 20% better results, and higher ROI.
Losers: Companies still mass-emailing prospects. They suffer sub-1% response rates, rising costs, and burned relationships.
The gap widens every quarter as email filters improve, CISOs become more selective, and sophisticated vendors capture the reactive buying moments.
The Real Insight
Here's what changes when you understand how security buyers actually behave:
Old thinking: "Security purchases are strategic and planned, so outbound doesn't work. We'll wait for inbound."
New thinking: "Security purchases are reactive and fear-driven, so we need to be positioned as trusted experts before the trigger, then execute targeted outreach at the moment of urgency."
This isn't about abandoning outbound. It's about making it smarter.
Build authority through content. Monitor for reactive triggers. Target specific accounts showing buying signals. Personalize your approach. Help rather than sell.
The data is clear: companies that do this achieve dramatically better results than those relying only on inbound waiting or outbound blasting.
Final Thought
The conventional wisdom that "outbound doesn't work for cybersecurity" is both right and wrong.
It's right that generic cold email fails. Response rates below 1% prove that.
It's wrong about why. Security purchases aren't planned and strategic. They're reactive and emotional.
This creates opportunity. While your competitors spam CISOs with generic pitches, you can build real authority, identify actual buying moments, and show up as the trusted expert when fear drives the decision.
The companies winning in 2025 aren't doing less outbound. They're doing smarter outbound.
The question is: which camp will you join?
Key Takeaway:
- Stop trying to create demand through cold outreach.
- Instead, build authority that positions you as the obvious choice when reactive triggers make companies urgently seek solutions.
- Use content to establish trust, intent signals to identify timing, and targeted account-based outreach to capture deals when they're actually happening.
*** This is a Security Bloggers Network syndicated blog from Deepak Gupta | AI & Cybersecurity Innovation Leader | Founder's Journey from Code to Scale authored by Deepak Gupta - Tech Entrepreneur, Cybersecurity Author. Read the original post at: https://guptadeepak.com/why-99-of-cold-emails-to-cisos-fail-and-the-surprising-truth-about-how-they-actually-buy/
如有侵权请联系:admin#unsafe.sh
